Azure Active Directory B2C preview: Provide sign-up and sign-in to consumers with Microsoft accounts
[AZURE.INCLUDE active-directory-b2c-preview-note]
To use Microsoft account as an identity provider in Azure Active Directory (Azure AD) B2C, you need to create a Microsoft account application and supply it with the right parameters. You need a Microsoft account to do this. If you don’t have one, you can get it at https://www.live.com/.
-
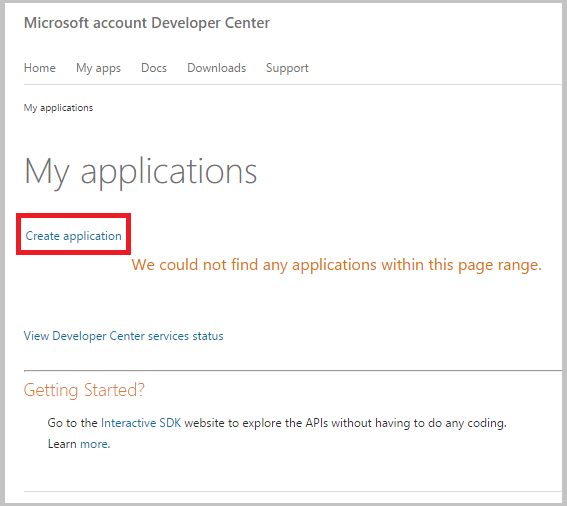
Go to the Microsoft account Developer Center and sign in with your Microsoft account credentials.
-
Click Create application.
-
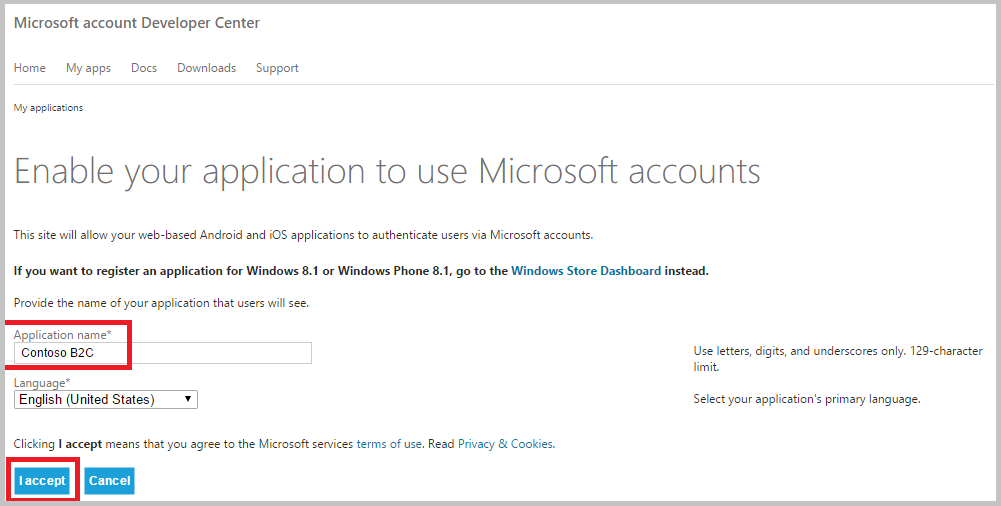
Provide an Application name and click I accept. This requires you to accept Microsoft services terms of use.
-
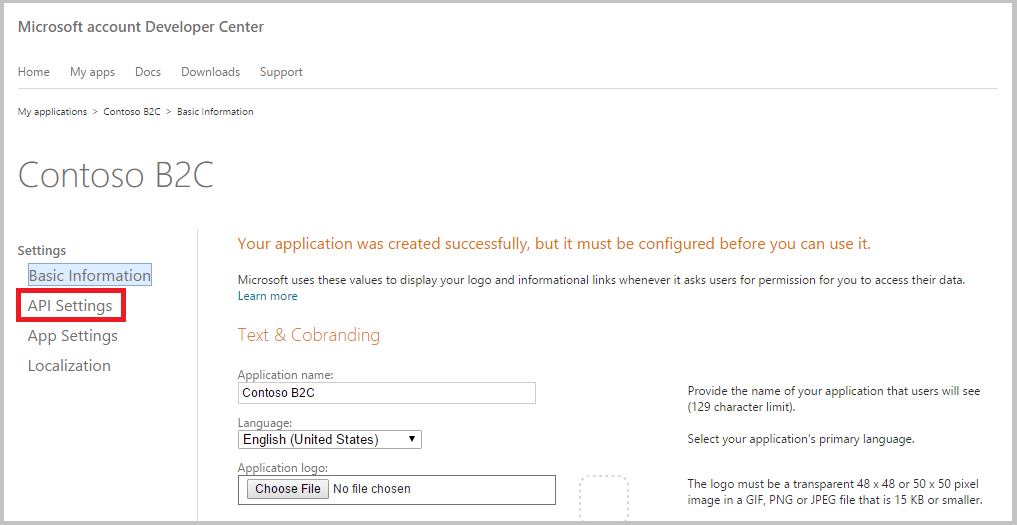
Click API Settings on the left navigation. Enter a valid Contact Email.
-
Enter
https://login.microsoftonline.com/te/{tenant}/oauth2/authrespin the Redirect URLs field. Replace {tenant} with your tenant's name (for example, contosob2c.onmicrosoft.com). Click Save at the bottom of the page. -
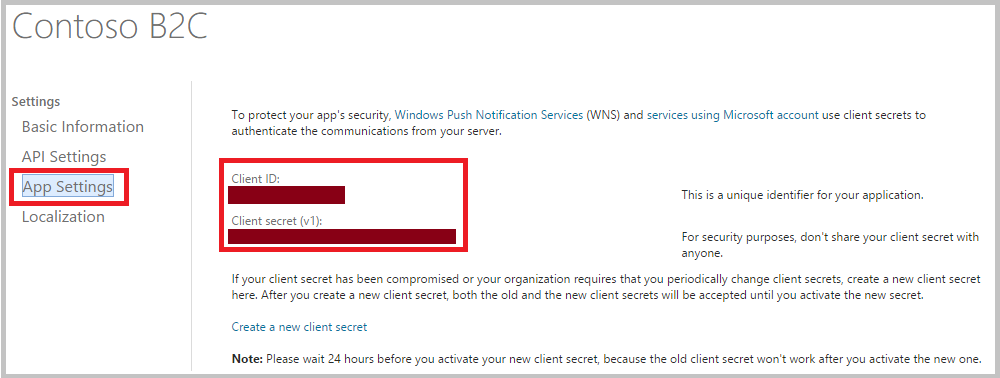
Click App Settings on the left navigation. Copy the values of Client ID and Client secret. You will need both of them to configure Microsoft account as an identity provider in your tenant. Client secret is an important security credential.
- Follow these steps to navigate to the B2C features blade on the Azure portal.
- On the B2C features blade, click Identity providers.
- Click +Add at the top of the blade.
- Provide a friendly Name for the identity provider configuration. For example, enter "MSA".
- Click Identity provider type, select Microsoft account, and click OK.
- Click Set up this identity provider and enter the client ID and client secret of the Microsoft account application that you created earlier.
- Click OK and then click Create to save your Microsoft account configuration.