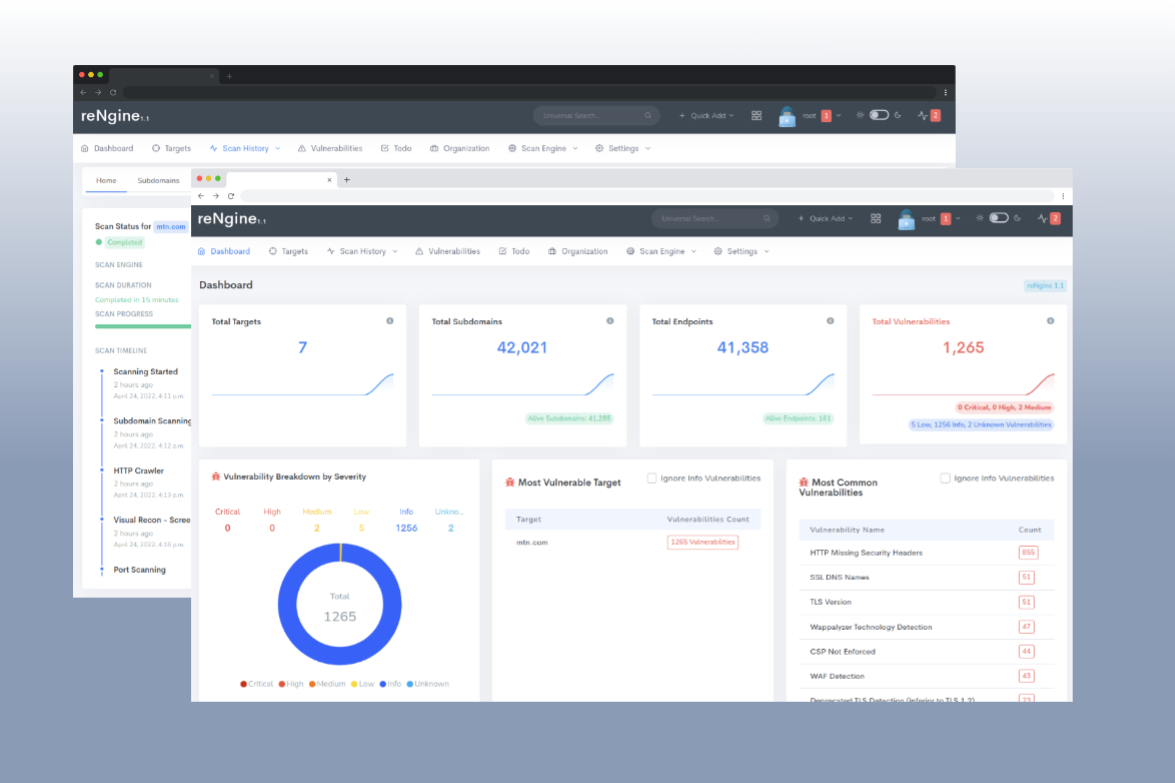
Quickly discover the attack surface, and identify vulnerabilities using highly customizable and powerful scan engines. Enjoy peace of mind with reNgine's continuous monitoring, deeper reconnaissance, and open-source powered Vulnerability Scanner.
reNgine is a web application reconnaissance suite with focus on a highly configurable streamlined recon process via Engines, recon data correlation, continuous monitoring, recon data backed by a database, and a simple yet intuitive User Interface. With features such as sub-scan, deeper co-relation, report generation, etc. reNgine aims to fix the gap in the traditional recon tools and probably a better alternative for existing commercial tools.
reNgine makes it easy for penetration testers and security auditors to gather reconnaissance data with bare minimal configuration.
⭐reNgine Documentation · What's new · Contribute · Report Bug · Request Feature⭐
- About reNgine
- Features
- Documentation
- Quick Installation
- What's new in reNgine
- reNgine Bug Bounty Program
- Screenshots
- Contributing
- reNgine Support
- Related Projects
- Support and Sponsoring
- License
I am currently working on reNgine 2.0 likely to be announced sometimes between May to August 2023. This version will be codenamed for Jasper. reNgine 2.0 will be the most advanced reNgine ever, a tons of work will be done in how scans are performed, things such as Pause and Resume Scan, Axiom Integration, more deeper coorelation, Project Options, Multiple Tenants, etc.
