We’re going to be creating and configuring an IAM user, and then limiting their access via IAM Policies, Permissions Boundary’s, and Service Control Policies (SCPs).
We’re going to create a user in an organisation sub-account, then test out creating S3 buckets and IAM users, using that newly created user.
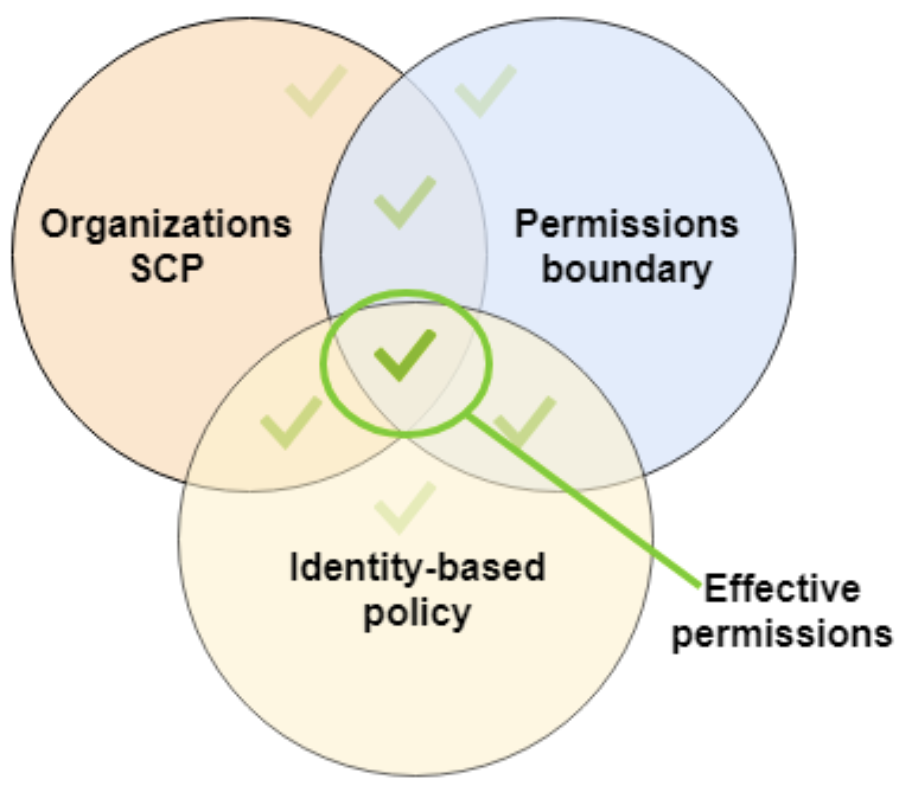
We will then use an SCP to prevent deleting buckets at the account level, and Permission Boundary’s to limit the user to performing everything in S3, all while having full AdministratorAccess at the Identity-based policy level.
The following diagram from the Cantrill Solutions Architect Professional course explains how these three permission tools work together.
Note: You will need to have an AWS Organisation set up to use Service Control Policies. They’re relatively easy to set up as long as you have 2+ AWS accounts, see the following tutorial for instructions: https://docs.aws.amazon.com/organizations/latest/userguide/orgs_tutorials_basic.html
Account: Sub-account
User: Your default user
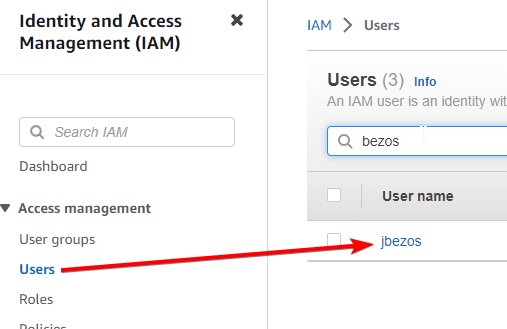
Head to the IAM dashboard: https://us-east-1.console.aws.amazon.com/iamv2/home
Go the Users page click Add Users
Enter the User Name, ensure “Enable console access” is selected, leave “Autogenerated password” selected, and leave “Users must create a new password at next sign-in (recommended)” selected. Then click Next.
