Deal with bad characters easily during exploit writing with badchars.
↑Instalation
using pip:
pip3 install badbyte or from repo:
git clone [email protected]:C3l1n/badbyte.git
cd badbyte
pip3 install .↑Usage
You can always use:
badbyte --help↑Cyclic pattern generate
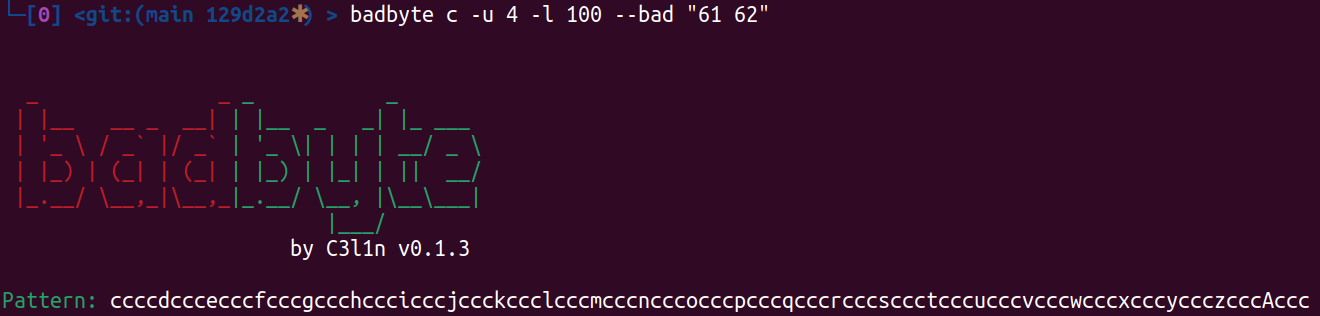
It is useful to search for offset at which you should put your sniper shot constants. For example return address: you generate pattern with this function, trigger vulnerability with generated payload. EIP value (remember about little ending in x86) has uniq part of pattern and offset of that part could be calculated with badbyte parse (see next chapter).
badbyte c -u 4 -l 100 --bad "61 62"↑Search for offset in cyclic pattern
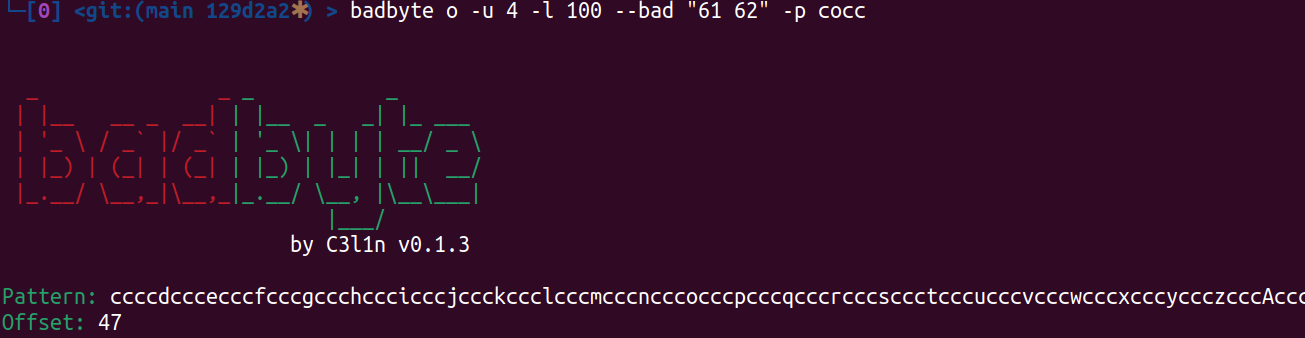
Search for offset of provided part in --pattern argument.
