The data we collect here includes subdomains, URLs, web servers, cloud assets, and a lot more data on public bug bounty programs. Our aim with this project is to:
- help bug bounty programs get up and running on new programs as quickly as possible.
- give security teams better visibility into their assets.
- reduce the load and noise that some programs face from automated tools (we run them once, give the results to everyone)
graph LR
title{Number of<br>Subdomains} --> subdomainsDate1[[On 1 February 2022]] --> subdomainsNum1{{12482}}
title --> subdomainsDate2[[Today]] --> subdomainsNum2{{32983219}}
graph TD
title{URL Status Codes} --> 10x[[10x]] --> Num10x{{0}}
title --> 20x[[20x]] --> status20xNum{{921283}}
title --> 30x[[30x]] --> status30xNum{{12123}}
title --> 40x[[20x]] --> status40xNum{{23131}}
title --> 50x[[50x]] --> status50xNum{{92139}}
graph LR
title{5 Most Used<br>Technologies} --> tech1{{Apache}}
title --> tech2{{Tomcat}}
title --> tech3{{Jenkins}}
title --> tech4{{Jira}}
title --> tech5{{Confluence}}
We have selected a few popular, public bug bounty programs as a start (open to suggestions!). A Trickest workflow picks up these targets, collects data on them, enritches it, cleans it up, and pushes it to this repository.
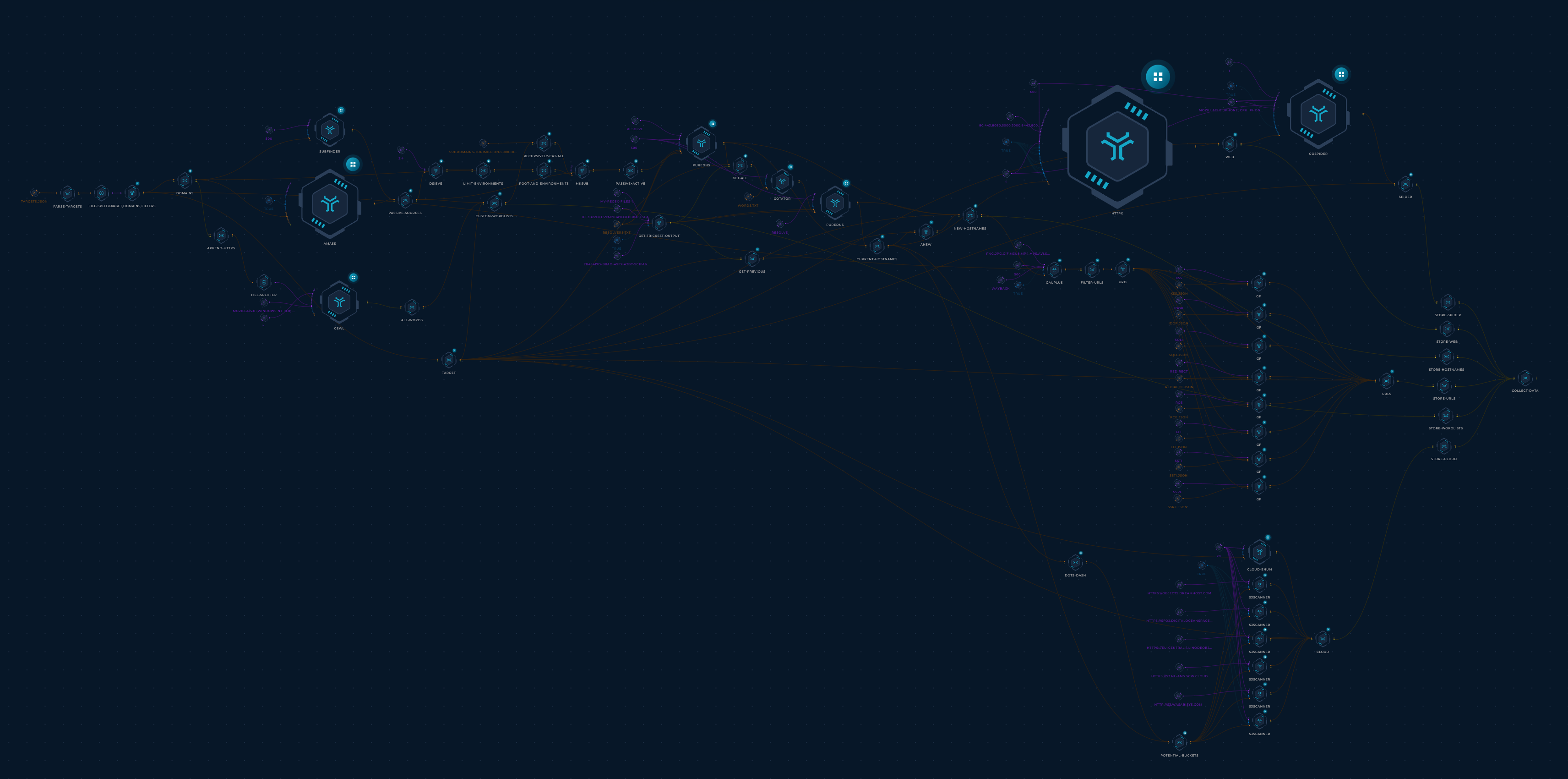
- Get the list of targets from targets.json
- For each target:
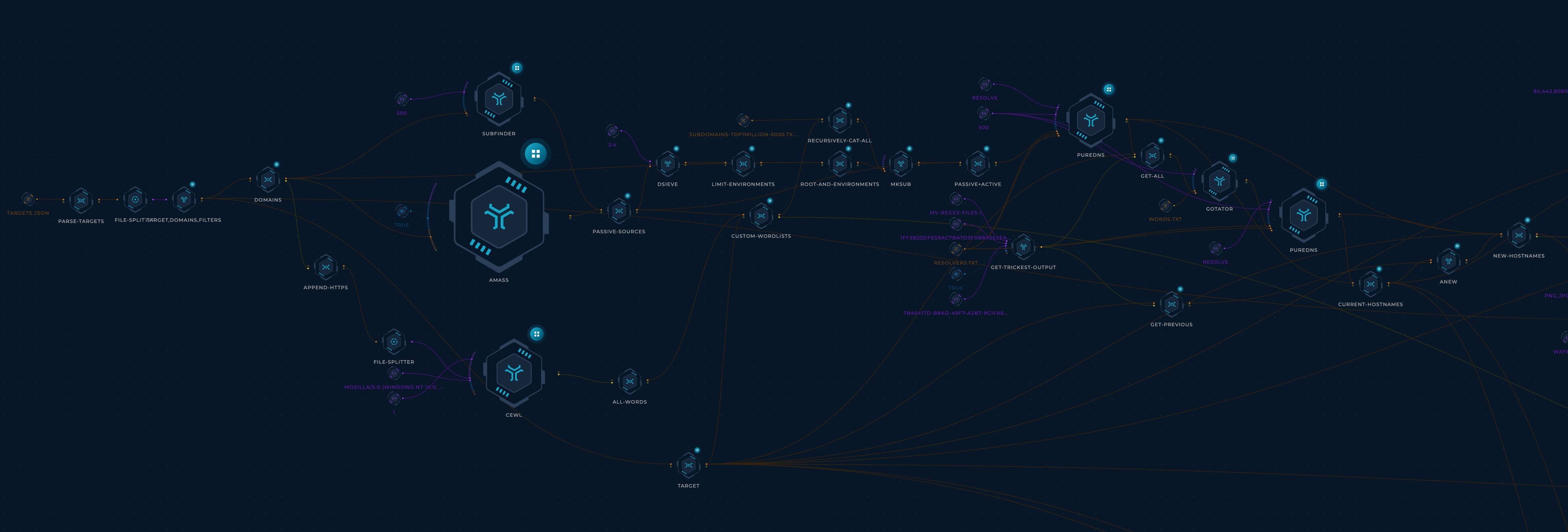
- Use subfinder, haktrails, and amass to collect subdomains from passive OSINT sources (Thanks ProjectDiscovery, hakluke, OWASP, and Jeff Foley!)
- Pass the fonud passive subdomains to dsieve to collect their
main environments(e.g. foo.admin.example.com -> admin.example.com; this will help generate more permutations later). - Use CeWL(https://github.com/digininja/CeWL) to crawl the main domain and generate a custom wordlist (Thanks digininja).
- Combine everything found so far into one
wordlist. - Use mksub to merge the
wordlistand themain environmentsand generate DNS names. - Resolve DNS names using puredns (Thanks d3mondev).
