You havebeen called by a client to examine a sample that their IR team collected from one of their systemsin the human resourcenetwork.
Sample:
- Lab_02.zip (password =
infected)
The goals of this lab areto get comfortable analyzing a Windows Portable Executable (PE) sample and providing initial knowledge about the sample and its capabilities.This information will aid in building IOCs later.
192.168.210.10 / AdminELS / Nu3pmkfyX
- CFF Explorer
- PEStudio
- PEView
- DependencyWalker
- Resource Hacker
Question
Analyzethe DOS, NT, File,and Optional Headers of the sample given and make sure you provide details that could help answer questions similar tothe following:
- What are the file signatures and magic values?
- What machine is this sample complied to be used on?
- What was the date and time when this file was compiled?
- How many sections does this file have?
- Where will this sample be loaded in memory?
- What is the minimum Windows version required to run the sample?
- Is this ita console or GUI programand where could this be found?
- Is this an executable of a DLL? (reminder: both are PE files, but one flag is difference)
- Is the sample DEP and Terminal Server Aware?
- What is the address of the first instruction that will be executed once the file is started?
- What section is the address pointing to?
- What are the alignment settings for this sample?
- How much memory space is required for this sample?
Answer
1 - File Signature and Magic value
Open the file Lab_02.exe using CFF Explorer:
- As shown in the Dos Header, the Magic Value is
0x5A4D(MZ). - This is a signature of an EXE file
2 - What machine is this sample complied to be used on?
The related information can be found in the File Header:
- The value of the field
Machineis0x14C, which refers toIntel 386machine type. - Also this indicates it is a 32-bit application.
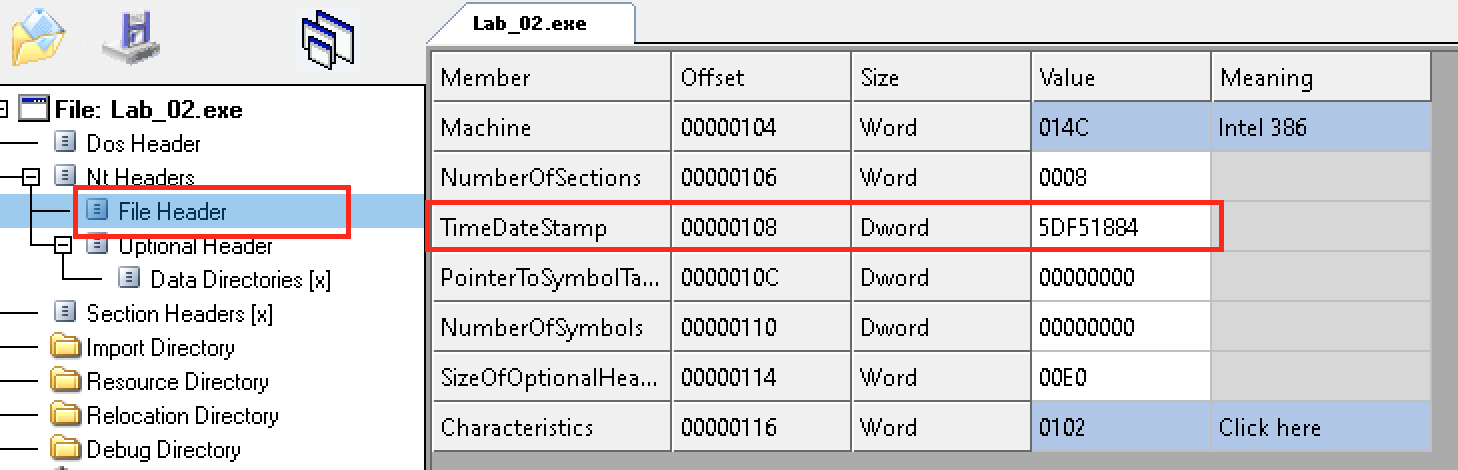
3 - What was the date and time when this file was compiled?
The datetime of compiled can be found also in the File Header:
- The
TimeDateStampis0x5DF51884(=1576343684) - Then use EpochConverter to convert the time to human-readable time:
- The compile time is
Saturday, 14 December 2019 17:14:44 GMT
4 - How many sections does this file have?