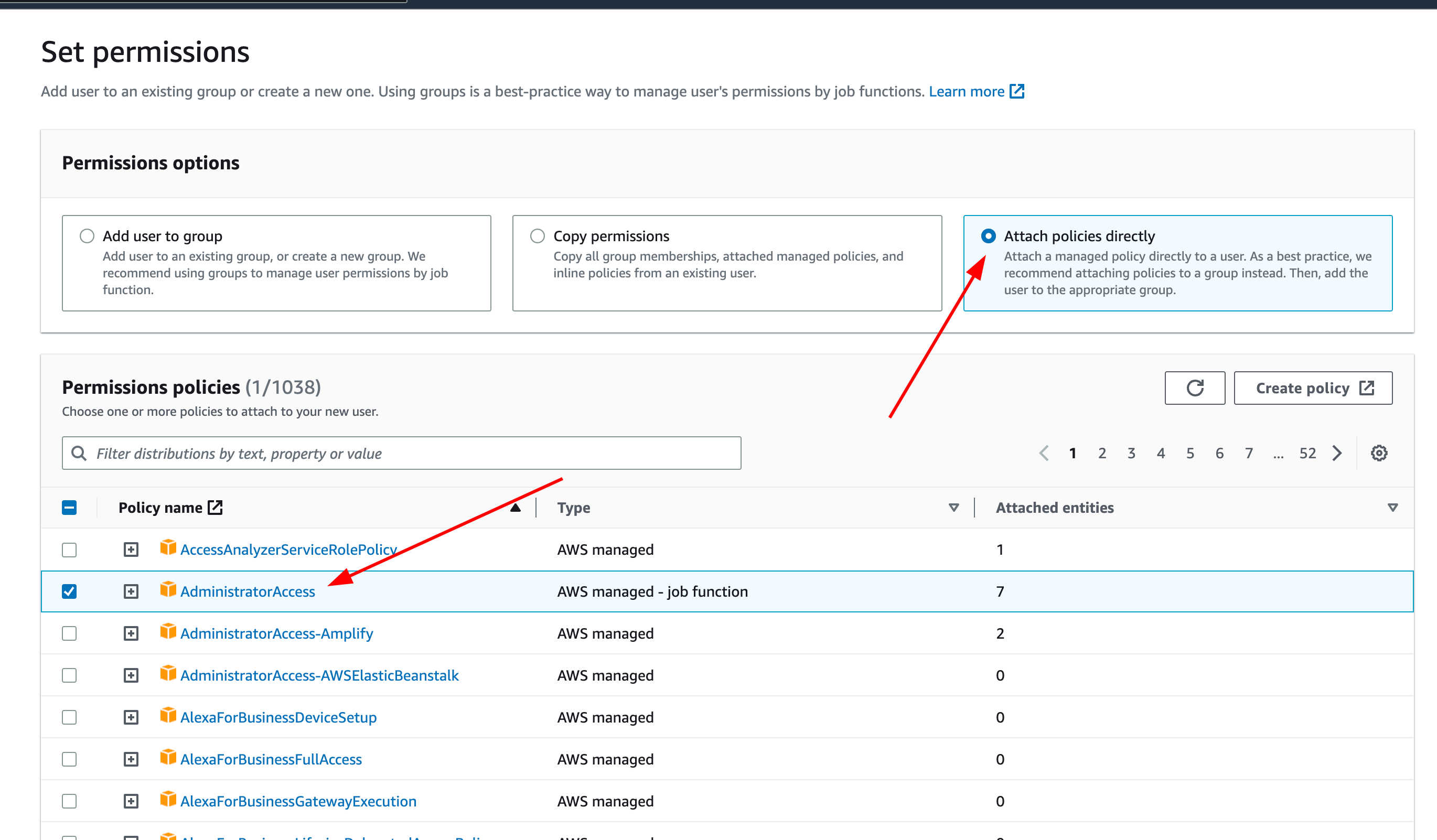
On the next page, select “Attach policies directly” and check “AdministratorAccess”
Click Next
On the next page, click Create user.
Make sure you copy down the autogenerated password as you’ll need that for the next step.
This user now has unrestricted access to perform any tasks / API calls in this AWS account, because they have the “AdministratorAccess” identity-based policy assigned.
Account: Sub-account
User: Newly created user
Let’s test out some actions, first we’ll create an S3 bucket.
