NOTE: Some exercises in this repository include answers to HackTheBox penetration challenges. To respect accepted rules & terms of the HackTheBox website, spoiler information of hacking servers in their test network environment is not published in this repository. This policy will change only if the following conditions are met: 1) the particular computers are retired or offline. In any other circumstances, information of hacking HackTheBox-related computer servers is not published in this repository. Thank you.
The information in this repository will be re-evaluated later.
-
Aim of this repository is to present and simulate multiple attack types against web applications and various OSes, including Microsoft Windows
-
This repository
-
utilizes multiple penetration methods with various tools, including Kali Linux and Metasploit Framework
-
The repository is mainly set up as a requirement by a school cource in Haaga-Helia University of Applied Sciences, Helsinki, Finland.
-
The repository contains various exercises, currently presented in Finnish but will be translated into English later.
-
OWASP WebGoat - Install OWASP WebGoat as a systemd user service
-
OWASP Zed Attack Proxy - Install OWASP ZAP as a systemd user service
-
MATE Desktop/myGtkMenu - Convert BlackArch Openbox penetration tool menu entries into myGtkMenu compliant format, use these entries with myGtkMenu
Iptables firewall ruleset featuring the following:
- Do not respond to ping echoes by clients (possibly reduce spambots)
- Drop all incoming connections, apply only SSH, HTTP and HTTPS
-
[Patch] Apache - Manipulate standard HTTP header response codes
- Manipulate HTTP header response codes returned to a client by Apache HTTP server.
- Server HTTP response codes in range 402-451 are returned as error code 400 response instead.
- Server HTTP response codes in range 500-511 are returned as error code 400 response instead.
- Server HTTP response codes in range 100-308 are returned normally, including 200 OK message.
-
[Patch] Apache - Remove default HTML error message from all error pages
-
Remove default error pages returned by an erroneous HTTP client request.
-
Remove additional HTML error messages as well (such as ones generated by servers behind an Apache proxy, if ProxyErrorOverride On directive is used)
-
NOTE: These are experimental patches for Apache HTTP web server, use with caution. Feel free to modify them! The server configuration can easily break because we break very deep standards here, just be aware and proceed with care! Thanks!
NOTE: This patchset is useful in some cases but it can bury underneath problems in server configuration. Thus, use discretion before implementing the patches in your Apache server.
NOTE: Apache will complain about missing error codes after you have applied this patchset and if you have custom error redirections in your .htaccess or in other settings. This is why you need to adjust your custom ErrorDocument directives and equivalent settings (RewriteRules, for instance) in your VirtualHost/Page configuration file (/etc/{apache2,httpd}/sites-available/*.conf).
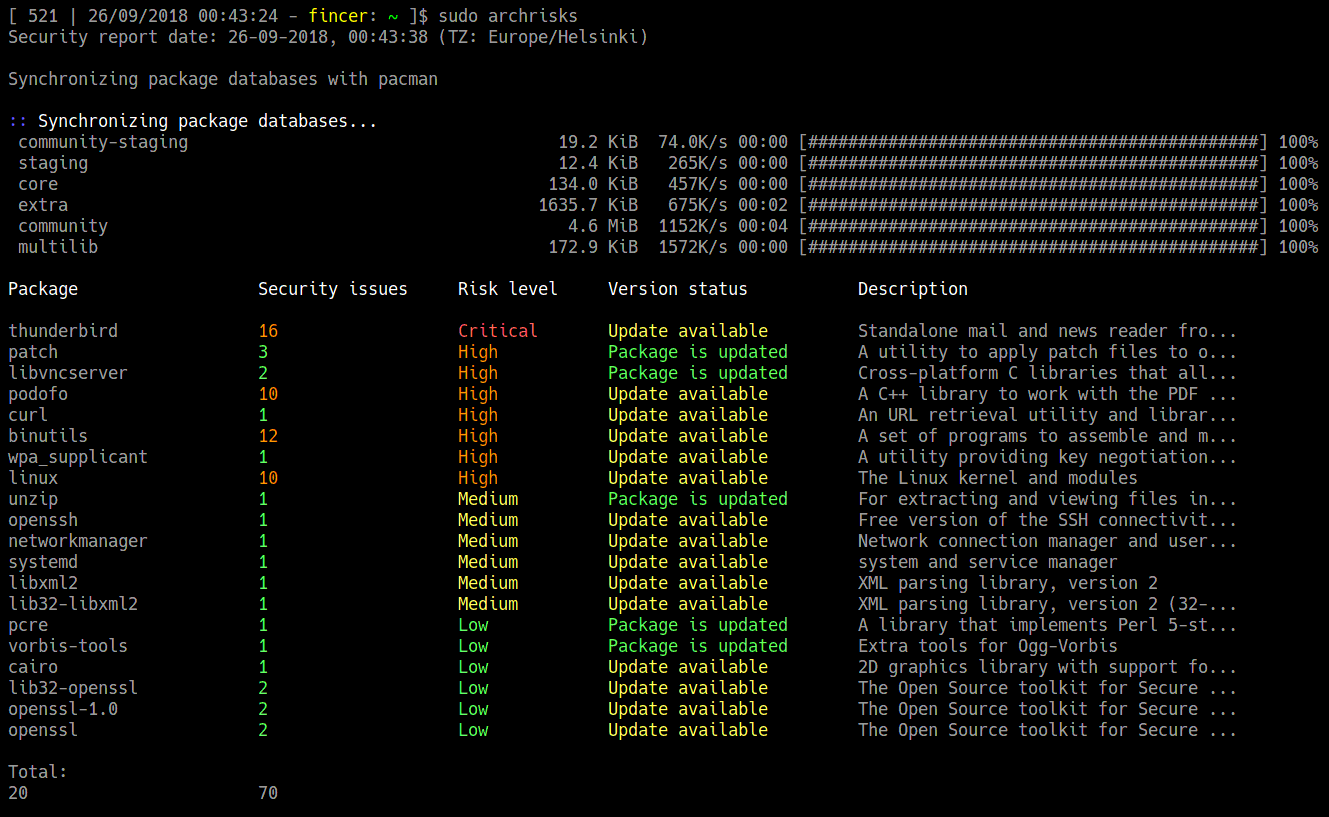
[Bash script] archrisks.sh - Fincer/archtools
Check packages on your system and find out number of potential CVE issues and evaluate generic risk of an outdated package on your Arch Linux system. Does not give detailed information, just a basic summary. Do further analysis for any package if needed on Arch security database and using regular CVE databases
-
Requires Arch Linux (core dependencies are: pacman and arch-audit, bc and bash version 4 or higher)
-
Simple bash shell script
-
CVE security information from Arch security database
-
NOTE
sudois required for package database updates retrieved bypacman. If in doubt, you can always check the script yourself (link here).
Author of this repository is not responsible for any possible illegal or malicious usage of any files or instructions provided by this repository. The repository is provided as an act of good will and does not intend to encourage users to participate in any illegal activities. All exercises presented in this repository have been carried out in a pre-configured test environment, minimizing any possible attack vectors or unintended harm to outside parties.