- Generate permutations using gotator (Thanks Josue87).
- Resolve permutated DNS names using puredns.
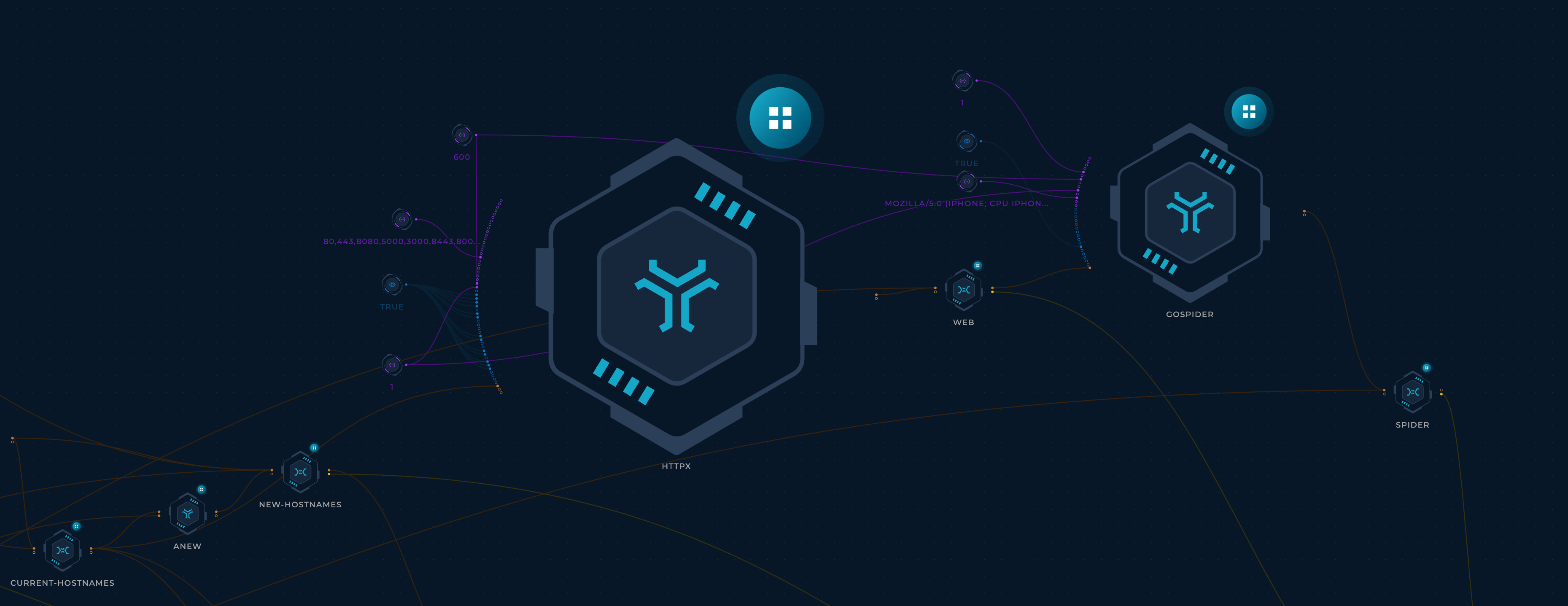
- For each target:
- Probe subdomains using httpx to find live web servers and collect their:
- HTTP titles
- Status codes
- Content lengths
- Content types
- Final redirect locations
- Webservers
- Technologies
- IP addresses
- CNAMEs
- Parse httpx's output and organize it into a few files for easier navigation.