Head to the S3 console: https://s3.console.aws.amazon.com/s3/buckets
Click on Create bucket
Choose any name and any region, and leave all other settings as default.
Click Create bucket
It should have created without any issues.
Let’s try and delete that bucket. Select it, and click Delete
Enter the bucket name in the confirmation window, and click Delete bucket
As expected, it worked.
Now, head to the IAM console: https://us-east-1.console.aws.amazon.com/iamv2/home
Go to Users and click Add users
Set the User name to anything you like.
Click Next
Under Permissions, select “Attach policies directly”, and select the “AdministratorAccess” policy
Click Next
Click Create user
As expected, it worked, and now the organisation has a user that was created with administrator privileges, that isn’t tracked / necessarily known by the owners or administrators of the organisation, which isn’t definitely isn’t ideal
Select the user you just created, and click Delete
In the confirmation box, enter the username and click Delete
Account: Management account
User: Your default user
Head to the AWS Organizations console: https://us-east-1.console.aws.amazon.com/organizations/v2/home/
Go to Policies then Service control policies
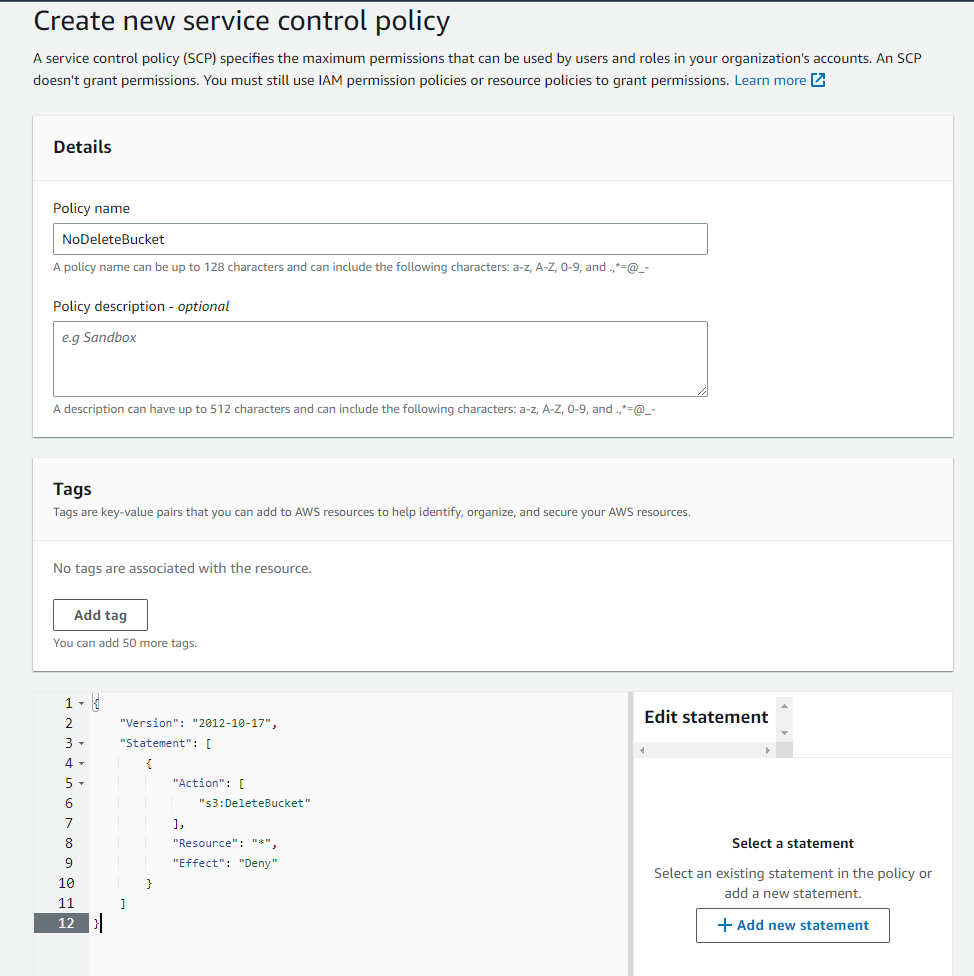
Click on Create policy
Set the Policy Name to “NoDeleteBucket”
Then in the statement box, enter
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"s3:DeleteBucket"
],
"Resource": "*",
"Effect": "Deny"
}
]
}Click Create policy