We can find the value of NumberOfSections in the File Header:
NumberOfSections=0x0008, which means the PE file has 8 sections.
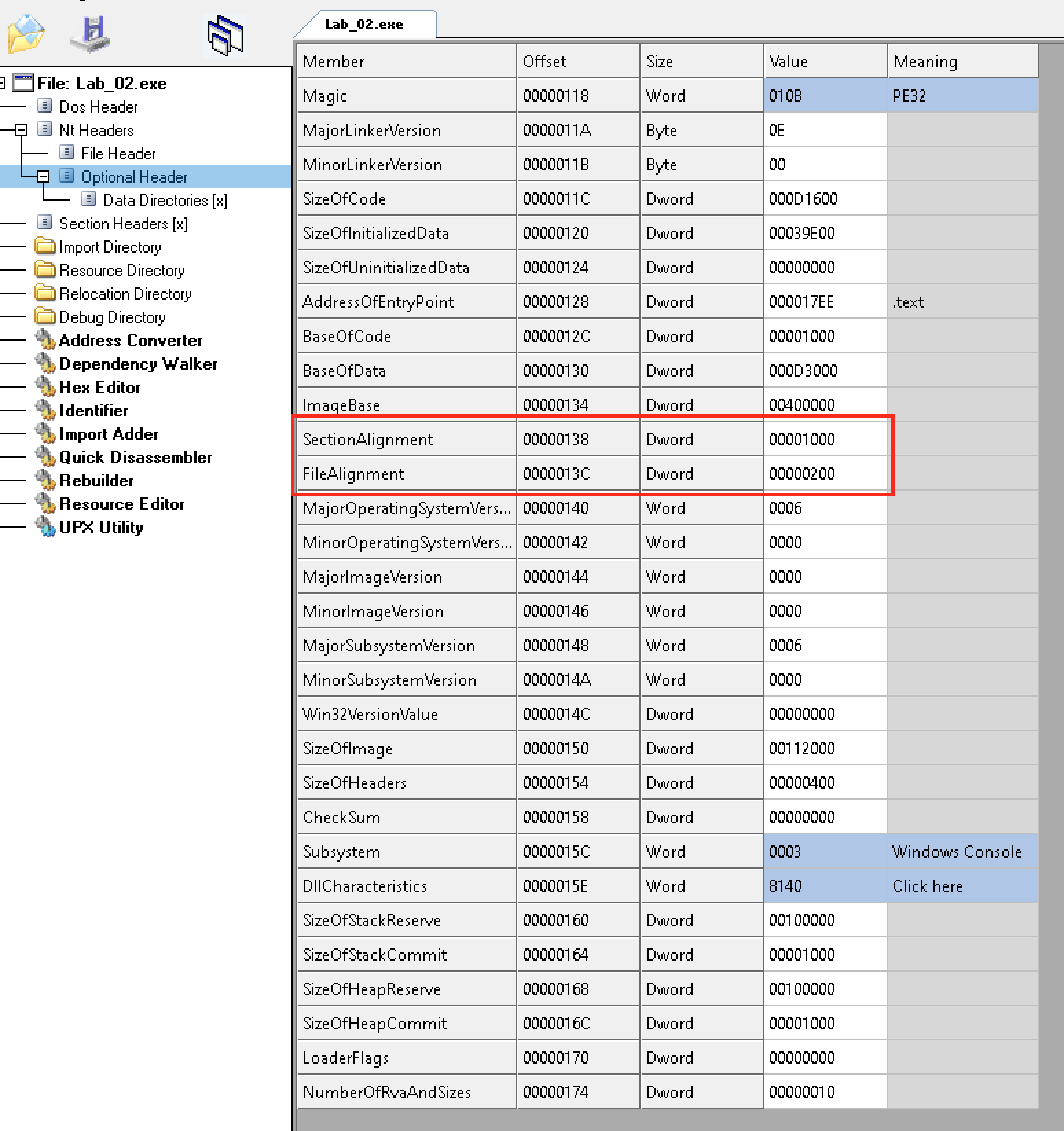
5 - Where will this sample be loaded in memory?
ImageBase located in the Optional Header indicates the preferred address of the first byte of image:
- The image will likely to be loaded at
0x00400000
6 - What is the minimum Windows version required to run the sample?