badbyte o -u 4 -l 100 --bad "61 62" -p cocc
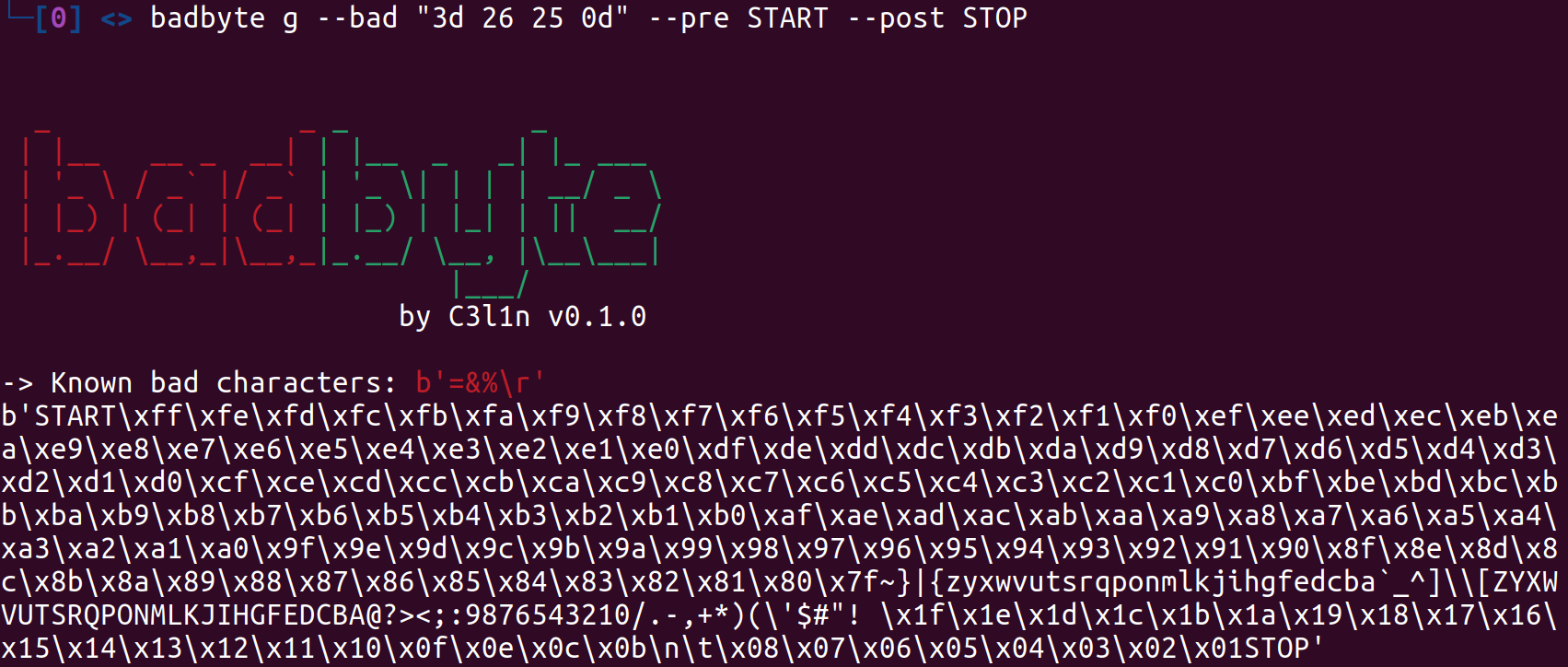
↑Generate payload to check all characters
badbyte g --bad "3d 26 25 0d" --pre START --post STOPuse:
- --bad to supply hexascii values of bad characters
- --pre to set string for marking start point (or leave default)
- --post to set string for marking stop point (or leave default)
Then use payload in your exploit and fire it.