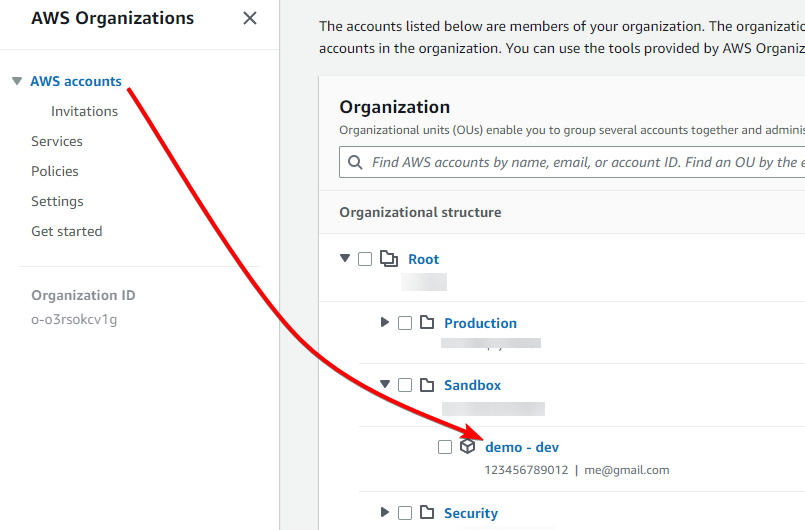
Now go to the AWS accounts page, and click on the sub-account you’re using for this demo (and where you have created your IAM user)
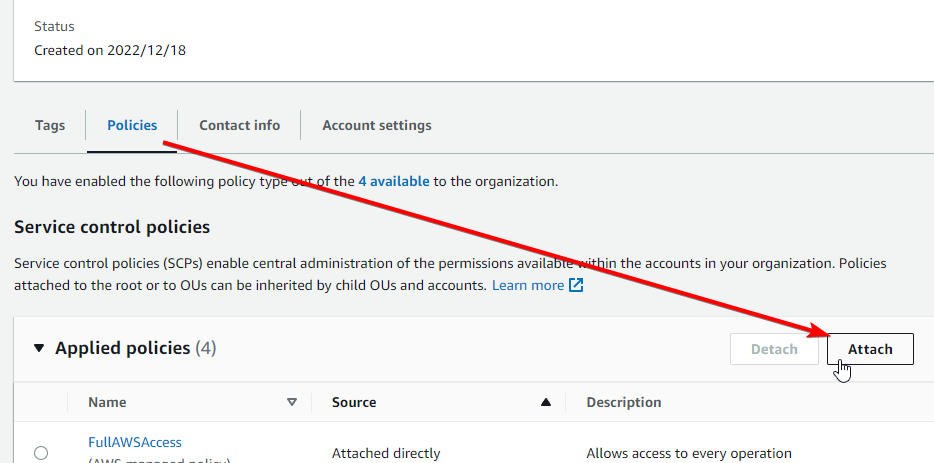
Go to the Policies tab and click Attach
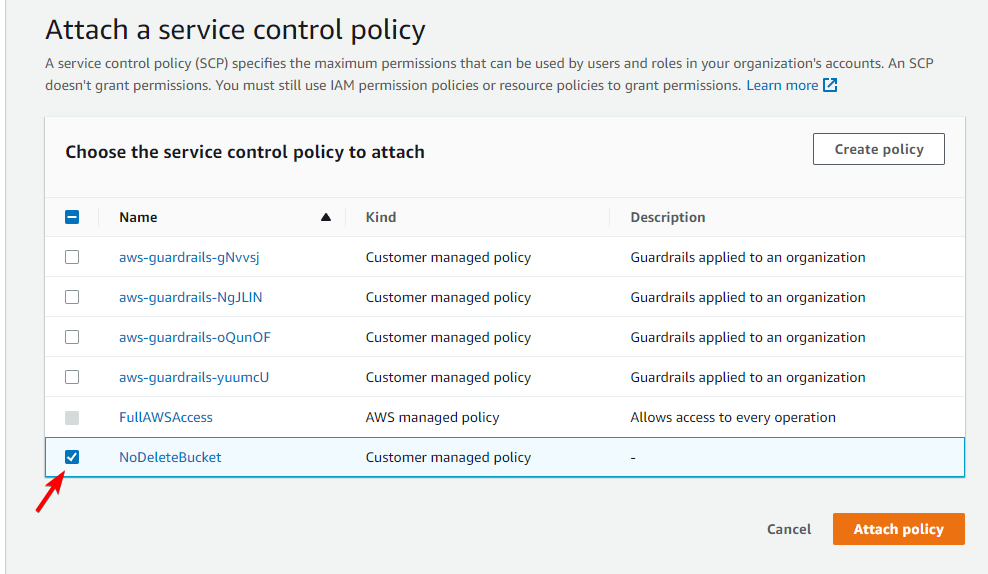
Select the NoDeleteBucket policy and click Attach policy
Account: Sub-account
User: Your default user
Head to the IAM console: https://us-east-1.console.aws.amazon.com/iamv2/home
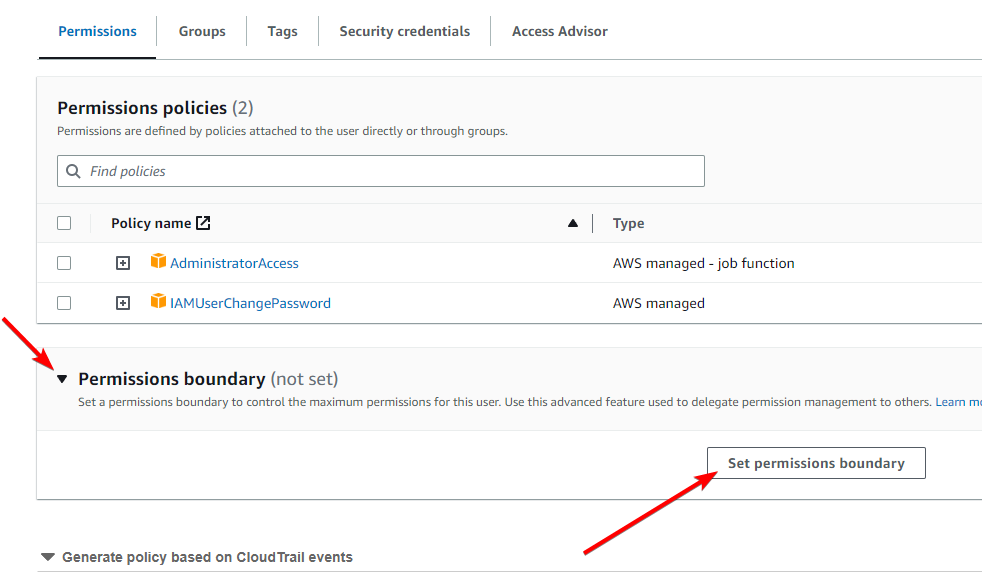
Go to Users and click on the user you created earlier
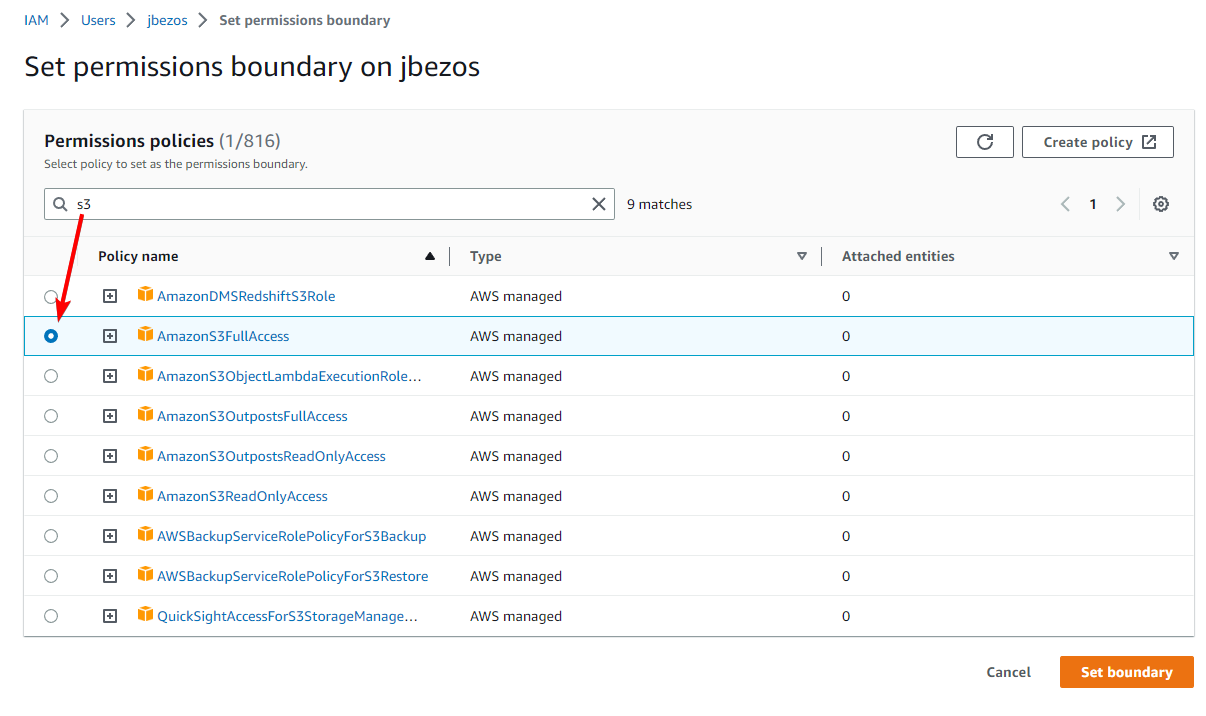
Expand “Permissions boundary” and click Set permissions boundary
Search for “AmazonS3FullAccess” and select that policy
Click Set boundary
Account: Sub-account