MajorSubsystemVersion indicates the Win32 subsystem major version number. This field can be found in the Optional Header.
- The minumum Windows NT Version is
6 - According to https://en.wikipedia.org/wiki/List_of_Microsoft_Windows_versions, this refers to Windows Vista
7 - Is this it a console or GUI programand where could this be found?
The field Subsystem in the Optional Header shows the required subsystem to run the image.
- The value of the
Subsystemfield is0x0003 - According to https://docs.microsoft.com/en-us/windows/win32/debug/pe-format#windows-subsystem, it means
IMAGE_SUBSYSTEM_WINDOWS_CUI - It is likely a console program (but it could also have a GUI)
8 - Is this an executable or a DLL? (reminder: both are PE files,but one flag is difference)
To check, we can inspect the Characteristics field in the File Header:
- The file is an executable but not an DLL
9 - Is the sample DEP and Terminal Server Aware?
To see if the image is compatible with DEP and terminal server aware, check the DLLCharacteristics field in the Optional Header:
IMAGE_DLLCHARACTERISTICS_NX_COMPATindicates whether the image is compatible with DEP- Therefore, the image is compatible with DEP and it is terminal server aware
10 - What is the address of the first instruction that will be executed once the file is started?
The field AddressOfEntryPoint indicates the location of the first instruction to be executed.
- The address is
0x17EE
11 - What section is the address pointing to?
The EntryPoint points to .text as indicated in the screenshot.
12 - What are the alignment settings for this sample?
We can find the alignment information in the Optional Header:
SectionAlignment:0x1000FileAlignment:0x200
13 - How much memory space is required for this sample?
The required memory space is represented by the field SizeOfImage in the Optional Header:
Question
Analyzethe Section Headers of the sample given and make sure you provide details that could help answer questions similar to the following:
- How many sections does this sample have and what are they?
- Provide a brief about each section (type of data that could be found in it).
- Provide details of at least three sections covering its:
- VirtualSize
- VirtualAddress
- SizeOfRawData
- PointerToRawData
- Characteristics
Answer
1 - How many sections does this sample have and what are they?
The number of section can be found in File Header:
- Number of section:
8
The sections layout can be found in the Section Headers:
.text.rdata.data.idata.gfids.00cfg.rsrc.reloc
2 - Provide a brief about each section (type of data that could be found in it).
| Section | Description |
|---|---|
.text |
The code of the program |
.rdata |
Imported information or read-only data |
.data |
Initialized data |
.idata |
Information about imported functions - Import Directory, Import Address Table |
.gfids |
Section added by Visual Studio 14.0 |
.00cfg |
Control flow guard CFG section added by newer version of Visual Studio |
.rsrc |
Resource information for a module |
.reloc |
Information for base relocations - if required files cannot be loaded their preferred addresses (because already something mapped to it) instructions or variables relocated with that information. |
3 - Provide details of at least three sections covering its: VirtualSize / VirtualAddress / SizeOfRawData / PointerToRawData / Characteristics
.text
- VirtualSize: 857160 bytes
- VirtualAddress:
0x00001000 - SizeOfRawData: 857600 bytes
- PointerToRawData:
0x00000400 - Characteristics:
0x60000020(Is executable, Is readable, Is writable, Contains code)
.rdata
- VirtualSize: 185528 bytes
- VirtualAddress:
0x000D3000 - SizeOfRawData: 185856 bytes
- PointerToRawData:
0x000D1A00 - Characteristics:
0x40000040(Is readable, Is writable, Contains initialized data)
.data
- VirtualSize: 12424 bytes
- VirtualAddress:
0x00101000 - SizeOfRawData: 6144 bytes
- PointerToRawData:
0x000FF000 - Characteristics:
0xC0000040(Is readable, Is writable, Contains initialized data)
Analyze the Import Sectionof the sample given and make sure you provide details that could help answer questions similar to the following:
- What are the libraries (DLLs) being imported / referenced?
- How many functions are imported from each DLL?
- What are the functions being imported? List all of them.
- Are all functions imported by name? If not provide an example and explain why, what does it mean, and what is the difference?
- Can you map the imports to their function names?
- What capabilities can you attribute to it based on imports?
- Is the function
WSAStringToAddressAimported by this file? - How many functions are exported?
