| layout | title | permalink |
|---|---|---|
page |
Windows Blue Team Notes |
/notes/WinBlue |
Table of Contents
- TOC {:toc}
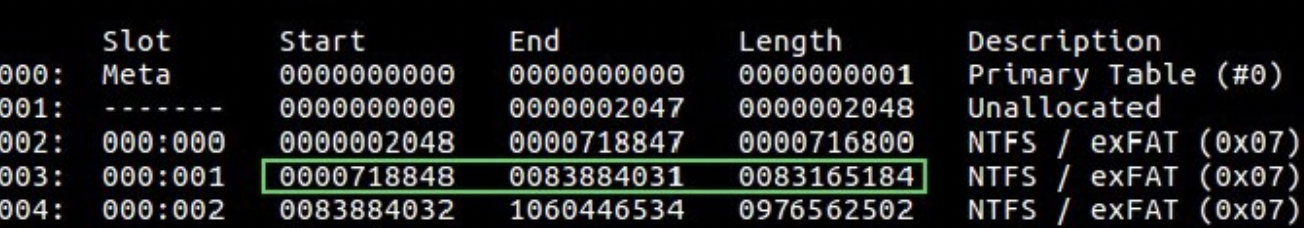
In general, this is used to list the partition table contents so that you can determine where each partition starts. The output identifies the type of partition and its length, which makes it easy to use ‘dd’ to extract the partitions.
mmls disk.image
In case you are analyzing a disk image dump for a virtual machine then you need to specify the options [-i affib].
mmls -i afflib disk.vmdk
The OS begins at partition 003, since 002 is too small and 004 is too large. Note that the OS starts at offset 718848.
Using fls, specify the OS partition offset in order to view the Files and Directories.
fls -i afflib -o 718848 disk.vmdk
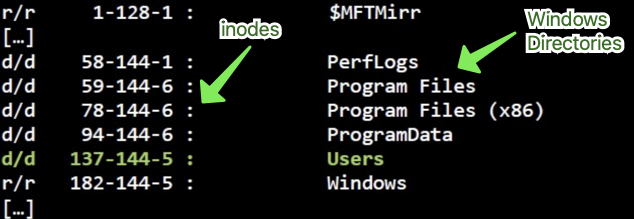
First field in output:
type from file name structure / type from meta data structure
r = regular file
d = directory
- = unknown
v = TSK (The Sleuth Kit) virtual
fls -r -m C: FILE.E01 > FILE-vss.body
for i in vss*; do fls -r -m C: $i >> FILE-vss.body;done
sort FILE-vss.body | uniq > dedup-FILE-vss.body
mactime -z UTC -y -d -b dedup-FILE-vss.body yyyy-mm-dd..yyyy-mm-dd > file.csv
Filter out the noise
grep -v -i -f noise_filter.txt file.csv > final.csv
- Change into the directory where the image or mount point is located
cd /location/of/dd/image - Create the plaso.dump KITCHEN SINK bodyfile by pointing to an image file (.dd), KAPE output (.vhdx), or a mount point (/mnt/image-mount)
log2timeline.py plaso.dump Image.dd - Select the primary partition (typically the largest sized partition)
- List the available parsers
$ log2timeline.py --parsers list | more - Create a targetted plaso.dump file (comma separate the parsers required)
log2timeline.py --parsers win7 plaso.dump /path/to/image.dd
- Get the filter files (files containing specific files & directories)
wget https://github.com/mark-hallman/plaso_filters - Create a targetted plaso.dump file
log2timeline.py -f filter_windows.txt plaso.dump /path/to/image.dd
- Run the following command to run the web history parsers against the files and locations specified in the filter file
log2timeline.py --parsers webhist -f filter_windows.txt plaso.dump /path/2/dd_image
The following command will provide these details about the bodyfile:
pinfo.py plaso.dump
- Shows start and completion time of the dump file
- Command line arguments used to create the dump file
- List of all the parsers used
- Number of events for each of the parsers
- Lists the types of exports available: Ex: l2t csv, native xlsx, and timesketch
psort.py -z utc -o list - Build a timeline (basic execution / all time)
psort.py -z utc -o l2tcsv -w timeline.csv plaso.dump - OPTIONAL - Build with a timeslice starting on 2022-02-10 15:00 (5min before and 5min after)
psort.py -z utc -o l2tcsv -w timeline.csv plaso.dump --slice '2022-02-10 15:00' - OPTIONAL - Build a timeline containing any events during Quarter 1 2020
psort.py -z utc -o l2tcsv -w timeline.csv plaso.dump "date > '2019-01-01 23:59:59' AND date < '2020-04-01 00:00:00'"
- This method does not require a bodyfile to be created. It will create the bodyfile and timeline all in one command by invoking the psort and L2T.