User: Newly created user
Login to your sub-account, as your newly created user.
First, like we did before, we’ll create a new S3 bucket.
Head to the S3 console: https://s3.console.aws.amazon.com/s3/buckets
Click on Create bucket
Choose any name and any region, and leave all other settings as default.
Click Create bucket
As expected, it worked.
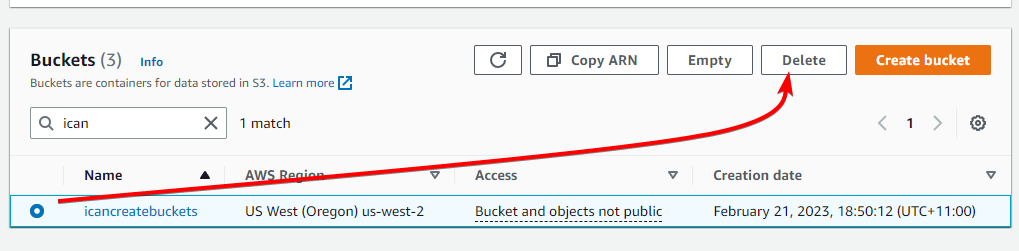
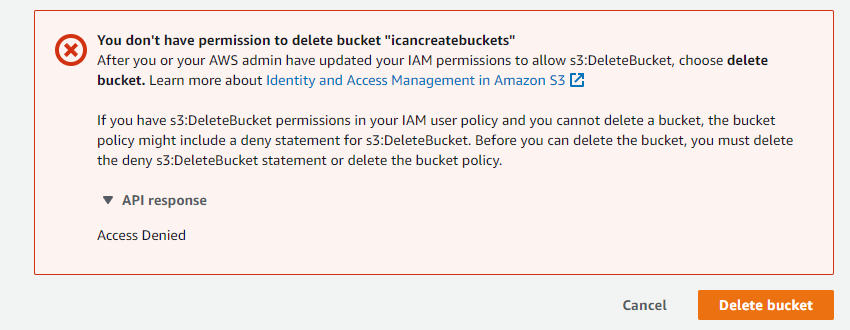
Now we’ll try and delete our newly created bucket. Select the bucket and click Delete
Enter the name of the bucket and click Delete bucket
You should receive an error:
Remember, our SCP, applied at the account level, is preventing anyone from deleting S3 buckets.
Now let’s try creating a new user like we did earlier.
