ArgoCD embeds and bundles Dex as part of its installation, for the
purpose of delegating authentication to an external identity provider. Multiple types of identity
providers are supported (OIDC, SAML, LDAP, GitHub, etc...). SSO configuration of ArgoCD requires
editing the argocd-cm ConfigMap with
Dex connector settings.
This document describes how to configure ArgoCD SSO using GitHub (OAuth2) as an example, but the steps should be similar for other identity providers.
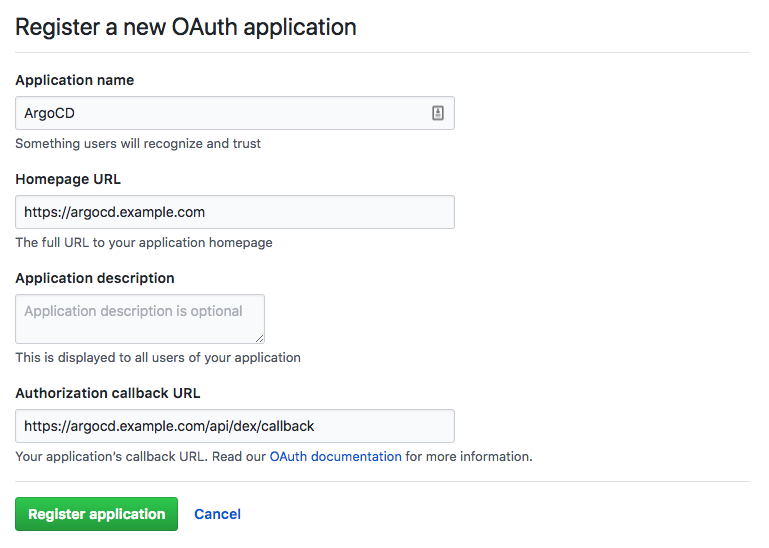
In GitHub, register a new application. The callback address should be the /api/dex/callback
endpoint of your ArgoCD URL (e.g. https://argocd.example.com/api/dex/callback).
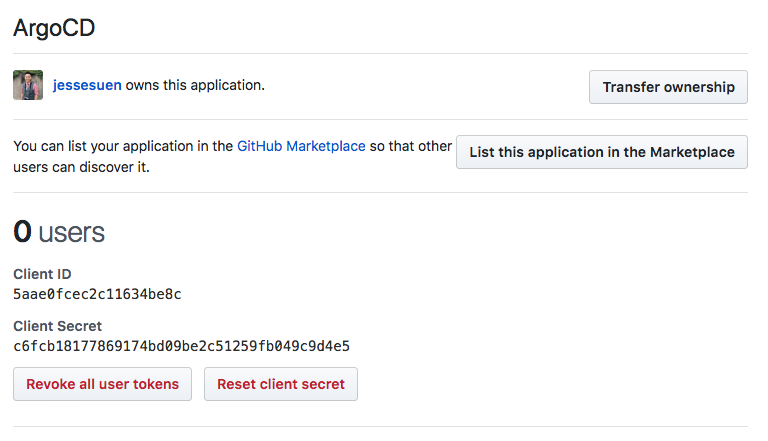
After registering the app, you will receive an OAuth2 client ID and secret. These values will be inputted into the ArgoCD configmap.
Edit the argocd-cm configmap:
kubectl edit configmap argocd-cm
- In the
urlkey, input the base URL of ArgoCD. In this example, it is https://argocd.example.com - In the
dex.configkey, add thegithubconnector to theconnectorssub field. See Dex's GitHub connector documentation for explanation of the fields. A minimal config should populate the clientID, clientSecret generated in Step 1. - You will very likely want to restrict logins to one or more GitHub organization. In the
connectors.config.orgslist, add one or more GitHub organizations. Any member of the org will then be able to login to ArgoCD to perform management tasks.
data:
url: https://argocd.example.com
dex.config: |
connectors:
# GitHub example
- type: github
id: github
name: GitHub
config:
clientID: aabbccddeeff00112233
clientSecret: $dex.github.clientSecret
orgs:
- name: your-github-org
# GitHub enterprise example
- type: github
id: acme-github
name: Acme GitHub
config:
hostName: github.acme.com
clientID: abcdefghijklmnopqrst
clientSecret: $dex.acme.clientSecret
orgs:
- name: your-github-org
# OIDC example (e.g. Okta)
- type: oidc
id: okta
name: Okta
config:
issuer: https://dev-123456.oktapreview.com
clientID: aaaabbbbccccddddeee
clientSecret: $dex.okta.clientSecret
After saving, the changes should take affect automatically.
NOTES:
- Any values which start with '$' will look to a key in argocd-secret of the same name (minus the $),
to obtain the actual value. This allows you to store the
clientSecretas a kubernetes secret. - There is no need to set
redirectURIin theconnectors.configas shown in the dex documentation. ArgoCD will automatically use the correctredirectURIfor any OAuth2 connectors, to match the correct external callback URL (e.g. https://argocd.example.com/api/dex/callback)