- Crawl the found websites using gospider (Thanks jaeles-project)
- Probe subdomains using httpx to find live web servers and collect their:
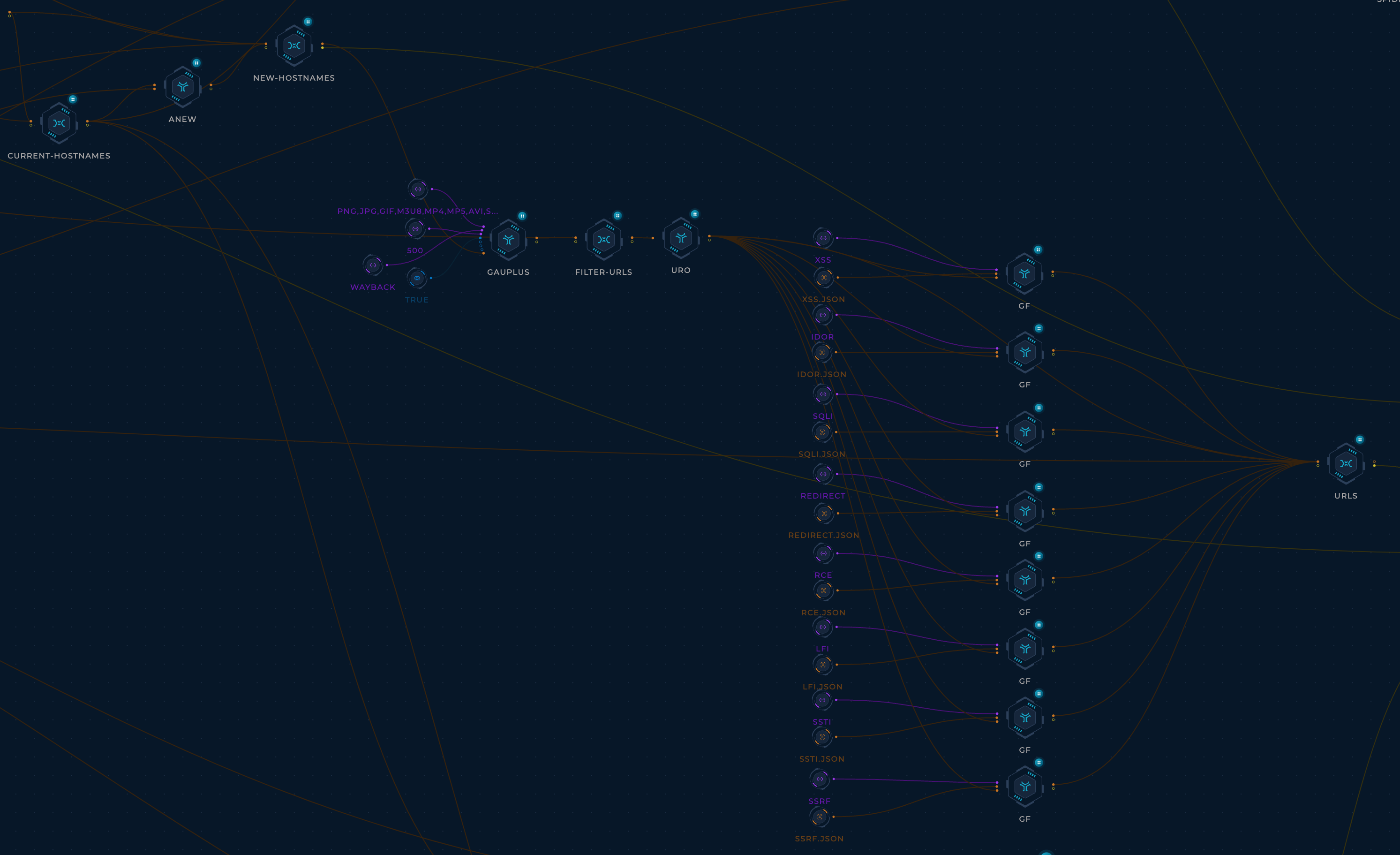
- For each target:
- Collect URLs using gauplus (Thanks bp0lr)
- Use gf and gf-patterns to cateogr
- Save each pattern's URLs to its own file for easier navigation.
