⚠️ Disclaimer : This repository, together with its tools, is provided by Taisen-Solutions on an “as is” basis. Be aware that this application is highly vulnerable, including remote command and code execution. Use it at your own risk. Taisen-Solutions makes no representations or warranties of any kind, express or implied, as to the operation of the information, content, materials, tools, services and/or products included on the repository. Taisen-Solution disclaims, to the full extent permissible by applicable law, all warranties, express or implied, including but not limited to, implied warranties of merchantability and fitness for a particular purpose.
| CWE | Description | Difficulty | Estimated Reward in Bug Bounty |
|---|---|---|---|
| CWE-22 | Path Traversal | Medium | 500-5.000$ |
| CWE-78 | OS Command Injection | Easy | 1.000-10.000$ |
| CWE-79 | Cross-site Scripting | Easy | 500-5.000$ |
| CWE-89 | SQL Injection | Easy | 1.000-10.000$ |
| CWE-94 | Code Injection | Hard | 5.000-50.000$ |
| CWE-91 | XML Injection | Hard | 0-500$ |
| CWE-98 | Remote File Inclusion | Hard | 1.000-10.000$ |
| CWE-184 | Incomplete List of Disallowed Inputs | Hard | 1.000-10.000$ |
| CWE-213 | Exposure of Sensitive Information Due to Incompatible Policies | Very Easy | 500-2.000$ |
| CWE-284 | Improper Access Control | Medium | 1.000-5.000$ |
| CWE-287 | Improper Authentication | Medium | 500-5.000$ |
| CWE-319 | Cleartext Transmission of Sensitive Information | Very Easy | 500-2.000$ |
| CWE-326 | Inadequate Encryption Strength | Easy | 1.000-5.000$ |
| CWE-434 | Unrestricted Upload of File with Dangerous Type | Medium | 500-10.000$ |
| CWE-502 | Deserialization of Untrusted Data | Hard | 5.000-50.000$ |
| CWE-521 | Weak Password Requirements | Very Easy | 500-2.000$ |
| CWE-532 | Insertion of Sensitive Information into Log File | Very Easy | 100-2.000$ |
| CWE 639 | Insecure Direct Object Reference | Medium | 500-5.000$ |
| CWE-611 | Improper Restriction of XML External Entity Reference | Hard | 1.000-10.000$ |
| CWE-787 | Out-of-bounds Write | Easy | 500-5000$ |
| CWE-798 | Use of Hard-coded Credentials | Very Easy | 1.000-10.000$ |
| CWE-829 | Local File Inclusion | Easy | 500-2.000$ |
| CWE-918 | Server-Side Request Forgery (SSRF) | Medium | 1.000$-10.000$ |
| CWE-1270 | Generation of Incorrect Security Tokens | Medium | 1.000-20.000$ |
| CWE-1395 | Dependency on Vulnerable Third-Party Component | Easy | 0-500$ |
- Become a project sponsor and gain access to all the solutions.
- Or just buy me a coffee and get an unique Nuclei template (not for my students)
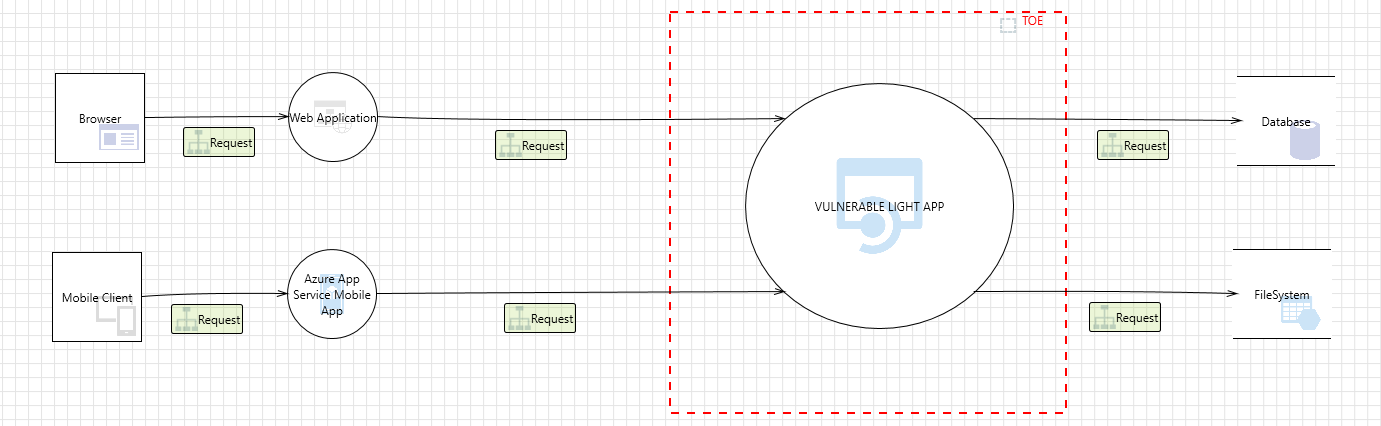
VLA is designed as a vulnerable backend application, running in the following environment :
Be aware that VLA is works on Linux and MacOS But is only tested and supported on Windows.
Check .csproj file to get the current dotnet version and install .NET SDK
git clone https://github.com/Aif4thah/VulnerableLightApp.git
cd .\VulnerableLightApp\dotnet build.\bin\Debug\net8.0\VulnerableWebApplication.exe [--url=<url>]Alternatively, you can run directly with
dotnet runVerify you use the intended .NET Framework
where dotnet
dotnet --version
dotnet --list-sdksTo trust the certificate
dotnet dev-certs https --trustdependancies have to be dowloaded from standard sources
dotnet nuget add source "https://api.nuget.org/v3/index.json" --name "Microsoft"- Special thanks to all the hackers and students who pushed me to improve this work
- Project maintened by Michael Vacarella