psteal.py --source /path/2/image.dd -o l2tcsv -w timeline.csv
- NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Run
- NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Runonce
- Software\Microsoft\Windows\CurrentVersion\Runonce
- Software\Microsoft\Windows\CurrentVersion\policies\Explorer\Run
- Software\Microsoft\Windows\CurrentVersion\Runonce
- Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit
- NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\WordWheelQuery
- NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\TypedPaths
- NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs
- SYSTEM\CurrentControlSet\Control\SessionManager\AppCompatibility
- SYSTEM\CurrentControlSet\Control\Session Manager\AppCompatCache
- SYSTEM\CurrentControlSet\Services\bam\UserSetings{SID}
- NTUSER.DAT\Software\Microsoft\Windows\Current Version\Search\RecentApps
- NTUSER.DAT\Software\Microsoft\Windows\Currentversion\Explorer\UserAssist{GUID}\Count
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces
- SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Signatures\Unmanaged
- SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Signatures\Managed
- SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Nla\Cache
stat dumped_image.mem
OR
exiftool dumped_image.mem
vol.py --info | grep Profile
vol.py -f dumped_image.mem --profile=**INSERT PROFILE** directoryenumerator
vol3.py -f dumped_image.mem windows.info.Info
Run the following:
vol3.py -f dumped_image.mem windows.getsids.GetSIDs > sids.txt
Filter the output
cut -f3,4 sids.txt | sort -u | pr -Ttd"
- Run and create output file
vol3.py -f dumped_image.mem windows.filescan > files.txt - Filter the output file
cut -f2 files.txt |pr -Ttd | head -n 20 - Filter for size of the files
cut -f2,3 files.txt |pr -Ttd | head -n 20 - Find the files you want by extension
cut -f2 files.txt | sort | grep 'ps1'
cut -f2 files.txt | sort | grep 'exe'
cut -f2 files.txt | sort | grep 'evtx'
- Search for a file
cat files.txt | grep -i Powershell | grep evtx - Pick the virtual address in the first column and feed the value into the --virtaddr flag
vol3.py -f dumped_image.mem windows.dumpfiles.DumpFiles --virtaddr 0xbf0f6d07ec10 - If the offset address is known, look at the ASCII from hex
hd -n24 -s 0x45BE876 dumped_image.mem
- Run and create output file
vol3.py -f dumped_image.mem windows.cmdline > cmd.txt - Filter the output
cut -f2,3 cmd.txt | pr -Ttd - If something catches your eye, grep for it
cut -f2,3 cmd.txt | grep -i 'powershell' | pr -Ttd"
- Run and create output file
vol3.py -f dumped_image.mem windows.netscan.NetScan > net.txt - Get everything interesting
cut -f2,5,6,9,10 net.txt | column -t - Extract just the external IPs
cut -f5 net.txt | sort -u - Extract the external IPs and their ports
cut -f5,6 net.txt | sort -u
- Run and create output file
vol3.py -f dumped_image.mem windows.pslist > pslist.txt - Filter the output
cut pslist.txt -f1,3,9,10 | column -t - Show the IDs for parent and child
cut -f1,2,3,9,10 pslist.txt
- Run and create output file
vol3.py -f dumped_image.mem windows.pstree.PsTree - Manually work it out if we follow a specific PID
cat pslist.txt | grep **INSERT PID**
- Zero in on the process you want
cut pslist.txt -f1,3,9,10 | grep -i note | column -t - Get the PID from the first column
vol3.py -f dumped_image.mem -o . windows.dumpfiles --pid **INSERT PID** - ALTERNATE METHOD (errors less)
cat pslist.txt | grep **INSERT PID**
vol3.py -f dumped_image.mem windows.pslist --pid **INSERT PID** --dump
file pid.6988.0x1c0000.dmp
- Run and create output file
vol3.py -f dumped_image.mem windows.envars.Envars > envs.txt - Filter the output
cut -f2,4,5 envs.txt
- Run and create output file
vol3.py -f dumped_image.mem windows.registry.userassist > userassist.txt - Filter the output
grep '*' userassist.txt| cut -f2,4,6,10 | pr -Ttd
This will also get the start time of a program, the program itself, and how long the program was run for.