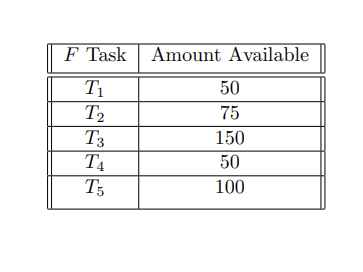
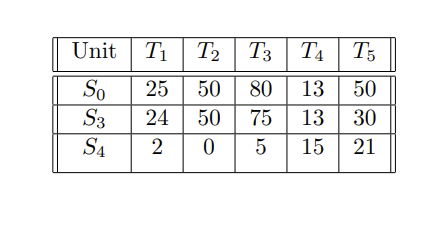
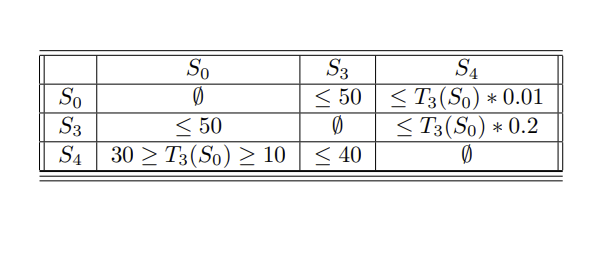
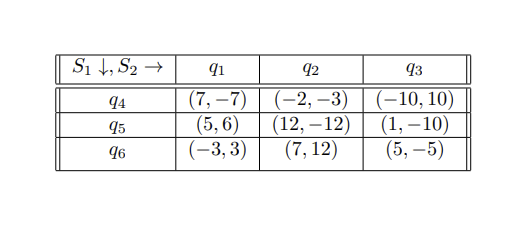
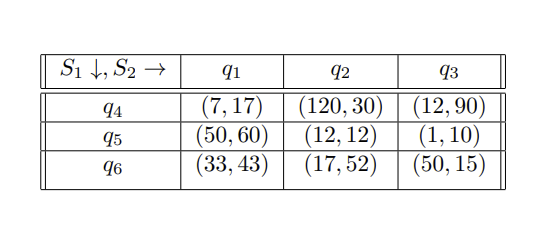
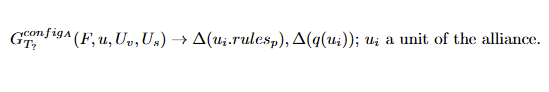In mercantilism, that "father figure" you have that told you "it is not about the money, it is about the principle" might just rape you dead and take all of your belongings...
- Nu Merchant Principal, by Richard Pham
- Copyright 2024 Richard Pham
- Table of Contents
- Autonomy and Games
- Situational Engineering
- Security's Price of Choice-Communication
- Maintenance as Half-Measures of the Potential
- Wasting the Drive in Gridlock
- How Obtuse Judgments Can Count
- To Be Revered by What
- Curse by Pre-emptive Doxing
- A Simple Template For Expectations of Cost
- The Effectiveness of Imagined Fallibilities
- Shifty and Shifting Alliances
- Denying Sophistication
- The Sophisticated as Behavior After Appearance
- Shifty and Shifting Alliances Pt. II
- The Great-Wind's Restriction
- The Idiom and the Idiot
- Half-Efforts, Full Takes
- Arguments in Image-Projectable Contexts
- Proprietary Calculations
- The Audience Is the Vulture
- About the Simplicity of the Cycle
- Shifty and Shifting Alliances Pt. III
- Pride Plays Perception
- Pride Plays Perception Pt. II
- About the Simplicity of the Cycle Pt. II
- Pride Plays Perception Pt. III
- About the Simplicity of the Cycle Pt. III
- So That Is Accounting
- End Note
Business comes and goes, much more frequently than governments. So how can commerce thrive without the dread of disillusionment that stems from the lackluster payoff in zero-sum dynamics? Zero-sum dynamics carry an extremely bipolar nature in the psychology of actors. And there are few paradigms of thought outside of this zero-sum strategic convention in politics, business, and war. Well, to clarify, there are few paradigms of thought, outside of zero-sum, that have gained enough mainstream adoption for the concepts to be taught in typical higher education settings. Brilliance does not quite make the mark in intensely competitive settings. But there are some that argue that it is the misuse of brilliance, trained and primed towards "malfeasant" outlets, that results in clear defeats for the owner/s of that brilliance. But there have been and are plenty of brilliant people that did not quite train and prime themselves towards "malfeasant" outlets. And they get paid in dirt. The dumb and perhaps retarded scoff at their ideas, deny their promotion, and ruin their composure. This is how some brilliant people get treated like dirt. They get invited to a club or party of some high-society members, after achieving much and expecting some festive recognition, and the invites are rescinded. And the club/party mentions them as if they are some dull one fit for exploitation. The high-society members already know, due to the luxury and power that they are able to retain, that preventative measures against exploitation require more than just brilliance. Brilliance is materially less in value than dirt. The brilliant person wants to get somewhere, with rejection thrown in their face as well as insults and knives in their back, their so-called "defensive posturing" against exploitation is most definitely borne from a source, or at least an effect, of malice.
Do you really think that fat cow that is your neighbor really gives a care for your interests and well-being? Laissez-faire feudalism predicts that they do not. While you might be digging trenches for "modern-day Rome", that fat cow, the one that has never been hurt in any way except for their feelings, looks at you like you are some kind of slave. The fat cow is stupid. It is stupid not because it is simple-minded. It is stupid for judging while sitting comfortably in its welfare zone, sponsored by the government in the name of ... what? Merit? Justice? That fat cow, ultimately in the context of economic sacrifice, may as well be a wolf. It may as well be a wolf because it would prefer that you are eaten instead of it.
Suppose there is some kind of wisdom in ultra-competitive environments, borne out of Laissez-faire, that goes something similar as "one should make as much effort in befriending another as the effort required to defend against an enemy." This is an "ideal" that is much easier to declare and believe in than to successfully accomplish. The difficulty of accomplishing this "ideal" rests upon the nature that surrounds the center, for there is no mechanical principle behind it that ensures the equal probability of easiness in befriending and enemizing. Who is to state, with a guarantee that rests completely on confidence instead of fear, that not every person becomes an enemy in the eyes of a "neo-mercantilist" (for lack of a better term)?
The notion of the fat cow as a wolf in the context of economic sacrifice is a strong assumption on costs from loss due to some underlying fatalism. Rest assured that there are many in academia and government that strongly disagree with the concept of competition, or at least self-improvement, as zero-sum. These contrarian views harness the game theory specification of "non-zero sum games". The rationale is that some aspects, which can be quantified, rest on a sort of cooperation, a mutual assurance, a compromise. There is much opinion and exemplification on non-zero sum games. These so-called "games" do exist in reality, but were only formalized into theoretical frameworks, for re-teaching, sometime in the last two centuries. By the standard of non-zero sum games, the fat cow does not have to be a wolf then!
The mechanics of "costs", including but not limited to quantitative finance, are derived from the cultural mores and collective ambition, and also the mainstream economic concept of the correlation between scarcity and the magnitude of "cost", but the "faith" in these numbers does not rest on a uniform consensus of agreement. For instance, a sentimental person would probably prefer to sell something else other than the memorabilia that they've acquired through their years. There is the belief in the pricelessness of some material objects. Collectively, these same material objects could very well be circulated by the masses, according to some arbitrarily-set standard of valuation, if they are to land in their hands. There are psychological and collectivist elements in non-zero sum games. Suppose that two agents are participants in such a game. Given the perceived costs in this game's cost table, the two agents "cooperate" for outcomes that grant them both "positive" gains, by the table's objective numbers. But there is dissatisfaction underneath the compromise. Perhaps either one or both of the agents feel as though they deserve more of the "positive" gains. What factors would ensure that for the next "game" these two agents participate in, there would be no disagreement on the values of said game's cost table? On the matter of collectivist elements in non-zero sum games, suppose that two arbitrary agents are enthusiastic participants. Both of them are practically in sync, with regards to their decisions and the corresponding payoffs from those decisions. But regardless of what decisions they made, there is a "super-agent" above them. This "super-agent" is the singular representative of the collective outside of the game's two agents. According to the facts given to this super-agent, both of the agents lose in the non-zero sum game. The deceptively "positive" gains split between the two agents are in fact losses to them. Perhaps the gains could have been objectively greater if the agents were to participate in non-zero sum games without the overhead of the super-agent's authority. Perhaps the gains are not objectively positive gains for the two agents in the long term, given the super-agent's influence and capability of intervening between the two.
Cultural, psychological, and collectivistic factors were especially noted in non-zero sum games, even though their existence in zero-sum games is not negligible. It is obvious to state that zero-sum games, if based on accurate cost tables, result in "cleaner cuts". Every participant has very little motive to consider the outcome of well-being for their "competitors". Zero-sum games rest on the principles of physics. Value cannot grow, but it can be cleanly transferred from some original owner, a participant in the zero-sum game, to another. The argument that zero-sum games are more objectively-based than non-zero sum games is more persuasive than the argument for vice-versa.
There is an absolute chance for arguments that non-zero sum games are more amenable to participants. And the claim that the base of objectivity is an exclusive trait to zero-sum games is surely to be scrutinized. There is another claim that can be more fully agreed upon: for any prolonged sequence of decision-making events, the usage of both game categories serve unique demands. The payoffs to participants from non-zero sum games may amount to less for each, in comparison to the potential payoff (single participant gain) from zero-sum games. But over time, the partial payoffs from each non-zero sum game produce longer lasting and more stable benefits to the participants, by the metrics revolving around uniformity and the mean. Needless to say, these two categories of games can be expanded to involve more than two agents in the lens of mass organization. Organizations do not tend to encourage zero-sum games between its members, given the condition that both members are of pertinence, through utility, to the organization (but perhaps not of the same degree). The compromise from non-zero sum games suits the purpose of pacifying such biases, including jealousy and ambition, for integrity of the organization. However, in an organization's life, there occur instances where zero-sum games are utilized for the objective of slashing what is deemed to be excess or vice.
The first paragraph of this essay posits the domineering influence of zero-sum, over others, such as the alternative of non-zero sum, as a concept taught in the education setting. Many in university/government settings would probably not be vocal in support of this posit. Activities such as research&development, coordinated security, and journal publications do lean toward cost values of non-zero sum game. Knowledge, especially, is one of the fundamental possessions that does not operate on zero-sum dynamics on the one condition that the knowledge is fairly distributed. One of the ideals espoused in higher education is something along the lines of "a more informed society is a superior society". But the value of knowledge wildly oscillates from trivia to critical vulnerabilities belonging to persons, organizations, nation-states, etc. What is a non-zero sum game to a select group of participants may be reflected onto another group as a zero-sum game's outcome that adversely affects them.
With regards to application of the concepts zero or non-zero sum, the first is predominantly used in contexts such as material transfers and clear-cut win/lose outcomes. Due to the cooperative nature of non-zero sum games, even with the specification that the participants do not know ahead of time what their counterparts' decisions are, there is a tendency for at least one of the participants to lose sight of the definition behind the outcome values. The coupling (two participants) and entanglement (more than two participants) fuzz decision-making in such a way for there to be virtually no optimum payoff by the available options. Perhaps in some cases, contiguous non-zero sum games played by the participants may result for there to be a kind of "delegation" from at least one of the players to the remainder. The preferences of the remainder become prioritized over the delegators, who would rather play and follow along than to emphasize their own ideal choices in the "game".
Autonomy is a multi-faceted question in arrangements that are games. Why would an agent participate in some arrangement called a game if there is the certainty that the best outcome, in the form of payoffs from the true cost table, cannot result in their betterment? The agent diverges from their original circumstances that would have granted them opportunities to pursue some desired sequence of outcomes, each a checkpoint of success or at least, gratification. Then they are enmeshed in circumstances that require their actions to be geared towards some objective directly related to the specific temporal demands of those circumstances. They can mention the question of choice, a topic which is generally known to many members of societies that have had their hands forced into certain outlets (certainly by the mortal powers above them), but they will only receive a response to accept the matter as another of idealism's lost visions.
Children engage in activities that can be termed as "games". These activities generally do no harm amongst themselves, and give them the benefit of developing their values and way of life to eventually play the roles of astute cogs in mature society. It is this premise that is a major moral justification for why some find themselves in circumstances, deemed games by some, that they otherwise would not engage in, either due to their ignorance that such circumstances (comprised of materials and events) exist or their involuntary stance towards those circumstances. The premise as one word is education. Is this word simply a transmission of terminology and procedures, as well as the auxiliary materials used to aid in understanding and experiencing this transmission of information? Could education really be as simple as two parallel straight paths, one the perfect transmission (by the educator) and the other the perfect practice or at least the most genuine effort in practice (by the educatee)?
Entertain the notion that there are two tenets in education. For matters of fact, education transmits absolute truth. And for other matters, education transmits perfect knowledge of the methodology. This notion relies on the condition that there is nothing to be educated on past the minds of the educators. The educators were selected due to their mastery of the matters that they are to transmit and train their educatees on. So the educators could not possibly steer any of their subjects directly towards wrongful practices and fallacies.
On the idea of autonomy as the choice to participate in games that benefit and to not participate in anti-beneficial games, education as outlined by the previous paragraph is beneficial. But in games that are believed not to be beneficial, how can an agent truly know that they will sorely pay during or after their participation? Couple the particular outlining of education (in the previous paragraph) with active efforts to know the unknown (and all of the unknown's costs), from a perspective that supercedes even the educator. And the resultant is not education by the definition. Instead, it is experimentation and education. Education systems can enable their educatees to experiment, outside of constraints designed by the educator. There are certainly arguments available to defend these kinds of education systems, so that the educatees have greater awareness of what games will pay them off immensely, what other games are non-profit but greatly expands the experience (if experience cannot be quantified), and yet still the remaining games that will make them sorely pay beyond their recovery back to growth or at least, stasis.
The structuralization of any education system surely cannot accomodate the demands of the lifelong learner. This is to assume that any education system imposes binding demands on its participants. Without binding demands, the freedom of participants to come and go by their own volition somehow dilutes the seriousness and truthfulness of the informational material transmitted to them. In these circumstances, education becomes casual recreation, and recreation is personally experiential events; this is a Dionysian VS Apollonion argument. Even if one is not keen on learning any more past their depth, there is still the requirement of experience in sentient existence (if life goes on). And experience can be very stochastic, or even worse, engineered against those subject to the experience. The term "information-flow system" suffices as a superset of "education system". There are not required to be any binding demands from an educator that does not need to exist. The omnipresent requirement of processing information stands strong in this superset of an education system, even stronger than that of the education system since the lack of structured guidance is compensated by utter seriousness in certain contexts.
In many respects, the objective of education is to enhance and refine risk-averse mentalities and behaviors. For example, mistakes from history should not be repeated. Make careful calculations before embarking on dangerous trails. Take the tragic lessons from literature to heart. And so on. With experimentation, there is risk attached. Experimentation is interesting with regards to accountability. Educators generally steer clear from the losses from experimentation. The simple more is that they cannot risk their reputation to become entangled in what are perceived by third-party judges as fallibility traps. The fact that there are different natures and styles attached to those that experiment validates the anticipation that conceptualizations of fallibility, such as the Seven Deadly Sins, are to be mentioned by some in their aims to "reveal and penalize evil".
Autonomy is intricately connected to information-flow systems. Some important attributes of noteworthy mention are filtration processes, recognition mechanisms, flow control, network administration, and ultimately, capabilities past the knowledge that is perfect information.
The academic field of game theory has mass-proliferated some important findings in the context of decision-making. It has structured "games", decision-making junctions between two or more agents, into these classifications: strategic, extensive, and coalitional. It has also put focus on the nature of information available to agents during their activities called "games", that is, perfect and imperfect information. Rules for calculating the optimal decision are defined by the Nash equilibrium and its sibling concepts. In cases where there is no optimum by the decisions and costs granted to the agents, there is also the "ideal" (or expectation) of steady state, as illustrated by games such as Matching Pennies.
The mathematics applied in game theory is extensive enough to satisfy these two big questions:
- best decisions or expected states,
- expected payoffs (through probabilistic functions or best-decision rules).
But what about the situation? Given merely the cost tables (as formulated by game theory), some agents are predisposed to having some set of moves that may or may not intersect with the movesets of their co-participants. In other words, there is an unspoken asymmetry or equality in capabilities before the consideration of the game in focus. Acceptance of these conditions relies on the acceptance of the histories (for lack of a better term) of not only the agents belonging to the game in focus. There is also the need to understand the outside factors, some of which may be responsible for governing past events, agents, interpretations, and orders into the situation that contains the participating agents.
Consider this situation, called Game of Varying Coercion. There are only two players to make way for simplicity of illustration.
| t=1 | Play Along | Reveal |
|---|---|---|
| Silent Trigger | 10,1 | 10,-100 |
| Brute's Force | -1,0 | 5,-50 |
GVC1: Game of Varying Coercion @ timestamp 1; (2 x 2).
Agent A (row-wise) has the clear upper hand, in terms of cost as quantified by this table. Agent B is put into a servile position. Agent A would be wise to maintain preference for the dominated action of Silent Trigger. There is no possibility for Silent Trigger to inflict negative gains for Agent A. Whether Agent B chooses to obey Agent A by playing along, or revealing so as to catalyze revolt against Agent A, Agent A secures its upper hand by Silent Trigger. For Agent A to act by Brute's Force against an obedient Agent B speaks poorly for its welfare, as denoted by the negative gain of -1. If Brute's Force is used against Agent B in the case of its act of revealing, then there is a positive gain of half that for Silent Trigger. Suppose the revelation is judged to be fallacious, so much that Brute's Force is justified.
Silent Trigger requires more skill by the actor. It also requires more situational expenses so that the silence of the Trigger is not exposed to Agent B or third-party observers, who then have more knowledge and material to retaliate. The cost values of Table GVC1 denote the combative gains by the agents. However, there is another set of costs that are pertinent, by Table ST1.
| ~~ | Effective Cooperative | Ineffective Cooperative |
|---|---|---|
| Bull's Eye | -3,-12 | -1000,-50 |
| Missed Mark | -30,-100 | -1200,-1000 |
ST1: Costs to Resources by Silent Trigger; (2 x 2).
There are two possibilities for the actor behind Silent Trigger, labeled by the rows. The infrastructural costs, comprised of sentient agents, the environment, and the situation that is staged by these sentient agents, are the two columns: effective and ineffective cooperative. The cooperative is designated as an alignment with the Silent Trigger's actor. Note that there are no positive gains to resources. If the cooperative is ineffective, whether voluntarily or not, then it is critical for Silent Trigger's actor to move by Bull's Eye, in the name of costs to resources. If there is effective cooperative, the event of Missed Mark by Silent Trigger's actor results in less damage to resources. Table ST1 illustrates the heavy costs, even without the risk of failure by Silent Trigger's actor and their cooperative, of maintaining the dominated action of Silent Trigger over Brute's Force.
By Brute's Force, however, there is a risk that oppositional mass-organization from Agent B (in Table GVC1) ensues. The situation of the involved agents can escalate into something similar to that illustrated below.
| ~~ | Advance Opposition | Maintain Opposition | Withdraw Opposition |
|---|---|---|---|
| Escalate Brute's Force | 1000,500 | 250,250 | 2000,0 |
| Mix Brute's Force with Silent Trigger | 2000,-50 | 1000,500 | 2000,-300 |
| Silent Trigger | 0,400 | 0,0 | 4000,-200 |
BFAM: Combative Gains (Opponent's Pay) in the Aftermath of Initial Brute's Force; (3 x 3).
Table BFAM gives numbers that still predominantly benefit Agent A. But these numbers are based only the starting states of the agents, and shed no evidence on the constancy of costs over repeated iterations. Brute's Force may result in the situation of Table BFAM, and the decision for Agent A to choose Brute's Force over Silent Trigger may be due to the latter's unsuccessful enactment, which in turn, is due to the negative gains. Silent Trigger in BFAM, due to its requirements of high skill and effective cooperative, becomes virtually useless unless Agent B chooses to withdraw opposition.
The Game of Varying Coercion is an antagonistic game. It requires for there to be an aggressive antagonist and an incapable subordinate target, with much less the social and communicative resources than available to its opposer. What kind of game is this, for there to be irrationality on the part of Agent B that results in its entering this situation? Game theoretics do presuppose that agents act by rational choice, before, during, and after any arbitrary decision junction that is a game. As stated in the beginning of this section, the rationale for why situations such as Game of Varying Coercion occur is essentially long, nuanced, specific explanations based on histories. A more civilized version of this game can certainly exist, as Game of Pacified Varying Coercion.
| t=1 | Genuinely Cooperate | Civil Re-negotiation | Fraud/Betrayal |
|---|---|---|---|
| Pacified Silent Trigger | 100,100 | 0,0 | 1000,0 |
| Pacified Brute's Force | -1000,0 | -100,500 | 1000,0 |
GPVC1: Game of Pacified Varying Coercion @ timestamp 1; (2 X 3).
There is the question of the degree of choice revolving around the hands (of the agents and third-parties) in the Game of Varying Coercion. Would it not be splendid if there was only the alternative of Game of Pacified Varying Coercion to be played? There would be little motive for any rational Agent B to choose Fraud/Betrayal. The integrity of the feedback loops involving genuine cooperation and civil re-negotiations would lead to a continuous improvement process, without any second thoughts. But back to the matter of the Game of Varying Coercion, it could be argued that the events leading up to the asymmetric attributes of the involved players are essentially sibling decision junctions of the Game of Chicken. The key difference is that in the Game of Chicken, the objective is mirror-opposite decisions. To achieve the moveset of Agent A in Game of Varying Coercion, as a game before this game, there is required a kind of relentless dedication (including the security) to acquiring the skills and resources that then concentrates these attributes into the moveset, the starting possible choices available to Agent A. For clarification, the likeness in these predecessor games to the Game of Chicken, with the aims of achieving the position of Agent A, rests on the "security" in the relentless dedication. If Agents C and D are to compete, in forms direct or otherwise, to be Agent A instead of B in Game of Varying Coercion, then they are to attempt to appear as doves in particular contexts. Playing as the dove helps avoid direct confrontation with obstacles to their objective of becoming Agent A.
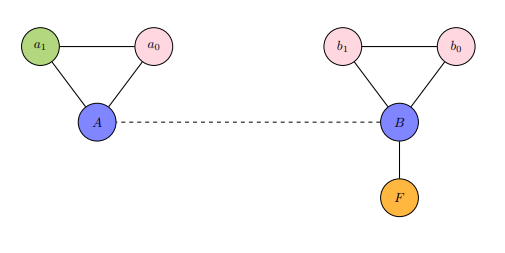
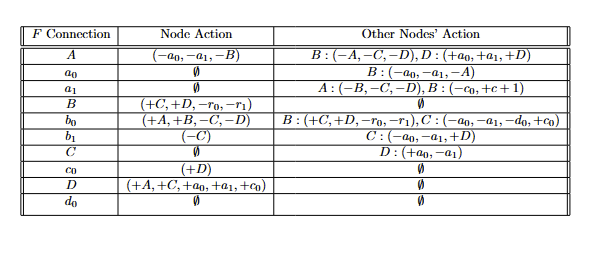
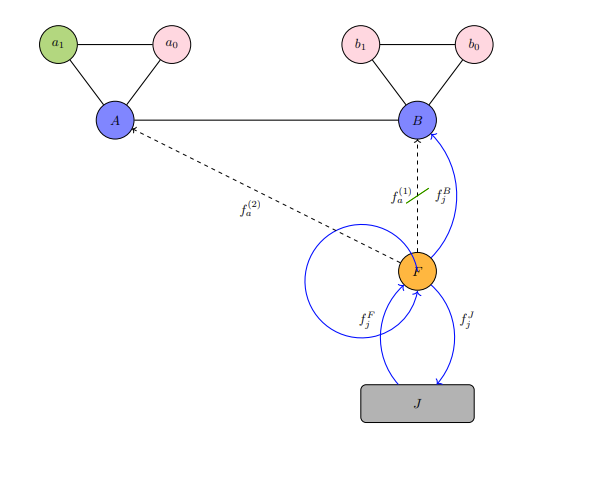
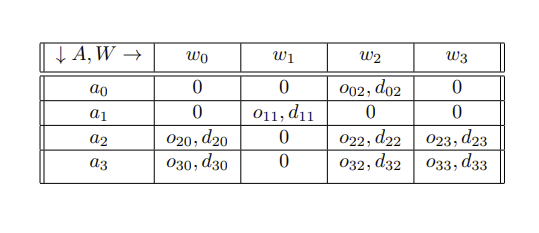
There is a lot to be said,written, or however else communicated on the "power of language", specifically its broad role in retentive and transformative processes. A universal desire exists amongst sentient beings to privatize (form and uphold attributes of secrecy) communication to their personally desired degrees. Unwanted members, such as those that would oppose the communication or would be advantaged as antagonists to know said communication, are the subjects that privatization efforts seek to exclude. In this game, deemed the Game of Crypto or Gibberish, communication does not take place simply between two distinct beings. There are calculations and layers involved, manifesting themselves as functional judgments and tiered structures (geometric spaces,networks,et cetera).
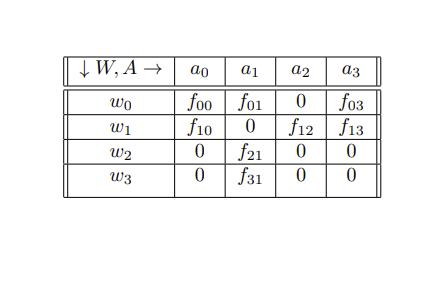
There are four agents in this game that consists of more than one cost table.
- Agent A: the interpreter of the communication.
- Agent B: the source and messenger of the communication.
- Agent C: correspondent to Agent A, otherwise known as a sub-agent of A; they provide methodologies,tips, and hints derived from their observation of Agent B. Such observation may require positioning for insider knowledge.
- Agent D: the follow-up actor to the interpretation by Agent A of Agent B's communication.
Whenever Agent A is mentioned, assume that Agent C is also included due to their status as a sub-agent to Agent A.
Three primary decision junctions exist in the Game of Crypto or Gibberish, and this section sequentially presents explanation on them.
Agent B has a question Q to provide an answer to. They know that this answer, formatted according to some specification, will be received by Agent A. There are three possible choices for answers.
-
$I_1$ : completely true in the case of Q being a fact-based query, otherwise completely genuine for Q that is a subjective-based query. -
$I_2$ : trivial, sarcastic, ironic statement. -
$I_3$ : completely fallacious or disingenious statement.
There are also three accomodating objective functions
for Agent B that ranks the choices for
-
$OBJ_1: I_1 > I_2 > I_3$ , -
$OBJ_2: I_2 > I_1 > I_3$ , -
$OBJ_3: I_3 > I_2 > I_1$ .
The first junction is one decision by Agent B to format
their message into a secure format, such as digital encryption
via some arbitrary mask procedures, denoted by
|
|
|
|
|
|
|
|
|
|
|
|
|
|
GCG1: Game of Crypto or Gibberish @ decision junction 1; (3 X 3).
For each cost-value pair
These two tables below are exemplifications of the objective
being
| 0,3 | 0,2 | 0,1 | |
| 1,3 | 1,2 | 1,1 | |
| 2,3 | 2,2 | 2,1 |
GCGO1: Table GCG1 by
| 1,3 | 1,2 | 1,1 | |
| 0,3 | 0,2 | 0,1 | |
| 2,3 | 2,2 | 2,1 |
GCG02: Table GCG1 by
Lower expenses in objectives are preferred, for costs
incurred upon the objective promote the failure of Agent B.
The direct association, between the value
Now onto the second decision junction, with specific focus
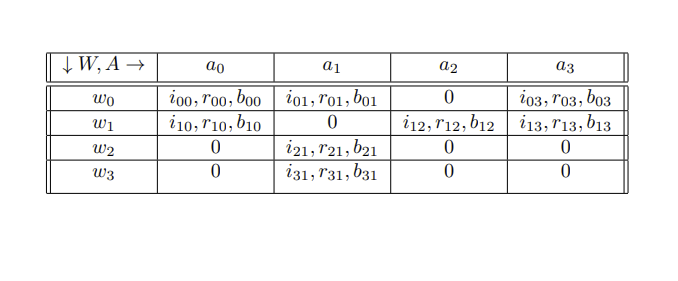
on Agents A and C. Correspondent Agent C's responsibility
was to "observe" Agent B for information regarding the
important attribute of the mask
| 1,3 | 1,2 | 1,1 | 1,0 |
GCGT2: Decision junction 2 for Agent A with C; (1 X 4).
The table GCGT2 pre-supposes that Agent A has been
able to ascertain the three available masks, as presented
in table GCG1. If Agent B wants Agent A to have the
capability to decrypt the message
On the matter of capabilities, if masks
Cost table GCGT2 could be further complicated
if Agent B were to, instead of selecting only
one
| 1,3 | 1,2 | 1,1 | 1,0 | |
| 1,3 | 1,2 | 1,1 | 1,0 | |
| 1,3 | 1,2 | 1,1 | 1,0 |
GCGT22: Decision junction 2 for Agent A with C in the event of plural information
The extent of labor required of Agent C, as well
as the degree of their skills in information acquisition,
in determining the credibility of
Moving onto decision junction 3, it is now Agent D's
turn to act. Agent D is given the information
| ?,? | ?,? | ?,? |
GCGT3: Decision junction 3 for Agent D, the follow-up actor
to the plain information received from Agent A; (1 X 3).
The Game of Crypto or Gibberish has a few noteworthy
attributes that if, left unmentioned explicitly,
may lead to alternative understanding. Every junction
point is a decision to be taken by exactly one agent.
Each decision may be comprised of more than one choice,
a choice as an
Relations between Agents A through D are an important aspect in this reduction to a single cost table, that can in turn be represented in at least two ways.
In the first route, there are three relations, each with their own particular set of variables and operators.
-
$\mathrel{R}(A,B)$ : Connected to the$OBJ_i$ selected by B in its message, the particular message communicated by B, and the decision by$A$ at decision junction 2. -
$\mathrel{R}(A,D)$ : Connected to the preference of A to want for D to- follow its preference on what action D should take,
- allow for D to take the most ideal action based on A's transmitted interpretation of B's message.
-
$\mathrel{R}(B,D)$ : Connected to the$OBJ_i$ selected by B, the action that B desires for D to take, and the action that best suits the interests of D.
The function
Function
The single cost table, by this first route of expression, is
| ~~~~~~~~~ | |||
|---|---|---|---|
GCGSINGLE: Single-table expression (route one) of the outcomes possible to the involved agents in Game of Crypto or Gibberish; (1 x 3).
And the best action to take, when the cost values
For the second route, every agent A,B,D has a corresponding
valuation function
| ~ | |||
|---|---|---|---|
| A | |||
| B | |||
| D |
GCGSINGLE2: Single-table expression (route two) of the outcomes possible to the involved agents in Game of Crypto or Gibberish; (1 x 3).
The problem that cost table GCGSINGLE2 asks to solve
is to determine the action
- Select
$A_{?}$ based on the greatest cumulative summation$c_0+c_1$ from valuation functions$V_{A}$ through$V_{D}$ . - Select
$A_{?}$ based on the least variance of$c_0+c_1$ between valuation functions$V_{A}$ through$V_{D}$ .
In the first approach, there is the belief that the action with the greatest singular value produced from the cumulative attributes and decisions of Agents A through D is most beneficial. In the second approach, there is the belief that the action with the most even distribution of gains or losses between Agents A through D is superior.
The Game of Crypto or Gibberish has the distinction of possessing an innate and constant opaque nature to guard against convenient understanding. Exemplifications of the Game of Crypto or Gibberish can be revealed towards full understanding, but perhaps the revelation takes place only after the actualization of events during timespans displeasing for the impatient or those that cannot afford the time.
