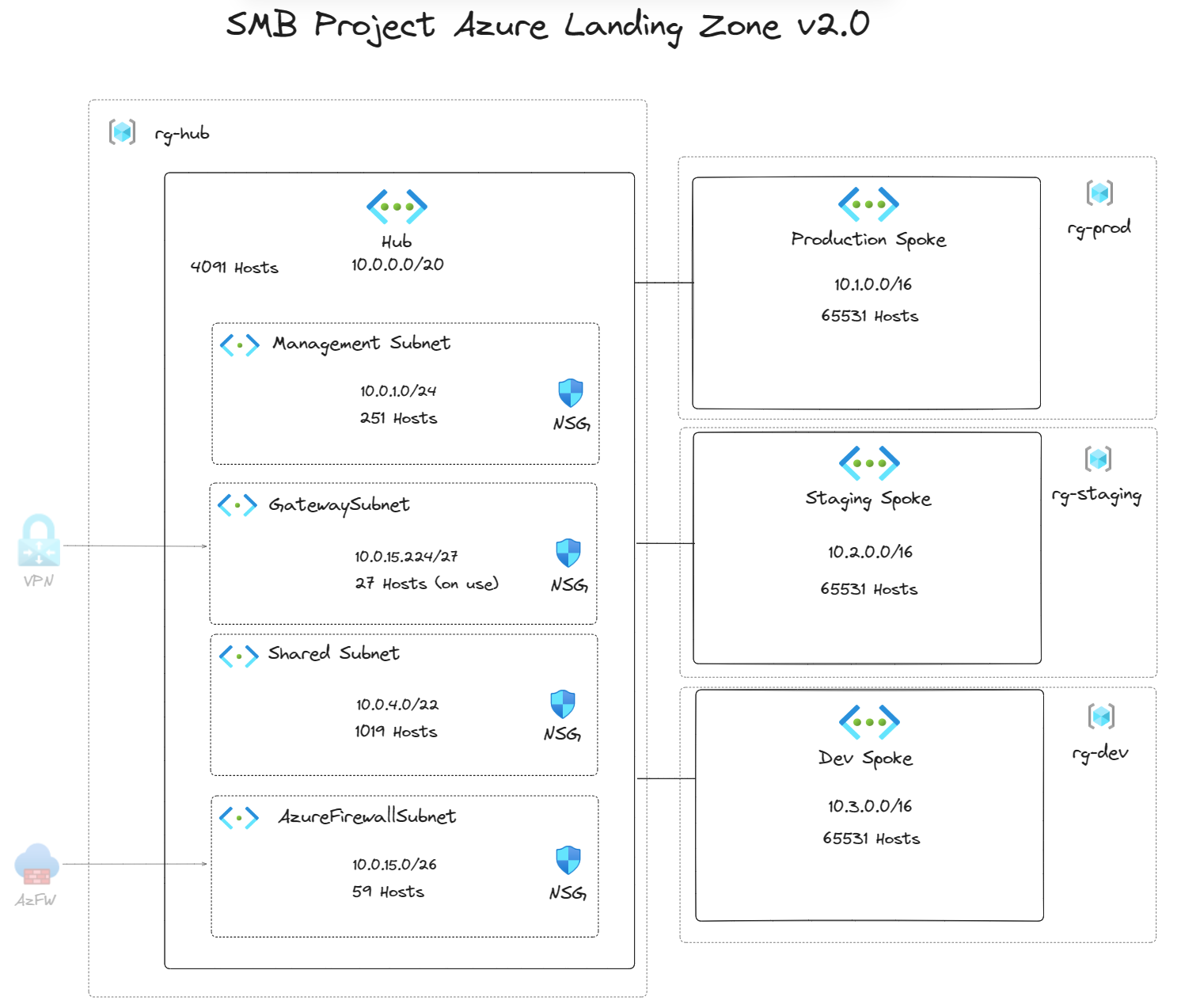
This repository contains the SMB Landing Zone, a tailored solution for small businesses and startups in the industry. The SMB Landing Zone provides an Azure landing zone to get you quickly deploy and manage your cloud resources.
-
Scalable Architecture: The SMB Landing Zone is designed to scale with your business needs, allowing you to easily add or remove resources as required.
-
Provides a good starting point: The Landing zone architecture is built small to support bigger scales with minimum complexity.
-
Security and Compliance: The landing zone follows industry best practices for security and compliance, ensuring that your infrastructure meets the necessary standards.
-
Automation: The deployment process is automated using Terraform and shell scripts, enabling you to quickly provision and manage your resources.
-
Flexability: By performing
terraform destroyyou can delete the entire landing zone and undeploy it quickly. -
Cost Optimization: The landing zone includes cost optimization strategies to help you optimize your cloud spend and maximize your return on investment. Also, resources created by this landing zone doesn't cost any money. (not included traffic from Azure and between spokes - hub)
To get started with the SMB Landing Zone, follow these steps:
-
Clone this repository to your local machine.
-
Install Terraform and ensure it is added to your system's PATH.
-
Create an app registraion in Azure and copy the client ID, tenant ID and subscription ID to the provider.tf file. Don't forget to uncomment those lines and save.
-
Grant the app registration you just created an owner role on the subscription.
-
Run
terraform initto initialize the Terraform environment. -
Run
terraform planto review the planned changes. -
Run
terraform applyto deploy the SMB Landing Zone.- Create 4 resource groups. Each represent an environment.
- Deploy 4 vnets: hub and 3 spokes each representing an environment.
- Create and auto assign subnets for each of the vnets as shown in the diagram.
- Create Network security groups for those subnets created with basic security rules.
-
Run
./associate-peering.shto associate the NSGs to each of the subnets created and peer the spoke vnets to the hub. ** make sure the script has exec permissions on the client:chmod +x associate-peering.sh.- Associate each NSG created to the relevant subnet.
- Peering each spokes vnet created to the hub vnet.
** Consider creating a Virtual Private Network and attach it to the GatewaySubnet in the Hub vnet and creating Azure firewall to associate with the AzureFirewallSubnet also for enhanced network security and secured access to private resources.
Contributions are welcome! If you have any suggestions, bug reports, or feature requests, please open an issue or submit a pull request.
- Tzahi Ariel - Initial work - zakarel
This project is licensed under the MIT License.