Penetration tests often require a lot of repeat work that can be easily automated. Multiple solutions for infrasture as code (IaC) exist such as Terraform and Ansible. By wrapping common options in a bash script I hope to add a bit of modularity for different deployment scenarios. All EC2 instances deployed are by default are Free Tier eligible to try and minimize costs. If you really want to limit the amount of cost you can run the C2 server locally.
Current state of deployment does not utilize mh.sh and relies on Terraform configurations. This is a temporary solution.
- Automatic AWS VPC Creation
- Automatic AWS Subnet Creation
- Automatic AWS Firewall Rule Creation
- Socat Redirectors
- Apache HTTP(S) Redirectors
- Automate LetsEncrypt Registration
- C2 Server Deployment
- Sliver
- CobaltStrike
- Wireguard Bastion (RedRoute)
- Ansible
- Terraform
- Python3
- AWS Account
apt install terraform
#installs hashicorp/aws provider to manage EC2 instances
terraform init
apt install ansible
Ansible requires Python3 to run so if you don't have that installed I believe it will pull it down for you.
git clone https://github.com/arokota/magichats
cd magichats
vi terraform.tfvars
Edit terraform.tfvars and fill in your AWS credentials and SSH keys
Current implementation requires instances.tf to be edited to manually instruct what nodes you would like to deploy. To only deploy a single type of listener or exclude deploying a C2 server in the cloud then you simply need to comment that out. (Also requires editing the output.tf file since it complains)
(Default redirects port 80,443 -- very easy to change to 53 for dns shells :))
- Create an AWS account and add a default SSH key for instances to be created with
- Download Magichats and install using the instructions above
- Edit
instances.tfandoutput.tfand comment out Apache-Redirectors- Edit
/ansible/setup-sliver.ymlif you would like to have a different operator name than the default
- Edit
- Run
terraform applyto deploy.- Enter how many redirectors you want
- Take note of
c2_ipsince you will need to reverse SSH port 31337 (default Sliver) to access
- Ansible will dump
<your-operator-name>_localhost.cfgto the project directory which will be your Sliver access profile. Use this to connect
(Default redirects port 80,443)
By default Apache will use self-signed certificates. Current implementation does not automate letsencrypt but you can easily subsitute that if you would like. Personally I prefer to put my DNS behind CloudFlare and use one of their certificates, letting my backend run raw HTTP through the Amazon VPC.
- Create an AWS account and add a default SSH key for instances to be created with
- Download Magichats and install using the instructions above
- Edit
instances.tfandoutput.tfand comment out Socat-Redirectors - Edit
ansible/setup-apache.ymland fill Apache Rewrite rules you would like. - Run
terraform applyto deploy. Take note ofc2_ipsince you will need to reverse SSH port 31337 (default Sliver) to access- Enter how many redirectors you want
- Take note of
c2_ipsince you will need to reverse SSH port 31337 (default Sliver) to access
- Ansible will dump
changeme_localhost.cfgto the project directory which will be your Sliver access profile. Use this to connect
Just don't edit anything out and start from step 5.