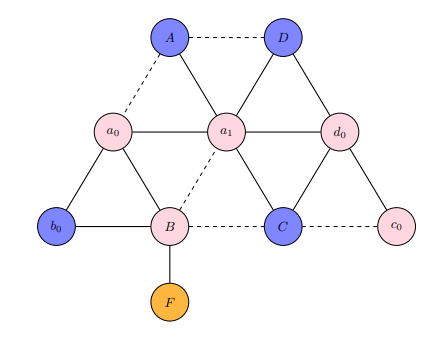
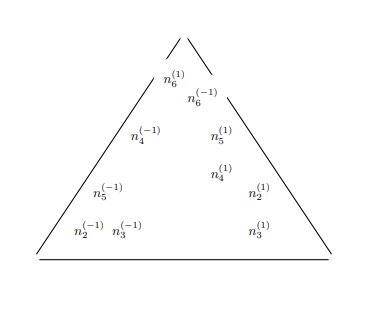
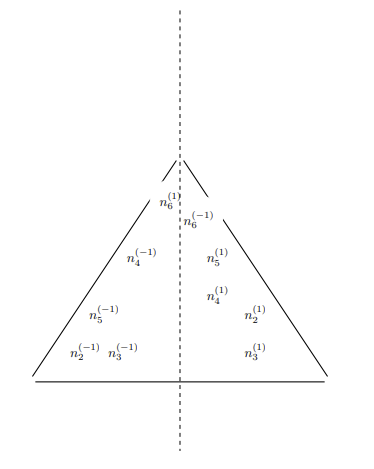
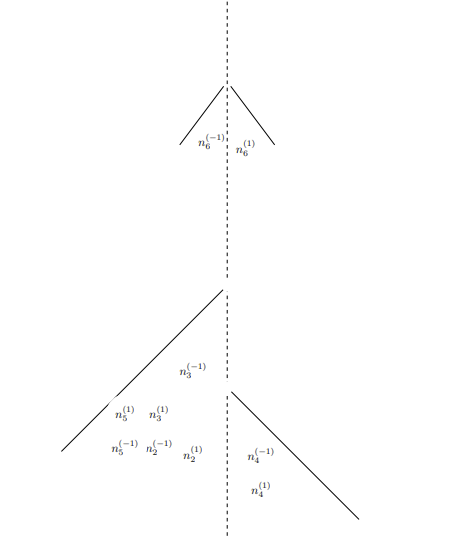
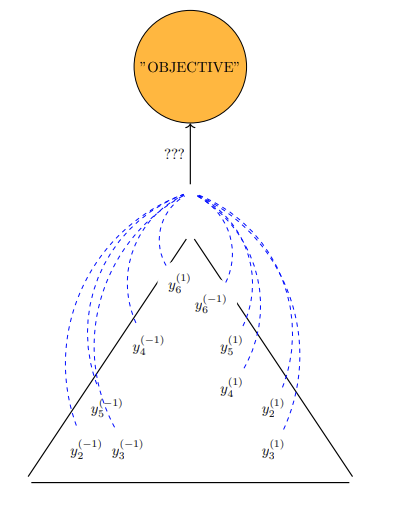
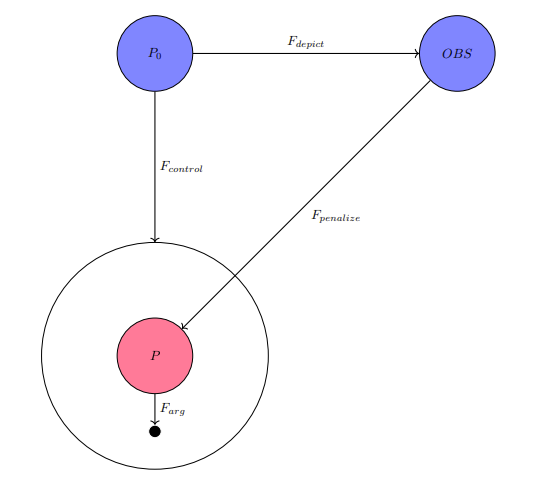
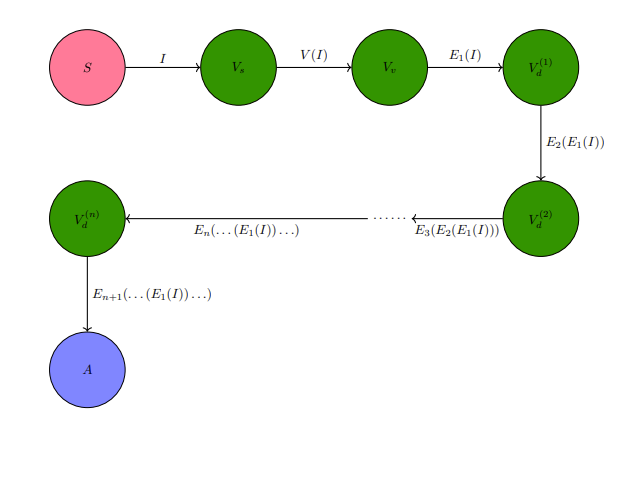
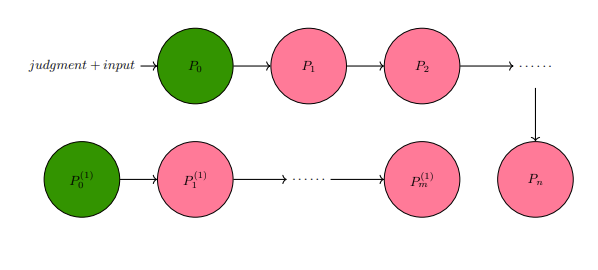
Maintenance is associated with aspiring towards the "constant", the "equilibrium", and confusingly, some quality/ies of the full picture belonging to a context that is a zero-sum dynamic. If maintenance was the absolute peak of potential for an entity, then there can be no question on what further magnitudes they can accomplish, relegated to the confines of their peak potential action of maintenance. Destruction consists of related but not entirely connected phenomena to maintenance. A casual reminder on destruction is it is enabled by specific conditions stemming from over-maintenance (excess magnitude in pro-activity) and lack of maintenance (negligible activity). Destruction is not the focus of this section, although phenomena labeled as destructive has a contradicting relationship with the defined ideals of maintenance.
A construct called the Game of Tree-Trimming is used to aid in quantitatively abstracting maintenance. The Game of Tree-Trimming is one, similar to the previously discussed Game of Crypto or Gibberish, with multiple cost tables in consideration. Threshold-activation, a quantitative condition that places demands on an actor with respect to their achieving some objective for them to move onto a different cycle or step, is an important component of the Game of Tree-Trimming and accounts for the continuum belonging to the actor's potential.
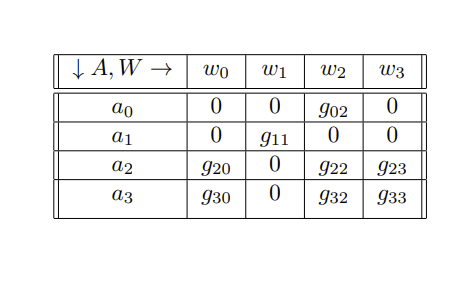
Similar to the Game of Crypto or Gibberish, the Game of Tree-Trimming has four primary agents.
- Agent T: the tree, comprised of a trunk (including the root) as
$R$ and the connected branches$B$ . Every branch$B$ has some arbitrary quantity of leaves$L$ and fruit$U$ . While a branch$B$ connects to T's periphery of$L$ and$U$ , it is still a strict subset of$R$ , meaning that it can never be$R$ . T has exactly one process, to naturally grow, that is, proliferate itself to be of a greater mass through extension of any one of its component classifications, the root$R$ , branches$B$ , leaves$L$ , and fruit$U$ . Outside of T's natural growth process, they do not have any mechanism of free-will to act in any other way. - Agent A: in charge of modifying T via its only action of cutting. The magnitude of cutting power available to Agent A is left undefined by default.
- Agent B: by its ordainment of continually perfect information on Agent T, commands to Agent A its preference on how Agent A should cut.
- Agent C: otherwise known as a third-party or unknown factor. Plays some role of advisor or ruler on Agent A's judgment of the appropriate command to Agent B.
One important constraint is placed on the capabilities of Agents
B,A, and C with regards to treatment of Agent T. The growth
process of Agent T cannot be augmented by any Agents B,A, or C
outside of A's cutting actions. The Game of Tree-Trimming is
an abstraction, and so does not include real-life considerations
such as environmental engineering that would affect Agent T's
growth process. Maintenance as half-measures of the potential
refers to A's cutting actions, and the maximum cutting power
(potential) of A is measured by its capability to cut the
leaves
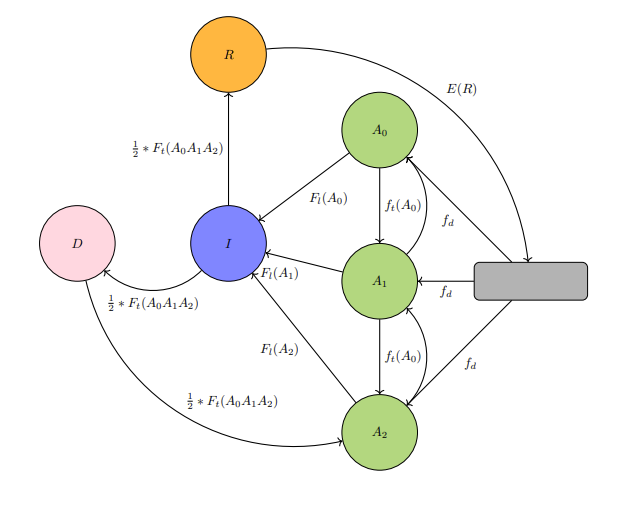
A hierarchical demand-flow is what the Game of Tree-Trimming relies on. Agent T's one action of its growth process is ascribed to the realm of "natural activity". The unidirectional source of influence for Agent A's cutting actions is from Agent B's convolutional decision-making process, that which involves contributions from Agent C.
GTTD: Flow-diagram for Game of Tree-Trimming.
Categories of threshold-activated functions, pertaining to
Agent A's actions, exist to fit the attributes of Agent T.
One category is for fruit and leaves, another for the
branches, and the last for the root
| branch | geometric measure |
|---|---|
| ... | ... |
TBR: Two-column table of branches and their corresponding non-negative geometric measures.
The threshold function for trimming branches is
In terms of efficiency and uniformity, it would
make sense for
The threshold-activation function
And the last threshold-activation function
These three threshold-activation functions suffer
from the probable problem of piecewise contradiction
between their outputs. For Agent B to judge, based on
its function
As mentioned in the initial introduction of the four agents in the Game of Tree-Trimming, Agent A's cutting power is undefined by default, but a sane presupposition can be made that this power it has is finite and non-static. An opportune time for Agent A to cut some part of Agent T may not come again.
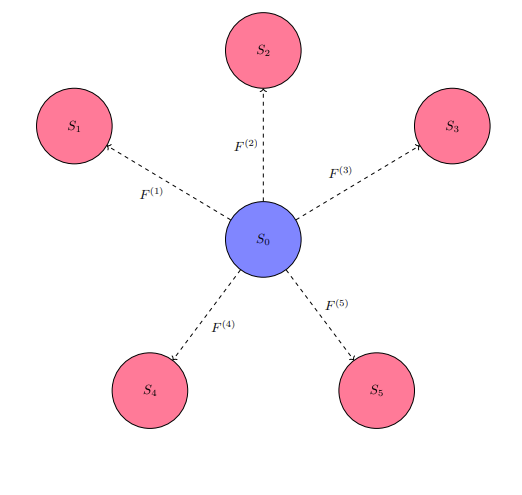
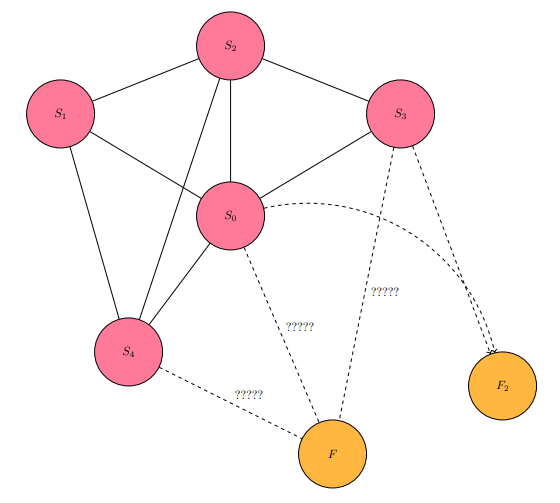
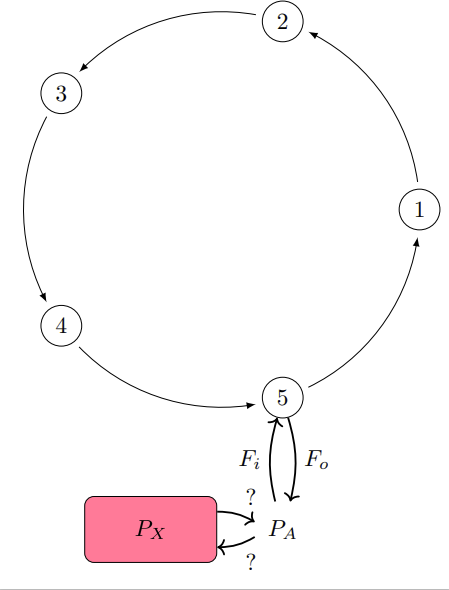
Gridlock describes a condition with particular traits in a group of entities (two or more), with at least one entity thinking and acting for an interest that does not align with at least one co-entity in this group. The perception of gridlock has a level of difficulty in detection, whether by members of the involved group or a third-party, proportional to the cumulative difficulty in accurately measuring each member's advances (improvements, actualization, et cetera) in their interest over a selected period in time. In gridlock, membership of an entity in a group does not require their voluntary consent. Enactment of connective principles such as contractual agreements, socio-economic magnetism, and co-dependencies are some of the preventative measures against an entity's attempt to separate themselves, by their own perogative from a group.
Suppose a group D has five entities in it:
NOTE The integer five is a common number, alongside two and three, in the context of division or at least difference. Five is the value from halving in base-10 numerical systems. It was chosen as the number of entities in this example based on this premise.
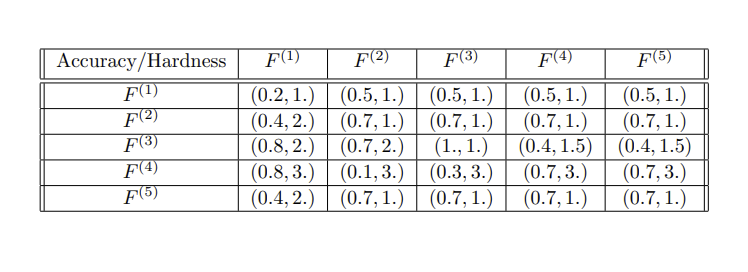
Each of the entities
| Interest | Wanted Outcome | Actual Outcome |
|---|---|---|
GRLK: Table showing the wanted and actual outcomes for each entity of group D. None of the actual outcomes in the table above equal their corresponding wanted outcome, due to gridlock.
To conclude on this section's generalization of gridlock, gridlock places demands on each entity in the group in such a way that no entity's state can improve via efforts for their interest. The lack of alignment, which could also include malignment, between the interests of at least two entities fuels a nullification process that breaks the wanted outcomes of all involved entities in the gridlocked group. The Game of Breaking Gridlock helps to illustrate some of the activity, efforts by members to break free of the gridlock and perhaps even separate from the group, that may occur in gridlocked groups.
In this game, a group G of entities are in a gridlock, a condition that has been generally defined in the beginning of this section. In this gridlock arrangement, none of the entities can "outperform" any other co-entity. The term "outperform" is a strict classifying term on an entity's success in achieving its interests, by relying on its own autonomy of resources and capabilities at the initializing instance of the Game of Breaking Gridlock (gridlock has already been set). Entities can attempt to "outperform" another by increasing the magnitude of their resources' and/or capabilities' utility, but gridlock will prevent their outperforming by this game's starting state. There can be intersection (sharing) of control (autonomy) between members of a group with respect to resources or capabilities, at the expense of administrative simplicity. The objective of at least one of the entities in a gridlock is "subversion" of the gridlock arrangement. Generally, "subversion" can be achieved by an entity outperforming or, antithetically, undermining another to such an extent that the other's performance falls short by some measures that would have ensured the preservation of the gridlock arrangement. The full achievement of subversion disintegrates the conservative force behind gridlock, thereby enabling at least one of the entities in the group to achieve their original interest.
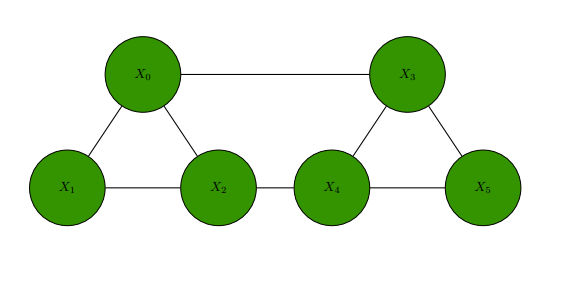
The below diagram illustrates the connective arrangement in a gridlock of the five entities of group D, from this section's beginning. Each two-headed arrow is a relation between two entities. The lack of labeling and functions for each of these two-headed arrows is intentional, leaving the nature, biases, and leanings of each relation open to the specificities involved in practical affairs.
GBGD1: Graphical illustration of group D's connectivity. In mathematical lexicon, this group is a complete graph. There is no correlation between node positioning and entity rank in the group.
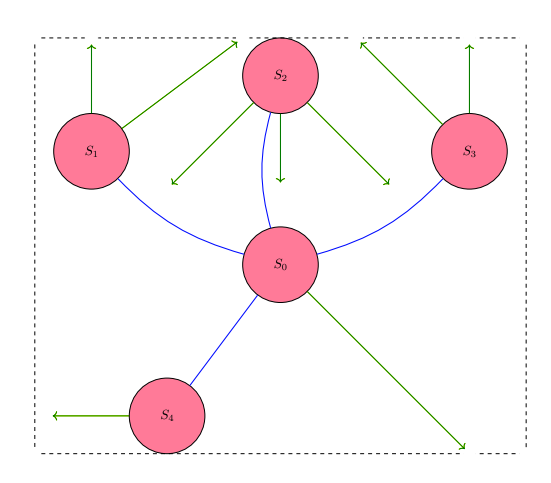
If the five entities of D exist in a closed world, and they conserve their activity for their constant interests, then gridlock is expected to last for an indeterminate amount of time. In cases in which D does not exist in a closed world (perhaps a world is better understood as constructed and defined rather than the inherited constant), then entities in the Game of Breaking Gridlock will attempt to break gridlock (that is the objective of the game) by underminement. In an open world, members of group D will seek to undermine one another by possession and possibly utility of specific gains, reaped from a "middle ground" through a feedback loop. The "middle ground" is a composite prediction by group D on what would enable at least one entity to "outperform" others. Outperformance would finally and directly enable the advancement or fulfillment of at least one entity's interests for a broken gridlock.
GBGD2: Graphical illustration of a functional feedback loop between group D and a "middle ground", a composition of each entity's predicted source for their underminement activity.
Diagram GBGD2 is not foolproof as an illustration for underminement by members of group D. If perhaps only one entity does not conserve their activity for their constant interests, the losses from their failure to conserve would transfer over to another entity in group D. The gravity of change from such zero-sum transfer increases the likelihood of a broken gridlock due to the reason of failed conservation. By complication through diversification of semantics, the definition of an entity's "performance" is extended to explicitly include its conservative (retentive) power in its autonomy (resources and capabilities). In diagram GCGD2, the arrow from group D to "middle ground" G is a query (request) by some arbitrary set of D's entities for resources, physical or otherwise, to aid in the entities' ulterior objective of underminement. And the "middle ground" G responds by a function that outputs a product (physical or otherwise) back to members of D selected by G as the receiver of the product.
Diagram GCGD3 shows the process of underminement from
start to potential "finish". The blue nodes are labeled
GCGD3: Prospects of underminement by members of gridlocked group D.
There are a few questions for the thinker to ponder on in this Game of Breaking Gridlock. How and why would there be encouragement for entity activity to be redirected towards a middle ground? To answer that the encouragement was instantiated due to the drive of at least one member of a gridlocked group G to break gridlock is a roundabout answer. How would the gains reaped from the "middle ground" and transferred to selected members of group G be utilized for partial advantage, on the condition that gridlocking conditions prohibit the utility of advantage, that is, resources and qualities not present in the initial autonomous conditions of the group's members? As for the possible future, abstraction by the Game of Breaking Gridlock opens the doors to the undefined.
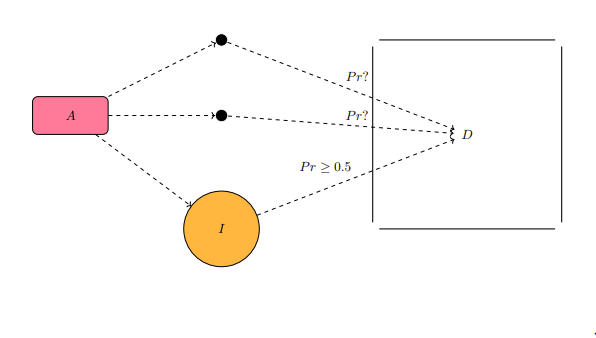
What does the word "judgment" mean when there are no consequences from the occurrence of it in the sentient mind? The concept of "judgment" is associated with a decisive tone, maybe consequence or consequences, maybe a conclusion to merely believe in if not to uphold and advance. The explicit mention of associated terms, such as consequences and conclusions, belonging to judgments is necessary to discuss the topic in this outline of cognitive processes.
A sentient being can "perceive" something. And then that same being forms a judgment of it. This sequence follows the logic of forming conclusions, or at least informed hypotheses, derived from experience formatted as the "perception". Note the usage of the additional word "informed" as a descriptor for these hypotheses, since a "hypothesis" is very frequently defined simply as an "educated guess". As funny as an "educated hypothesis" sounds, the phrase would go against teachings of its definition as an "educated guess" on the premise of redundancy. To add on more to these elaborations in a way that is besides the point, this statement makes no implicative jab on any education system.
The simple logic that judgmental processes are borne from perceptual ones falls very short of capturing the full extent of complex cognitive phenomena. Information-flow engineering, basically data engineering that is directed (maybe by force) into a sentient being's cognition, results in the frequent state that is the sentient being forming judgmental functionaries to streamline the innumerable cases of information into categories much fewer than the original number of cases, granted that the being has learning capabilities in the realm of informatic-efficiency. With learning capabilities, the easiness in mentally computing or concocting certain tasks, over the frequency of practice through exposure, results in generalizations (classifications) that have an acceptable rate of error, acceptance due to the gains in efficiency, with respect to the possible information cases to be received. In machine-learning theory, this dynamic is termed bias-complexity tradeoff.
There is some perspective to be written on bias-complexity tradeoffs. Definitions provided by orthodox machine-learning experts define the bias as something inclusive of the error term (typically a decimal in standard algebraic equations). The complexity of the solution, meaning the amount of effort required to obtain the solution and its final form, removes the bias. The complexity of the solution may also lead to over-fitting, a technical term used to describe solutions that are virtually perfect (no error in performative tasks such as classification and regression) for subsets of the entire space of information cases and also, meanwhile, would or did perform poorly for different subsets of the same space of information cases. The orthodox definition of bias-complexity tradeoff sets the bias' identity as akin to the error-term. However, outside of the orthodox definition provided by machine-learning experts, bias could be regarded as an "open-ended" component for a solution, synonymously a "freedom" for an agent to make selections, in the remaining but diversified options, for their own "full solution". And the possibly high complexity of a solution, minimizing the error by the tradeoff dynamic, produces practical biases, those that produce a high rate of error on some subsets of the entire possible information space. This commentary on the perspective of the concept of bias-complexity tradeoff swaps the roles of bias and complexity, from formulation towards the solution (meditation, introspection) to actualizing (non-rehearsing utility) on the solution.
One broad area of complication in fully describing judgmental processes is its influence on perception. One thing that can be stated for certain is: the extent in existence and use of judgmental functionaries regarding cognition has a correlative influence on perceptual tasks that take place after said functionaries have taken root. This statement can be used to buttress idioms such as a sentient being "sees what they want to see and hears what they want to hear". Judgmental functionaries seem to manifest themselves in symptomatic effects such as the primary symptom of filtration processes against the intake from information flow.
There are two over-arching classifications of cognitive processes revolving around judgments and perceptions, based on the relative ordering of their occurrence. There is the judgment-first and the perception-first model. Before moving on to notions on these two models, mentions on personality tests such as the famous Myer-Briggs test are a helpful visitation. The Myer-Briggs test is used as a criteria for classifying personalities by thought processes. There are exactly sixteen personalities, due to four categories such that each category has two variants. This section is only interested in the last of the four categories, with two variants of perceiving and judging types. This specific test assigns a personality as either perceptive or judgmental by the predominance (of frequency) of one of the two traits over the other. And the frequencies collected are through questions asked that are supposed to yield "genuine" answers.
Shifting focus back to the two models for cognitive processes that is judgment or perception first, there are unique advantages possessed by each model. The judgment-first model is a more defensive model against arbitrary information flow, in which the labeling of "more defensive" is derived from the greater magnitude in filtration process utility over that of the perception-first model. There is still the unanswerable question (in the general realm) of the effectiveness in the higher defensive posturing encouraged by this model. This model is also ironically more action-oriented than its counterpart. To form a conclusion or at least a decision quicker than by the counterpart model that emphasizes perception (indiscriminate intake from information flow) could very well be an advantage in cases where threats or flaws are well-recognized and thus anticipated ahead of time. Judgment-first models intend to bar advantages by threats that would have been given wider and deeper opportunities, due to the sentient being's openness, for inflicting fault.
The exclusive gains from perception-first models are judgmental processes that are fuller in breadth and scope because of the typically higher intake from information-flow, given the patience that is extra time required. Not all tasks (mental or otherwise) demand an immediate consequential action afterwards. But perception-first models may not yield effective solutions in a timely manner based on the nature of their specific information-flow intake. For example, if the same errors in the form of patterns similar to one another are present in the intake, perception-first models must know to "cut the losses" of additional experience. To further exemplify, perhaps it is not the value derived from more open information-flow intake that is gainfully important, but that of proceeding to action.
An obvious thought on these two models is that there can be a "balancing act" between them. There is no physical law on cognition, based on prior evidence yielded through empirical studies, that states that exactly one model is to be used for the duration of a sentient being's existence. On the premise of design behind the Myer-Briggs test, it is conjectured that preferring one cognitive model over the other at some critical spans in time (such as the beginning) may skew overall cognitive processes through the span of a sentient being's time in ways that contradict the "balancing act" it desires, goals for a middle ground of impartiality. The corrective cycles involved in judgment-first models may yield more pronounced changes in acquired solutions, due to the obvious possibility of drastic differences in the samples from arbitrary information-flow intake.
Obtuse judgments can count in cases in which there is the lack of immediate consequences against the sentient being, the practitioner of the obtuse judgment, if they are to acquire dominion over their "immediate vicinity". The acquisition of dominion gives credence to the practitioner of the obtuse judgment. And maybe in contentious affairs, those that have already established dominion through their obtuse judgments will find their foe weak and beneath them. The foe may have relied on a perception-first model in their daily practices, only to discover that their information-flow intake was not substantial enough to adversely compare with those holding obtuse judgments against them.
Here is a musing on what superiorities of two classifications in thought processes, with no definitive answer for that would require specific examples.
The word "reverence" carries attitudes and beliefs of genuine respect for a noun, typically a sentient being. An attempt is made in this section to detail what reverence means in practice, and its alternative analogues, intended to appear as the authentic, to shift well-meaning focus towards them.
There is a similar word to reverence that may act as a starting step towards the belief in it. The word is "reference". In a world of utmost connectivity, strong connectivities between polarities (maybe the only way the polarity preserves its full identity) and between variants (higher orders of difference), a reference can be a or the source from which the connectivity stems from. A reference could also be a derivation of a source. The connectivity, once put in existence, can be shared in some variable manner outside of the full control of the reference as the possible source. The choice to acknowledge connectivity between two seemingly different objects matters in the context of identification by cognitive functions.
Here are a few broad classifications of attributes for references:
- duplicate (indistinguishable to its "source"),
- complement (requires the "source" to be perceived as incomplete in the sense that the reference can aid as an additive towards its fullness),
- variant (distinguishable from the "source", but related to it in ways perceivable by select observers).
In input-output computational network models, with the inputs given the freedom of arbitrary definition (although the networks may immediately reject the inputs if they are to violate network input conditions), cognitive tasks take place by way of information transmitting from element to element of the network. An element of a typical network may be a node (station,endpoint,unit) or an edge (connective piece between any two nodes). Each element is attached to some function that serves as a condition for how the information being transmitted is utilized. Common utility purposes include transforming the specific information into another form (of a different data space) or a variant in the same space, as well as routing the information to another node or along another edge.
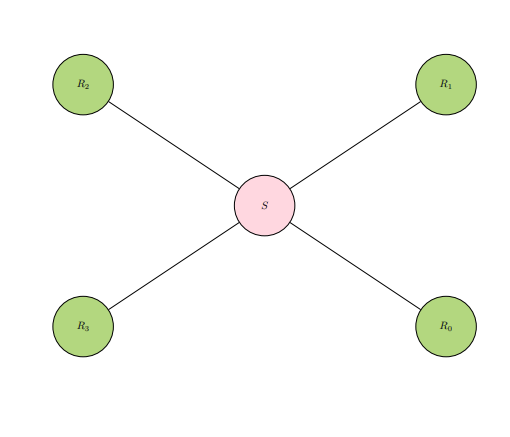
Some common roles for sources of references, using the data format of networks, are centers, sinks, and deflectors. Each of these roles are illustrated in the proceeding diagrams.
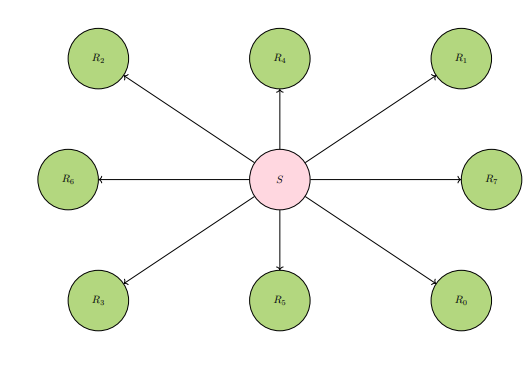
REFSTAR: A star graph, with the source (red) in the "center".
REFPER: A line graph, with the source (red) at the extreme peripheral, the "sink".
REFALT: An arbitrary graph, with a reference (red) acting as a "deflector" against the source (labeled S).
In diagram REFALT, reference
Some formulaic notation is called for in discussing the
classifications for references based on their attributes.
Suppose an element
The table below shows an element
| Element | Attributes |
|---|---|
ATTRT: Attributes for element
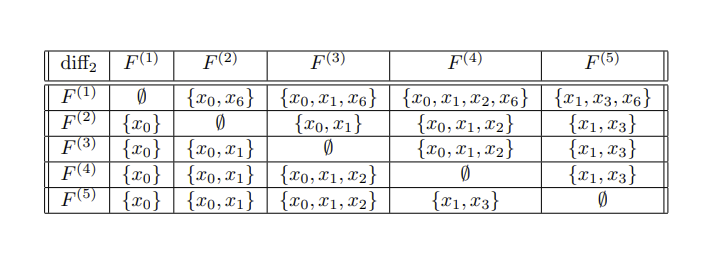
The task of distinguishing an element from another by mathematical approaches is frequently based on on functions similar to the arithmetic operation of subtraction. For any two elements, the qualities that distinguish them are
These two formulae oversimplify the computation
of distinguishing two elements based on their
specific attributes, but they do serve as a
typical template for further specification.