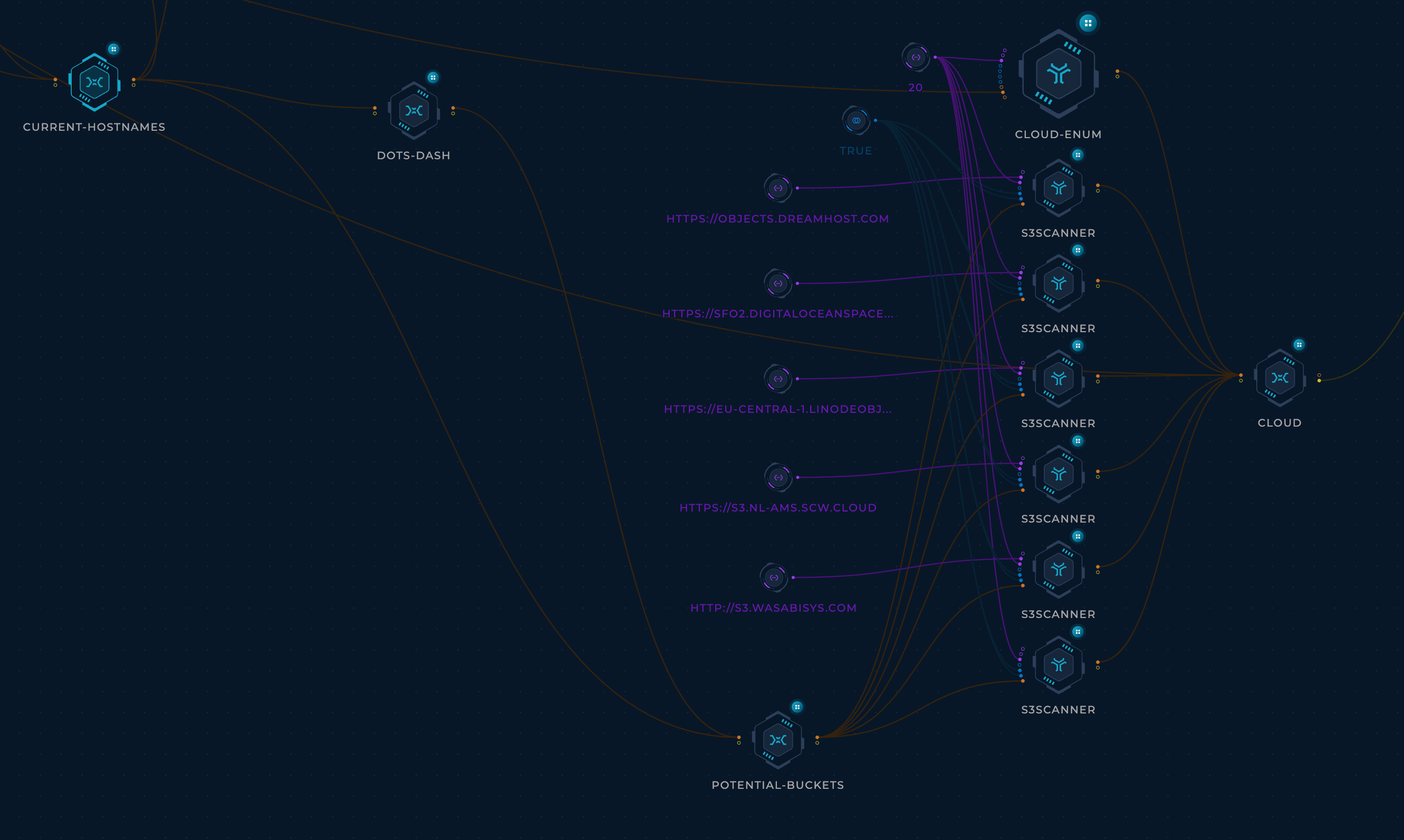
- For each target:
- Collect cloud resources using cloud_enum (Thanks initstring)
- Collected resources include
- AWS S3 buckets
- AWS apps
- Azure websites
- Azure databases
- Azure containers
- Auzre VMs
- GCP Firebase databases
- GCP App Enginee apps
- GCP Cloud Functions
- GCP Storage buckets
- Use S3Scanner to bruteforce S3-compatible buckets (using the subdomains collected in Hostnames to seed the wordlist)
- Collected buckets include:
- AWS S3 buckets
- DigitalOcean Spaces
- DreamHost buckets
- Linode buckets
- Scaleway buckets
- Wasabi buckets
- Save each type of resource to its own file for easier navigation.
In the end, we deduplicate and merge the results of this workflow execution with the previous executions and push them to this repository.
As described, almost everything in this repository is generated automatically. We carefully designed the workflows (and continue to develop them) to ensure the results are as accurate as possible.
You can use trickest-cli (public release soon!) to run this workflow on a custom target(s) using the following command
trickest execute Inventory --targets targets.json
All contribtutions/ideas/suggestions are welcome! If you want to add/edit a target/workflow, feel free to create a new ticket via GitHub issues, tweet at us @trick3st, or join the conversation on Discord.
We believe in the value of tinkering. Sign up for a demo on trickest.com to customize this workflow to your use case, get access to many more workflows, or build your own from scratch!