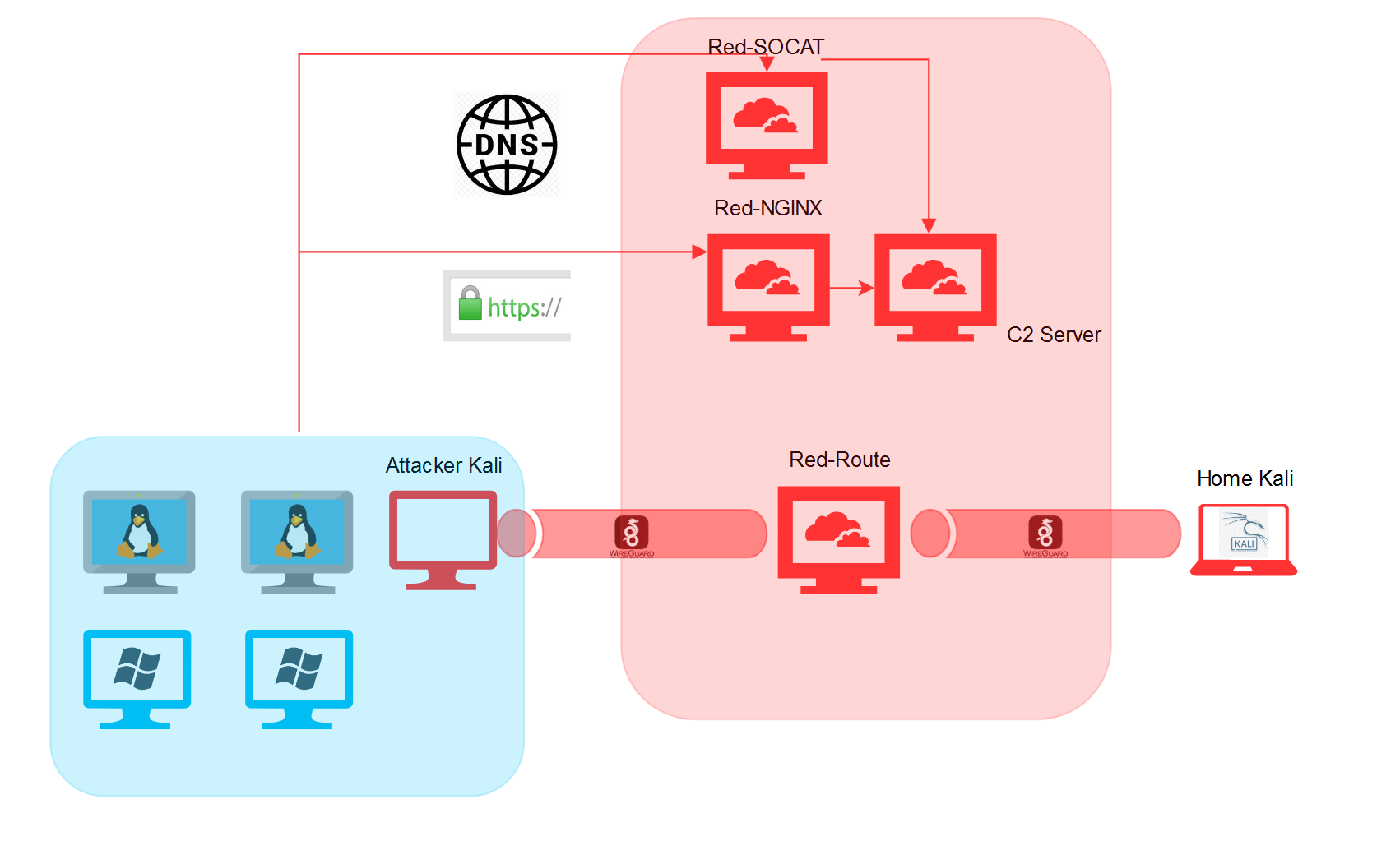 Diagram is a little out of date...will have to update that in the future but you get the idea.
Diagram is a little out of date...will have to update that in the future but you get the idea.
- Modify primary workflow to work as follows:
- Run
mh.shand answer prompts for what you want to deploy - Answers written to variables in a .tfvars file and Jinja2 templates for ansible
- Terraform launched with the `--var-file="variables.tfvars" file
- Profit
- Run
A lot of these folk wrote really great blog posts that I definitely totally did not lift a couple of snippets here and there from (or whole files in some case). Overall I think it's a great excercise to build this out yourself rather than just using someone elses deployment scripts. Shakes fisk at Ansible
- https://rastamouse.me/infrastructure-as-code-terraform-ansible/
- https://anubissec.github.io/Using-Ansible-and-Terraform-to-Build-Red-Team-Infrastructure/
- https://www.ired.team/offensive-security/red-team-infrastructure/automating-red-team-infrastructure-with-terraform
- https://github.com/tevora-threat/rt_redirectors
- Image Credit: https://www.deviantart.com/d4nt3wontdie/art/Magical-Hats-Magic-Artwork-760500482