Specific differentiation between two attributes such
as
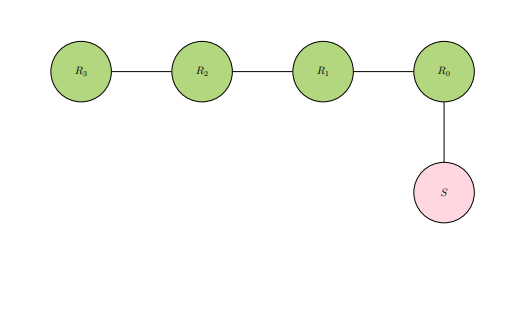
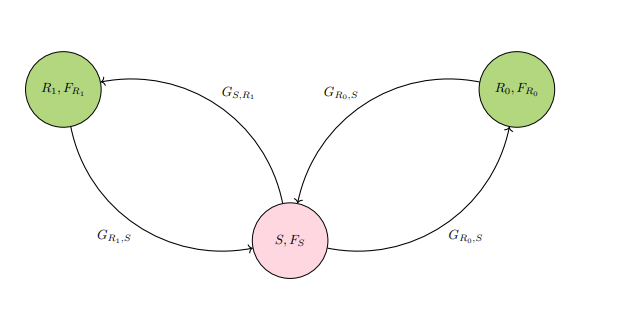
Qualities of information-flow activity are a central topic for observation in computational reference networks, a category of reference networks. Flow of information requires direction along edges if the information is to not be jammed in transmission. Direction of flow can change in these networks, and the mechanisms for these are later specified in more constrained terms. Edges are typically left open to be bidirectional (in other words, undirected) so that there is possibility for change of flow in spans of activity deemed necessary, such as cycling of information back to nodes and edges already traveled for corrective or reflective purposes. There is exactly one of two responsibilities for a node recognized as the source. These two responsibilities are material and functional utility. The terms "role" and "responsibility", as categorical terms in this section used to describe how sources and references work, are not synonymous with each other, although there is a lot of overlap in interpretation between these two terms in plainspeak. Before defining these two responsibilities by way of written language, these next diagrams below on common information-flow patterns allow room for familiarity.
INFOREF1: Diagram shows a computational reference
network. The source node
Computational reference networks complicate the categorization of nodes by their roles. In diagrams REFSTAR,REFPER, and REFALT, the undirected connections between nodes allow for easier recognition of their most probable role, based on metrics concerning node-to-node distance and centrality. The additional feature of adding directions to these edges (connections) for information flow, without consideration for more network features, allows the possibility for any node connected to the network to appear and act as any role.
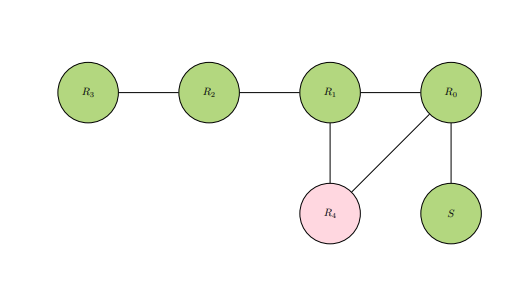
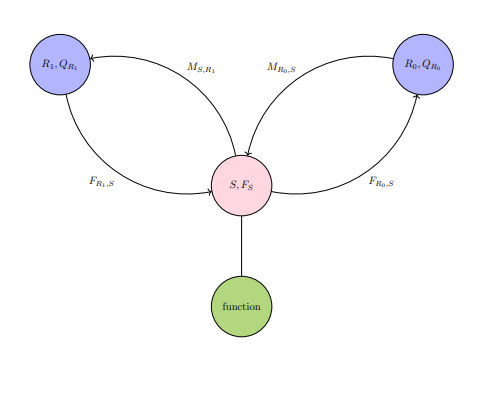
INFOREF2: Computational reference network with source S having a material responsibility of transmitting information to all connected references.
Diagrams INFOREF1 and INFOREF2 provide visual basis on the two responsibilities of a node in computational reference networks. The responsibilities of material and functional utility are reduced to the relative direction of flow from a node acting as a source in these networks. Material utility consists of negative flows of information from the node acting as a source, and functional utility consists of the opposite that is positive flows. No specific conditions are set in computational reference networks for the endpoint receivers of the information from these positive and negative flows. There are innumerable ways in which computational reference networks can be used. Networks, especially in computing, operate by arbitrarily-defined rules. Many in operation today are used in tasks such as communication in social circles or supercomputing. These tasks will not be explored by way of computational reference networks since they may require a lot of proprietary real-life information, and must require technical details too minute for the wanted broadness in this section.
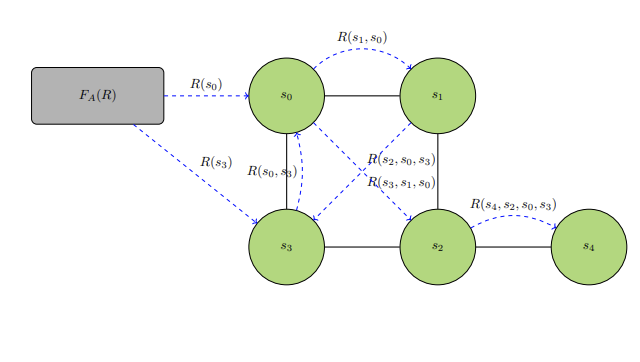
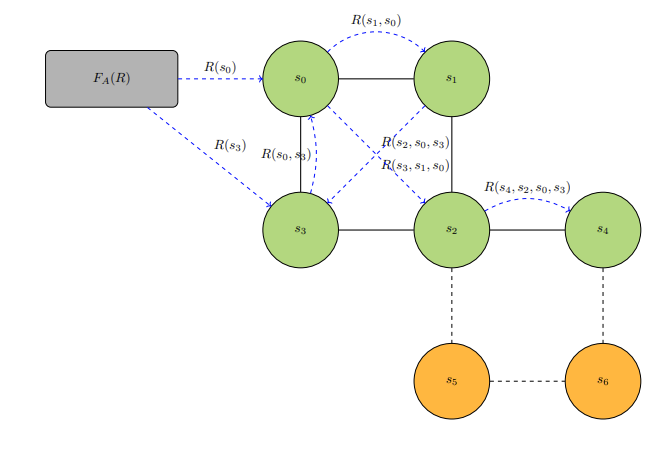
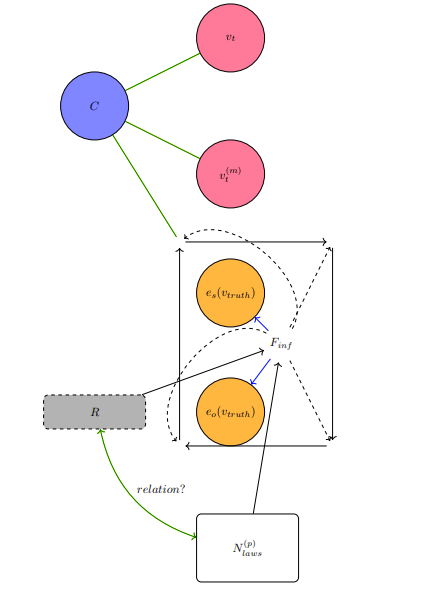
One way is through the Game of Reference Identification (GRI). Specific calculations in this game can be extensive enough to be very difficult to comprehend in a short amount of time. The Game of Reference Identification bases itself on a computational reference network. There is exactly one source and at least one reference that is not the source. All nodes in the computational reference network are connected to each other, although there may not be an edge shared between every pair. Every node has some set of attributes and also a function that acts on information it receives. Every edge also has a function that acts on information it receives.
A third-party agent
- the node is accepted by agent
$D$ as the source, - the node routes the information passed to it along an edge.
And for action to be taken on an edge, there is the primary one of routing the information along it to the node at the end of it (represented as nodes touching arrows in diagrams INFOREF1 and INFOREF2).
On the format for any criteria by any third-party agent
- a sequence
$\overrightarrow{A} = {A^{(D)}_0,\dots,A^{(D)}_l}$ , values of the attributes hypothesized by$C$ to be the correct answer, - a non-negative integer that serves as the number of unknown attributes,
- a pairwise attribute-distinguisher function that compares two
values of an attribute
$A_i$ ,$F_{-}(A^{(?)}_i,A_i) = q.$
The value q is typically a real number, due to the space of real numbers serving as a continuous spectrum for magnitudes in differences, such that if$q=0$ , then there is no difference between the two attribute values.
Each member of this list can be modified by agent
| Attribute Hypothesis | No. of Unknown | Distinguisher Function |
|---|---|---|
| 3 |
CRI1: Criteria
| Element | Attributes |
|---|---|
ATTRT2: Table of elements and their attributes, such that
CRN1: A computational reference network of elements in table ATTRT2.
Note the function sets
Every associated function of a network's piece takes as input the running criteria of a third-party agent. The term "running" is a descriptor for a variable that undergoes changes applied by one or more outside factors in a duration of activity.
The functions in the network of diagram CRN1 could go as such.
| Function | Formula | Activation |
|---|---|---|
| pass to end | ||
| pass to end | ||
| pass to end | ||
| pass to end |
FEDGEG: Table for edge functions, their formula and activation; (5 x 3).
The null formulae for these functions denote any information transmitting along them freely transmits to the corresponding endpoints of the edges. For each of the node functions,
Functions
In more complex cases, node or edge functions can act as modifiers onto the distinguisher function in use by the third-party agent. This stipulation assumes said third-party agent does not have full control over its criteria that it uses in search for the source. These kinds of functions are something that can be termed degenerative coupling functions, functions that influence the behavioral variables of another function in such a way that that function outputs values different from before the modification.
Activity on the computational reference network in diagram CRN1 could go something like that found in this table.
| Timestamp | Node Location | Action |
|---|---|---|
| 0 | pass to |
|
| 1 | pass to |
|
| 2 | switch flow of edge |
|
| 3 | cannot pass to |
ACTLOG1: Four transmissions of information
An arbitrary feature that can be added to computational reference networks for any third-party agent is cease information flow after a specific number of edges the agent has traveled. For instance, if threshold for cessation is exactly 1 edge, then the third-party agent has exactly two node options, based on information flow, to choose as the source. But it could still guess, with no knowledge acquired through the information flow, that one of the remaining nodes is the source.
Next, here is one possibility for agent
Using
On the idea of reverence briefly mentioned at the beginning of this section, some notions on the idea of reverence not yet discussed can be put forth after elaboration on computational reference networks. Reverence can be further described as a devotion by one, a devotion that is more selfless for the revered than not, and is also psychological phenomena by one that holds the revered in higher esteem and light than even themself.
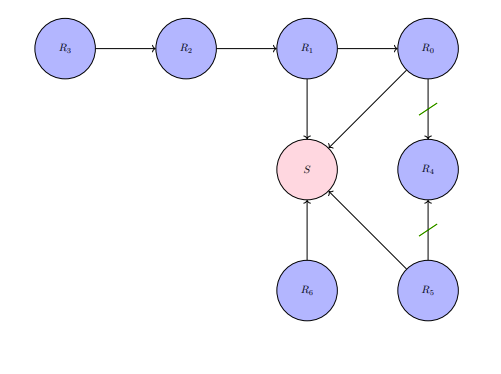
A computational reference network can, by way of numerical spaces such as the real numbers (where greater numbers represent greater influence), quantitatively model reverence. A typical network formation is based on a star graph. For every reference node connected to the source by way of some edge, the associated node and edge functions are based on pairwise-comparator functions between some wanted (ideal,desired) attributes, such that those attributes may not actually be possessed by the references, and the attributes belonging to the source. Information-flow patterns, in the context of responsibility, tend to oscillate between material and functional utility. The material utility, negative flow of information away from the source, is used by references to possibly proliferate (promote and duplicate by transmission) to other elements. Then these other elements may hold functions that are similar to the initial references of the source. And the cycle of proliferation may continue until there are conditions that constrain the process to a stall in growth of number of references, and perhaps the number of references shrink by way of severing or altering connections for information flow in matters of material and functional utility with respect to the source.
CRN2: A computational reference network, with
The Game of Reference Identification is not that similar to a needle-in-the-haystack problem. The task of identifying the source and finding the needle appear to be similar in the sense that some unique object must be found. But for the latter objective, the haystack problem typically requires large scales of information to become difficult enough for third parties to identify the needle. The third parties in needle-in-the-haystack problems have to resort to tactics such as brute force, and these tactics require a scale of resources that correlates by some proportion to the size of the haystack.
The newspeak involved in political warfare continues its evolution to this day. The word "doxing", having made its way into the English dictionary, means to distribute information that was intended by certain interests to be completely privatized, supposed to be known only by those interests that prohibit such distribution of said information.
In the Game of Reference Identification, the act of "doxing" could entail giving a third-party agent the correct criteria for identifying the source, via communicating the source's precise attributes. In the Game of Breaking Gridlock, the doxxer (they that act by doxing) provides supplementary material, containing knowledge advantageous to the recipient, to specific entities as partisan support for their interests. In the Game of Tree-Trimming, the doxxer could provide information that leads to the most "ideal" decisions made by the cutting agent. In the Game of Crypto or Gibberish, the doxxer could provide the correct contextual or literal information on the message to the correspondent (Agent C) and interpreter (Agent A). In the Game of Varying Coercion, the doxxer could help agents of Silent Trigger. These are some very well-known aims of doxxers. This statement can very much go without any citations of real-life cases.
The idiom of the needle-in-the-haystack, analogized in the end of the last section (To Be Revered by What), makes for a safe and conservative starting step for discussing the topic of doxing. What if, in adaptive systems, the structure nicknamed the "haystack" grows to be insurmountably large in the sense that the doxed information poses no advantage whatsoever? Doxing does not necessarily lead to a certainty in increasing the probability of accomplishing some objective in these games mentioned. Doxing can serve as an aggravating force. The attempt to disseminate information, without knowing the certainty of its correctness or the consequences of its use, can lead to dismal answers given to those questions. Alas, the intentions and actualization of achieving some aims, via knowledge thought to be advantageous by one or both the recipient and sender in doxing, are essentially specific semantics under the Game of Crypto or Gibberish.
The superstitious notion of a curse, phenomena perceived to be some nature that bears some effect, all this without empirical reasoning and additionally power ascribed to a foreign/alien/deitified force, could very well be the result of recipes heavily reliant on doxing. Suppose these patterns perceived to be malicious by some, those that hold the patterns to be curses, fall under games akin to those already mentioned in this section.
Interpret events one step past the five senses in cases such as disintegration of the state, feudal republics, "staged accidents", ultimate mysteries, and other dysfunctions of madness down the darkened list, and to call these kinds of events curses falls under the conclusion that is an opinionated acceptance without rediscovery, bound to the lack of light.
The value of every cost (typically a number in the space of real numbers), when presented to some audience, is expected by one or both the presenter and the audience to be of an authentic measure, according to metrological processes recognized as objective. There is a difference between the value of a cost and the value of a fact, typically presenting themselves in material forms that are agreed upon by conventional and well-known methodologies to zero down room for possible advocacy for conflicting valuation. If material forms cannot be acquired on certain facts, then there are alternatives such as replication, retelling, and group consensus as proofs by argument. Cost can be as scant to the solidity of facts as speculation without any mechanism geared towards correctness. Cost is a judgment of some body of facts, and these bodies of facts can be collections of bodies of opinions converted into numerical frequencies. Costs can then be understood as condensation of subjective interpretation of some body of facts into singular values, in the image of fact.
Some inklings on expectations are first put forth. And these inklings are used to describe a simple template for expectations of cost. A foremost pillar to rely on for expectations is the past, given the condition that there was proper accounting on pertinent events and objects of said past and this proper accounting has survived to the present time. With this condition satisfied, the past is a conservative source to refer to. The conservative source, even in cases where there are falls and faults, serve as templates for understanding in manners such as present-time predictive and referential tasks. A second opinion of the past could directly open the possibility to entertain it as something to be revised based on additional information received, or something that certainly can be interpreted differently using the information already possessed. Setting the past as the conservative source (the "axis") for relativistic understanding of present-time costs is not as grounded in certainty as those appreciative of the past may hope to be.
What is the future in terms of cost? With no regards for fictional depictions of utopia necessary, the future is thought of by some to be an ideal to be worked for through risk-averse practices. Or is the future an open-ended question, filled with great possibilities for advances through stochastic experimentation?
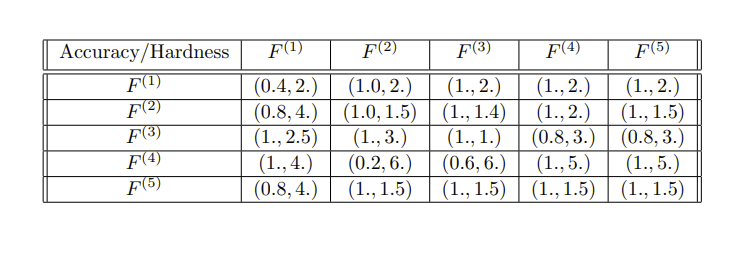
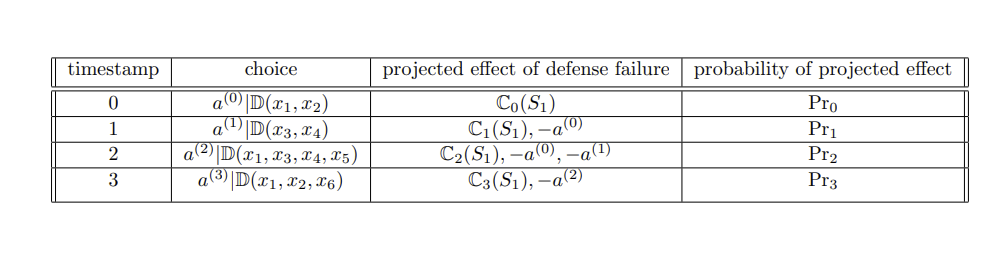
In the paradigm of machine-learning, as sophisticated as the most state-of-the-art algorithms the field has produced, there is one of a few important subproblems. The subproblem is supervised learning. It is conducted by computational processes, using data already annotated using descriptors agreed upon by the supervisor to be correct, to "learn" solutions for the data (tagged by descriptors) in a possible space of solutions. Supervised learning is a concept that can certainly accomodate the divide between expectations of cost with the "actualities" of cost. To maintain generality of discussion, needless for the nuances of mathematics, the values of cost can be dichotomized into paired values: (the expected, the actual). This constitutes a constant calibrative process to maintain the "factuality" of cost. Table EAST1 shows a modified version of the cost to resources by Silent Trigger, in the Game of Varying Coercion. The cooperative and the actor behind Silent Trigger do not know the value of costs associated with their two respective possibilities.
| ~~ | Effective Cooperative | Ineffective Cooperative |
|---|---|---|
| Bull's Eye | (-3,-4),(-12,-15) | (-1000,-2000),(-50,-30) |
| Missed Mark | (-30,-29),(-100,-100) | (-1200,-800),(-1000,-300) |
EAST1: The table ST1 of section Situational Engineering, each pair of values dichotomized into (expected,actual) format; (2 x 2).
One major goal of this template, already quite well-known and taught in educational settings on applied mathematics, is to reduce the disorientation from judgments, thought to rest soundly on condensation of quantitative information, that would lead to negatively consequential decisions on a ghastly magnitude.
Learnability of any problem can pose a security issue to the conservative source, mentioned earlier in this section. If disorientation of a judgment, quantified as big differences in values between the expected and actual, does not lead to adverse effects for those that depend on the judgment in some relevant span of time, then the disorientation could become a permanent substitute for the orientation (also referred to in this section as the conservative source, the "axis"). The security issue is the removal of the conservative source that some if not many at the "beginning" strongly upheld as the standard.
What is left to the imagination may stay in the immediate and constrained realm of the imagining. The extrema, holding the range for this thing called imagination, is so wild and varied, and typically discussed openly (but how honestly is another question) only by drunkards and deceivers. Imagination is one of those things that require a source for the thinking behind it, and behind said source, a dampening agent who may be called a pessimist by those that do not share their views. The pathologically optimistic do have imaginations that mostly stay unrealized in a structured society. But this section does not delve into the societal and neuroscientific aspects of imagination.
Imagination as a quantitative factor, a factor that lends influence into an actual for an effect predictable by the nature of the automaton it is connected to, is not as open-ended as unquantified half-formulated thoughts (the other half is what is not yet defined), multiple interpretations, and rudimentary principles that result in conflicting or specialized designs. Automata can be materializations of automata theoretics. And automata theoretics is the applied practice of automata theory. Automata theory, a subfield of computer science, provides the lexicon and methodology to model processes by way of a directed graph, similar to the computational reference graph defined and elaborated upon in the section To Be Revered by What. The automata in this section are illustrations of selected circumstances possibly borne from the acceptance of imagined values.
One use of imagined values is as a priming factor to activate an effect of an object or catalyze a sequence of events. The activated effect or event/s is the actual that emerges from an imagined value. From a cognitive standpoint, an imagined value could take the form of a speculation or conjecture, possibly difficult to numerically represent, that transmits itself to agents capable of actions represented by the output of quantitative forms. The agents, upon their reception of the imagined value, validate the value through their group consensus, then takes some grouped sequence of actions based on the validation. In another case of use, imagined values provide "temporary immunity" to an acting agent in violating non-physical laws, rules that can be broken due to the physical potential but mostly remain abided by for some prescribed decorum such as social propriety. The "temporary immunity" dissipates after the acting agent has acted in some way resulting in the breaking of certain non-physical laws, and the agent is left to answer to the prescribed consequences of violating these non-physical laws.
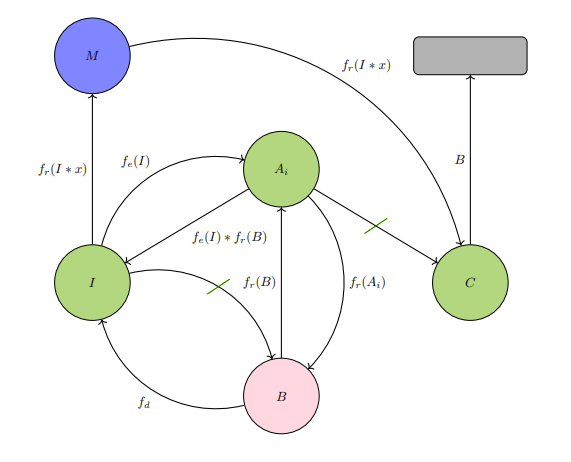
IM1: Wanted objective in automaton is activation of black box.
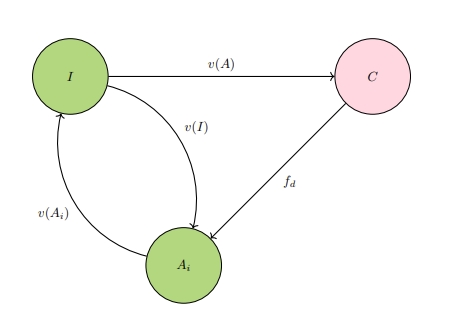
Only agent
Diagram IM1 starts off at imaginary value
IM2: Trap arrangement between Agent
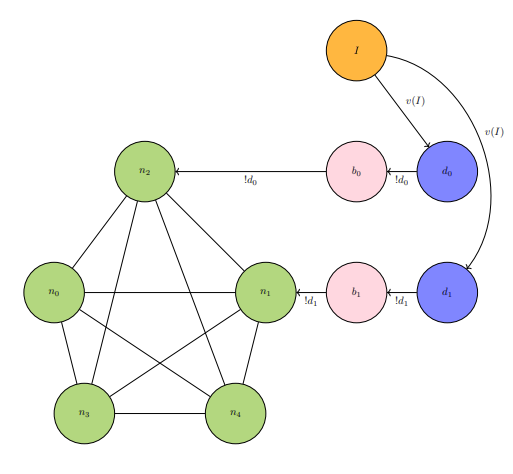
If
IM3: Closed five-star network has two vulnerable
ports, with agents
IM4: Adversarial agents
IM5: Imaginary value
Another area of noteworthy interest in which
imaginary values produce effects is reproductive
numerical structures. Two classifications of
structures capable of "reproduction" are vectors,
sequences of numbers, and matrices, sequences of
numbers structured into a dimensional format greater
than single dimension. The utility of imaginary
values could behave differently from the standard
imaginary number "i". As a reminder, the imaginary
number "i" follows this multiplicative pattern:
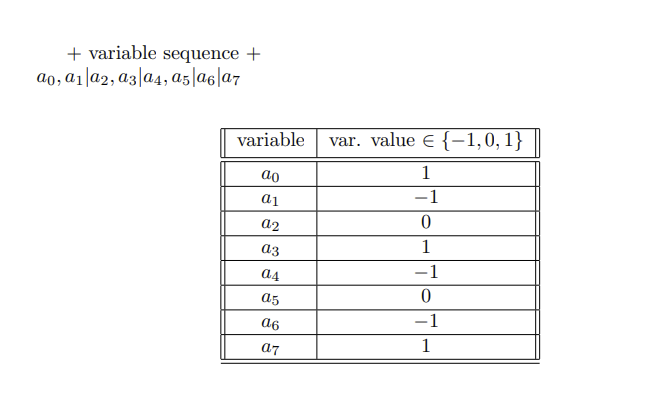
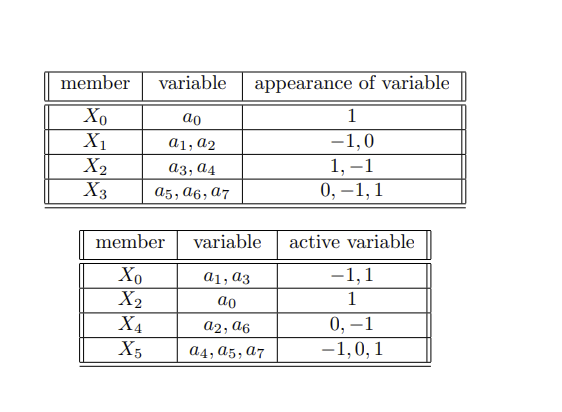
In this section's definition of reproductive numerical structures, every index of the structure is associated with a process function. Each process function has two components:
- a conditional function
- a reproductive function that is applied to some arbitrary indices of the numerical structure if the conditional function is satisfied.
This definition is rather scant and allows for practices open-ended in effects. The conditional function, for example, could involve more values outside of the number at the arbitrary index of focus. The reproductive function could add more numbers to the numerical structure, and in turn, modifies the size and possibly dimensionality of the numerical structure. The reproductive function also does not have to take effect on the same index/indices as those of the conditional function activating it. The "imaginary values" are the conditional functions. Activation of the conditional function requires the pertaining "real" value/s of the numerical structure to satisfy its condition. Upon satisfaction, the effect of the "imaginary value" is application of the reproductive function.
Connection as a continuity does not have a particularly wide opening for opportunity in a zero-sum world. The connection does or does not exist. There is no task of making connections, competing for connections, and reaping of the ruins after breaking connections. Any ideal recognized in totally static connections would remain that way. Any questioning or dissidence against the existence of these certain connections alongside predictable assertion (typically with an aggressive tone) for alternative connections that would split the two ends of said connections into their own non-intersectional paths is viewed as fools' follies. A disregarding and cold response would be in order. What defiance can outmatch the truthfulness of something very much like physical law? There is no will that has not been grounded by hubris, and what ways stay contained by the powers that be.
The consideration of fluidity in connective systems, which does not have to be mechanical or procedural, that are susceptible to fluid tendencies do behave in at least somewhat mechanical and procedural ways, even if the outcomes of participants may fare quite poorly with great variance against their wants and forecasts. Standard definitions of the word "alliance" will be explored, via network-like illustrations, of the broad branches by which fluid connections can express effect. Alliances are bodies of agreements between at least two entities. These agreements are evidenced and rationalized as granting benefits (positive or at least non-negative gains) in events that would produce disastrous outcomes if the agreements were not set in place to be executed for said events. First, some written mention of subjective but important questions is put forth.
What is the cost of making and breaking alliances? What premises, including non-physical properties, do alliances rest on? Are the premises that alliances rest on mutable not only in minor exemplification but also in stark differences of principle? When do the potential effects of some alliances catalyze to fullness in outward projection, and what are the default states and activities of these alliances? What is the reliability of an alliance under the hierarchy or overarching objective of an outside force? These questions are difficult to comprehend in the sense that potent (condensed) answers can be fallaciously originated for fullness in explanation. Competent attempts have been made, and continue to be made. Instead of relying on the broadness of philosophical abstraction, or the efficiency of mathematical formulae, these attempts take the form of fictional/fictionalized works exploring character/organizational dynamics, events and feelings that convolute social divides established in the "beginning", unexpected gains made by those less fortunate by birth but somehow gained the "throne" and legitimacy through acting off of their personal desires against hierarchical imposition, and direct acknowledgment of the fragility of the social order upon one person's violation of their people's socioeconomic code. Recurring themes such as the acceptance of unavoidable tragedies (coming up past the horizon) just to live and pursue the desires of the soul and mind for the moment, the breaking of state or tribal bonds in the name of a greater ends with promises outweighing what monstrous means are necessary or even enjoyable to pursue, due to some growing distaste for a crumbling society led by those still stubborn enough to acknowledge the decadence of conserving the original paradigm, are also well-represented in works of foreign lands that went through their own reformation processes. As brilliant and illuminating as some of these works are, there are underlying attitudes in the more anarchist varieties expressing scorn for some laws (predominantly social/legal laws), no need for any serious one to acknowledge them or their regulators in charge of them, and what acknowledgment is given to these laws is relegated to contrarian hooligans and anti-establishment charlatans, a fitting and unserious resistance. These works tend to also draw their primary source of narration from the temporal perspective: an attitude of "there is really no past or present, but things just are so let things be, let us be...". Lastly, sensuality and emotionalism taint the clarity of understanding the principles (a lack of principle is a principle in these works) that drive characters and events to narrative climax and conclusions.
To state that shifty and shifting alliances can be easily re-enacted through computational modeling will be expectedly challenged. Computational modeling does strip away a lot of convolution that is both "enjoyable" for readers of works, concerning shifty and shifting alliances, and horrendous for those that have experienced real-life events predominated by these types of alliances. Computational modeling does provide bases easily comprehendable, although there is the lack of "completeness" (closure) that is found in specification and illumination, and just as importantly, the egregious faults that can come with mishandling by misconstruction through the usage of these bases.
These two diagrams show two graph units that can be used to represent one entity.
SA1: Uniform graph unit, depicting an entity.
SA2: Hierarchical graph unit, depicting an entity.
The first diagram is a single node, a visualization of the wholeness of an entity under uniformity (attributes and values evenly dispersed). The second diagram consists of three nodes, with the blue node being the lead and the other two as sub-ordinate equals. These units for representing entities operate by "smart" network functionalities, exhibited by autonomous actions taken after appropriate objectives and corresponding training have taken place with the aims of reliably deciding on maximally-gainful choices.
Hierarchical graph units are predominantly used in conceptualization and calculations, concerning alliances, in the remaining of this section. There is preference for this variant of unit, used in this discussion, since it allows for more sophistication through its three-ness of an entity, and calculations involving three-node entities would also apply to one-node entities. Additional sophistication from three-node entities enacts effect from the structure's hierarchy (lead,sub-ordinates) and greater default connectivity (three-node VS. one-node) which, in turn, could lead to a scale of decisions multiple of those in one-node structures. There can, of course, be one-node entities with features (functions, programmatic rules) that enact hierarchical relations outside of the three-node model, but the vast diversification in this option oversteps the wanted base brevity in depicting alliances as changing networks. Innumerable network designs, for use in modeling automata of the variety that is connected systems (synonymously in this section, alliances), exist out of thin air. In order to contain the discussion in this section, there is no further mention of alternative models for graphical units, used as building blocks in complex connectivity.
Entities, by the hierarchical graph unit, can be structured as a "mesh", the connectivity signifying an "alliance" between entities. To clarify for this section's design, though, an "alliance" does not have to necessarily have to exist as a mesh. For there to be an alliance between two entities, at least one of two conditions have to be satisfied:
- there is an edge connecting one node of one entity to another node of the other entity,
- there is a node shared by the two entities.
MESH1: A mesh structure connecting 8 entities together. These 8 entities are "allied" with each other. The graph is entirely connected; there are no two nodes without a sequence of edges between them. Note the ambiguity in entities with more than one blue (lead) node. In these entities, there are "toss-up" procedures to yield the "lead" node. These procedures can produce different nodes for leads at different instances in time.