↑Analyze memory dumped after trigger
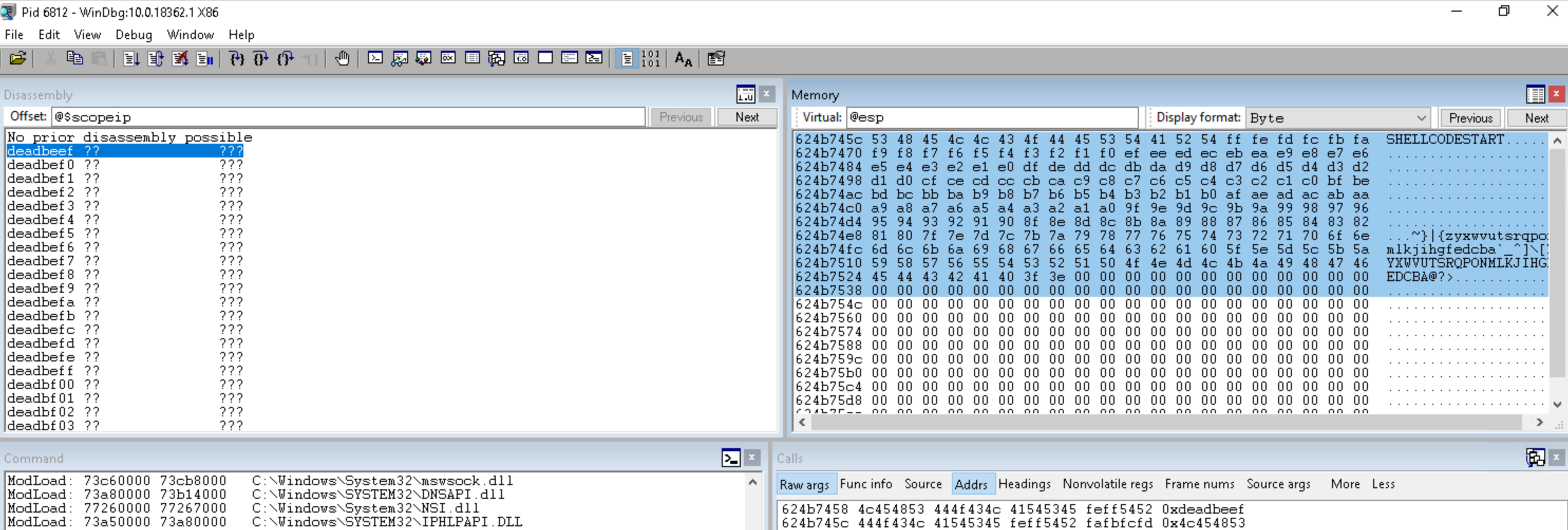
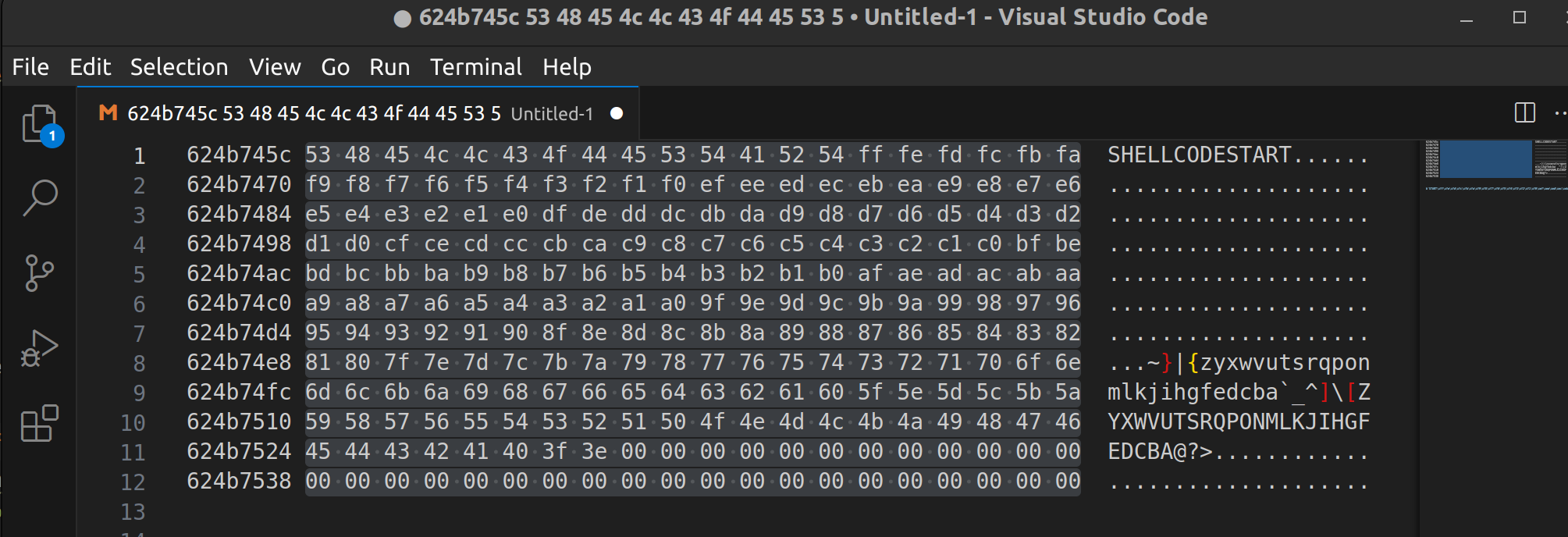
Copy hexascii from memory dump of your favourite debugger i.e. windbg:
remember to skip addresses and ascii representation. I use vim and column select or visual studio code and alt+shift select.