Please submit your feature requests via github issues or you can use this form as well.
You can watch reNgine 1.1 release trailer here. (Recommended)
reNgine is a web application reconnaissance suite with a focus on a highly configurable streamlined recon process. reNgine is backed by a database, with data correlation and organization, the custom query “like” language for recon data filtering, reNgine aims to address the shortcomings of traditional recon workflow.
Developers behind the reNgine understand that recon data can be huge, and manually looking up for entries to attack could be cumbersome, with features like identifying Interesting Subdomains, helping penetration testers focus on attack rather than recon.
reNgine is also focused on continuous monitoring. Penetration testers can choose to schedule the scan at periodic intervals and get notified on notification channels like Discord, Slack, and Telegram for any new subdomains or vulnerabilities identified, or any recon data changes.
Interoperability is something every recon tool needs, and reNgine is no different. Beginning reNgine 1.0, we additionally developed features such as import and export subdomains, endpoints, GF pattern matched endpoints, etc. This will allow you to use your favorite recon workflow in conjunction with reNgine.
PDF reports are something every individual or a team needs. Beginning reNgine 1.1, reNgine also comes with an option to download PDF reports. One can also choose the type of report, Full Scan Report or just a reconnaissance report. Also, we understand that PDF reports need to be customizable. Choose the color of the report you like, customize the executive summary, etc. You choose the way your pdf report looks!
reNgine features Highly configurable scan engines based on YAML, that allows penetration testers to create as many recon engines as they want of their choice, configure as they wish, and use them against any targets for the scan. These engines allow penetration testers to use tools of their choice, the configuration of their choice. Out of the box, reNgine comes with several scan engines like Full Scan, Passive Scan, Screenshot gathering, OSINT Engine, etc.
Our focus has always been on finding the right recon data with very minimal effort. After having several discussions with fellow hackers/pentesters, a screenshots gallery was a must, reNgine also comes with a screenshot gallery, and what's more exciting than having a screenshot gallery with filters, filter screenshots with HTTP status, technology, ports, and services.
We also want our fellow hackers to stay ahead of the game, reNgine also comes with automatic vulnerability reporting (ATM only Hackerone is supported, other platforms may come soon). This allows hackers to define their vulnerability report template and reNgine will do the rest of the job to report vulnerability as soon as it is identified.
- Reconnaissance: Subdomain Discovery, IP and Open Ports Identification, Endpoints Discovery, Directory and Files fuzzing, - Screenshot gathering, Vulnerability scan using Nuclei, WHOIS Identification, WAF Detection etc.
- Highly configurable YAML based Scan Engines
- Support for Parallel Scans and Subscans
- Automatically report Vulnerabilities to Hackerone
- Recon Data visualization
- OSINT Capabilities (Meta info Gathering, Employees Gathering, Email Address with an option to look password in the leaked database, - dorks, etc)
- Customizable Alerts/Notification on Slack, Discord, and Telegram
- Perform Advanced Query lookup using natural language alike and, or, not operations
- Recon Notes and Todos
- Clocked Scans (Run reconnaissance exactly at X Hours and Y minutes) and Periodic Scans (Runs reconnaissance every X minutes/- hours/days/week)
- Proxy Support
- Screenshot Gallery with Filters
- Powerful recon data filtering with autosuggestions
- Recon Data changes, finds new/removed subdomains/endpoints
- Tag targets into the Organization
- Identify Interesting Subdomains
- Custom GF patterns and custom Nuclei Templates
- Edit tool-related configuration files (Nuclei, Subfinder, Naabu, amass)
- Add external tools from Github/Go
- Interoperable with other tools, Import/Export Subdomains/Endpoints
- Import Targets via IP and/or CIDRs
- Report Generation
- Toolbox: Comes bundled with most commonly used tools such as whois lookup, CMS detector, CVE lookup, etc.