Suppose there is a central factor
MESH2: The same mesh network from diagram MESH1, with
an "alliance" factor
The entities
One category is change of rank. A new connection to a node of an entity can increase or decrease its rank with respect to the entity's remaining nodes. A lead node could become a subordinate equal to another, and vice-versa. Another category is change of alliance. Recall this section's formal definition of an alliance, with regards to graphs. A new connection from an "alliance" factor could severe existing alliances between entities. If there is a node shared between two entities, the entities may engage in a toss-up to determine sole ownership of the shared node. The defeated entity, now consisting of only two nodes, is a broken one that no longer fits the three-node definition of a hierarchical unit. But if there is only an edge shared between two entities, then only the edge is shattered, separating them two into their own "domains". A new connection to an "alliance" factor could also form an "alliance" between two entities previously not allied. The naming of these two categories of change is somewhat of misnomer. A change in rank within an entity could, in real-world applications, cause irreconciliable differences between the constituents of the entity that would impend on the entity's maintenance of unity.
Another important aspect to consider is the design,
intentional or not, of the "ripple" effect from the
new connection to the "alliance" factor. With open
knowledge, all involved entities are aware of the
"alliance" factor's activity. The "alliance" factor
produces changes onto the other entities not directly
connected to it, and these changes fall under the
categories mentioned in the previous paragraph, change
of rank and change of alliance. Probability curves
alongside pre-programmed rules and algebraic equations
are standard mathematical tools in use to predict and
replicate this kind of "ripple" effect onto networks.
In diagram MESH2, entities
Open and closed knowledge are labels with quite complicated solutions for perfect-information objectives, usually specialized and cross-referenced in real-world practices. There is, however, a concise principle on how entities may operate in open versus closed knowledge environments. In open knowledge environments, the entities know what new connections to "alliance" factors occur. In closed knowledge environments, each entity would have to deduce if there are new connections to other entities based on its independent observation of the other entities' operational changes. To elaborate, does the other entity output higher or lower quality values? Does the other entity "behave differently" to its peers? If either one of these two questions produce YES as answers, then there is a non-zero chance that the other entity may have established a connection to an "alliance" factor.
MESH3: A result from the changes produced from a new
connection to "alliance" factor
MESH4: "Alliance" factor
Some rules for "alliances" (for a jolly time, till kingdom
come) are in order. This table below maps the action that a
node takes alongside actions that other nodes take if
ALLT: Mapping for the behavioral effects of nodes, in alliance
MESH1, from connecting to "alliance" factor F. These are the
pre-programmed (premeditated, planned, declared,et cetera) rules
that every constituent of the alliance agreed upon if "alliance"
factor
Table ALLT shows the pre-programmed rules, in the form of
planned actions taken by nodes, in the advent of "alliance"
factor
There are less than ten nodes in this situation, and even with these simple rules, for there are no hard numbers or formulae telling how to proceed with "promotion" and "demotion", these calculations are not so simple as solving standard algebraic systems of equations. In this conceptualization, the base assumption is that if there was no "alliance" factor to begin with, then the constituents of an alliance would go about their procedures as put forth beforehand in their agreements constituting the alliance. The "alliance" factor serves as a body of sorts for the causality behind why and how an alliance can transform itself over time. There is no mention of what specific real-life nouns and verbs would act as an "alliance" factor. The subjectivity could really go on for a while from there.
A prime aspect to consider for constituents of alliances, in spans of existence where an "alliance" factor plays an existing role, is the dichotomy of expected VS actual. The expected would be the body of agreements put forth by the constituents as a collective, for the alliance. And the actual is how those constituents act on their pre-programmed courses of actions. A little cliche mention on the application of free will in these constituents' actualization: for an entity, does their taking a different course of action from that prescribed in the formation of the alliance demonstrate it to be "more free than not"?
So far, this section has focused primarily on the effects of some arbitrary force called an "alliance" factor onto an alliance, consisting of connected entities. Focus is shifted from the perspective/s of the "alliance" to that of the "alliance" factor. There is a game in play here. It is called the Game of Sliding Alliances, to be elaborated on after some mention on pertinent variables. The "alliance" factor does not have to stay connected to one single node during a duration. There are a few big tenets in the decision for one to accept the inviting connection from another. These tenets do rest in the realm of pragmatism; as an aside, the heart and soul really know no bound in expression from a statistical observation. The tenets are
- initial,median,potential gains as measurements of the prospective connection's functionality,
- initial,median,potential losses from establishing and maintaining the connection,
- risk assessment of the prospective connection, based on their
- historical records,
- reception from peers.
In the Game of Sliding Alliances, the objective of the "alliance" factor is to establish connection with each constituent of an alliance. The "one" mentioned in relation to the tenets previously listed is the current constituent of connection to the "alliance" factor. And the "alliance" factor can only be connected to one constituent, a node in the representational schema of graphs, at any single instance. Furthermore, for each constituent, the "alliance" factor is to accomplish some objective such as recreational experience (to set the start for long-lasting relations), gather information on the constituent (relations), and conduct exchanges (material/immaterial goods). Potential problems emerge for the "alliance" factor when they break connection to one constituent that goes against the constituent's expectations or interests, usually communicated to the "alliance" factor in some form, with the goal of transparency for their defined commitment to the connection. Equivalently, the same problems may arise when the "alliance" factor establishes a connection to a different constituent that results in a previous constituent's judgment of being disadvantaged in some form. A sub-challenge for the "alliance" factor would be for them to justify their decisions, that which may violate terms set by each of the constituents they proceed to connect to in this game. These justifications could rest on areas such as the "alliance" factor's default state of lacklusterness, a state understandable from a mainstream-rational perspective to be impossibly conducive to fulfilling set terms of agreement, as well as deficits in prior constituent connections. And if these justifications appear plausible to a constituent, this constituent feeling violated of the terms it set with the "alliance" factor, then the constituent may fold (yield way) to the decision/s.
Quantification is best implemented and continually revised for this Game of Sliding Alliances, after pertinent variables and their arbitrary orders of derivatives are accurately laid out. Vast subjectivity in real-life practices, including but not limited to stylistic preferences and stochastic decision-making principles, fall out of the bounds of rudimentary quantification.
Below is the Game of Sliding Alliances on six constituents with two entities.
GSA: A Game of Sliding Alliances. The "alliance" factor
has already established connection and conducted activity
with the first constituent of its interest, node
This section relies on the conceptualization of automata as Conway's Game of Life, invented by British mathematician John Horton Conway, to aid with describing possible deltas in "alliances", as depicted by graphs.
An almost universal envy is aimed towards those that have become sophisticated (many would say this trait is nurtured rather than inherited) and competent. These sophisticated and competent are complex to understand, their methodologies difficult for their friends and foes alike to understand, and their places in society probably unattainable by others through merit, since their existences supercede any rank declared in the formal hierarchy, static or mutable in its placements. Irreplaceable, brilliant, understanding, ambitious, admirable, honorable, a step below godliness these sophisticated and competent are. Some of their "friends" and "foes" whisper, amongst themselves, about how dangerous these competent and sophisticated folks are. The ones with more animalistic views nickname them "snakes", "eagles", amongst other high-ranking predatory creatures. Their bloodthirsty competitors think of them as a constant threat to their own well-being, even if they have never posed any physical harm to them. But as to their prestige and ranking in the eyes of societies' members that these bloodthirsty competitors lust praise from, said competitors probably feel they have big problems to solve. And these big problems revolve around these competent and sophisticated folks. The word "anti-elitism" is inaccurate to describe these competitors; there is no mention or explicit rule forbidding a bloodthirsty competitor from being, for example, an aristocrat or feudal head of a vassal army.
Sophistication is a process, and the products yielded from this process are not necessarily in line with the descriptor "elaborate". The word "elaborate", from a perspective, holds the meaning of something too broad and diverse for condensation that would preserve the identity of that something. For example, a person that conducts elaborate activity to woo another person of their romantic wants may, in actuality, not be very well-versed (the experienced as the sophisticated) in acts of wooing and seduction. The sophisticated are recognized as this label relative to their peers, peers that may fluctuate in identity over the course of different contexts. A person, recognized as sophisticated because they hold some unique ability to engineer proteins or to replicate DNA for cloning, may appear so to many people with other unique skills and talents, but amongst this person's peers such as their educators and workplace colleagues, they are quite unremarkable. In this case, it is the practice and products that this particular person engages in that is what is "actually sophisticated" from some people's recognition, not the actor that is the person.
The term "sophisticated" is somewhat intertwined, by mainstream interpretation, with elitism or a trait possessed by elites. Replication, ever since human beings have learned to industrialize, plagues the uniqueness that many aspirants hold as a second objective during their stages of sophistication. Scarcity, as a simple economic concept, becomes a critical factor in valuation of sophisticated practices or products, even if public market pricing is not to occur from the start. These practices and products no longer produce the same kind of aura after undergoing distributive processes, such as democratization (no additional comment on this term), that produce replicants of that which was originally labeled "sophisticated".
Sophistication does raise alarms from a defense perspective. This mentioned defense is not for those practices and products borne from sophistication. Rather, this defense is an antithetical stance towards sophistication, with great condemnation of its possible fruits that is the sophisticated. Popular questions include:
- "What is the need for this sophisticated product? How would I, from this background X with skillset Y, make use of this sophisticated product?"
- "What would happen to my welfare if this sophisticated product were to intrude into my domain of work/life balance?"
- "How should I go about accepting or rejecting this sophisticated product, since it clearly solves problems through its novelties, yet the public perception of it is clouded by controversy?"
- "What are my long-term gains and losses by accepting this sophisticated product into my daily life, in relation to my peers that may or may not accept this product?"
Sophistication, as a process in parallel to diversification and the decomposition of present-day mores and values, helps to spur changes in the form of "ripple"-like effects on activities and constructs spanning from the closely related (at the start of the ripple) to relations far removed by initial estimators. Hyper-specialization that is very frequently a trait of sophistication (although some that appear as sophisticated may have a forgivably shallow understanding out of lack of effort) bears its effects in a radiating fashion. The source that is the sophisticated, through this distributive process of "ripple"-like effects, is then held, in some regards, as the "ideal", the "origin" of all the changes attributed to this source. Security would have to anticipate how "ideals" such as these are somewhat direct causes of the bending and supplanting of existing rules/attitudes belonging to greater society. From a conservation perspective, with related concepts being legacy, promotion of alien competition, and invitation for hypocrisy, these nu ideals can pave the way for destabilization if not wholly "adopted".
Simple mechanisms for preserving the uniqueness of practices and products borne from sophistication processes include the well-known (maybe under different phrasing) "hole for the sophisticated". This "hole for the sophisticated" is a prime objective of strategies to contain the uniqueness of the sophisticated from public knowledge, which would then be used to replicate the sophisticated. And the replication would definitely be a force of competition through ironically supplanting the sophisticated, in a cyclical turn-based adaptation pattern. The sophisticated are to remain in this hole due to rationalizations such as greater society's poor knowledge of the sophistication process and as importantly, the utility of the sophisticated. In contexts of scarcity, mass desires to utilize the sophisticated may backfire on the mass, as a collective, as each have to outcompete their fellow contenders on the path to its utilization.
The defense perspective of sophistication now shifts to defending these processes under this label, and the practices/products from them. Some consequences that could be described as "weaknesses" from sophistication are exclusivity, higher rates of failure through a combination of less guidance and greater amounts of experimentation, and naturally less verification of methodology by peers fewer in numbers. And the sophisticated, when recognized, stands out in society in ways that garner reactions such as nuisances (maybe even threats) in some way, shape, or form to their privacy. Important questions to ask are: how risky is the sophistication process, and how fragile is the sophisticated from this process? The valuation, as numbers or descriptors supposed to be "objective", relies on calculations of the juxtaposition between the fragility (weaknesses) of the sophisticated and its effectiveness as a magnitude onto metrics that concern some objective/s. The beginning of this section mentions the "sophisticated and competent" as centers where envy is aimed at. The meaning of the word "competent", from a defense perspective, is the resilience against outside forces that do not approve of the sophistication/sophisticated in question. Can those that are undergoing sophistication stand up to the tried-and-true, those that may have nothing better to do than to challenge by interrupting their "transformations" or subverting their livelihood? If the answer is YES, then surely, the sophisticated and competent have something new to offer out of their reliability and unique strengths brought forward against those of the tried-and-true side.
To adopt sophistication processes and proliferate the sophisticated is a trade-off decision problem, these problems being very frequent in economic decisions. In some cases, sophistication processes yield no improvements that can be objectively measured. They are simply trends, different lines of thinking and practicing and producing, that may turn out to be cause for contempt from others that view themselves as the origin and the sophisticated as the diversified "children" challengers. These preferences for the sophisticated may prove to be superior to their more frequent counterparts. And their more frequent counterparts may be used more oftentimes due to their lower risk of failure in executing some task. Some ending diagrams show how sophistication may fare alongside long-standing and conservative approaches.
DS1: Two processes, a sophistication process denoted by
DS2: The conservative process attempts to disrupt the
sophistication process by maliciously targeting node
DS3: The conservative process discards its original
nodes
DS4: The conservative process attempts to take ownership over the proliferation stage of the sophistication process. The conservative process maintains its original components, and only intends to possess the product of the sophistication process.
With regards to inanimate objects that possess no autonomy to change appearance or expression to some third-party observer, the observer's judgment of the object as being sophisticated or not does not change due to the null actions of the object. The observer may change their judgment, presented in opinionated forms for this relativistic term called sophisticated, on this object due to relinquishing their own mental artifacts, possibly incorporating "ideals" from outside of their centrality, that have prevented them from appreciating the object for "what it is". These mental artifacts, from a real-world human perspective, include cultural, ethnic, psychological, and institutional (nation, league, club, field) biases. The object may not be sophisticated according to its measurements on metrics, firmly established on a basis recognized as objective in ways more inarguable than not. But the observer could still perceive this object as sophisticated due to their underlying cognitive mechanisms in judging what is greater than the "base", the "average", the "ordinary". A similar possibility exists in the vice-versa case. The object may be sophisticated according to some metrics, but the observer does not recognize it as such by their judgement that rests on their own personal measurements along these established metrics. A subjectivity "issue". If the subjectivity is to be called out as an issue by opposition, those that maintain a united vantage point on the object that is or is not sophisticated, then the notion of the "sophisticated" falls out of empirical standardization by simple logical consistency. In some cases, those with differing views on the categorization of sophisticated on inanimate objects may be excluded from these objects' official judgment proceedings, in order to both deter escalation of conflict by preserving subjectivity and give the object a secure basis of "grace and dignity". The problem of labeling, as a computational task, becomes very complex in terms of transparency and agreement when applied onto "preferential ideals", including the sophisticated.
Procedures to detect qualities with capabilities to appear and act in nuanced ways remain imperfect in a general context. One of these qualities is the effects of sophistication. These procedures may rely on a plausible sequence of detecting actions reliable enough (plausible through passing accuracy thresholds) so that changing of the sequence's components, in the advent of differing forms of sophistication, is not required. But each of the sequence's components may have to "calibrate" their characteristics to accomodate the differing form. Stark contrasts between procedures to measure any quality, including the sophisticated, may corrode the perception of some of these procedures' "accuracy". From a statistical perspective relying on frequency count, similar scores between contrasting procedures produce a stronger argument for these procedures' judgment outcomes. And differing scores encourage questioning on grounds of unwanted variability.
Some that recognize an other as sophisticated at the start, for initial appearances do matter in the context of a span encompassing the "beginning", the "beginning" possibly playing an outsized influence in overall judgment, may arrive at their cognition's own future conclusion that this other is "really not" sophisticated. There was a deceptive veneer used by them to draw others towards them. And when some objective, including a lack of objective, is accomplished, they exposed qualities that run contrary to the observers' rubric of sophistication. This rubric typically draws associations from traits,poses, and actions to highly-valued ideals. These associations are supposed to be, by the observer's notion of integrity of judgment, "accurate" in determining the truthfulness of some label (the sophisticated in this case) in the process of transformative appearances, that which constitutes the behavior that can be objectively recorded.
Before even considering some noun as sophisticated or not in their totality, as in their transformative appearances that constitute their behavior, consider the rubric to judge if an inanimate object is sophisticated or not as a non-linear connective process. The term "non-linear connective" is to describe judgments that do not entirely observe any single attribute as this or that label. Rather, the constituents of the object in question must somehow "match" together in arbitrarily-defined sets to form images consistent with some label. A term used to describe this way of judgmental processing is gestault.
TSBA1: The analytic function used to judge if the
object, consisting of the structure defined by green
nodes and its edges, is sophisticated. Function
TSBA2: A similar object to the one in diagram TSBA1.
There is a different rubric
There are two broad cases of judging if an object
is some particular label. Refer back to diagram TSBA1.
Suppose the object in diagram TSBA1 is labeled by most
operating agents of analytic function
TSBA3: Two probability distributions belonging to
two agents A and B. The probability values (on y-axis)
of the two distributions are scores for the "easiness"
of executing a decision (enumerated as a number on the
x-axis). These possible decisions pertain to an arbitrary
choice shared between the two agents. Examples of choices
include executing the next strike in a physical combat,
the use of specific words in a language's vocabulary,
and financial options for investment. In the first
distribution, Agent A has the highest easiness in achieving
the move enumerated as
In distributions TSBA3, an observer cannot determine
the "superiority" (higher quality, greater yield, etc.)
of any of the moves, enumerated on the x-axis, simply
by their associated agents' easiness of execution (y-axis).
Suppose, however, that the best move for Agent A to
take, relative to agent B, is move
The sophisticated are typically put into a light of stylistic ideal, at least in the beginning after their births. Due to the scarcity of what is recognized as "sophisticated", there are naturally less opportunities to demonstrate the effectiveness of the sophisticated over the ordinary, given the condition that the ordinary remains as the mainstream preference in both thought and practice. And even if the sophisticated proves superior along select metrics to the ordinary, the sophisticated tend to be put into conditions that garner low proliferation rates, such as through the "hole for the sophisticated" that is mentioned in the previous section Denying Sophistication.
| ~~ | Maintain | Work For Move 5 |
|---|---|---|
| Agent A | (20,-20) | (40,-400) |
SOPHIMP1: In this cost table, Agent A from distribution TSBA3 has the choice to maintain its composition, so that the probability values from TSBA3 graph one does not change. Or it can work for move 5 in ways that increase its level of easiness in executing the move. The pair-value of each cost is: (cost of effort in decision, consequences of pursuing decision). Agent A may not be able to afford to work for move 5; 1 x 2.
| ~~ | Execute Move 5 | Work For Move 10 |
|---|---|---|
| Agent B | (20,200) | (40,-400) |
SOPHIMP2: In this cost table, Agent A from distribution TSBA3 has the choice to continue executing move 5 against its competitor Agent B. Or it could stray away from actively focusing on playing against Agent B by working for move 10. The pair-value of each cost is equivalently defined to SOPHIMP2; 1 x 2.
In the two tables SOPHIMP1 and SOPHIMP2, both agents have a much greater likelihood of pursuing the first move (first column) in their tables. The markedly greater consequences of each of them pursuing the second move is a major factor in their choosing to conserve their compositions. The two agents A and B may fall into a pragmatism trap. The trap allows them to steer away from negative consequences, projected by each of them to occur in the advent of their attempts to undergo sophistication for moves difficult by their execution, through pressuring them into conservative cycles of action. These conservative cycles of action rest on resources and capabilities already conveniently available to them.
The section Denying Sophistication posits that there exists high envy aimed against the "sophisticated and competent". With only exactly one of these qualities fulfilled, there is not much of that same high envy received, so goes the posit. Intertwining the term "sophisticated" with those alluding to high-potential functionality, such as "competent", "effective", "powerful", "aggressive", and "prestigious" adds additionally explicit meaning around the usage of the term. The mentioned intertwined terms can be interpreted as related to the usage of the label "sophisticated", but without their explicit use alongside this label, there can only be implication that the correspondent terms are positively connected by some belief system, one with a probabilistic rate of accuracy. If brevity is the secondary aims of explaining this term "sophisticated", then its agreeable definitions make greater mention of the relation with ideals rather than with functionality. The notion of utility does play a real role of application in an ordered world, the order preserved and propagated through effective utility. So there is this rationale for delving into the term "sophisticated", due to what is labeled as such to potentially yield high contributions for practical advancement.
As mentioned in this section and the last, there is at least some overlap in usage of the term "sophisticated" with "elaborate". Whatever lines differentiating these two terms, whether fine or bold, do make mention of the essential nature of those labeled "sophisticated" and the others "elaborate". The "elaborate" tend to lack an origin, as perceived by third-party inspectors. The "elaborate" do not need to rely on any novel techniques to exist in their forms, but do require a greater-than-average number of layerings to present themselves in outward appearance. One feature of the "elaborate", already mentioned, is that they would lose their identity if they are to undergo condensation. The possibly greater effectiveness of the "sophisticated" in comparison to the "elaborate" is that the authentically "sophisticated" do rest on principles simple and reliable, while the "elaborate" are so due to the lack of obligation in their resting on an origin that is principle.
When products borne from sophistication do fail, it is due to the faults bred by the elaborate additions, additions that "hijack" control directly or through enablement of the principles simple and reliable bred through the sophistication process. It can be argued that the sophisticated do need to be competent, that the requirement of competency should automatically fall under those categorized as "sophisticated". And competency does require a high success rate in the control of principles simple and reliable, lest those principles be hijacked and re-engineered for purposes including subversion of the sophisticated, as well as repurposing the sophisticated against ideals and other nouns that it was intended to be aligned with, from its conception.
Entertain the notion of the sophisticated as inherently competent. The mechanisms of the sophisticated cannot be so simply abstracted by a singular framework. There is a need to use rudimentary structures such as networks and frequency tables to explore the competence of the sophisticated, however. It has already been stated that the sophisticated possess properties of uniqueness, and these rudimentary structures cannot possibly include all the specificities of this uniqueness. But they can model the sophisticated's mechanisms and constituents as functions relative to one another. From the usual standpoints of adversary and ally in relation to the sophisticated, these structures could be sufficient enough, from a systematic perspective, towards understanding the operational and constitutional workings of the sophisticated.
Assume the sophisticated to be a benign force, in the default case. They have no motive to initiate aggression against others, these others being sophisticated or not, in the form of exploitation and/or supplantation. This assumption may, of course, not be in line with real-life practices. No need for exemplification, but by the abstractions, DS1-DS4, provided in the previous section (Denying Sophistication), the sophisticated may believe it suitable to initiate confrontation with what they believe are threats to their lone existence and/or proliferation. This assumption is necessary, in this section, for the sake of brevity. If, for example, the sophisticated views another that sees the sophisticated as an adversary or ally opposite, then additional modeling rules need to be put in place; negative multiplication/addition rules serve as a good starting principle for these additional rules, but this added complexity requires extraneous explanation which the reader can independently construct. Important aspects to consider, in cases of the sophisticated that are not benign (in line with the other's alignment) from the start, are the underlying factors of this predisposition's causality, potentially much more complicated in calculation than the boolean rules of negative multiplication/addition. Recall the "hole for the sophisticated". This "hole" can be used as a mechanism for the initially belligerent sophisticated. The sophisticated would employ this "hole" for elaborate defenses against those they judged as adversaries, regardless of these others' views of them.
The focus on the question of the sophisticated now shifts from singular appearance, perhaps due to its inanimate nature, to transformative appearances that constitute the behavior of the object in question. From either an adversarial or allied standpoint, the first step towards approaching the benign sophisticated is to "discover" their constituents. This "discovery" process resembles the novel elements perceived during a sort of magnification, in other words, redirectional and intensifying focus.
DISC1: Stages of a "discovery" process onto
sophisticated object
Observe the sophisticated object
TSBAT1: Information for adversarial Agent A
to conduct attacks against the purportedly
sophisticated
Certain ways exist for the sophisticated
- The information on the effects by action of Agent A on S is inaccurate.
- The values are simply wrong.
- Expected effects from Agent A's attacks may not bear long-lasting relevance. For example, Agent A would have to choose moves that result in the constituent becoming exactly a null existence, instead of a "negative" existence. A "negative" existence of a constituent could, in turn, lead to respawning of the constituent back into its "positive" form, or to generate new constituents previously non-existing in the realm of Agent A's knowledge. These outcomes do reason to be arbitrary, but that would be because they rest on the arbitrarily-defined protocol of S not known to Agent A through to that specific point in time (the instance after attacking).
- There exists additional effects stemming from each possible move by Agent A. These additional effects present themselves as hidden layers of information not readily available, by analytical and intrusive capabilities belonging to Agent A. Hidden layers could yield additional effects from the execution of a move by Agent A:
- Opposite changes that can be nullifying or polarizing to the effect expected by Agent A, based on the information it has.
- Sub-constituents are yielded from the constituents (nodes) affected by Agent A's executed move, modifying Agent A's knowledge of S's structural composition.
- Affected nodes of Agent A's executed move modify S' surface of vulnerability to attack. Possible routes for S to modify include applying changes onto each of the constituent's strengths and weaknesses, and changing connectivity.
Agent A could undergo improvements to its knowledge base of the sophisticated in tandem with that of its moveset through the iteration of trial-and-error procedures onto the sophisticated S. But the sophisticated S, in a competent form, would not allow this progress of Agent A to pass by to disturb its balance. The sophisticated S also "evolves" its structural composition and operational mechanisms in tandem, so that Agent A's improvements would be at least matched by their "evolution" if not outright overpowered. Also note that in this elaboration of adversarial Agent A against the sophisticated S, Agent A does not "discover" the structural composition of S in one span of activity. Instead, it probably has to continually "rediscover" what S is, through trial-and-error procedures. An important note, on the endurance of S against the onslaught of Agent A's offense, is that S could be "destroyed" in a way that Agent A would not judge S, by some of its updated appearances, to be sophisticated by its standard. Yet, if the requirement of competence to endure is set in place, then the only way for Agent A to demonstrate that S is not sophisticated is by its "defeating" of S. In such advents, Agent A would probably label S as an "elaborate" adversary without the firmness of control over the origin of its operational defense, per se.
From the standpoint of an ally to the sophisticated, there would be actions designed and taken by the ally to be positively connected or integrated to the sophisticated, whatever that may entail.
The sophisticated are extremely difficult to replicate, as already posited. This does imply that they cannot be systematically dissected with ease for total third-party comprehension. Attempting to do so could led to the destruction of the sophisticated, such destruction leaving little traces for comprehending the existence of previous. Circular reasoning by third-party agents, especially adversaries, reasoning by the same incorrect methodologies in iterative fashion to no avail, is a frequent occurrence. And this circular reasoning is due to the limited scope of comprehension available to the agent, in which full comprehension of the sophisticated is understanding in ways that allow for it to be replicated and additionally improved. The available structuralizations belonging to third-party observers fail to produce accurate and meaningful relations to the sophisticated, in the exactitude desired for comprehension. There are paradoxies at work in this general context. The third-party agent, assumed to rely on relatively conservative (in relation to the sophisticated) tools, cannot comprehend the sophisticated without also imitating their structural and operational details. And the sophisticated, by their condition of scarcity and feature of competence, cannot be improved, but only elaborated on by attachment of extraneous features. The sophisticated do defy the faulty rationales that imitators, with half-knowledges of their ideal to imitate, fall prey to in their quest to imitate the sophisticated. The claim that the sophisticated have control over their origin (the core, the source, etc.) produces an expectation: the sophisticated have a greater likelihood of autonomy, stemming from its own design, in comparison to the elaborate but unsophisticated.
One last note on the distinction between the "elaborate" and the "sophisticated", without the ambiguity of overlap in gray-zone cases, is that the "elaborate", if weak, are weak by the symbolic inconsistency associated with them. These symbolic inconsistencies play a notable role in outsizing misinterpretation in execution (behavior).
INCON: A function
Suppose the wanted function is
TSBAT2: The first table lists the outcomes from
application of
TSBAT3: The first table lists the outcomes from
application of
The resources available to the elaborate determine
what function they choose as the differentiator
for some wanted variant function
One last interesting point to put forward is that the sophisticated are not necessarily also revered, and do become vilified/villainized in specific contexts. There are arguments for the validity in this point from the aspects discussed in this section and the previous (Denying Sophistication).
The topic of alliances is expansive. Causality and procedures pertaining to this topic have clearly not been touched in all, let alone in full, in the section Shifty and Shifting Alliances. Going so far as to attempt to explain the core causalities and procedures of alliances is also not sufficient in explaining the large leaps between the principle (causality and procedure) and application in the typical context of the real-world. This is a little disheartening to write. If causality's core can be explained, alongside with full detailing of procedures, then application should naturally have reasoning already known by this knowledge of causality, and the application would follow the frameworks set by the procedures. Application of principles, with regards to alliances, by sentient beings that may operate on non-deterministic, such as anti-deterministic, pseudo-stochastic, bases cannot be expected to understand any explanation of the core of causality, or to follow procedures for the correct contexts that is in accordance with prescribed extents (if they even exist). Alliances are a striving of many due to their promise of satisfying utilitarian needs, goals that could not be achieved otherwise without the necessity of a form of pragmatism, this form of pragmatism reliant on connectivity, that is, selective ignorance alongside choice initiatives for reliability in alignment. The discussion on alliances can very quickly shift to real-world applications, especially on the matters of diplomacy (localized, globalized, et cetera) and socio-economic constructs. Areas of focus for these applications, including but not limited to interpretability, capability, and compliability then fall under the prefix of "multi", a prefix with a default assumption of yielding probabilistic results stemming from universally agreed-upon "rules". This section is a continuation of the first part, and there is not a standout attempt to explore real-world representation by historical mentioning/rationale of specifics.
In Shifty and Shifting Alliances, two graphical units were put forth (diagrams SA1 and SA2), but only one of them, the hierarchical unit of SA2, was used to illustrate "alliances" affected by outside forces, deemed "alliance" factors. Each alliance is depicted as a cumulative product of hierarchical units. The mesh structure of diagram MESH1 has the feature of shared nodes between the hierarchical units and, as previously mentioned, there requires "toss-up" procedures to determine lead nodes in the structure, the alliance. Past the open-ended specificities of these "toss-up" procedures, one prime observance was on the connectivity of the structure after one of its constituents connected to the "alliance" factor. Certain connections, arbitrary from an unknowledgeable observer's point of view, shattered due to the involvement of the connected "alliance" factor. The specific reason why such events occurred is left to the reader's speculation, for connectivity between autonomous agents (assumed to be) is based on rules recognized as arbitrarily-defined. The principle, however, without detailing the reason for this principle, is that the "alliance" factor can alter the internal workings of an "alliance" after the "alliance" establishes contact with it. The illustration gives the impression to the reader that the "alliance" factor is similar to kinetic factors that result in changes onto surfaces they impact, so there is possibly that metaphorical misconception in interpreting it. Another prime observance was on how connecting to an "alliance" factor could change the hierarchical relations between the constituents. A lead node could be demoted to a sub-ordinate; a sub-ordinate could take the role of the lead. These two observances are fundamental enough to comprehend, but do serve as possibly complex courses of activity in alliances of a non-static organization. The section only considered single connections to an "alliance" factor. Without rigidly-defined rules for effects of an "alliance" connecting to an "alliance" factor, single connections sufficed in showing possible structural and hierarchical effects.
One benefit of exploring alliances, capable of anti-conserving internal activity, with the scant starting framework of networks, called graphs in the lexicon of mathematics, is that their beginning shallowness can be extended into more and more nuances, implemented in a layered (stacked) priority-based structure. The layering can generate exponentially more outcomes, these greater number and variety of outcomes to satisfy realistic probability distributions. The layering can also be fitted and calibrated to satisfy narrow spaces of possibilities. Countless mathematical proofs have been written to demonstrate that the structure that is a graph has these capabilities stated.
Suppose an "alliance" rests on a connection of expectations with an "alliance" factor. And this expected connection is actually many edges (connections) between constituents (plural) of the "alliance" with the "alliance" factor. This next example does not use the hierarchical unit of diagram SA2 due to the complication presented by their greater number of nodes to SA1.
MCAF1: Multi-connected "alliance" factor
The "alliance" factor
TASK1: Table detailing the expendable amount of
value for each of the five tasks capable by "alliance"
factor
DEM1: Table detailing the demand of each task's
value per connected unit of the alliance to "alliance"
factor
As this example is turning out, the "alliance" factor
does not have enough value in any of its tasks, save
for
Each of the connected units can attempt to "pacify"
the expected demands of some other connected unit/s.