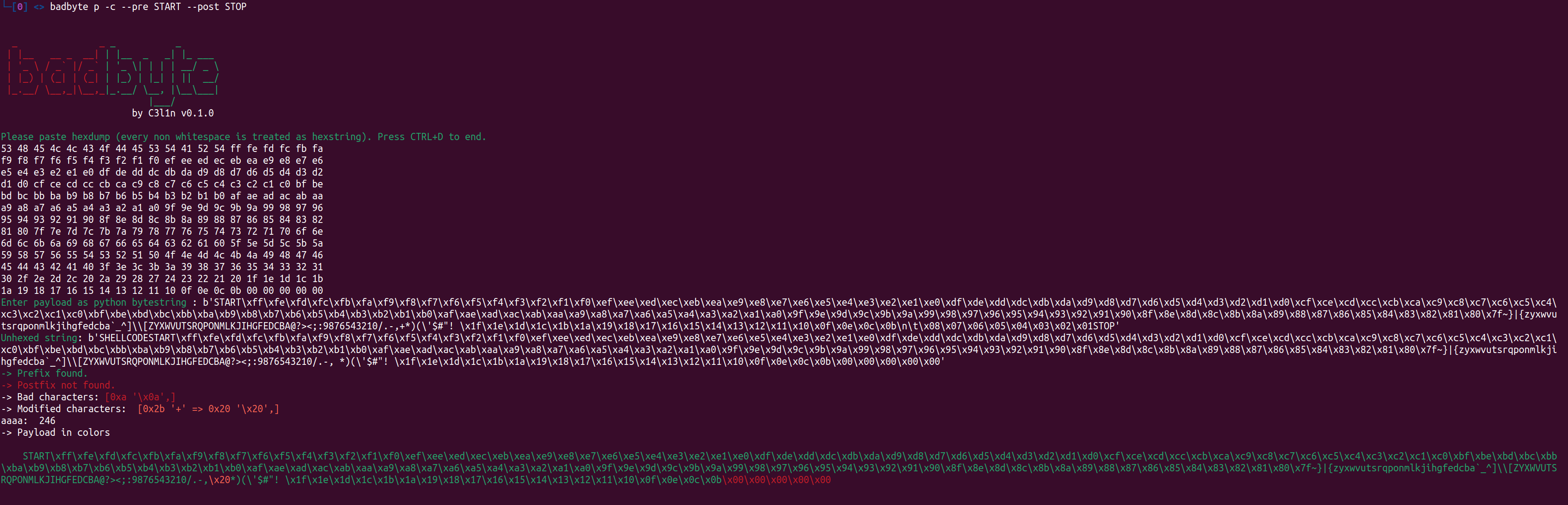
Fire badbyte to analyze output:
badbyte p -c --pre START --post STOP↑Programatically use
Documentation not made (feel free to read code) but you can find in example/programatically_generate_payload.py example of payload generation in exploit.