- Identification of related domains and related TLDs for targets
- Find actionable insights such as Most Common Vulnerability, Most Common CVE ID, Most Vulnerable Target/Subdomain, etc.
You can find reNgine documentation on https://rengine.wiki
(Only Ubuntu/VPS)
- Clone this repo
git clone https://github.com/yogeshojha/rengine && cd rengine
- Edit the dotenv file, please make sure to change the password for postgresql POSTGRES_PASSWORD !
nano .env
- Run the installation script, Please keep an eye for any prompt, you will also be asked for username and password for reNgine.
sudo ./install.sh
if ./install.sh does not have install permission, please change it, chmod +x install.sh
reNgine can now be accessed from https://127.0.0.1 or if you're on the VPS https://your_vps_ip_address
A detailed installation guide can also be found here. Thanks to Rubén!
Installation instructions can be found at https://reNgine.wiki/install/detailed/
Please find the latest release notes and changelog here.
Security Researchers welcome onboard! I am excited to announce the bug bounty program for reNgine in collaboration with huntr.dev, this means you'll be rewarded for any security vulnerabilities discovered in reNgine.
Thank you for your interest in reporting vulnerabilities to reNgine! If you are aware of potential security vulnerabilities within reNgine, we encourage you to report immediately via huntr.dev
Please do not disclose any vulnerabilities via Github Issues/Blogs/Tweets after/before reporting on huntr.dev as it is explicitly against huntr.dev and reNgine disclosure policy and will not be eligible for monetary rewards.
Please note that the maintainer of reNgine does not determine the bounty amount. The bounty reward is determined by an industry-first equation from huntr.dev to understand the popularity, impact, and value of repositories to the open-source community.
What do I expect from security researchers?
- Patience: Please note that currently I am the only maintainer in reNgine and will take some time to validate your report. I request your patience throughout the process.
- Respect Privacy and Security Reports: Please do not disclose any vulnerabilities in public (this also includes GitHub issues) before or after reporting on huntr.dev! That is against the disclosure policy and will not be eligible for monetary rewards.
- Respect the rules
What do you get in return?
- Much thanks from Maintainer
- Monetary Rewards
- CVE ID(s)
Please find the FAQ and Responsible disclosure policy from huntr.dev.
Scan Results
General Usage
Initiating Subscan
Recon Data filtering
Report Generation
Toolbox
Adding Custom tool in Tools Arsenal
Contributions are what make the open-source community such an amazing place to learn, inspire, and create. Any contributions you make are greatly appreciated. Your contributions could be as simple as fixing the indentations or fixing UI to as complex as bringing new modules and features.
See contributing guide to get started.
You can also join our discord channel #development for any development related queries.
Please note that reNgine is beginner-friendly. If you have never done any open-source yet, we encourage you to do so. We will be happy and proud of your first PR ever.
You can begin with resolving any open issues.
Please do not raise any github issues for support requests. Instead, join our discord channel #support
There are many other great reconnaissance frameworks, you may use reNgine in conjunction with these tools. But, they themselves are great, and may sometimes even produce better results than reNgine.
Over the last few years, I have been working hard on reNgine to bring new features with the only goal to make this a De-facto standard for reconnaissance. Most of my out-of-office hours and weekends are spent working on reNgine. I do this in addition to my primary job. I am happy to have received such overwhelming support from the community. But to keep this project alive, I am seeking financial support.
| Paypal | Bitcoin | Ethereum |
|---|---|---|
| https://www.paypal.com/paypalme/yogeshojha11 | 35AiKyNswNZ4TZUSdriHopSCjNMPi63BCX |
0xe7A337Da6ff98A28513C26A7Fec8C9b42A63d346 |
OR
- Add a GitHub Star to the project.
- Tweet about this project, or maybe blogs?
- Maybe nominate me for github stars?
- Join DigitalOcean using my referral link your profit is $100 and I get $25 DO credit. This will help me test reNgine on VPS before I release any major features.
It takes a considerable amount of time to add new features and make sure everything is working. A donation is your way of saying: reNgine is awesome
Any support is greatly appreciated! Thank you!
Distributed under the GNU GPL v3 License. See LICENSE for more information.