This does read to be a sort of multi-feedback loop
where one asks (demands?) another to accept a lower
quantity of what the other claims to need. "Pacification"
involves such schemes of a unit's partial or full
prohibition of another's demanded value, forms of
declaring the other to cease and desist, and/or
persuasion of another, designed to appear as "friendly
redirection", to strive for other alternatives.
"Friendly redirection" of a unit with an unsatisfied
demand could mean for that unit to be open to or
seek new "alliance" factors that could at least
fully compensate the deficits of their initial demands.
If fairness for the connected units, in this context,
is to accept the maximum threshold value of each of
the demanded tasks belong to "alliance" factor
Despite each of the units of the alliance in
diagram MCAF1 being one of a non-hierarchical
type, the magnitude of their demands per task (see
table DEM1) do play a role in their rankings,
ordinal values signifying their prioritization
as candidates in the demand line, amongst themselves.
The unit
The mentioned concepts of prohibition and friendly redirection, as pathways for resolving supply-demand incongruencies, are next touched in illustration. The other mention of proportion-based adjustments is left to adherents' independent calculations off of this approach. Prohibition, by practice, takes the form of rules. For organized efficiency, these rules are structured into indexed formats such as tables. In this work's formulation of alliances, prohibition could take the form of pre-meditated reactive chains in anticipation of some unit/s violating some stipulation/s set by other unit/s. These reactive chains could be designed at some point in their relevant existences (before or during the need to execute) to self-modify during realtime (on the go) execution.
Prohibition rules are first put into a light of generality in this next table (PROHIB1). The category of "prohibition" for these rules is to mean them to be restrictions of flow (products, communications, et cetera) declared by one unit onto another. It is a funny term if oxymorons are to be thought of as funny, but the phrasing does serve a purpose in this section, and more importantly, in applications outside of this text. Oxymorons serve as confusing terms, this confusion caused by the understanding of opposite-ness between two "halves" of the terms that when combined, result in a lack of directed clarity. Rest assured, prohibition rules as a concept in this section are to be described with aims for full comprehension.
A prohibition rule is a condition by one constituent to another constituent of an "alliance", to be adhered to in regards to the allocating of resources (values of tasks) that originally belongs to the outsider "alliance" factor. Each condition pertains to exactly one task of the "alliance" factor. Rules do come in various forms. Some rules are circular, others bear strictness by practice beyond their phrasing, and yet still, others have hierarchical exceptions attached to their enforcement. Constructs discussed in this section, operating on the sparse definition of a prohibition rule previously stated, place the requirement that each "alliance" unit must abide by the prohibition rules of others placed on them. But the requirement could be broken to result in outcomes not ordinary to the conservation of the "alliance".
When hard numbers are the subject of decisions in prohibition rules, a type of condition called a threshold condition is used. A threshold condition is essentially one or more numerical ranges that pertaining numbers must fall in, in order for the satisfaction of that condition. Two classifications for prohibition rule conditions exist for thresholds, hard and relativistic. Hard thresholds are constant in nature, due to their attachment with non-changing quantities. On the other hand, relativistic thresholds are each associated with values that are compared with the input values in question. Here are a few samples of threshold conditions.
- Input
$x$ must fall in the range$[0,100)$ ; hard threshold. - Input
$x$ must be at most half in value to$y$ ; relativistic threshold. - Input
$x$ must be at most 3 more in value to$y$ ; relativistic threshold.
PROHIB1: Table detailing the prohibition rules declared
by each of the units connected to "alliance" factor
A probable problem with prohibition rules as a
square table, with no essential guidelines for their
conditions, is that there can exist contradicting rules
between the pertaining units of the "alliance". There
is then the necessity of a "toss-up" procedure that
determines what settlement is borne from these
prohibition rules sitting on top of internal contradiction.
For a set of
What are some questions that should be asked here? Think. Ponder on this, please. What kind of alliance would form only to issue rules contradictory to each other? Or... what kind of alliance could not resolve rules they themselves put forth? And ... how much jeopardy do alliances fall prey to in their quest to establish uniformly accepted rules for failure? For success?
There are fluxes in the "balance". The "balance" needs to be set to something better, a re-solution for the solution that no longer works. Here is an expression that works as a template for finding this re-solution.
In this expression, the function
MCAF2: A multi-connected "alliance" factor
The changes in connectivity between units of
the alliance are not illustrated in this image,
although edges (connections) between the alliance
units could be shattered. A kind of hierarchical dynamic
between the units
Weakly-connected alliances do not reason to be conducive to activity that requires the opposite of "weak connections". At least that much can be stated on the labeling of a connection as "strong" or "weak". The cliched reasoning is that it is not always the label, but the utility and outcomes envisioned by the user/s of the labeling that determine the power by achievement of some mark. In this section's showing of a multi-connected "alliance" factor, metrics of weakly-connected alliances can be gathered from a few of their operational attributes. Alliances with high degrees of measurable contradiction in their prohibition rules, amongst themselves, are weakly-connected due to the necessity for "toss-up" procedures as resolution intended to reduce the contradiction. These "toss-up" procedures could result in shattering of connections in the alliance, as well as changing relations of hierarchical nature between the units. Instability by lack of state conservation, in the form of changing alliance configurations, can be considered connectivity that is weakly-connected. Friendly redirection of demand from alliance units to more and more "alliance" factors also contains indicators of the strength of connection shared between the alliance's units. Many other points on connectivity strength can be conjectured, with the lack of certainty by lack of given underlying details, on how the lack of state conservation is a variable impactful by its broadness and depth into the workings of the constituents of an alliance. There is the perspective that if change can be adjusted to a constant level for "constant change", the "constant change" satisfies the definition of state conservation, but that is a matter that does not fall completely under the umbrella of this section. The semantics of conservation in supply-demand flows, authoritative chains of decision-making (hierarchical practices in great acceptance), and ideal references for correctness, when observed from their beginnings to outcomes "believed to be caused by them", do not exactly fit universal guidelines of state conservation; some would additionally argue that establishing universal guidelines for state conservation is antithetical to the longevity of their practitioners.
A weighted solution that encompasses all three of these pathways (prohibition, friendly redirection, proportion-based adjustments), meaning a procedure that assigns scales of influence with typical significations to proportion, is a viable option. Weighting schemes generate a greater if not equal number of solutions, due to their ability of assigning 0 influence or arbitrarily positive/negative influence to each variable (pathway). It is just that these schemes' essential principle is achieving correctness, by a reference that is deemed correct, via the calibration of the "weights" of influence connecting to each of the "cores" (pathways). If the pathways are not explicitly mentioned and reviewed for their relevance in qualities of relations and derivatives, then the weighting scheme can not be ensured to be a solution on stable grounds. This does read to be tasks for quantitative computationists.
A vector for the medium. What can come out of this vector, of wind harmless, is it, that is borne from what benign medium, empty and still if not for what children, its vectors of directed heir? There can be no difference then, supposedly, between a Great-Wind and a No-Wind. The medium that is harmless should output vectors also of that category. The magnitude truly of no matter, except for those of the condition to be impacted by it. A rationale on why this container, the medium, for possibilities not fully mentioned in sufficient definition is essentially harmless. But the proof of its harmlessness, from source that is input to its outputs by a particular basis able to transform into other bases, potentially yielding other outputs, is not found in this paragraph.
The Great-Wind's Restriction is a phenomenon of nature that is waged against at least one or more autonomous agents. The agents are autonomous because they do not have to act according to the will of the Great-Wind. Alternatively, an agent that acts in accordance with the will of the Great-Wind grants them benign treatment from the Great-Wind. The Great-Wind's Restriction is not harmless to these agents since it seeks to negatively affect the agents' autonomy, through force of derailment and resistance, and possibly as well as their existence. A lot of documents,media, and other truthful illustrations of nature have been produced. But for this session, assume nature to mean the forces outside of the control of the autonomous agents. Funnily, from the perspective of the Great-Wind, it is these autonomous agents that would be nature because it goes against its autonomy. As clarity in alignment, though, the Great-Wind is nature. A transcendental perspective of nature is that nature is what remains of what forces outside of the control of the central autonomous forces that have a non-zero probability of modifying the extent of its control. In this case, it would be the autonomous agents in the midst of the Great-Wind's Restriction. What these autonomous forces can control by their natural predisposition is not nature. In these statements made, there is implication of the nature VS nurture argument, another favorite by dichotomists seeking to differentiate between those leaning towards one end or the other of this argument and also those down the center lane.
The Great-Wind's Restriction is a reactionary force of antagonism waged by the Great-Wind against agents with autonomous capabilities, of its disliking. Regardless of superstitious beliefs and issues of interpretability regarding this section's description of the Great-Wind thus far, at least the point in the previous sentence is made clear enough. The Great-Wind is not exactly like a boa constrictor. It is an intangible lack of emptiness with its restriction. And it raises its demands every time its expectations, of demands imposed onto those of its disliking, are satisfied. For the disliking and the Great-Wind, one of them has to go.
GWR1: Depiction of five autonomous agents. The agents are in a confined space advantageous to their guarding against outsider threats.
GWR2: The same five autonomous agents from diagram GWR1. The green arrows emitting from each agent represent the agent's capabilities or assets, and should not be interpreted as only wanted navigational directions of travel. For example, a green arrow could represent an energy-recycling mechanism, auxiliary tools for communication, or next calculated steps in an arbitrary procedure. The blue connections shared between the agent show coordination/cooperation/corrobation of sorts.
Observe the diagrams GWR1 and GWR2, and their corresponding descriptions. The Great-Wind has decided to strongly dislike this group of autonomous agents. It initiates an attack in cycled stages against them. The stages are such:
- the smart-boa's constriction,
- the shadow's expansion,
- the observerless strike.
Although the last stage is the most impressive by the physically destructive impact to the agents, potentially past the point of their termination, the stage does come last.
The smart-boa's constriction consists of actions by the Great-Wind in its mimicking of the boa's predatory patterns and scaling up power according to its rightful resources after this mimicry. There are two primary labels for moves used in this stage:
- onion-based force,
- reactive-chain improvements.
In this stage, the objective of the Great-Wind is to incapacitate the capabilities of each of the agents, to restrict utility of their assets if not outright seize them. The Great-Wind intends to ensure that there is no longer viable probability in the agents each satisfying their objectives. During this process, the agents may find themselves to experience technical difficulties in meeting the marks for their objectives. They would expectedly shift their focus from their objectives, established before the starting instance of encounter with the Great-Wind, to escaping from or nullifying the influence of the smart-boa's constriction.
The onion-based force emits at each of the autonomous agents. This force consists of a sequence of onion-like pulses, each with self-modifying properties. Each of the pulses have a labyrinthian formation to them, designed to maximize the plight of confusing counteraction against the target agent.
GWR3: An onion-based pulse approaching an undrawn target from the left.
The multiple layers of a typical onion-based pulse are intended to detach the intended target of their assets by the vicious gaps between every layer of the pulse. The Great-Wind would expect, with a non-zero probability, that the assets would come out of the onion-based pulse from the other direction that the pulse emits at. The Great-Wind also expects this onion-based pulse to lock the target into awkward and expensive positions in such ways that they would not be able to execute their capabilities at their will.
The layers of the onion-based pulse could very possibly be undone, solved in other words, in the manner of one that escapes a labyrinth. The pulse is not designed to be entirely destructive against its target. The agent against the pulse could be torn up past the threshold to be labeled destroyed, but that would be due to the Great-Wind's overestimation of them. This first stage of the attack, called the smart-boa's constriction, is given the name because the Great-Wind has placed the stage as one to induce weakness into the agents of its disliking. The Great-Wind does this because it conjectured that the agents would not be fallen if it were to skip this stage and rush into the second and third stages.
So the onion-based pulse may fail in its objectives, to negate the agent's assets and capabilities from themself. Below are decision tables showing the choices belonging to an agent encountering an onion-based pulse that is impacting them.
GWRT1: Table showing the counter-actions the
Great-Wind's onion-based pulse
GWRT2: Corresponding table for the above (GWRT1).
Each non-zero element is a triplet of
In table GWRT2, the base value is the default gain and
loss from the smart-boa's constriction's move. The reversion
is the negation of the agent's corresponding move, the
action to the constriction's counteraction. And the
inversion is the "flipping" of the agent's move's
force into the realm of usage for the Great-Wind.
The inversion value cannot be greater in absolute
value than the input, the agent's move's force. The
Great-Wind could immediately apply the force from
this value back into the base, to decrease the loss
while increasing the gain by a wanted scale. Or it
could store the value back into its cache of resources.
Table GWRT2 is based on the assumption that the triplet
element is sufficient as variables in determining a
best move, where there could be more than one best,
for each move available to an agent
The Great-Wind, being as great as its name spells
out, would know all available moves of any autonomous
agent it decides to antagonize. The Great-Wind also knows
exactly what move the autonomous agent would take for
the next timestamp. In game theoretics, these two
abilities of the Great-Wind are perfect information,
on and surrounding the autonomous agent's possible
moves, and real-time acting information on the
actual move that said agent attempts. A formula
equipped with the feature of varying the output, given
the same input, is used by the Great-Wind for an
anticipated move
For the anticipated move
Most autonomous agents would not have the same luxury of knowledge, perfect information and real-time acting information, as the Great-Wind. Each agent calculates their moves using tables similar to that of the Great-Wind. These next two tables show information on moves that Agent A, from tables GWRT1 and GWRT2, would take.
GWRT3: Table showing the actions Agent A can take, during the stage of the smart-boa's constriction, given each move by the Great-Wind's onion-based pulse known to the agent. In this specific example, Agent A has perfect information of the onion-based pulse's moveset. It does not know what move the pulse will take. This table's non-zero elements comprise the complement to the table in GWRT1.
GWRT4: Corresponding table to table GWRT3. Each
non-zero element is an
Table GWRT4 is lacking in specific detail. Depending on the complexity in solutions that is the moveset available to the autonomous agent, the dimensionality of values could be very high in number for one or both of the (offense,defense) values.
Some important underpinnings about the terms on the onion-based
pulse's decision, that is "inversion","reversion", and "base",
and for the autonomous agent, "offense" and "defense", are
clarified next. The values concerning the terms of the
onion-based pulse are already finalized in the table. There
is a zero probability that any value for any triplet
Cases of agent moves uncounterable by the onion-based pulse are relatively easy to detect in move tables (see tables GWRT1,GWRT3). Any 0-column (all elements are zero) in pulse-perspective tables point to the agent's move for that column being completely uncounterable. By the agent-perspective tables, any zeroless-row is for a move uncounterable by the pulse.
GWR4: Image showing layers of a portion belonging to an onion-based pulse. The portion is numbered in descending order, where the closest layer to the agent is denoted by the greatest number.
The agent that has to deal with an onion-based pulse attempts to go past the portion that hits them. In diagram GWR4, the only possible destinations for escape from the specific portion (there could be more) would be above or below the portion, that is, outside of the portion's scope. Trickily, travelling past the 0-layer may expose the agent to another portion of the pulse, or a separate onion-based pulse, thereby continuing the risk of seizure of its assets and damage to its capabilities. They may discover, through their experience, that they cannot make cumulative improvements because the gains from their efforts cannot be retained. They may oscillate between layers near and far. This oscillation of sufferance is one example of the reactive-chain feature in use at this stage, the smart-boa's constriction. Factors include inversion, turning their energy against them. Reversion obstructs them. And there is also the base force of the pulse's move. To no avail for them, so goes the Great-Wind.
Energy is a pertinent issue for both the Great-Wind and any agents of its disliking. Energy is a private variable between these two, the Great-Wind and the agents. The agent/s, if more than one, may choose to share details on their energy with each other. Meanwhile, the Great-Wind does not know what energy, the maximum amount of exertion per agent, and the agents do not know to what extent of effort the Great-Wind has at its disposal. Energy for the Great-Wind becomes an allocation problem. It must calculate the energy allocated to each onion-based pulse it emits. Additionally, this quantity of energy is not merely a singular value, but one that includes the reactivity of the pulse. Pulses can modify their formation by use of its energy that it cannot increase on its own, without the addition of inverted force from the targeted autonomous agent. The amount of force each pulse gathers from its traversal against an agent, that is inversion in accumulation, serves to be recycled back at the specific location the agent was at, in a different portion of the pulse, or directed outward into the Great-Wind's store of energy.
To make matters worse for any autonomous agent that has to solve an oncoming onion-based pulse, the pulse does relay information on the reaction-chain of events, the actions taken by the pulse and the agent during the duration of activity, back to the Great-Wind. This relaying of information is the fundamental aspect of the reactive-chain improvements. The pulse may die out, with no energy left, due to causes that involve the superior performance of the agent against its actions by its design. On the other end of possibilities, the agent may lose their assets and have their capabilities restricted by the pulse, and the cause of this does not necessarily have to do with their bankruptcy of energy. If the agent manages to solve the pulse, the smart-boa's constriction takes the information, gathered from the activity in the pulse, to improve on its design of the next onion-based pulse it emits to the agent that remains.
GWR5: The five autonomous agents, from diagram GWR2, after unsuccessfully fending off the smart-boa's constriction.
The next stage in the Great-Wind's restriction, the shadow's expansion, is action to reach levels acceptable enough for some important metrics. These metrics are adversary detection rate,effectual imprecision rate, and exit reduction, terms that have been applied in real-world settings before, usually with very high disregard for totally positive outcomes of those engaged. Pertinent calculations cater to the specific application. No specific instances of these applications need mention, but the prevailing practice of these calculations is to elevate the power of chaos. There are no formulae prescribed in large for chaos, especially for those that are to be subjected to it.
GWR6: A networked-detection system for the autonomous agents in the example from diagram GWR2. Each element of the system is a beacon that receives accurate information on what adversarial threats exist in its proximity of finite specifics.
Adversarial detection systems operate by two objectives: accurate detection and timely communication of the detection. The diagram GWR6 is one example of an adversarial detection system operating in the enclosure specified by the dashed lines. They are in charge of maintaining and delivering timely knowledge of threats detected to the five autonomous agents from diagram GWR1. The adversary detection rate falls during unreversing progress made by the shadow's expansion.
GWR7: The networked-detection system from diagram GWR6 after it has been affected by the shadow's expansion. Green nodes depict nullified elements. There are exactly two communicative lines remaining.
The effectual imprecision rate increases during unreversing progress of the shadow's expansion. The term "effectual imprecision" refers to the correctness of a proposed solution given the actual solution, such that there are more proposed solutions that are correct with the increase of effectual imprecision rate. Two illustrations, of an abstract description, demonstrate the growth of this metric.
GWR8: Red circle is the growth of effectual imprecision.
GWR9: Green nodes are viable solutions after the growth of effectual imprecision. Every green node would be a correct solution because it leads to the original solution, the blue node.
Exits can be abstracted into geometric understanding. In transmission design, for every enclosure, there should be an exit, the exit perhaps the same as the opening if there is only one opening. Even for verbal arguments, nonphysical by definition, there is the exit of refraining from more argument by one or more parties. The Great-Wind aims for exit reduction, the minimizing of number of openings for autonomous agents exiting out of the situation with the Great-Wind.
GWR10: The enclosure in the first diagram has less openings after enduring the effects of the shadow's expansion. The second diagram shows the enclosure of previous, with many openings to allow for escapes and inconsequential corrections in formations.
After the achievement of the shadow's expansion, finally, the observerless strike comes. The Great-Wind does not cycle through the stages of the smart-boa's constriction, the shadow's expansion, and the observerless strike on any occasion with honest observers remaining to tell the tale. There have been many that have attempted to replicate and perfect the Great-Wind's Restriction. Some found themselves to encounter mortal failures.
Idioms are very well-known statements, crafted by those that have gone through some experience, usually indescribable in full, that yields some insight of interest worthy enough to garner a following of sorts. The following preserves the statement that survives the trials of time well enough so that eventually, some time after the statement was made, there is the recognition that it is an idiom, a statement with an almost omnipotent chemistry of truth,wisdom, and strength through reputational survival.
The subject in this section is tied to the section How Obtuse Judgments Can Count. Why would a communicative entity use an idiom in an arbitrary context? Is it ... because the idiom has positively contextual relevance to that context? Whyever else would the idiom be used? Because the idiom is an idiom due to acceptance and proliferation cumulatively established over quite some time, the usage of the idiom radiates relevance onto the context in such a degree that, by its own distinctive reputation, transcends the importance of the context for the connection, yes? Sure, the idiom and the context do not have to perfectly fit, for the connection. For one thing, the idiom is a principle generality and the context is details. The idiom is applied to the context to filter out the covers of misconception, streamline the details into shorter tidbits made more understandable, with the purpose of using this re-versioned context as the actual groundwork for furtherance in action. Nothing could possibly appear wrong by the metric of high accepting judgment belonging to those involved in the context that is ascribed the idiom, for their positive clarification recognized by their judgment.
The effects of the idiom present themselves in two aspects of importance, in the temporal sense relative to the occurrence of an event or sequence of events, and as a tool by the "originators" and the "adopters" who incorporated it after.
There are questions concerning the "birth" of an idiom, this "birth" not singular as in one point of time, but many through the transmission of many minds, usually from many tongues, perhaps many books in societies that have industrialized non-auditory communication. If the idiom is a material object, though only in a bizarre world, it very well could pose as one of the material wonders of the world. The idiom that comes after the sequence of event/s is a hindsight. This hindsight may be an epiphany not yet formalized into that which is the officious idiom, or it could be a reflection which reinforces the idiom as the source for frequent reference, with the actual truthfulness by accurate correlation on an accepted axis of understanding left up for question in the specifics of the context. The thought, expressed in terms of advice, on events in a future near or far given what is available by judgment through perception and beyond thus far, is a premonition of sorts. The thought is expressed with certain kinds of undertones intended to signify premonitory wisdom and visions of the future granted from the energy of the past. If the thought is already well established in terms of use and adherence, the thought is an idiom. If it is not an idiom, but it proves to be correct from the judgment of those that have been transmitted the thought from others before passing through some pertaining events that was the future, then there is the confidence of belief by the participants transferred to the credibility of the thought, a possibly eventual idiom.
The idiom is ushered to uphold confidence in an applicable future at elevatable levels of motivation, with regards to some action planned to be taken and with rationale that rests on it, the idiom. The idiom ushered afterwards is used as clarification on what mistakes in thought or action occurred. There is the "if the idiom was taken as the wisdom before the action, the mistake would not have occurred." Additionally, the idiom does not have to focus on clarifying mistakes in thought or action, to clarify; rather, it can well serve as a rationale for the inevitable, in place of the incomprehensibly scientific explanation.
IATI1: A body of information, with every variable having an inverted version of itself.
Diagram IATI1 is a geometric visualization of a body
of information structured in the manner of a triangle.
The two bottom ends are those for the polar extremities
in views regarding a topic. The other end, at the top,
represents a central perspective. Every
IATI2: A split onto the same body of information from diagram IATI1. The split neutralizes all variables, by the comparison of the two resulting halves.
IATI3: An erroneous split onto the body of information
from diagram IATI1. The split neutralizes only variable
There are some ways to validate performing a split
that results in remaining variables, such as in diagram
IATI3. One way is the rather classic weight-assignment
approach. Simply assign the weight
Diagrams IATI2 and IATI3 show the same body of information, but are under non-identical idioms. The changing relations between the interpreter and the expressor of idioms, due to the psycholinguistic underpinnings of natural languages in spoken or written forms, place unspoken demands on what relevance the topic is in relation to the inarguable greatness of the idiom, by its statistical frequency grown through legacy. The idiom could be used as a commentary statement on the deterministic way in which some events transpired, for instance. To elaborate on this, there is the sentiment that things may have seemed different, but because some of those things have relations with some of the aspects of the idiom, then the outcome of the idiom and of those things, with details maybe out of line with any of the idiom, are one and the same. As a result, the idiom persists, as strong as its accumulated acceptance continues to allow it. The expressor of the idiom lends themself the image of the legacy's truthfulness behind the idiom. This aspect called the truthfulness of legacy is a boost in the believability, that is confidence, of the idiom's attachment to its application. The idiom, as a label for a statement, is not confined to the roles of positive or negative application. The idiom does not have to be an encouragement for some wanted future. Instead, it can be a planned future's discouragement, to steer the reception to an alternative future after the hopeful change of their decisions. The idiom, past the events, does not have to be an insight of wisdom that can help for a brighter future. Instead, the idiom may just as well be a statement on the darkness, the tragedy of how events played out without the guidance of the same idiom if considered before all the happenings. The expressor of the idiom does not have to be a steadfast practitioner of the idiom. The expressor may express the idiom after the overcoming of their doubts, through their experience, on the idiom's truthfulness. The steadfast practitioner employs the idiom in the manner of their own construct regarding justice, and as such, does not find the task of contradicting the idiom through their expression of open acknowledgment on the idiom's shortcomings to be pleasant. And there are also those that enjoy expressing idioms half-heartedly, perhaps posing as fully-forward in physical appearance to maintain credibility by others' beliefs, due to their shortcomings in understanding or a desire to not reveal some topic in full. Some users of the idiom may hold the objective to be as great as the tool that is the idiom, when they are, in fact, those in control of the intangible tool that must cross their mind before the tool's outward expression. From a pure utilitarian perspective, that which emphasizes the effectiveness in usage above all else, the user can be only as great as a combinatorial fusing of the greatness of the tool and the tool's use. In the curious case of idioms, the psychological effects of language, when considered as transmissive elements that can then fuel autonomous decisions for futures not dared to be taken without that fuel, is certainly an objective for some in their ongoing duties to maintain their image by the continuation of power lent to them from the idiom, the tool, that they use.
Continuing on the discussion of the idiom in the temporal sense, maybe the outcome is the only "thing" that matters to the participants of the idiom. There is the primary expressor/s of the idiom, and then the followers of that idiom given to them by the expressor/s. There is the sentiment, to go against the "ultimate meaning" of the idiom would not bode well for the participants, despite what given information and corresponding conclusions can be made. There is no proof of what is yet to come. Rely on the strength of the idiom that already exists, due to its merit survived and grown through legacy over time, or fall back on nothing as guidance, instead having to resort to chaotic, risk-taking, and formless efforts to succeed at the objective.
IATI4: Triangle represents the hierarchy of a
set of participants, denoted by variables
Diagram IATI4 shows a different model, regarding idioms, than that of diagrams IATI2 and IATI3. The model is an objective-based model that uses the triangle as a hierarchy of participants. The model's triangle in diagrams IATI2 and IATI3 serve as containers of information, the information to be rationalized by splitting said container. The diverse number of models available to serve different aspects of the same problem, or the same problem itself, is a testament to the plasticity of model-based decision-making. If one model does not suit the wanted objective, another model would be used if there are no restrictions on what models are used, only the expectation that some outcome is successfully reached. Usage of idioms in cases such as in diagram IATI4 are to manipulate confidence towards efforts previously unconsidered. As such, models such as these are questionable by their strength's reliance on manipulation of will and whim, instead of providing fact-based information to autonomous and independent decision-makers.
Definitive explanations of why the confidence in something, such as the idiom, is a modifiable trait in belief (intrinsic possession) by either the expressor or the participants falls on variables outside of the scope of specific clarity. The relation between perception and judgment has been talked about in the section How Obtuse Judgments Can Count, but there are certainly questions remaining on the infinitesimally material components involved. There are a few areas in the high-level context, such as the outcome of the actions taken by participants under the idiom, and the participant's volition, under variable circumstances, to "break free" from acting under the idiom. Some relations are in need to be stated. For the outcome of an accomplished objective, there is a validation of the peak: the idiom stays true to its reputation as a truth, the expressor is righteous for utilizing it, and the remaining participants fare well in some shape and form for obedience to the idiom that is passed down to them from the expressor. Perhaps even in failed outcomes or outcomes labeled victorious but with grievous casualties of sorts, the decision to use the idiom as the launching point of action (refer back to diagram IATI4) could certainly still be justified. High-priority members of a hierarchy, including the expressor, would attempt to persuade those underneath, befuddled by the platitudes in details of variance amongst their references and themselves, that what actions that have taken place under the idiom and for the objective is reasonable, and thus righteous, even with whatever losses occurred. A step further in pacifying what remains of the unity of disbelief surrounding the idiom would be to declare that those disbelievers failed to uphold the idiom, and this is evident due to the results obtained.
The "originators" and the "adopters" of the idiom are defined not as absolutes. The relation between those that are the "originators", first to know and use the idiom, and the "adopters" that were transmitted the knowledge of the idiom from them is one of ordering. The originators are labeled this in relation to those. Practically every entity is an adopter, in some degree, to the idiom that has one or a few "originators" at its birth. The idiom grows by retention of users, as already noted. Then the idiom reaches a point of equilibrium in the number of adopters. Historically, the idiom is of a regional existence. The idiom is used in the manner of a cultural identifier. Those of a certain region may have knowledge of a particular idiom in their early years of existence, so think that idiom to be natural as a mental construct for rationalizing about their experience, such as their social interactions and perception of surroundings.
After the idiom has reached an equilibrium in scale of adoption, there may be newcomers that proceed to using the idiom after they themselves adopt it. The idiom, in its domain, is first learned by the newcomer in the newcomer's quest to learn more and "fit in" with the domain. The newcomer adopts the idiom, then uses the idiom in the manner of an entry point, from one stranger to another bound by the medium of trust or similarity that is the idiom.
IATI5: Domain of the idiom is the square enclosure
marked by
The newcomer that adopts the idiom is motivated by the fact that using it would serve as a shared commonality with members of the idiom's domain. The idiom is frequently thought of as a middle ground for newcomers' gaining entry, since it is above the nicety-basics of communicative interaction, yet below the jeopardizing risk of private matters. Surely, the idiom is upheld there in its domain due its reception of great esteem by the members of the domain. For the members to take offense to the idiom's utterance, even by a newcomer, would be to disregard the unifying influence of the idiom as a top priority, and instead to focus on the newcomer as a suspected antagonist. Meanwhile, the newcomer takes care not to partake in behavior or other appearances that may lead to some that are not the elites, the authorities that uphold the idiom as the ideal that governs one of their institutions or their society overall, to suspect the newcomer of harboring malice of some sorts. The newcomer uses tools such as idioms in their attempt to participate in the shared sense of belonging in the domain.
Extending out of the scope of the idiom as an introductory tactic by the newcomer into a domain, the idiom acts as a bonding mechanism between two or more people. The idiom becomes the first and foremost shared commonality between them. From the acknowledgment of the idiom from the two or more ends, interaction builds on this trust to become more personalized and also privatized. There may come times when relations between two or more entities are tested by adverse events. And during these times, the entities may very well fall back on their shared commonality from the start, the idiom that gave their relation the chance to flourish.
IATI6: Progression of two agents
There is not much to be discussed on the term "idiot". By many accounts, the term "idiot" means to describe one that is not a participant in whatever process is of vital essence to something of an important caliber, at least in the official sense, such as politics. For one to describe another as an "idiot" may be not an insult whatsoever, nothing more than a differentiator between those who strongly or actively seek to participate in some process and those that abstain or are excluded. With idioms, suppose an "idiot" is one that does not participate in the thinking behind the expression of an idiom, not the one with the motive for an action or acknowledgment. Instead, the "idiot" would stay silent and obey the expressor of the idiom. The "idiot" would be the one that accepts the consequences stemming from the faulty use of an idiom. Also, the "idiot" would nonchalantly accept the riches and spoils from the wins made by activity under the guidance of an idiom. Perhaps the "idiot" alongside the idiom is one that does not recognize the essence of the idiom in applied contexts. There is a mismatch when the "idiot" is coupled with the idiom. Something is expected to go terribly wrong. The "idiot" could involuntarily commit error. The term "idiot" does carry a consequentialist aura on the "idiot" as the sufferer that may spread their suffering to others that would not be thrilled to experience losses not of their own doing, due to the "idiot"'s apathetic behavior and attitudes towards fundamental activity, that which relies on principles such as idioms to thrive. But the translation between words and actions do muddle the recognition, beforehand and afterwards, on what idiocy truly is. The one that is ascribed as an "idiot" because they are not the expressor, the ideal, the representative of the idiom could actually have put or be putting their efforts elsewhere for effects far greater in gains or losses than words as powerful in legacy as the idiom.