Head to the IAM console: https://us-east-1.console.aws.amazon.com/iamv2/home
Immediately you will start seeing permission errors.
Even if you do go to the Users page, nothing will load, including the Create user button.
In production, this would be a lot more fine tuned, you would need to give your user access to change their password, MFA, etc, rather than just denying iam:*
Effectively, our user has three permission sets acting upon them:
IAM policy - Administrator access to everything
SCP - They can’t delete S3 buckets
Permissions boundary - The user can do anything in S3
This results in our user only being allowed to perform S3 actions, except for DeleteBucket
Account: Management account
Login to your management account
Head to the AWS Organizations console: https://us-east-1.console.aws.amazon.com/organizations/v2/home/
Go to the AWS accounts page, and click on the sub-account you’re using for this demo
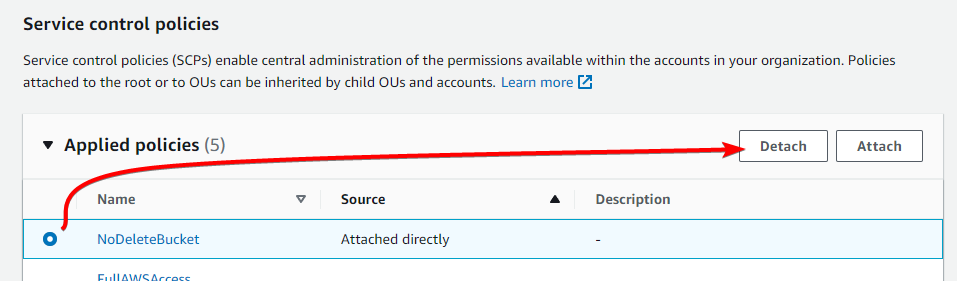
Go to the Policies tab, select our “NoDeleteBucket” policy, and click Detach
In the confirmation box, click Detach policy
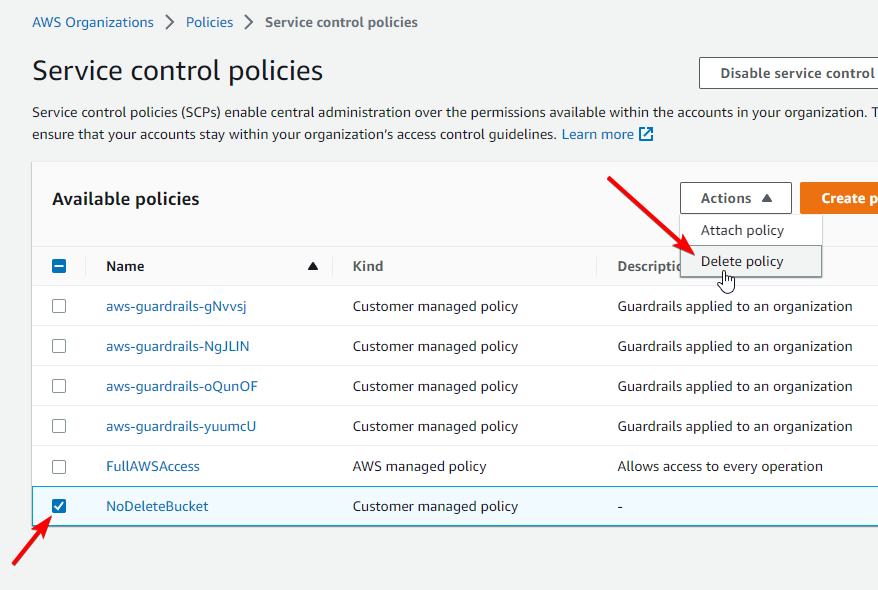
Go to Policies then Service control policies
Select the “NoDeleteBucket” policy, and click Actions then Delete policy
Enter the policy name in the confirmation box and click Delete
Account: Sub-account
Login to your sub-account, as the original user you used, to create the sub-account user.
Head to the IAM console: https://us-east-1.console.aws.amazon.com/
Go to Users, select the sub-account user you have been testing with, and click Delete
Enter their username in the confirmation box, and click Delete
Head to the S3 console: https://s3.console.aws.amazon.com/s3/buckets
Select the bucket you created earlier, and click Delete
Enter the bucket name in the confirmation window and click Delete bucket