1 - What are the libraries (DLLs) being imported / referenced?
Check the Import Directory:
WS2_32.dll, DNSAPI.dll, KERNEL32.dll and ADVAPI32.dll
2 - How many functions are imported from each DLL?
Referring to the table in [1],
WS2_32.dll - 25
DNSAPI.dll - 1
KERNEL32.dll - 105
ADVAPI32.dll - 3
3 - What are the functions being imported? List all of them.
Clicking through each of the DLL on the table:
WS2_32.dll:
- WSAStringToAddressA (The
WSAStringToAddressfunction converts a network address in its standard text presentation form into its numeric binary form in a sockaddr structure, suitable for passing to Windows Sockets routines that take such a structure.)
DNSAPI.dll:
- DnsQueryConfig (The
DnsQueryConfigfunction enables application programmers to query for the configuration of the local computer or a specific adapter.)
KERNEL32.dll (Kernel32.dll is the 32-bit dynamic link library found in the Windows operating system kernel. It handles memory management, input/output operations, and interrupts.):
- HeapQueryInformation
- HeapSize
- HeapReAlloc
- SetEnvironmentVariableW
- SetEnvironmentVariableA
- FreeEnvironmentStringsW
- GetEnvironmentStringsW
- GetCPInfo
- GetOEMCP
- FlushFileBuffers
- FindNextFileW
- FindNextFileA
- FindFirstFileW
- FindFirstFileA
- FindClose
- WaitForSingleObjectEx
- OutputDebugStringW
- GetTimeZoneInformation
- SetConsoleCtrlHandler
- SetStdHandle
- IsValidCodePage
- SetFilePointerEx
- GetSystemTimeAsFileTime
- FreeConsole
- WriteFile
- CloseHandle
- CreatePipe
- TerminateProcess
- CreateProcessA
- GetStdHandle
- ReadFile
- GetLastError
- PeekNamedPipe
- Sleep
- CreateThread
- FormatMessageA
- SetEndOfFile
- EncodePointer
- OutputDebugStringA
- InterlockedPushEntrySList
- UnhandledExceptionFilter
- SetUnhandledExceptionFilter
- GetCurrentProcess
- IsProcessorFeaturePresent ....
ADIAPI32.dll:
- CryptReleaseContext (The
CryptReleaseContextfunction releases the handle of a cryptographic service provider (CSP) and a key container. At each call to this function, the reference count on the CSP is reduced by one. When the reference count reaches zero, the context is fully released and it can no longer be used by any function in the application.) - CryptAcquireContextA (The
CryptAcquireContextfunction is used to acquire a handle to a particular key container within a particular cryptographic service provider (CSP). This returned handle is used in calls to CryptoAPI functions that use the selected CSP.) - CryptGenRandom (The
CryptGenRandomfunction fills a buffer with cryptographically random bytes.)
4 - Are all functions imported by name? If not provide an example and explain why, what does it mean, and what is the difference?
Not all of the functions are imported by name.
In WS2_32.dll, the most of the functions are shown and referenced as Ordinal.
However when examining the exeutable with another tool like pestudio, we can see the function names:
5 - Can you map the imports to their function names?
Use pestudio to find the function names referenced by the ordinal.
6 - What capabilities can you attribute to it based on imports?
See the remarks on [3].
7 - Is the function ‘WSAStringToAddressA’ imported by this file?
Yes - in WS2_32.dll
8 - How many functions are exported?
None
Analyze the resource section of the sample given and make sure you provide details that could help answer questions similar to the following:
- From the version information, can you find out what the original name of the file was?
- What information is presented?
- What are the security requirements for running this program?
1 - From the version information, can you find out what the original name of the file was?
No
2 - What information is presented?
Requested Privilege
3 - What are the security requirements for running this program?
The requested privilege is asInvoker.
According to https://docs.microsoft.com/en-us/cpp/build/reference/manifestuac-embeds-uac-information-in-manifest?view=msvc-160#remarks:
level='asInvoker': The application runs at the same permission level as the process that started it. You can elevate the application to a higher permission level by selecting Run as Administrator.
It means it does not require a high privilege user to run the program.If it was invoked by an administrator, it will use it;if by a normal user, it will also use it and run with that.