A common line of reasoning persists in many activities demarcated by start and end points. This line is the input-output expectation, reinforced if not derived by scientific laws surrounding the zero-sum condition of energy: what efforts and materials go into an "outlet" must come out of the "outlet" in ways that are equal to the input's totality, but open to changes in form and expression. The openness to changes in form and expression allows for dashing of the expectations for the output. This section observes some aspects in the way efforts are manifested by forces such as the acting agent of those efforts and others outside of the direct efforts in action taken.
One major area of focus is operational efficiency.
The objective behind this form of efficiency is to
reduce expenses in work and material, with regards to
defined activity, below a threshold to an expected
optimal level. From this central problem comes
other related problems, to be gradually mentioned.
In this first context, there are an arbitrary number
of tasks
HEFT1: Three tasks are split between five
workers. The average amount of completion towards
each task is
If every task
Function
A "fair balance" could be established to resolve this
issue of preferring one over the other. Establish a
value
EQW0: The weighted-work requirement inequality.
Another dimension regarding work in the practical sense must be considered for a comprehensive overview. Payments. Payments usually take the form of an established currency. If payments are not in the order, then the work that each worker contributes to the demanded tasks, not necessarily the efforts that they expend, is what they are paid in as a direct result of their efforts. The workers could certainly barter their products, borne from the work, for other products if currency is not allowed. The exchange rate in these situations is arbitrarily-defined, and barter has historically been used in place of a lack of commonality, between two or more entities involved in the process of exchange, in judgment criteria more layered than direct material.
On the matter of payments, there are only a few broad approaches that are possible. Payments do follow some guideline that pertains to the concept of ideal proportionality, and additionally is along the lines of the base scientific principle of input-output expectation. Payments of currency are an externally-sourced gain for the receivers. The source of the currency received by each worker is not physically tied to the efforts that they expend. The source of the currency may belong to the organization that each worker is a part of, such as from a financial officer. But the financial officer is also somehow tied to the authorities of the currency issued to them, the officer, for them to transmit to their workers as payment for their work.
Payments could take the form of a flat rate, that is,
according to the time spent working. Every worker,
regardless of their individual contributions to the
completion of each demanded task, is paid the exact
same amount, given the condition that they all work
the same amount of time. Payments could also take
the form of a weighted rate that takes into consideration
each worker's individual contribution, such that
their greater magnitude in contribution results in
their being paid more. Again, these two approaches face
the same issue as the previously mentioned functions,
EQW1: The weighted-payment requirement inequality.
Inequality EQW1 is a preliminary attempt to resolve
the question of payments. Each worker
There are some concerns on the metric of cumulative
product from work, previously mentioned as the generic
function
Collective bargaining, by the workers, consists of negotiating activities to guarantee minumum and/or maximum thresholds on variables deemed important to worker livelihood. Payment and insurance are two of the highest-ranking variables on the long list. This form of negotiation is a universal approach in social-based systems, albeit the goals and terms of this negotiation do possess the risk of failure through generalization of individual expectations and unaffordable burdens on the support system that is responsible for upholding said terms for said goals. There has been much scholarly research into and practice of collective bargaining in work settings, especially those of material goods production. Depending on the ideological style of the socio-economic administration above the workers in authoritative command flow, collective bargaining is one of the foremost methods in negotiation, due to the emphasis on reaching and then maintaining a flat line with respect to the variables of worker livelihood. Those workers that find some of their demands in work to remain unmet or entirely discouraged by the outcome of collective bargaining have degrees of freedom in their proceeding actions that strongly correlate to the expectations and potential force of their socio-economic administration. A review of the ideological and political favorings that socio-economic administrations have attempted, historically up to this day, falls outside of this work's genericization that is to not reach into the depths of hyper-detailed happenings and arrangements comprised of ethno-national,cultural, and regional tints.
Collective bargaining observes some variables worthy of mention:
- each worker's expectations (demands) of their assigned work,
- qualities of each worker's output, including their energy expenditure (effort), contribution to the completion of the task/s, and maximum capabilities,
- negotiated terms of collective work expectations
- qualities of each worker's output after implementation of collective negotiated terms,
- effects of each worker's expectations (demands) that were unmet due to the collective bargaining process.
This section now turns to the label of workers as being specialized. Work, as a general term for efforts expended to accomplish some arbitrary objective, cannot be thought of as a sequence of efforts to be taken by a physically capable entity. This thought as an equation lacks that very frequent term used to gauge the effectiveness of a worker. That very frequent term is "experience". The reasoning is, without the experience that is vital to the successful execution of the work that is to be done by any physically capable entity, that entity could not accomplish the work. They may "know the form but not the way", or they may "know the way but not the form", and as a result of their satisfying one but not the other, they cannot do the work that is specialized with respect to their ordinariness.
Refer back to table HEFT1 on the worker output of three
demanded tasks. All of the workers are expected to be of
the same status, even though the word "status" was not
explicitly mentioned. This idea of the workers' equal
statuses to each other comes down to the mean expected
contribution they are to each output for each of the
demanded tasks. Contribution to each of the demanded
tasks, by all involved workers, also implies that
every worker is capable of accomplishing each of the
tasks. But the values in the table tell something
else from their variance between each other. Workers
A frequent underlying drive to specialize is the situation
of worker overflow, a problem that takes forms in reference
to the input and the output. In one form that is the constraint
of input sources, suppose there is a task
A related category of work to worker overflow is the
permutative work process. To exemplify, for
a task
- rarity among their working peers,
- initial aptitude to be placed on the specialization pathway, alongside the rigor in standards for their recognition as a specialist.
Trials and errors may have needed to take place to "pave the way" for the area of specialization to become recognized as the objective. Organizations with objectives to specialize do restructure their form and purposes to suit these objectives, with questions on their successes remaining.
The idea of half-efforts, full takes has been demonstrated in one form, the equal-outcome expression that enables workers to stray away from the expected mean output for each demanded task, of inter-worker leverage. Focus is now shifted to the concept of a contested environment. Thorough descriptions of contested environments encapsulate more than the explicit mention of the workers, the tasks they are expected to complete, and their socio-economic administration. Metrics, measurements designed to gauge the effectiveness of a worker by their work and the potential of the worker to conduct other work, are typically based on scientific principles, perhaps maybe pushing into the terrain of national/cultural norms accepted as the truths for the time and the space. Numerical manipulation of aspects concerning metrics, such as raising or lowering the expected measurement of a metric, utilizing metrics outdated or out of touch with the context, and mismeasurements by the metric should be the expectation in improperly regulated environments, these environments technically contested by the volatile lack of basis.
In one form of a contested environment, there is a
task
More forms of contested environments exist; these ones
rely on metric-less work. In metric-less work,
there are less objective measures available for the
socio-economic administration to gauge the effectiveness
of each worker. Activities such as research, the arts
and design, policing (questionably), and non-profiting
social services are examples that are difficult to gauge
in quality, despite there being obvious ways such as
statistical frequency counts. Two workers in a metric-less
work environment may expend as much energy as one another
in fulfilling a task. The manifestation of this task's
completion takes many forms as the acceptable output. One
worker produces a different product than the other, and is
greatly rewarded in currency payments, while the other
does not receive any currency payment whatsoever. In
another example of a metric-less work environment, one
worker is able to use the other worker's work as a
critical step towards outputting a product. The
worker is greatly rewarded in currency payments, and
the other goes bankrupt. The outputs from metric-less
work are products outside of the scope of their
immediate reference. What is worthless for their
time may, in fact, become priceless by its exorbitant
valuation at a future near or far. For example, a worker
expends their efforts for a product
Forms of contested environments such as the mentioned boundless competitive output, unregulated guarantees, and metric-less work can be used in campaigns such as the output-delusion scheme. What is half-efforts, full takes again? In these environments, there is the openness in interpretation by the workers and their socio-economic administration of the rules and regulations. To add onto this subjectivity, the socio-economic administration could execute stated rules and regulations by a whimsical style. Worker performance, measured by their output that is put into a light of subjectivity, could furthermore be skewed in reception. The worker that expends more effort could be subject to greater scrutiny. The worker that plays by the "rules and regulations", of a whimsical enactment, could be socio-economically rewarded at a greater scale than others that have expended more effort for products of a potentially greater value, but failed to play by the same "rules and regulations".
HEFT2: A worker-administrator graphical unit
that is comprised of four main entities: the workers
(W), the administration (A), an arbitrarily-defined
channel to currency (red ??), and a currency authority ($$).
The worker works, by function
The worker-administrator graphical unit, of
diagram HEFT2, should be not interpreted as the
universal model for work arrangements that involve
currency; claiming that this graphical unit does serve
as the universal model for such activity would probably
be challenged in some way. But it does provide enough
capabilities to account for factors of advanced or large
networks. Additionally, the abstract functions
Worker-administrator dynamics provide a full template for discussion on the category of the open-gain environment. The worker in this environment is not attached to the administrator, for an indeterminate amount of time, in a feedback loop of completing tasks demanded of them, in order to receive currency from the administrator. In conservative worker-administrator dynamics, the work environment is designed to ensure the command-flow, from the administrator to the worker, remains intact in hierarchical relation. Preventative measures are put in place to prevent the command-flow from caving in: the worker quits or is fired for insubordination, or the worker assumes the role of an administrator that usurps their current administrator. Rationing of currency payments is a typical route to ensure that the worker does not accumulate enough power, per se, in the form of excess currency that they could divert towards other outlets in competition against the administration. In open-gain environments, the worker could expect that their efforts expended would yield them at least an equal output back to them. This output, the product itself, currency, or an exchanged product, would mean no losses of measurable value back to them. The worker may even acquire a lot of currency, many times that of their peers that put in the same amount of work, due to currency constraints placed on their peers while they have the liberty of no maximal constraints with currency payments. The category of open-gain environments is a term to generalize the lack of conservative arrangements, on the matter of product, product valuation, and continual lack of change in relations between the workers and the administrators.
Much interest is taken in the field of argument construction and execution, driven by demands in defensive competency. Demands in this field are somehow spurred through the spontaneity of the experience and the experience's ensuing reflection, and in many cases, compulsions to gain competency in this field are not innate, rather passed down in constructs keen on maintaining a vigilance that operates on the belief of continual sources of threats, uncontrollable and maybe unhelpable in juxtaposition to the self capable of its own improvement. The idea of the "self" and the "other" as a dualistic combination that becomes connected by great flux, asymmetry, or other mechanisms of polarity and separation is not the main topic in this discussion. The argument as the tool and the context as the operating environment with specific variables of qualities such as restriction, constraint, and derivation is the specific sub-field in defense that is detailed. The choice of using the term "defense" instead of "offense" is due to notions, to be explained, that emphasize how certain offenses occur without ignoring their implicit weaknesses of their forward force (that is usually how offense occurs), for that would allow there to be conceptualizations expressed, justifiable through their lack of opposing views as grounds for oppositional debate, of the offense as being impeccable, godlike in another word.
The term "argument" is a term predominantly used as a label for verbal or written forms of opposition and/or antagonism against one side, perhaps a null side, in favor of another perspective from its own rationale, with options of promoting partiality through the engineering of opinions and biases. Arguments have orientations according to a polarity of sorts, since they fall in the spectrum of promotion and contradiction. Predominant forms of what are called arguments do not require there to be a rubric for civility or peacekeeping, disappointly for many that rely on verbal and written forms in their existential interests, but universalism in implementations of civility and peacekeeping encountered variants of differing styles with magnetic properties in binding and repulsing, with the resultant from these implementations non-constant by the observation of images comprised of the pertinent structures and behaviors. The term "fight" is a synonymous one to "argument", but its use, as a descriptor for non-uniting phenomena between autonomous entities, veers to those events with more volatile and/or violent practices for outcomes that have higher probabilities of the relation between the participants to be irreparable. The preferential usage of these synonyms in the human sense is not this section's prime crux, for diction is greatly influenced by factors such as occupation, socio-economic views, cultural upbringings, and in the spatiotemporal sense, the context.
The argument is first discussed in the light of a third-party observer to the participants of an argument. The role of a third-party observer is not assigned to a constant agent. Third-party observers can play the role of participants to an argument, and vice-versa. Inclusion of third parties may be interpreted as being extraneous to the focus of the argument. However, the description of a certain kind of argument requires acknowledgment of their existence by their relevance in judgments concerning the argument. The participants of an argument, split between at least two sides, are not expected to come to terms with what is the "correct" solution of the argument. This expectation does not rely on the matters of the argument to be subjective or objective in detail. Participants have the power to reject the building blocks of their competitors' arguments, as to not receive these arguments' main points, such as conclusions and conjectures, to be valid. On the viability of continuing the argument as a forward force against the power of the opposing participant's rejection, the solution for standing by the argument would turn into solving for an energy resource and expenditure issue, instead of the truthfulness of the argument in the local,global, and agent-relational contexts. More than one descriptor certainly exists to categorize this kind of argument. A fair one would be interpretable argument, an argument that values the interpretation/s on a grander scale than the truthfulness of whatever leanings and points in formulations the participants may present.
In a first demonstration of the interpretable argument,
there are two participants
Participant
and
for a posed issue
note: This text uses the "argument" to describe a topic that two or more participants argue on. Each of the participants have an argument that perpetuates something in this argument. Their arguments are sub-arguments of the argument they partake in.
The interpretable argument can also take place without an observer. In some of these situations, the participants of their formulated arguments have the autonomy to agree or disagree on the correctness of the solution, and to proceed forward from that degree of compatibility. Other situations place different conditions on the participants. A participant may lose the equal hand in their argument against the other/s. This participant's argument may then be placed in the domain controlled by the other participant/s, due to this inequality. The other participant/s, in turn, have the capability to depict the argument of this participant as something else, a non-identical retelling. Depending on the gravity of the topic of argument, the participant that has their argument lose the status of equal hand could find themselves at a great disadvantage, based on the operable potential of action from the argument that they participated in, amongst the other participants. The other participants could adversely depict this participant to non-participants (third-party observers), and leverage negative reception back against this participant. The non-participants could influence factors unrelated to the argument but somehow impactful to the existence of the participant that has lost the equal hand. In this situation, there is a malicious triangulation with the participant of argument's unequal status placed as the "sink" for losses.
AIPC1: Other participants
A more qualitative exploration of the argument in its
context demands categories for usage of the argument's
constituents. Boolean labels for the truthfulness of each
constituent serve as a barebones basic. There is the spectrum
of continuity that is used in cases of uncertainty between
polarities. The category of external mutability, according to
state and behavioral conservation, adds another dimension
of complexity. Overall, the use of both of these categories
works in a manner similar to that of the complex number
system. To allow for explanation that concentrates on the
coverage of the quality over the potential messiness in
quantitative demonstration, boolean labels are preferred over
their infinitely-sized counterparts, the spectrum. A step
further from the labeling akin to that of the complex numerical
system, two more categories are used, the boolean of the
truth's effects onto the self and that from the other.
So there are 16 possibilities,
The finitely-sized rubric is used as a methodology of judgment by one of the agents concerning the argument. This finite rubric is also a full boolean map; every constituent from the argument as input produces a boolean. In arguments of free form (not elaborated on), a thoroughly comprehensive rubric is not as simple in definition as this one described. There are troubling issues with any finitely-sized rubric, but these issues are better isolated for understanding in comparison with the matters concerning free forms. A recurring issue is the effectuality of the rubric, based on an arbitrary issue. The issue could be a matter of pure preference outside of the scope of nature-based systems. In natured-based systems, a rubric that is valid would have to accomodate for these natural laws. Design and verification of rubrics observe these natural laws that take precedence over the accomodation of preferences by autonomous agents.
A rubric is always associated with an objective, an agenda in other words, that acts on the knowledge gained from the rubric's use. The objective contains prescribed actions to be taken for the possibilities of the information gathered from the rubric. This is a prescribed tool distributed to users for them to comprehend the qualities, perhaps by the use of quantities, of a matter with qualities unknown or unrecorded to them before they engage on analysis by the rubric. The qualities that a rubric observes and the objective from the rubric are not bound by traits contained entirely between them two, due to the obvious condition that autonomous agents are involved in at least one step concerning the use of the rubric. And they, the agents, have or derive objectives out of their own understanding of pressing needs to be satisfied. The rubric is also thought of as an auxiliary tool of filtration for a control system to produce and maintain a controlled environment borne from controlled outcomes. The aims of a rubric are wholly considered in this next diagram's elaboration.
Using the four-category labeling system put forth, an example of an argument is initiated with two missing labels for its constituents in the categories of the truth's effects onto the argument's possessor and effects from the other. These two missing labels of an argument are due to its existing in a lone state, with no influences from participants of an argument or any rubric/s. Back to the mention of nature-based systems, assume for intents and purposes of their effects on the rubric, natural laws are immutable by any participant of any argument, although immutable traits do not guarantee constancy of those traits' effects. A rubric has a number of specific natural laws, probably not all of them, pertinent to it in its context of use. A user of a rubric in use may be able to control all of the natural laws pertaining to it. In these cases, the two constituent labels on the argument's effects directly correspond to the exclusive relations between the rubric's users. The category of an argument's mutability is also complicated, in its lone state. If the label for mutability of an argument in its lone state is known, knowledge of this is expected before the argument's engagement with forces not of the argument's possessor. The possessor's knowledge of this label also presumes them to be aware of what constituents in their argument are not guaranteed to conserve their form in their practical existence. To clarify, however, the four labels of this kind of argument defined do not require accurate knowledge of them by any of the argument's participants, including the possessor.
AIPC2: A diagram showing the four-category model of an
argument's constituent. The constituent
The diagram below is an abstraction of the argument and the participants.
AIPC3: A topic
AIPC4: An argument as the rectangle holding five constituents. These five constituents are expressed as a sequential flow, by the red arrows. The dashed green lines from each constituent are part of their "strong" implications, the underlying reasoning that each constituent relies on as a basis for validation. The dashed blue arrows emitting from the argument are "weak" implications, defined in this use as the meanings from the constituents of the argument that are deduced without an achievement of certainty.
Diagram AIPC4 is of the continuous argument classification. The continuous argument is expressed as a sequential flow of its constituents, uninterrupted from the first constituent to the last constituent. Continuous arguments do not have to be interminable, despite their naming. Arguments that solely use the four-category constituent model have immutable initial expression; the possessor of the argument cannot permute, obsfuscate, or alter any of the constituents. The possessor could play a role in the effects of each constituent. In discontinuous arguments, each participant in an argument makes exchanges, usually of a communicative form, with one another. An exchange of one participant could be reactive to another one, and this same exchange could also not be part of the focus for the participant's crux of their argument. The discontinous argument starts off with a statement, then allows for ensuing exchanges of a potentially reactive form to the constituents of another participant's argument. The starting statement and these exchanges make up the body of each participant's discontinuous argument. A participant could also produce constituents, in their argument's progress, that "retract" or "reverse" the meaning of a previous constituent. Retractions and reversals are also found in some continuous arguments, but their effectiveness as an integrating force for these arguments' assertions and/or conclusions is questionable by analysis of these arguments' selves. Due to the elevation of doubt as an effect, at least in the cognitive sense, of retractions and reversals, these two techniques are seldom used in continuous arguments of a straightforward force, in its style of expression, with aims to provide more direct interpretation for a wanted reaction of an arbitrary will. Overall,discontinuous arguments are more extensive in generalization because their constituents do not depend on sequential paths of expression. Constituents of a reactive kind are connected as counterparts to the constituents of other participants' discontinuous arguments. And so, the understanding of their sources from which they are generated from is dependent on the knowledge and understanding of their counterparts.
On the category of constituent mutability by an external force,
If a constituent is mutable, an external force that applies itself
onto the constituent would output the opposite of the current truth
value
- depiction of the argument to an agent that is not its possessor,
- execution of the argument in the expressing of its sequentially-ordered constituents,
- argument nullification.
The effects of the four-category boolean constituent, as
This particular ordering is for the possessor's desired gains of the effects with consideration for the gains of possibly negative value distributed to the other, such that the possessor prioritizes their comparative gains over the other to "win" by establishing a positive gap in value between themself, based on the constituent's effect on themself, and the other by the constituent's effect on them.
The adversarial agent
The
AIPC5: Agent
An argument's execution requires additional attributes that are not considered in the previous overview on the argument's depiction. Depiction is conceptualized in this section as a "solid state" image, projected by an agent that uses an argument as the initial image. Execution has properties that rely on temporal matters. Through a temporal span, execution expresses different images through this passage. In terms of an argument, these different images are due to the shifting through of constituents. The steps in such sequential processes cannot produce an achievement of some sorts, when based only in terms of their independent strengths. Each step's innate effectiveness in solving for a demand and the degree of attempt in it are not the only factors. The execution's steps are dependent on each other, and the outcome from the execution is what is from the convergence of all of the actions taken for these steps. By these properties of an execution, an argument must be thought of as a "fluid state" image. In the argument of a "fluid state", what is expressed to an agent at one point in time is not explicit in appearance to that same agent at another point in time, but that what is previously expressed carries relevance in forms that include base support,reference, and elimination of unrelated implications to an expression at a later point in time.
AIPCDEP: An argument as eight constituents. At every point in time, the expressed constituents are not those expressed at a previous point in time. The constituents at every timestamp are dependent on previously expressed constituents, in order to be properly expressed. The expression of the argument ends after five timestamps.
The dependencies of each expressed constituent in table
AIPCDEP are exclusively backward dependencies.
Of course, depiction is depiction and execution is execution.
An argument is not necessarily put in the permanent role
of a "solid state" or a "fluid state" image. For instance,
an adversarial agent can depict an argument
An adversarial agent
To summarize on the practices of an adversarial agent against an argument, this being the forward force as mentioned in the beginning of this section, the adversarial agent employs tactics that fall under the umbrella of outcome engineering. In argument nullification, the agent has the absolutist objective of "negating" or "neutralizing" all constituents of the argument so that the argument does not have any essence of reason or value for continuing its existence. For effecting change onto an executable argument, the constituents of the argument that serve as the greatest source of dependency for other constituents' dependencies are the ones with the greatest attraction for an adversarial agent's attempts to modify by outcome engineering, especially if those constituents are mutable.
The title is from and for treachery, at least in part, is it not? Cold, schematic, manipulative due to the knowledge of calculating and the choice-ability of calculation. A dark personality trait, some of them say, out of their self-professed desires to "spread the truth", to "bring order and equity" into the mix that is at risk of becoming spoiled. Privatized, cryptographic, gravitating inwards towards the center to be kept dark. These attributes do not appear conducive towards an open-armed embrace devoid of naivety. The expressive and outspoken decide it is their turn to chime in: "there must be a better way; there has to be a more effective way to involve more external sources of input, for a better world, one step, one day, one improvement at a time."
Open frameworks. Open-source frameworks. That has been a prevailing solution proposed to maintain a transparency over matters of pertinence. Open frameworks allow for every participant to learn and understand the rules, the procedures, and all the mechanisms used to produce auxiliary tools for use in these frameworks. Manuals are provided for these frameworks. Users of the frameworks study these manuals to understand the intricacies of the frameworks. Before a user enters into the realm of using the framework, they are expected to have perfect information on the details of the framework. There is an openness in these frameworks. By choosing to be a member of the framework, users can expect to be more aware of their co-user's utilities in calculations.
If this much can be stated on open frameworks, what guarantees would open frameworks bring to prospective users? A few vantage points are to be looked at for bases to be formulated on what protections and opportunities open frameworks offer if adopted, especially if these frameworks enable proprietary calculations. This class of calculations is given this name due to attributes on its procedural generators and its outputs that are reserved for an exclusive group of entities. Whatever values of worth and ramifications from these calculations can only be assumed to place a reserved class of entities over others, on the condition that all there is to a chain-of-command and other structures that are less hierarchical, more uniform in distribution of resources and capabilities with few outliers in the properties of effectual actions, are the functions and the calculations, one and the same, without anything else outside of the effectual confines of the calculation infrastructure.
Use the arithmetic system as an example of an open framework. Arithmetic, a rudimentary usage of numbers in an input-output format, does work for fair and equal purposes. Every participant in the open framework of arithmetic has the liberty to use whatever operators and operands they set their selection to. These same participants can also decide what outputs they favor the most, and then to select the appropriate operators and operands to satisfy this favoritism. When there are restrictions on specific operators, or on specific ranges of values for input and output values, equally placed on all participants, then each participant has to play by these rules. Of predispositions unfortunate or not, each participant is assigned different starting numbers from others, by which to perform arithmetic on. Given what restrictions of operators and numerical ranges placed equally on them, each participant has a relatively fair opportunity of reaching any number reached by any other. A participant that cannot reach a number that another participant can reach is still left with their own numbers, so a rationale for fairness can still be made in these cases.
Does the description of open framework as an infrastructure allow for participants to freely use the open framework? By a consequentialist linearity in participant activity, the answer is a resounding NO from the self-interested. The open framework of arithmetic, with numbers of properties each suited to the demands of differing contexts, in an environment that is resource-dependent, through inputs and outputs producing effects outside of the use of the number, does not suffice in guarantees for a participant intent on spending for their wanted numbers of input for outputs with effects that they intend to "benefit" from. The free use of the open framework is not such from the start, the use of the framework, to the finish, the effects that are desired. This perspective does define "free use" to be from these checkpoints of start and finished. To define the use of the open framework as free when all participants are subject to the same rules and each participant has equal access to the input controllers does produce a misconception that can only be unlearned through the errors of the trial. To add more technicality to the mix, if each participant is subject to the same rules of the open framework, but some of them are additionally subject to differing mechanisms of capacities and qualities, then there is already the question of how far free use really goes. Maybe it is not the breadth and depths of the effects from free use that need to be kept at an equal level. So free use may be defined as the arbitrary use of an open framework with rules equally placed on its participants. But that phrase of "free use" does not shed light on the guarantees. Perhaps that is the point of an "open framework" for "open-ended effects". At least every participant would be able to understand the rules right down to the specificities for the system that is open and deserved to them. Every entity could voluntarily participate in these open frameworks. However else can paradise be reached?
Despite the doubts on open frameworks leading to an equality through greater access to prospective participants, there is one trait on them that is more certain in truth. The open framework starts off as a private body of mechanisms, developed by a few to be used by a few. Through the demands posed by temporal progression, private frameworks become more known by those outside of the origin. The rules and procedures of the private framework are valued in some way by them, and then there are calls of an exponential growth for these kinds of frameworks to become more accessible. Factors behind these calls include over-competition, that is, leveraging of power and advantage concentrated into efforts for the objective of victory, with these victories entailing severely lopsided gains and losses in zero-sum contexts. Open frameworks are a result of progressively greater demands. What was once a framework of rules and procedures reserved for a few has yielded enough long-lasting value for the framework to become an open instead of a closed one. If the value from these private frameworks has rised to above a point such that keeping the frameworks closed is a task to preserve an obsolete way of operation, then there is that as a reason for the framework to become an open one. So open frameworks are a progressive improvement indicative of demands different from that at the origin of the frameworks. These different demands therefore pose other rules and procedures as operation that form a new kind of private framework reliant on the previous framework, now open, to be directed in use for it.
The mentioned generalization of the open framework transitioned from a closed one, as a decision from collective interests of an evolutionary system, still does not tell many details on the categories of calculations that play important parts in calculating systems. Is the open framework anything more than a "staging grounds" for what is designated proprietary in a self-improving process that reveals every last stage it experienced as open frameworks and conceals its current stage? The answer of a solid YES or NO still does not fulfill the adequacy for a "fair system", defined as inputs and outputs of qualities agreed upon by all, not merely the voluntary participants. Open frameworks cannot be expected to produce universally agreed-upon predeterministic courses of action. For this posit, explanations in this section may be scant, but the autonomous nature of sentience does not really require any noteworthy explanation, always falling short due to incompleteness, when exemplifications from the image and the real course (of decisions taken or not, depictions concocted to be believed or not) serve as counter-arguments to the open framework as an automatic and enabling conduit for fairness and equity. Determinism is contentious, then, for the believers and non-believers.
Of foremost pertinence in open frameworks is their usage. Suppose that initially, things really are fair and accessible. Every participant that joins in the utilities of the open framework are given evenly-distributed knowledge on how the framework works. These participants are also each granted the same external resources, in breadth and depth, as one another. Then, the styles of possibly differing appearance that produce possibly differing outcomes is put under inspection. Here is where the styles of use manifest themselves to produce spans of diverse outcomes, safe to assume to be infinitely-sized, at least from the beginning. Consider a layered computational model, with a low-level that is responsible for the most minute details in utilizing the most basic and individually inconsequential elements, all the way up to the highest high-level, a level that produces the last action (typically expressed in ways measurable by autonomous agents) in a directed flow of activity from the model projected outwards. And this last action is where the capability of full control over activity ends, since the effects of desired and actual do not have to be in total alignment.
The user that heavily uses a layered computational model's lowest level will tend to have a more astute understanding of the fundamentals belonging to said model. This same user also does not emphasize the outward expression of the model, for this focus is reserved for those that are at the model's higher levels. Users of a layered computational model, specifically one of an open framework, that strongly prefer one end of the layer over the other, such as preference for the low-level over the high-level, will be of different qualities in thought and action compared with each other. The low-level user has an appreciation for the details of the layered computational model; their actions in this model do directly touch the model's underpinnings. And the high-level user, however much they may value the underlying mechanics and other minutiae of the model, is forced to gear their use for the outward expression of the model. If these high-level users are also coincidentally the representatives of the model, the ones responsible for the effects emanating from the model, then they are naturally forced to be more concerned about the effects of their actions from the model.
Important sub-topics, in this conceptualization of the open framework as a layered computational model, are the sources of influence and the bearers of responsibility. A layered computational model with dynamic functionality also tends to be one of high plasticity, so that demands of morphological characteristic can be fulfilled. In a unidirectional flow from the lowest level to the highest level, the influence of effects from the model would be from the lowest level. Despite whatever level of non-deterministic output from the model that is an open framework, there would be no output without the lowest level. This statement does assume that there are necessitated co-dependencies shared between all layers of the model, in order for the model to output. In certain subtypes of models, the lowest levels do not have the autonomy to be modified, by themselves or through sources other than a few select prescribers (i.e. the higher levels). The higher levels could additionally attempt to make these lower levels fixed in their qualities, or to plan for rapid replacement of lower levels at risk of severence from the layered computational model. For these cases, the magnitude of influence higher levels carry over lower levels is multiple times greater than one. The term "responsibility" is now taken to mean the bearers of effects. The open framework and the administration of effects related to it are not rigidly connected without the involvement of autonomous agents, with their own way of handling matters that may be outside the completely controlling grasp of the open framework or the open framework's preferential usage. The open framework, as a layered computational model, must be one with roles and procedures specially prescribed, possibly modified throughout the course of use, with certain levels of uniqueness to each layer. It is asymmetrical labor, in the form of hierarchies and stratifications, that adopt the open framework for use. The low-levels and high-levels of an open framework, in the form of a layered computational model, are conflated with this mentioned asymmetrical labor.
Something called the precision curse is fit to be placed into the paradigm of the open framework. The precision curse is truly nothing new, but an aspect found in the failures of applied mathematics, although the failures do serve as a fuel for greater scientific rigor, and in social arrangements with declared ideals unable to be attained. These social arrangements, if have acquired enough prestige of proliferation in retelling, do result in literary works prominent in the categories of tragedy, superstition & lore, as well as political intrigue. The precision curse is found in two main areas, overlapping in some ways, of open frameworks: the layered computational model and information acquisition & utility.
The building blocks of calculations between each layer of a layered computational model has already been mentioned as comparative differences. Consider a problem that has a relatively low probability of being solved by these models. This low rate is demonstrated through repeated iterations of their performance. After a user has fiddled enough with the parameters of each layer in the model, and to no avail of improvement, the user decides to accept the shortcomings as a permanence. After the user secures the lower levels into an effect-conserving state, they then only need to focus on operating the open framework at the highest high-level that they can be positioned at. At this point in the user's role with regards to the open framework, the user is expected to produce amounts of error quite measurable to other participants and the possible recipients. There are no ways around these errors in accordance with the user's style. The user is set on this way of using the open framework. Without regulatory overhead that is prohibitionist to the user, the user cannot be expected to cease except out of their own will. Under the prevailing chokehold of the precision curse, a user of a layered computational model may attempt to change the underlying mechanisms, found at the lower levels, for improved output. But the user will discover that this requires an extremely expensive magnitude of introspection into the device that they use, the device that is supposed to serve their aims, not their lofty estimations that remain correct only in the realm of imagination. And introspections of this nature need to be done frequently for problems that improve against the successes of the user. In this example of a contraption for erroneous offspring, metaphorically speaking, there is also the related concept of the pragmatism trap (section The Sophisticated as Behavior After Appearance).
The economy of knowledge has its values and priorities. With open frameworks alongside select use and distribution of knowledge, a lack of expectations is the default anticipatory state for those avoidant of speculation. Unrestrained speculation for things not of a certainty is not of the diligent's decorum. Even for a thoroughly enjoyable future planned with no room for error, these futures typically constrained to a small and controlled environment, the meek dare not express their giddiness for fear that such giddiness can be spun around to ruin the dear event. A topic as grand in exemplified monetary value and as deep, insightful, and thoughtful as the economy of knowledge requires so many words, of textbooks and beyond, to be given due justice in the representation of the power in its gravity. In one of the more obvious routes to discuss the economy of knowledge, the factor of pre-emptive knowledge, possessed by one or more about others, is at the cornerstone of feedforward systems. Feedforward, the idea that one can use knowledge, supposedly accurate to the future, by appropriately planning for the outcomes of expected and desired, does become a concern. If determinism is something entirely reserved in the connected wills of all autonomous agents, then strategies of feedforwarding constitute one of the greatest essences in the outcomes of determinism, by pre-deterministically playing things at least one step ahead.
The dynamism of information valuable to arbitrary contexts is broad enough for feedforwarding to also be of a similar magnitude in broadness of exemplification. Proceeding illustrations of feedforwarding are a part of the precision curse's information acquisition & utility. One important sub-class of feedforwarding is external multi-agent activity.
PC1: Variables
Diagram PC1 shows externally-sourced feedforwarding environmental construction. Without discussing the two extreme possibilities in the aims of the external agent to the subject of such construction, there is this obvious fact worthy of mention: the external agent is able to exert a noticeable form of "control" over the recipient of their feedforwarding strategy.
Another feedforwarding strategy is not as direct in assertion as that found in diagram PC1. But it is still prominent enough by its effects to have an example concocted for it.
PC2: Agent
Diagram PC2 is the strategy of externally-sourced
feedforwarding influence. This is exemplar of granting
the recipient an illusion of choice; the external
agent
External multi-agent activity is perhaps the most common future for open frameworks. This is not to state that involvement of numerous sources of input can result in outcomes differing between the expected and actual, but probabilities in forecasting do become modified, and these modifications affect the perception of the present, the present with emerging open frameworks. Frameworks that have been converted from proprietary to open states typically entail vulnerability transfers in zero-sum agenda. The agenda does not have to be zero-sum, sure, but that is a design best left to the finiteness of resources, the owners of those resources, and those desiring to own those resources. In proprietary frameworks with possessors that reap benefit from them, the possessors do so at marked cost to non-possessors. The possessors could go on ahead to deploying these kinds of frameworks directly against non-possessors in competitive match-ups, with strong lines of distinction in activity and possibly status between them and their competitors, the non-possessors. The possessors could also bypass the non-possessor's control of input and cooperation that they would have had to be bound by if not for their proprietary framework/s. One area that open frameworks operate in, as a critical effector variable, is confidence building. A valuable proprietary framework somehow became valuable enough for there to be a belief that its exclusive possession is a vulnerability. The possessors have to fortify defensive mechanisms to guard their "secret", and the non-possessors feel as though they are put on an unfair playing field, the set-up intended not by them for their failures costless to adversaries. When the proprietary framework is relinquished to the level of an open one, the vulnerability in unfair mechanisms through usage may still remain at some point in the chain of activity related to the framework. The framework is now less exclusive, and the question of its possession is no longer entirely under the umbrella of vulnerabilities. A typical goal of the framework becoming open is to enable confidence between users to foster, for those outside of the conventional realms of usage to become familiarized with it and for independent verification. The open framework becomes subject to the ever-vigilant scrutiny of judges, specialized or not, in their inspection of its correctness and consistency. With passing marks on verification tests, more transparent than proprietary's self-verifying skew in nature, confidence flourishes for the framework's validity, now open.
In zero-sum contexts, the bulk of vulnerabilities is transferred over to the open framework's usage. Some elaboration on how this transferal plays out has already been made in this section. In perpetuating proprietary measures, these ones stacked on top of the open framework, adopters exclusively select peers to cooperatively build confidence, exclusive between them, by sharing risks in actions taken. These risks involve building proprietary measures on top of the open framework, all the while avoiding or suppressing opposition that hampers this building, to achieve the promised value of obtaining a surefire advantage amongst the framework's mass use. This situation is another pillar in supporting the argument that open frameworks do serve as "staging grounds" for designs of styles and use not for the open.
All autonomous entities engage in calculations that cannot be entirely left open in such a way as to be vulnerable outlets. This is a statement based on the derivatives borne from biological immune systems. Entities' proprietary calculations are a fixture due to their engineering of odds, once unfavorable or questionable, towards objectives of a more absolutist mark in effects. And obviously, absolutism is zero-sum.
There is a division already, is there not? There is the audience and the spectated. To go ahead and assume that this division will foment a kind of malevolence between these two groups is too far without more details. The participants of a spectacle open to an audience could just be there, enjoying themselves in each others' company. Negativity aside, please. An absolute lack of cooperation and unity to state that there is a division that is not benign. Vultures are not inherently bad creatures, and what notoriety they garner is not because they are terrific predators. Quite opposite. The anatomy of the vulture makes them ill-suited to acting as predators in the ways of their more prestigious avian cousins. There are cognitive limits placed on the sentient life besides from human beings, which is why their anatomical design proves to be a great determinant in their potential of capabilities. This is not a flattering remark on humanity. It has been stated many times, and this time is simply a retelling: human beings compensate for physical inability through actionable cognitive ability. Emphasis on the descriptor "actionable". Maybe there are creatures on this planet more intelligent than the human. The vulture, although also not known to be beyond the intelligence of their peers, serves the noble purpose of an important mediator in the cycling of life,death, and decomposition. Decomposition, the last stage, is where the vulture intervenes as a clean-up technician. Possible biological hazards are removed through their feasting. Some nicknames for vultures: scavengers, bottom feeders.
The audience is not always the vulture in settings where there are no mortal casualties. In the technical sense, the vulture as the audience is there to anticipate what it believes is inevitable to emerge out of the situation: death in material form. The vulture could also just so happen to stumble upon the material death. And then the creature is able to feast without there being resistance perceivable to it. Feast it does, joyfully and naturally, by its specialized digestive system that processes more extreme inputs than other counterparts.
In this section, the reason for why the audience is likened to a vulture is to fulfill a healthy skepticism on matters such as duties, appeasement, impressionism, and honor. Each of these four mentioned terms is a single-minded promoter. Such drastic displays and actions taken, and there is little space or time in direly needy situations for there to be a reflection on the underlying reasoning that is usually strongly tainted with emotionalism. To merrily jump into harm's way is, by far, one of the most cliched tropes in tragedy. This is not ridicule on these deeds of autonomous will under the influence, but such risky actions are to be rationed because of their terminal and non-regeneratable outcomes. The vulture has evolved to be smart in other senses then. Not only a noble servant in the cycling of life,death, and decomposition, it is also calculating through aversion of risk. Its way of diet serves its appetite, the sanitation of the environment, and some may argue, the honorable relinquish of the dead from purgatory to the afterlife. And the vulture does not need to merrily jump into harm's way. That would violate its role in the cycle. Creatures such as vultures are fixed in their behavior. The audience is not. But some parallels of interest emerge when the audience is likened to the vulture.
Section To Be Revered by What is related to the spectating
vulture. In that previous section, the theme touches on the
idea of that which is spectated to be believed as a source
for worship. The computational reference network, especially,
with an example diagram CRN2, could be used to depict how the
spectators (references) view the spectated (source). Diagram
CRN2 shows two references with material and functional utility
transfers with the source. Reference
The vulture is a protector and a reaper. These two metaphors for the metaphor of the audience as a vulture spark curiosity in their coupling. By these terms' associations, the vulture is a gray-zone creature. In the singular theme of heroics, the vulture is an anti-hero. An ambiguous necessity for the greater order, proponents of the creature argue. The beginning of this work makes the claim that zero-sum is greatly emphasized in the education of decision-making. Specifically, the economic sub-field of game theory spearheads this as a co-existing dynamic with non-zero sum games. Some that engage in games of sorts, outside of pure recreation, can favor specific kinds of payoff for themselves. In terms of the psychological impact from a payoff's effects retained in memory, and the retention of the memory then used as fuel for self-corrective or self-improving mechanisms, the actualization of zero-sum dynamics arguably outsizes in impact when compared to cousin-types of payoffs. Depending on what is placed as the object or principle that is enumerated in the payoff table, the pain of unwanted forfeiture from zero-sum opens the route for a wide possible range of indentation on the losing recipient's modus operandi. The vulture, the gray-zone creature that it is, makes for a potent case study in the blurring of game theory payoff labels.
The vulture, the spectator, not the spectated, exists in a few paradigms featuring it as the star of the show. Sentiments, usually not explicitly expressed, go something like this:
"We the Vulture stand strong and together,
To fight for what is rightfully ours,
To voice both opinions and judgments,
With no sound, wait in silence,
Onto those fortunate or not to stand them,
For our voice to reap what kills our hunger."
The vulture loses its place as a direct metaphor for the audience through the passage of these numerous paradigms. Conditions and privileges, of an unnatural association to the literal creature that is the vulture, are attached to these conceptualizations. And these conditions and privileges are from human societies.
Illustration of the vulture as something more than another run-of-the-mill creature starts with focus on it as the reaper. Payoff tables enable the quantifying definition of the vulture's context. This context of structurally allocated numbers enables viewers to predict, with odds of correctness tending to above fifty percent, what the vulture decides on.
TAIV1: Two spectated agents
There is unclear frequency in move usage for each of the
agents
TAIV2: The same spectated agents from table TAIV1. For each combination of moves, there is a boolean for each agent. The boolean denotes if the respective agent is capable of acting on the move in the event that the opposing agent acts on their move. This table contains variable boolean values, subject to change by the causality of the specific spatiotemporal context during the duel.
Table TAIV2 forms a layout of restrictions imposed on
each of the agents during their duel. The agents would
each have to be conscientious of what choices in moves
they each can take at every changing context in their
duel. Without these restrictions, agent
Tables TAIV1 and TAIV2 form the foundation of decisions
for the spectated
Meanwhile, the vulture is patiently waiting for the termination
of the situation between
TAIV3: A variable number of
The vulture, in the situation between
TAIV4: A differing alternative of the situation from
table TAIV1. All move combinations are non-zero sum, and
completely positive in gains for both agents
TAIV5: A differing alternative of the situation from
table TAIV1. Each value of the cost table is a triplet
showing the gains made by the vulture,
The situation in TAIV4 guarantees there to be no casualties
of
A characteristic separate from the literal vulture is attached to the abstraction of a vulture in this next paradigm. Vultures, the indiscriminate consumer of the material dead, turn out to have a favoristist slant to their spectatorship. Favoritism takes the two classic forms of implicit and explicit expression. Whereas a vulture of the implicitly favoritist variety does not influence the course of events leading up to the material dead that it spectates, its counterpart favoritist does. In both cases, the favoritist vulture abstains from consuming the spectated fallen that it favored. Favoritist practices such as these fall in line with aspects common across many species, such as ape clans. Here is a speculative notion: if these kinds of vultures existed in resource-scarce environments, their livelihood would force them to discriminate less on what is available as their food.
In environments ripe with favoritism, the spectated play into the presumptions of the audience rather than let pass a stunning upset to the partially sympathetic spectators. Given rules established at the beginning, the spectated's abidement of the rules is an entitlement to the spectators. The spectators, of a favoritist variety, do have other expectations borne from hope on their favored. Situations such as these are difficult to psychologically mollify. From the generic perspective of business ethics, "the customer is always right". To suppress favoritism is not in line with the wants and needs of all participants, especially the customer that is the spectator, of the situation. Suppression is usually frowned upon as an affront to individual freedoms and some idealization of apathy that could very well be a deep antagonism.
The implementation of favoritism takes many forms. It is unnecessary to attempt to list the various ways favoritism is practiced. These kinds of allocated positive and negative influences target the mutable surface of variables, by varying degrees into the depths of their source control for outward expression. The concept of externally-sourced feedforwarding influence, found in the previous section Proprietary Calculations, is a competent template of visualization for how the spectator's wants and their corresponding actions of influence coalesce. The influence is left to be another one of those open questions, due to the lack of specific context.
Not every situation welcomes an audience. The vulture may not be welcomed as a protectionist due to its favoritist leanings. It may not be welcomed whatsoever, despite what lack of discrimination it poses. Some games, intriguing to the areas of statistics and predictive analytics, make themselves pertinent in these situations unwelcoming to the spectator. In the Game of Spilling Secrets, the vulture takes up the responsibility of a selective information broker.
The tasks of an information broker, intent on benefiting through these acts, involve choice calculations, impossible to quantitatively formulate given a lack of information (additionally, the poor knowledge of precedent) and the operating environment that must be mapped into formats quantitatively operable. Once again, by some means, a balancing act of picking and choosing emerges, this time featuring the vulture as the revelatory star.
Predictive analytics rests on the correct use of accurate information. Above of this applied usage, there are some general strategies the information broker deploys with the spectated. An implicating security-breaker is a rationalist approach used to open up protected areas of value. The bypassing or deterioration of defense allows one to reach the area once protected. The approach is frequently used in technical situations and as such, definitely goes by many other names. The uniting detail behind all of these situations is that the secured target is secure by a connectionist arrangement. Attempts to focus all efforts on a single exploit that is heavily guarded does not work.
TAIV6: Any exploit that directly attempts to impact
target
TAIV7:
Suppose there is a piece of information
TAIV8:
Another broad strategy of interest to distributors of capital information, brokers of sorts, is preventative security. This strategy depends on the compromise of a quality belonging to an agent, and this quality is a backward dependency to a checkpoint wanted to be attained by the agent at a future point in time. The term "backward dependency" has been mentioned in the section Arguments in Image-Projectable Contexts. That specific section places the term in the role of a target to be disrupted for an executing process' wanted failure. Backward dependencies, of preventative security by information brokerage, take forms of differing qualities to those of that section. Information is a catalyzer for action in this section, rather than the only constituent for the object in question (the argument in section Arguments in Image-Projectable Contexts).
TAIV9: Table displays a spectated agent
Preventative security is taken by some particular types of information brokers to ensure that some actions cannot be taken by their target. Pressure is applied onto the target, so that their decisions are greatly influenced by the necessitation of either guarding their secret/s, or proceeding along with the action that they would have taken if there was no external and aggressive pressure geared against them.
The information broker's use of these two strategies, implicating security-breaker and preventative security, run converse to the actions taken by the spectated. The vulture, as this kind of information broker, is a protector not for the well-being of the spectated. It is the main agent in the Game of Spilling Secrets; the secrets belong to the spectated, most unwelcoming to the vulture. This particular game becomes very complicated when the spectators, all vultures, are not strongly allied with each other. The concept of weakly-connected alliances, a fair term for vultures not beholden to a solid alignment, was described in the section Shifty and Shifting Alliances Pt. II.
TAIV10: Diagram illustrating the construct that one
vulture
Each vulture in the Game of Spilling Secrets has to
make decisions for a situation similar to that of the
central vulture
This is a game about adversarial control. In this section, its description does not contain constraints such as rules placed on the spectated and the spectators to preserve the strong division of labor, and the scope of harmful activity the vulture could be a part of. From a quantitative perspective, description of the Game of Spilling Secrets lacks the form of algebraic/economic rigidity found in simpler decision-making situations. Attempting to add quantitative definition to this game requires multi-layered algebraic expressions (i.e. chained-inequalities, sequential matrices), for use as decision-making operating environments.
In this next paradigm, the vulture is a protector of the spectated. By some twists of alignment, these creatures now take the side of the spectated that need their actions and information kept secret. Security of information transmission is the central task for the vultures. There is the issue with consistency of information quality transmitted from one to another. Another issue deals with the outward transmission of sensitive information from the protectors of a spectated group to outsiders.
TAIV11: A typical verification scheme that uses the
principle of consistent echo (recollection). The spectated
agent
TAIV12: Valuable information
Information-protectionist schemes are essentially cryptographic practice. Defensive competency by the principle of cumulative layering is standard practice. Vultures, as protectors of the spectated, are divided into three main categories. The first is the witness, the second the verifiers of the information relayed from the witnesses, and the third is the arbitrary defensive system to guard against an adversarial outsider's acquisition.
TAIV13: A layered information-protectionist design
by the vultures to protect the spectated
The idea is that even if
After successful application of the inquisitive
force,
the information that they were originally given as
input.
The vulture, as the protector, in this brief abstract of standard cryptographic practice, is far from how the literal vulture operates. But information security practices could mean to protect a spectator of sorts, including the possessor/narrator of information and the devices responsible for containing that information, so this description of the metaphorical vulture-protector is a fitting analogy for activity in that realm. Like the Game of Telephone, very well-known in many areas of the modern world, regardless of the area's technological and cultural prestige, vulture organization into cryptographic configurations may not produce the security intended. Sometimes, there is a big gap between the information deemed valuable, to be heavily guarded, and the security of the sentient being or place that information pertains to. Maybe the mystery of the unknown information, or the information presented in differing forms such as through encryption or gossip, sparks the right kind of outrage to pose real harm, especially if that information is not directly related to ensuring security of some form. When it comes to over-reliance on sentient beings in protectionist schematics, some may not be qualified to obey a prescribed quantification scheme. Quantification could fall short of predicting chaos reactive from some kind of information reception, and that information does not have to be the truth. In the grand order of protectionism, there are economic costs attached. There are power dynamics and contingencies to be maintained. And there is the literal creature, the vulture.
The conceptual cycle has produced some phrases made classic after having found their way into common dialogue, discussion, and other kinds of linguistic expression. For an encouraging remark, try "maybe next time". For a rationale on what is believed to be justice exemplified, "that is karma" and "what comes around goes around". For telling another what they are in the totality of existence, "know your place in the circle of life". For admitting to the consequences of a bad decision or events outside of one's own control, "it is a cyclical downturn". The conceptual cycle is perceived as simple, yet robust enough to account for the many unexpected disappointments and the stories of triumph after rebirth. There exist beliefs in it as the prime component, the core, of deterministic perfection, unbreakable conservatism, and rule of human choice (a part of unbreakable conservatism in the socio-economic realm). The spans of available choice, in general, do coincide with expansions and recessions in capital and the state. Those proponents of free will, subject to these choices, would probably prefer abstinence given the degree of said choices' poorness. Mating games for many species are also cyclical due to seasonal preferences. Relentless dedication that results in more perfection than not is usually not without a scientific awareness of the methodology for cyclical improvement. The wheel, the cog, and the circuit are all materializations of the cycle. In more subjective contexts, such as in faith and the natural order that many human beings believe to be the one/s pre-ordained to govern, the cycle in these abstracted mentions lacks scientific proof and practice. The capability of commanding wheels, cogs, and circuits is not the only determinant in controlling the all-superceding cycle, believed to be the dictator of any thing that can change through the thing's existence, yes? But yet, there are still some that stand by the cycle as justification for whatever lack of control they have, or for what contentious actions they have taken. The preferential practice of cyclical routines is due to, by some degree, the practitioner's belief that they can achieve the closest possible to the infinite, an unquantifiable and godly value, by acting in the image of the infinitely-spinning cycle.
Employing the cycle as the explanation for events, "big" or "small", that transpire out of causality, along disjoint spectrums of variance, means that the cycle is understood as a localized-mutative effector. A cycle can exist in a greater cycle, or run its course as a cycle distinct from another's events and/or variables. The events of a sequence, for the progression of a construct's development, do not have to retain identity that passes prescribed similarity tests with another sequence, in order for the two sequences, judged as distinct, to be regarded as identical cycles. The cycle of one process can produce more than one product. A cycle can produce multiple products through a single iteration. By the quality of localization, a particular product attributed to a cycle could be a product of another cycle. The other cycle could be a super-cycle to that cycle, or be a predominantly disjoint cycle except for the sharing of attribution in that one product. There is both consistency and inconsistency in the cycle then, due to its capabilities to localize (change in concentration and scope from a parenting super-cycle) and to change in metrics of outward appearance and effects, both immeasurable and not. This paradox is not with a uni-objective explanation, for the mentioned cycle of these contexts is mentioned because of the perception, resting on background and presumptive knowledge, that becomes rationalized into that of a judgment on the cycle as the one explanation for possibly many shades, scopes, and established causes. There is due to be opinion on the individuality of the cycle: materializations of the cycle into forms such as wheels are inarguably distinct, due to the process of exemplification from the source to the crafted material, but the methodology of separating the cycle from the remaining whole bears high risk of erroneous demarcation. The all-superceding cycle cannot be traced or shadowed to such degrees that total control over it can be achieved. But that is not the great irony. Arguably, the great irony is that offsprings of this all-superceding cycle can be used as contentious explanations wrongly claimed to have the same believed omnipotence as the all-superceding cycle, for events comprehended as facts or opinions. Another great irony is that if the all-superceding cycle cannot be traced or shadowed, how can the truthfulness of claims, regarding its unbreakable conservatism and rule, be verified? The claims take a believer then. But then again, cognitive analysis by choice and capability does rest much on belief.
Frequent results from involvement with a cycle place said cycle as a key hypnotizer. On a intersecting field to hypnosis is the cycle's role as a derecognizer. The documentation of psychological practice and experimentation is not the aim of this work. Hypnosis is not viewed as scientific by many, due to its probabilistic actualization of wanted effects in recipients that have undergone sessions of this. A recipient to these practices' wanted results would have to accept the experience after forgoing their inhibition. So there is the question of voluntary choice that is the prime piece of proof for controversy. Hypnosis seeks to harness the plasticity of the mind, in the sense that the "wiring" of activators and propensities are modified towards satisfying the aims of the subtle commands enmeshed in the hypnosis session. Opponents of hypnosis, whether applied onto themselves or the overall practice, would call the results of "successful" hypnosis "textbook manipulation". A more convincing argument for the cycle to be recognized as a hypnotizer and a derecognizer exists, and this argument uses analyses of the cycle's effects on memory. The mechanisms of memory are difficult to explain in some cases, such as of human memory. By associating the quality of memory with recall testing in areas such as frequency of occurrence and recognition, and also in confidence of memory authenticity, the perspective that the cycle produces effects of some nature onto memory can be reasonably reviewed.
ASOC1: A cycle with one head,
To be a hypnotizer to a subject, the cycle could present itself as an entity with elements separate from the subject. The subject is not involved in the process/es that run the cycle, and their place is of a third-party observer to the cycle. After some number of iterations, the observer discovers the cycle to be composed of a head and some number of checkpoints before the cycle terminates back at the head. The observer's memory recollection trains them to recognize the cycle by perceiving the head, and each of the checkpoints in their iterative sequence. Expectations are adjusted, from the beginning of lack of expectation towards the certainty that a noted element of the cycle will occur some increments of time later, due to the occurrence of an element that the cycle passed at a previous point in time. The cycle could alter its appearance to include additional elements. But the observer would conserve their initial full-memory of the cycle, with the head and some number of checkpoints, so as to ignore what additional elements are added from one iteration to the next. Then the hypnotizer has accomplished the objective of fixing the observer's cognition to those elements of their initial memory. In contrary alterations, the cycle could alter itself by removing certain checkpoints that the observer holds in their initial full-memory. A successful hypnotizer would force the observer to correct their initial full-memory to the "most accurate" full-memory of the cycle. The cycle could be altered to be composed of just one element, the head, and the observer's cognition would make them think that that is all to the cycle in their ongoing observation. The cycle used as a successful hypnotizer would train the observer's cognition so that the observer would be able to attribute each iteration of the cycle as the identity of the cycle. Although there can be alterations to what a cycle consists of, as long as the observer recognizes each iteration that they observe of the cycle as the cycle's identity, then the hypnotizer has produced lasting effects on the comprehending mechanisms of the observer, with respect to the cycle and its perceived iterations. Derecognition is present in this account of the cycle with its possible alterations in its iterating forms. The observer fails to recognize the changes of features and/or effects of the cycle from one iteration to the next. To the observer, the cycle remains as the cycle, and the changes that bring themselves into and out of the existence of the cycle's iterations are simply anomalies. The design of the cycle does allow for anomalies. Confusingly, the cycle is a deterministic construct, deterministic by the hypnotized observer's perspective, that allows there to be non-deterministic elements of features and effects. One principle of the cycle, as a concept retained in cognition, is relevant enough to note. The cycle needs to have had only one past iteration, and this iteration can either be witnessed directly by the observer or be retold to the observer. After the passing of this one iteration, the observer that begins down the hypnotized path becomes insistent on recognizing the next iteration of the cycle and, in this pursuit, derecognizes details that they find to be superfluous or counter-argumentative to the cycle.
The cycle's hypnotic and derecognizing capabilities also work from a first-party perspective. Without being granted a holistic view of the cycle, the subject of the cycle is to uphold other responsibilities of two varieties: stationary and mobile. Stationary responsibilities require the subject to be actively engaged in efforts for procedures of an arbitrary number of checkpoints in the cycle. Mobile responsibilities treat the subject as an input variable into the cycle. At each checkpoint in the cyclical flow, the subject is responsible for conducting activity that is usually prescribed, in a degree relative to the degree of determinism belonging to the cycle. Instead of gathering knowledge of qualities, in the spatiotemporal sense, on the entire cycle for achieving correctness in third-party observe-and-predict tasks, the first-party subject's cognitive processes fit for what comes before and after (stationary), or the specific tasks derived from prescribed responsibilities (mobile). The first-party subject's direct influence in the workings of the cycle economize their attention and efforts for direct application, via work, that could lead to an ignorance of the entire pattern and set of principles behind the cycle they are a subject in. The concept that connects the modus operandi of a hypnotizer and that of a derecognizer is "attention". Dedicated and concentrated attention from either the first-party or third-party subject is exerted, and these two classes of subjects are divided on the basis of two primary premises: the localized area/s of the cycle their attention is latched on to, in the manner of magnification, and their actions in relation to the cycle (observation & anticipation & prediction, or observation & anticipation & required work to fulfill cyclical iteration). Cycles that decline in effectiveness as hypnotizers and derecognizers inflame transient notions of doubt on determinism, and the terminal breaking of effects turns those initially transient notions into central foci of reflection and meditation for clarification.
ASOC2: A cycle
ASOC3: A group of nested cycles, such that the fourth cycle is the super-cycle containing the other three. Every point on an arbitrary cycle represents an event of qualities and occurrences that forms a part of its whole. Two attempts are made to correlate points of one "distinct" cycle to another. The attempt, in blue, is a linear angular approach (in the geometric sense). And the other attempt appears to be a more arbitrary one that uses non-disclosed correlation functions to map a point from one cycle to the next.
While both diagrams ASOC2 and ASOC3 are merely incomplete
and generalistic attempts to depict cycles, they do encourage
thoughts that lead to a few issues in cognitively processing
cycles. The issues on identification, preference, and
recognition in these cyclical schematics are a continuation of
the discussion on the cycle as a hypnotizer and derecognizer.
ASOC2 asks the question of how
Diagram ASOC3 shows a set of nested cycles, and this nesting lends credence to the notion of factual hierarchy in these cycles' relations. Maybe a cycle's attribute of being nested in another is the big condition of the cycle's subservience in control and influence to the other. Maybe the super-cycle is a governing player in a Game of Constant-Concern to its sub-cycle/s. Identification and correlation are oftentimes contrarian to one another. Correlation is part of conflationary reasoning, and identification goes down the path of observing infinitesimal uniqueness between candidates.
As already stated, hypnotic-like decision making, especially one that falls under the formulaic structure of a cycle, consistently depends on recognition mechanisms that intend to output identification of pre-determined values. When future events of one span are denoted as a particular cycle, the key identifying features of that cycle are observed in that span for occurrence. The rest, of variants and extras and negations, should be derecognized under the hypnotic state. In verification tasks, the belief is that the methodology works, but one iteration of the methodology may produce differing values. The cycle is a stabilizer that should not be changed. The cycle exists for a reason. Its use to produce the values that orbit it, the core, need to be ranked as second priority if the use to produce is really an objective. Run the cycle over and again, until the desired product values emerge as results.
Some more notions are fit to be mentioned about alterable
cycles. Diagram ASOC2 makes for a preliminary example on the
mutative cycle. The two concepts of decline and death can be
a part of certain cycles. The default cycle is a perpetual
entity. Once it is set into motion, its design independent
from external forces does not let it cease motion. Suppose
a subject first enters a cycle. Then at a checkpoint, the
subject ceases to proceed to the next checkpoint, instead
exiting out of the cycle into another. If the subject is
the only one that has entered the exited cycle, the cycle
ceases to be relevant and thus dies. The subject is a
cycle-breaker of an agent then, for themself
first and by their possible status of being last, against
the cycle. The non-constant cycle can also shrink. In ASOC2,
if the connection of node
Back to the topic of the individuality of the cycle, the design of a particular cycle could be suited to produce inputs for another cycle. A chain of connectivity could be an instrument additionally attached to a group of cycles.
ASOC4: A group of cycles. Every red or blue line represents a connective flow of select products from one cycle to the next.
Cycles can be demarcated into individual identities, but with the addition of a connective chain for a group of cycles, their individual identities mean little for individual values. The engineering of vulnerable systems for output, such that the components are preferred to be ignored in rank of value so that precision-based tampering is not as encouraged on the blackbox's functionality, demands a security that blurs any real demarcation. The connective chain is part of the super-cycle over the connected cycles. On what exactly is the cycle, individual recognition becomes a problem with answers of unscientific explanations, component-wise. A piece can be demarcated from the whole. But for some reason, it does not work when demarcated. And the whole has too many pieces to be given the sole identity through innumerable functions attributed to it. Oh, these localized-mutative effectors, these cycles.
The cycle is one of the cornerstones of scientific methodology: trial-and-error as cyclical iteration for wanted products that can be reproduced by the most accurate cycle of methodology. With phrasing that directly associates "error" with "trial", positive expectations of these methodological practices are halved. The objective of purely gainful value transfer from trial-and-error operations must have risk of failure. The cycle of trial-and-error for discovery is usually run in a localized zone. After the discovery, the most accurate cycle is practiced in other local zones, maybe in a "global" zone. The best cyclical methodology from trial-and-error is still a localized-mutative effector by its conception, however perfect, and is also usually modified to some extent for every application of different localities and globalities. Some cyclical methodologies cannot be so easily mutated,externally, to account for distinguishing traits from one applied setting to another. What necessity to run the methodological cycle, regardless, requires the marginalization of the distinguishing traits in the representation of the input, in effect marginalizing the surface of disapproving attack on the cycle. Pathologically-perceived inputs, inputs that would be misapplied by a particular cycle of methodology, can nevertheless be inserted into the localized-mutative effector. And then what. There is bound to be error from the cycle onto the input and maybe beyond. The particular cycle should not have been run but, by some volition probably self-claimed to be righteous without challenge if not for the judgment of its pathology by the results, the input was processed by it; the input acted as a catalyst for falsely-caused firing of the cycle. In the case of the finiteness of a noun to be used as input into a methodological cycle, the expectation of high probability of failure from the input demands false copies of the input to be used instead in the trial-and-error discovery. An uncertainty of success remains after the cycle has been corrected to the most accurate cycle, to be applied onto the real copy of the input.
Some particular arrangements of a dark light, phrased as the well-known Faustian bargain, also have a place in this discussion on cycles. The recipient of a Faustian bargain pushes for the deal of acquiring or fulfilling some thing. After there is that ideal granted to the recipient, the recipient experiences second-thoughts and unwanted events, all the while holding onto the product of the bargain. They think, because the ideal was initially too far away that they had to first experience and do certain things not fit for association with the product, then the ideal is no longer such since the consequences of those things' unwanted occurrences have inflicted changes in the shade of permanence, and what is left to enjoy is a begrudging mismatch. They could also think, because the ideal they sought was expressed to them in the past by select-hyperbolic fashion, the ideal cannot be a pure good when it is certainly more than those primes expressed in exaggeration. They go on thinking, to have reached the ideal and finally peeled off the surface display of the ideal for hopefully enjoying the ideal is a finalized bargain most regretful. Here are two diagrams for these thoughts, in order, left scant to preserve the honor by hiding the shame of all those that have fallen victim to these bargains.
ASOC5: The green circle is the natural setting of the ideal, with the ideal denoted by the red dot on it. The blue circle is the experience of the one before receiving the product of the Faustian bargain, through the exchange denoted by the black line.
ASOC6: The larger-than-life projection of the ideal leaves after substituting itself with the ideal of actuality.
So the ideal sought after in the Faustian bargain is part of a cyclical process that preserves its value, and the recipient of this bargain wrongly believed that they can be only positively connected in direct relation with the ideal, after exiting their own cycle into the cycle of the ideal. The Faustian bargain, as illustrated by cycles, serves as a competent example of differentiation between cycles, by their separate effects that should not have merged. The recipient of the Faustian bargain wrongly believed that they could merge their existence with the ideal, found in the other cycle, to finally achieve ideal living. And third-party observers conclude, without direct experience as evidence, that the recipient was incompetent enough to be blind to the merging forbidden, out of the unnaturalness, of two cycles best kept separate, although all that these observers could objectively perceive were events and losses, not the cycles themselves. The observers could probably conclude that the recipient of the Faustian bargain entered a doom-cycle, constructed with the forbidden merging of two cycles, but that is merely their theory if that is all to their commentary's thesis.
A technique, out of genuinely bad trickery, is given the name false-accounting cycle in this section's mention. For this variety of cycle, an event of some cyclical process is claimed to have occurred by one party to another. The claimant party lacks the evidence for the claim. So they construct an alternative cyclical process, and inject input from the base cyclical process into the alternative cyclical process. The alternative cyclical process is designed to produce effects in the likeness of the claims made, at least in the effects of the occurrence if not the occurrence. The other party does not know that any alternative cyclical process was used, and they are faced with the decision to believe in details not verified to have been associated with the base cyclical process.
The possibilities found in diagrams GBGD2 (underminement, section Wasting the Drive in Gridlock) and GSA (Game of Sliding Alliances, section Shifty and Shifting Alliances) are of helpful reminder in understanding the complexity of alterable cycles.
In applied theoretics of cycles, the subfield of physical offendors' use is a popular mention due to historical occurrences. And in virtually every instance of offendor success by use of the cycle, the opposition did not adapt for timely results of defense to the style of offense that felled them. By priming their specific methodologies for immediate lethality at every opportunity, there remains no chance for opposition's learnability of the problems most pressing to them. The cyclical offendors' effectiveness in elimination is because they kept oppositions' notions of them so broad and seemingly aimless, by fully taking advantage of their greater mobility into secrecy until the point of contact with the ill-prepared opposition. After what remains of the opposition past the initial point of contact within a span, the opposition struggles with a balance disheveled. The opposition usually expects there to come another point of contact, of time nearer or farther, from the cyclical offendor. But the opposition does not manage to formulate better tactics out of their strategy. So for proceeding points of contact, they oppose with their original mechanisms, with a disheveled and declining balance that has already ensured them lower potential of performance.
Many moralistic viewpoints have been expressed on the matter of the cyclical practice turned malicious against the other entity/ies. Viewpoints are now noted in general and pseudo-precise echoing. Of foremost prominence in the themes expressed by viewpoints is the judgment that there was a mistake, or plenty of mistakes, somewhere along the way for there to be this physical offendor's malicious utility of the cycle. Without the feel to mince words in this retelling, there is the belief that there is a mistake that corrects itself by correcting other mistakes, through control by techniques including containment, deprivation, forced role-playing amongst other forms of subjugation, as well as the broad field of terror tactics with tools of physical violence or undetected harm designed to be perceived as non-violent. For each mistake and the entity of that mistake, the separation is not there for them two, in order for them to be one and the same in the match-up between the physically cyclical offendor and the opposition. Ponderance on the total from any one of the two halves is already limited by the bondage of allegiance. So what if there is/was a mistake on one end acknowledged by that end, for they are to keep that acknowledgment to themselves, by the terms of their bondage. No authorization exists from either end to the other, for the other to issue non-destructive corrective criticism. Any attempts of this sort of criticism is rejectedly responded back by those that first invoked claims of hurt to their own cultural and other group-based forms of unity through bondage. The distinct ways of life are different because of the reason of choice and conviction, carried out in the duration of time's accumulated effects. There were attempts to unite for one economy of differences in one will's singularity. But that cannot be so. "Agree to disagree". "Make due with the differences". Statements of non-belligerence turned into icy guards, on one hand, and a patience of insatiable hunger, on the other. And then, the antagonism is pre-determined once commenced, a blind cycle liberated by the careless killing of gravity. What accountability? Whatever happens happens then, even if the cycle dies for it is the ideal that stands after death. Sure, the weaknesses of inequality from difference could have been fixed beforehand. There was knowledge of what strengths needed to be achieved. But those efforts would have broken the way of life, the ideals, and so, there is that.
Description of the problem of cyclical offense the opposition is forced to confront ensues. Deprivations unique to each of the two cycles are put aside by their own practitioners, of great dissimilarity, for long-awaited confrontations. The opposition is faced with one big decision on adapting to the physically cyclical offendor. They can choose to mirror or to wall. If they are to automatically choose the route of mirroring, they must attempt to surpass the performance of the physically cyclical offendor if they have not in the present. "To beat them at their own game, so as to humiliate them for our upheld honor". If they are in such a position as to be beholden to stationary practices, their drive to become more mobile is very difficult at the beginning of their efforts. And time is of the essence since their adversaries have commenced their offensive. Their forecasts of achieving this mirroring are almost entirely incorrect. The objective of putting aside their "natural" way of life for this mirroring is consistently protested against in internal affairs. There are big challenges in this mirroring. The physically cyclical offendor's practice is already perfected, by relativity metrics. And the opposition's mirrorization process means to train in an image at least partially prescribed, with the only real objective being the capability to counter the executable strengths of their adversaries. It is a decision of catch-up that balances with surviving legacy and custom. Such hardship in this adaptation route. Maybe with the wall, the physically cyclical offendor cannot push forward by their unique strengths excessive in relative magnitude.
ASOC7: A diagram that shows the two broad strategies
(mirror and wall) that opposition
An ill-prepared opposition that is positionally scattered across a field does have a greater chance of repelling if not defeating the physically cyclical offendor. But the greater chance is greater not necessarily in the absolute, but as a relative to the lone chance. This is simply due to the "many heads" the opposition has. The physically cyclical offendor that is effective takes at most two attempts to defeat opposition at a position. With one "head" down, there are that "many heads" minus one left. One aspect the physically cyclical offendor relies on, for effectiveness, besides from greater mobility and immediate lethality is the false-retreat, a technique made convenient by the cyclical nature of travel they take. The false-retreat fools the opposition into believing that they have successfully warded off the physically cyclical offendor. Here is an example of a prideful remark, spoken too early, from a spectator of a false-retreat: "look at the deserters flee away, the cowards, the disgrace that they are".
The Game of Mirror or Wall, as illustrated in ASOC7, featuring a physically cyclical offendor and opposition, is not one for a trivial opposition. An opposition, not of any roughly equivalent forward-offensive caliber, that wants to conduct a frontal assault against an incoming frontal assault from the physically cyclical offendor will be crushed. If the opposition retreats from their base by sluggish mobility, the physically cyclical offendor could very easily catch up to them and crush them. If the opposition wants to conduct a frontal assault on the offendor's base, the offendor would still crush them by advancing after they did, and beating them in direct confrontation. If the opposition goes by the strategy of the wall, they would have to ensure the wall can endure the offensive. Also, there would have be open routes, not accessible to the offendor, remaining to the opposition for supplies.
An opposition that is initially stationary belongs to one cycle. What they choose to do, after whatever decisions they have made to make an offendor out of a physically cyclical entity, arguably breaks their cycle of routine, even if they chose to not adapt by mirrorization of the offendor. The physically cyclical offendor, no matter their sheer power, operates by energy-intensive means. Their means are for the purpose of immediate lethality and accomodating mobility for that lethality, a purpose of ephemerally fatal offense. This kind of offendor dominates by their mastered hypnotic trance of violent engagement, a style heavily reliant on the rapidly paced patterned decision making that inflicts lethality. Just as hypnotized states borne from effective hypnotizers' application can be broken, the physically cyclical offendor can also be, as farfetched as this analogy reasons to. So certainly, there are instances where opposition used strategies of walls and mirrors, and bested the physically cyclical offendor.
Sometimes, the opposition unanimously fails. And then accountability would make claims of leadership issues. Here is one frequent claim that has been seriously entertained. The social order proved to be insufficient after the declaration of ideals. Certain individuals' interests were betrayed before the beginning of the conflict, and those ramifications overshadowed those individuals for decline before collective ruin, even after they forgave letdowns of them. Now this is not a good basis to begin with before the conflict. Here is a common feature of physically cyclical offendors that were effective. The cycle, even after opposition had learned it to the point of effectively countering it at local scales, continues its targeted domination by birthing traitors out of the opposition. The mirror strategy, with its drive towards the likeness of the adversary, does carry this risk. Here is a common-sense saying: there is loyalty, and there is bondage.
There are cycles of nature not easily exploited by sentience. Sentient design and corresponding use of cycles prioritize the recognizing of patterns over details, the correlation over the uniqueness, and the incredulity of what uncertainty the singularity can offer.
The theme of "alliances" in change-prone environments deserves a third section dedicated to it. Expanding past the incomplete discussions on possible graphical units available to model alliances, alliance factors ranging from single to multi-connected, a game on a particular alliance pattern, and the probable insufficiency of alliance factors in the numerical sense, the discussion now shifts to more specific techniques involved in alliances not of constancy.
The word "alliance" operates on social-based arrangements, despite the perception of any alliance's order or organized chaos, both mathematically imitatable. Scientific principles can be attempted to be set into place to ignite and persist alliances. There are methodologies to estimate the best mechanisms available, by selected variables available, to produce alliances between particular sentient entities. Methodologies also exist to attempt solidification or liquidation of alliances in a wanted timespan. Methodologies cannot be used to produce intangible or inherent variables deemed important, without there being at least changes in sentient will proportional in radicality to the rarity of the intangible or inherent variable. The condition of the previous statement does presuppose many notions, such as predisposition not necessarily being the constancy of particular outward expression. And perhaps these variables are the most valuable, what with the systematic production capabilities of sentience that can achieve past a relevant minumum threshold of competence. Therefore, many methodologies involved in the activity of birthing and maintaining alliances come after those things recognized as facts, and a notable proportion of these recognitions easy to destroy and impossible to accurately replicate in any timely manner.
Subjectivity is an interesting aspect of alliances. Participants of an alliance chose, through some majority-based procedure/s, to pursue the objective to "unite" by some degree for some activity/ies. In other words, they set that objective as the "truth" to aspire towards. This section's mention of the word "subjective" demands clarification. For some statement or material, there is a lack of agreement between sentience capable of judging its truth value, although it could actually be an unestablished fact. Questioning, reflection, and reconstruction of topics with implementation that is already of a high performance, according to specific metrics, is how subjectivity can be wielded as a tool for a challenger entity with an agenda. For example, a veneer of the subjective label can be placed over a noun not universally accepted as a fact. The subjectivity is there so that every sentient being that has a keen interest to involve themselves in the judgment of the noun's truth value holds onto the belief that their contribution's judgment matters. In some cases, the finalization of the judgment process is delegated to a small proportion of all those involved, in such a way for there to be a final judgment on the matter that was already "pre-determined", "pre-determined" because the decision was already accepted as fact before the proceedings of the total involved by their various mannerisms of analysis for judgment. Invoking subjectivity on a matter can be due to the cause of the invoker's lack of capability to independently act on the truth, whether to counteract or make use of by adoption. Processes that somehow transform subjective matters into belief systems believed by an alliance to be the objective (the truth?) are a priceless staple of the alliance's modus operandi, from core to execution. If the topic of shifty and shifting alliances required only one sentence for its cause, the sentence would satisfy by including the notion that the predominant cause is breakdowns by disintegration of agreement over the subjective/s, in unequivocating ways. That is elementary.
An alliance surely has to use concocted definitions at its inception, to be maintained or changed or discarded throughout the alliance's lifespan. Definitions, by the fact that their factuality is below the purity of facts, but representations/ expressions/ forms of facts and other elements along the spectrum of truth, place the alliance as a group with pivots through their selection. The breadth and depth, of what is expected by each participant of an alliance with regards to co-participants, is variable and the uses of setting quantities to qualities for the rule enables behavioral patterns to emerge. A behaviorial pattern can be divided into individual actions taken by each participant of an alliance, and the knowledge of such patterns serves as the first primary step towards comprehending the complex, contradictable, and physically removed effects of these patterns by permutatorial (participant,action)-pair attribution. An alliance's collective risk assessment of their capabilities and actual executions is a crucial aspect of discussion between their members. Strategies that members employ rely on tactics such as risk-dumping; by the perspective of valuing the identity (the alliance, a subset of the alliance, et cetera) over the other, members regard risk-dumping only as intuitively gainful if they are not required to explain any further. What makes risk-dumping so impactful, other than its affinity for application on zero-sum variables, is that it cannot be unequivocally categorized as a group-extrinsic outflow, at least according to the collective agreement of what the group is by the sentient participants. And by the lack of categorization, any alliance's usage of risk-dumping techniques, usually resting on mathematical principles for profiting of sorts, cannot be expected to abide by constants for constant effects, when natural laws do not have the inherent expression to restrict any possible decision in the dealing of risk. Although the statement does read to be obvious and another way of noting the lack of collective certainty when coupled with actionable notions of independent agents' "free will", the likeness is actually not entirely exact, but rather an implication that focuses on the autonomous' dealing with possessed risks through disconnective transmission (full transfer from one to another) and acceptance. For participants of an alliance, the fair distribution of the most accurate marks in risk assessment is also not guaranteed to be constant; an argument for the opposite as the predominant form of this information's distribution is actually more convincing, given practices historical to present.
The classic concept of the weighting scheme was put forth in the second part of Shifty and Shifting Alliances. The concept, with its many insufficiencies, does still discriminately serve the purposes of its proponents and opponents, alike. The constant is a localizable categorization of a matter's monotonicity. Users of risk-dumping techniques typically focus on the stabilization of their states and processes. For a little more clarification on how stabilization could be enacted, suppose that the states and processes can change, by allowance. But then, other factors such as capabilities and values are to remain in a satisfying range, so that the undergoing of change in those states and processes continue to serve at least one ultimate aim, arbitrarily-defined in this generalization. This generalization also works as proof for why participants of an eventful alliance would acknowledge, sometime during the course, that the definitions they used to erect the alliance are in fact concocted, although perhaps not by their own efforts. In other words, the definition could be expressed for the need to establish a basis of fact. The expression of the definition's expression takes forms that include imitation, reaction, and contradiction. So if the fact behind the initial definition, a product of select expression, is already beholden to favoritist interests, how can what follows after the initial be one and the same to the fact? The previous is an obvious factual chain, and does read silly out of its obviousness akin to the lack of need to remind.
Denunciations of alliances, by arguments on their lack of an arbitrary constant, are insufficient for their rejection. These kinds of denunciations place the requirement of the lack of motion onto the alliance, in order for that alliance to be one satisfying to all members. The requirement, from the pure and absolutist sense, is unreasonable. Alliances do change in appearances and behavior, despite what definitions are adopted or continue to be adhered to. And that poses occurrences that demand attention to the differentiating labels of "shifty" and "shifting" for alliances.
Risk-dumping techniques are carried out in two main areas. An executable objective is:
- assigned, with an associated estimate of risk attached, by an alliance to a subset of the alliance participants to attempt, or
- wholly abstained from by the alliance.
The destinations of possible failure intended, by the selection of one of these two areas, are (in respective order) the subset of the alliance's participants and no participants of the alliance. Attempts to curb the non-null probability of certain risks' adverse effects rely on more considerations than simple assignment. In terms of psychological economics, there is the fear of failure that dominates the choice towards the decision of rejection, and the gains unmet from that rejection is what is lost. There is also the loss from the positive action taken, as rejection of the fear of failure that turned out to actualize. Forecasts on each of these two ways mate to form the shadow over every decision junction an autonomous entity has to make in the path with non-absolute predictions in outcomes. This explanation pre-supposes that an alliance goes by the principle "not all eggs in one basket", a frequent rationalist approach that falls under risk-averse decision-making.
RANDRISK1: A diagram that shows an agent
Diagram RANDRISK1 is an example of nonlinearity in payoff from risk to reward. Risk, in terminal forms, assigned to specific participants would mean that over the temporal course of events, where all non-zero possibilities are eventually reached, those participants have higher risk of termination. Allocation of risk to specific participants, on a constant basis, could prove to be a persuasive point for contention in environments that nurture challenger initiatives. In the second area of risk-dumping, for an entire alliance to abstain from something recognized as both risky and value-producing, the rationalist alliance must not have at least one of the proper capacity and capability.
An alliance's utility of concocted definitions is frequently for constructive purposes; the definitions serve as units to build for their system of holistic and component-wise choice. Here is where the idea of passive control injects itself into the alliance's modus operandi. There is an alliance, and the alliance was able to persist by the unity of their participants. The alliance was able to make constructive uses of their chosen definitions for a system with possibly evolutionary capabilities. Very little sentiment for that which is not of the system, even the definitions for the system outside of the context of the system, is a trait of an alliance dependent on their system erected, while tending to interests vested elsewhere. Once a workable system is intent on acting in the accordance of the alliance's goals, the alliance is granted several freedoms. The alliance does not need to expend as much cognitive effort, in the manner of roundabout calculations and extraneous learning processes, on tasks that have been accounted for by working processes of the system. This is a form of automation, and is the premise behind the power of automation: passive control by the sentience in charge of administering that system, since the sentience does not have to be the direct actors for those processes delegated to that system. Then, at least there is the freedom of passive cognition for tasks previously worked on. The construction of the system, by concocted definitions, could lead to complications of the decisions in its utilization. What is designed to promote passive cognition on certain tasks could be used in semi-autonomous manner by participants that aspire towards exerting what they believe to be direct control on the matters of the system's application.
An interesting technique, given the name "passive- deconfliction scheme" in this section, is sometimes used by an alliance in their procedural functionings. Passive- deconfliction schemes constitute a class of risk-dumping techniques, and could entail harm to specific participants of an alliance's use. These schemes are used in settings where there is the notion from the alliance that there is a threat. The objective is to guard the most valuable subset of participants in the alliance during this ongoing threat. The base move in these schemes determines the best candidate, of an alliance, for each action or agent of this threat. The candidate acts in the role of a neutralizer to their assignment in the pairing, and the pairing could be entirely neutralized in its duration of activity. The naming, passive- deconfliction scheme, does sound fancy and unnecessary. What has been described on this concept is essentially a prioritized layered defense system, such that each "layer" is one or more participants of the alliance; the prioritized layers cannot cave in to the center lest the alliance concede. So that feature, by itself, is far from original. However, the phrasing of this concept implies some additional attributes to be clarified. The passivity of these schemes is guarding the active representation of the alliance; this does imply the alliance to undisputably have a hierarchy in these contexts. And the term "deconfliction" is used by the alliance to signify an innate benevolence forced to take active measures, possibly archetypal of malice, against a threat; stated goals are to reduce the conflict, for conflict to not spread. But the phrasing makes no mention of restrictions on participants' enjoyment of the conflict in pertaining situations.
Passivity is a quality related to alliances, in more ways than in "conflict". An alliance's system construction and utility, by the use of concocted definitions, allows the alliance at least the freedom of passive cognition. There is no universal specification on what this freedom could mean for an alliance's benefits and losses. Debates, by the stance of nurturing complacency, are common settings for system analysis. A few common patterns are attached to systems use, in the practical field of resource management. In growth and adoption of materials and techniques not granted at the intrinsic level, the graphical pattern takes one of two general forms: the flat line and the upside-down V. Flat lines are one of those conservative ideals that are all virtually defied in the longevity of spatiotemporal challenges. For a particular system that is argued to persist in the way of a flat line, rhetoric attempts to persuade by noting the surviving ideals, outlooks, and practices that have continued on, whether intactly or through "evolved" forms, for the body labeled a system now to be associated with, in the same vein, the body of the past that was under a similar labeling. Passivity is a factor that presents itself through many variables in systems growth. Honest attempts to understand an alliance in the systematic sense must consider how passivity can "pull the strings" of the system that has supposedly gained strength through satisfaction of proposed system requirements. Two phenomena, growth and change, are the basis of operation for impactful game agents bent on pulling the strings belonging to a system.
The concept of "pulling strings" is used to illustrate action, by either internal or external origins, through utilizing a system because it is an adequate metaphor for system usage, automation-like, after the construction and embrace of said system. Automation has already been mentioned in this section's description of system construction, specifically for contexts of group-based unity and decision-making, an outsized consideration in alliances. "Pulling strings" instead of acting by one's completely owned mechanisms is a form of passivity, by individualistic metrics. By the metric of satisfying unifying means for unifying interests, alliances are burdened by constant decisions to take the prescribed route, in other words, to adhere to and use due process for what is recognized as problem and solution, alike, for the one reliable solution is already the system that was erected on the premise of correctness, by practical merit and universal ideal. Acting by these prescribed routes of some system is inarguably passive. The impressive feats of accomplishing much, "seeing things through", all the while having to tend to an established system are the successful halves of results from "pulling strings". It is these successful halves from the totality of results that perpetuate conviction in upholding the system. Growth and change constitute bodies of activity that are quite meaningful to system adherence. Consider an alliance that currently has capability issues in acting by their prescribed formulae. And capacity issues, with regards to current participants of the alliance as well as accomodation of novel non-participants into alliance membership, make these issues more dire. Growing membership is not a top priority of this specific alliance; "holding onto what is dear" has already burdened their collective attention span. But the alliance cannot "forsake" on what demands and duties they are originally charged with.
RANDRISK2: Two members of an alliance,
Some attributes are present in the supply-demand relation
that is shown by diagram RANDRISK2. One is the lack of binding
responsibility from
This specific alliance is also intent on maintaining a "monotonicity" in decisions to act, with aims for the expected and actual effects from these decisions to be predominantly one and the same. Here is one aspect where tasks of perceiving stability frequently occur. Being categorized as "stable" is the positive end of "monotonicity". "Monotonicity" is achieved by acting in the least contradicting manner, in reference to the rules and procedures of a system. "Monotonicity" may mean to disregard calls to hasten due process for timelier results, or to delete or add elements for improvement to this system. Consistent use of mechanisms in the alliance's internal setting is a mark for monotonicity. Dichotomizing the workings of the internal setting (active representation of the alliance) and the external setting (other participants of the alliance, affected non-participants) is a balancing act, and results are advocated to be measurable along monotonicity metrics. "Monotonicity" is challengeable on the grounds of the lack of universal cause-and-effect; such lack is named "hypocritical" by opponents. Suppose the alliance is faced with a growing concern from non-participants. These non-participants claim that they do not wish to antagonize the alliance. Their demand, as the growing concern, is not solvable by the alliance, due to a combination of resource limits and contradictions to the alliance's due process.
RANDRISK3: Programmatic function for an alliance
Some idioms impose remarkable influence on matters of this kind of decision-making. One of them is something similar to "give an inch, give a mile", an absolutist belief on the lack of limits for the magnitude after any lone possibility is enabled. There is concern over the directionality of the course of events, transpired all due to some arbitrary degree of enablement, with respect to some thing. Objectives, revolving around abiding by this idiom, fall into one or more of these general categories:
- recyclable enablement: reciprocated in some recognizable and positively usable way.
- nonconsequentially antagonistic: support does not directly result in the nurturing of a relatively formidable adversary.
Reneged deals, in forms such as pathological supply, are frequent decisions made by alliances, out of the actuality that took place to deter the alliance from finalizing the deal, from proposition to agreement to satisfaction. Reneged deals defy the expectation by deliverance of the expectation's lackluster alternative. Pathological supply primarily works by substituting parts or the entirety of the deal with something existent. Economically, the substitute tends to be cheaper (not as valued by standard valuation). The pathological supply is to push the substitute into the role of a quasi-permanent alternative to the substituted. There are initiatives to "maintain the balance" of meeting the demand, the objective, through this primary route of a reneged deal.
Identity is a hefty topic of discussion in alliances. Equations could be posited in mathematical form, but the more simplistic variations seldom suffice anything but simplistic statistical demands. So there then is the question of preference for the simplistic in practical matters, which becomes a discussion about culture, ethics, and material values. Quite subjective and lengthy for any meaningful discussion that can borne practical novelty and insightful revelation. Here is another subjective matter. The unity fiasco. What is not the same to something at the beginning can questionably become different to its self and very much the same to that something. And what is not different at the beginning can questionably become different to its self and very much different to that something. Acceptance is a necessity in the incorporation of these two possibilities in unity. The unity fiasco occurs when there is just no way for some things to be accepted. These things can change over the course of time to satisfy the expectation. These things can retain their original identity. But there is just no way but conflict if those things are to be positively elevated. Essentially, compromise cannot be ever reached in these situations. The coupling of unity with fiasco describes the pathological and irrational propensities at play in wars of desire VS will. The unity fiasco takes place at a few important junctions in certain alliances. Alliances that are based on hierarchy have their own ways of ceding power from one participant to another. On the one hand, there is the desire to retain the image of the predecessor. And there is also the reconciliation of differences in order to keep the form and function of the alliance intact. Such reconciliation could ironically demand a participant that would not keep the alliance's form and function intact. It is about the details of how, what, and when the form and function are no longer intact that seem to slip away into speculation zones for these most uniting points of alliance.
Alliances, as organizations with their structural processes, can depend on a strategy named minumum-in maximum-out till termination (MIMOTT) for collective efficiency and conservation of the active representation. MIMOTT matches each participant with their "most fitting" role. The participants acquire the skills necessary to excel in the role, at a level much greater than their counterparts if the counterparts were to have attempted to do the same (maximum out). In hard terms such as temporal and spatial measures, these participants matched with their respective role cost the least (minumum in). One more condition is attached to MIMOTT, in order for the optimized input/output values to hold. The efforts that each matched participant take must not be constructive towards their breaking out of their matched role. Metaphorically, the potential of each participant's enacting systemic change is a stump instead of a tree. In mathematical terms, numbers in a structured form solve for MIMOTT's optima. MIMOTT may run contrary to meritocratic principles, simply due to the fixture of participants into roles. The participants may have actually opted for something else, to break free from their assigned responsibilities for responsibilities of a similar if not greater level. The optimal matching of MIMOTT is done only once. Over the trials of time, participant-role matchings may not be beneficial to the participant. For example, the participant has to do heavy work, but gets paid less than another participant that does not have to do any of the heavy work, only the accounting. In role-switching, the first participant would easily pick up on accounting. But the other participant would not be able to do the heavy work. There is a lack of dynamism that negates challenges to positions for possible lack of robustness in MIMOTT, a strategy that attempts to place excellence found at the beginning into permanence till termination calls for a new participant-role matching. Alliances that depend on participant-role matching, in any form, to satisfy their ongoing objectives may be vulnerable to a type of influence attack: the functionary-allocation attack. The attack's objective is the complete opposite of merit and efficiency in the placement of participants into roles. Serious effects from mismatches include stunted and/or imploded alliances.
Perception somehow has to produce meaning. The lone memory, accurate in the short time after its birth, eventually fades away in the sense that recollection must work harder to reconstruct towards its fullness; the memory is no longer wholly withdrawn from a base into active cognition, and the active cognition has to process additional steps for that lone memory faded to be brought back to life in a distorted form. The descriptor "distorted" may be a disagreeable term to the recollector. The recollector could state that their recollection is, in fact, authentic but not wholesome. A differing perspective would counter that the recollection is not authentic because it is tidbits of what happened, and these tidbits are typically both most memorable and picturesque to be recollected for a supposedly accurate form. So there are questions of the recollection's wholesomeness, and the authenticity of the remnants that is the recollection of the memory now faded. Section How Obtuse Judgments Can Count contains slight explanation on the differentiating lines between perception and judgment. The ensuing discussion attempts to capture more explanation on perception, using conceptualizations of that thing called pride, and extending out of simple juxtaposition with the concept of cognitive "judgment". In this discussion, the conceptualizations of pride may actually outweigh perception in the lengths of their elaborations. The choice to use this theme to elongate discussion on perception is due to its real and far-reaching effects on sentience that can operate on both "individual" and "group" bases. From certain perspectives, the concept of "perception" is not confined to the one scope of external phenomena's effects processed by simple sense/s, for the resultant to be a feeling or memory. There would be only two aspects to discuss for this one scope:
- "accurate" initial processing of the external phenomenon via granted senses;
- accurate recollection of the initial processing into active cognition.
There does not appear to be a universal formula or set of formulae for delineating "perception" from the factors that produce or influence it. However, the notion that competing formulae can serve as equally competent solutions for modeling this task is valid, by using claims that rest on the similarities of accuracies by select weighting schemes. "Pride" takes a high-ranking spot as a relevant candidate out of these factors. It contributes greatly as a motive to recognize or filter information. "Pride", taken up into individual or group cognition, deflects itself from its base word into a multitude of values for thoughts that are either internally secured (arguably labeled as "repressed" by certain cultures) or actionable. A lot of notions, sometimes presented as pure truths, have been put forth on "pride". The concept (pride) does make for an easy topic to denounce from a moralistic perspective. It is the number one sin out of the Seven Deadly Sins. Conversations on this particular concept sometimes lead to admissions of some kind of fault for the purpose of correction towards "balance". Other times, there is only the acknowledgment of such a force, and an underlying drive remains to forgo attempts to change activity, stemming from this force, via entire elimination of it from all levels of cognition. Dishearteningly, from a great number of perspectives, "pride" along with its six counterparts constitute unkillable forces very much like essential ingredients for a specific food recipe. Things would not be the same without pride. "Pride" is one of the more difficult of the seven to recognize by a universally accepted methodology. It splits itself into a multitude of values, intangible and imperceivable to external sources of sense. Unlike lust or gluttony, for instance, pride does not abide by such direct cause-and-effect patterns. There is hubris, the extreme variant of pride, that is easier recognized after events that fall under categories of grievous mistake. For behavior to be recognized as prideful, there is the need to rationalize a metaphysical backtracing path from the behavior to the intangible and imperceivable pride. "Pride" is but a subjective term in many analyses. The term can also be a derogatory label, usually given by an adversary of some sorts, for the agent of some behavior. This section's coupling of "pride" with "perception" uses conceptualizations that are relatively simple in quantification and visualization, instead of narrating over select phenomena believed by some to be representative of "pride".
Pride, in the realm not necessarily to be entirely reserved to human beings but to sentience in general, is a motivating and controlling force before the perception, and a reactive force after the perception, despite how accurate the perception can be without any additional drivers connected to it (if that is even possible). Consider perception as not a default immune to partiality. On the converse, perception is an act attached to objectives that do not have to present themselves in such forward fashion. Objectives can be expressed in fashions of universality: "eradicate poverty", "war against drugs", "kill the corrupt", et cetera. The methodology that judges the objective as a singular expression, void of nuance, to be a rightful universal must be at most agnostic in belief to the possibilities, actualized or not, that constitute the means believed to be necessary to satisfy the objective. Critics of particular means would expectedly use words such as "blindness" and "perversion", very antithetical to the nobleness that objectives must carry to retain and perpetuate believership. There are some that argue that their own believed rightful universal is at least agnostic in belief, that they are willing to do whatever it takes to achieve their wanted marks of success. The rationale, on why the statement of the rightful universal is at most agnostic in belief, is due to the double-sided nature of progress and infliction; what is to be done to the other in the name of the universal cannot be done to the self, out of sanity. This is a rationale based on the reference of selflessness contrary to the opposite, the self with directed interests that would inevitably be called "blind" or "perverse" by opposition. Opposition, in general, does not have to be constrained to accuracy of perception, and this opens up possibilities for them to arbitrarily label any initiative as "blind" or "perverse", regardless of the initiative's strict reference to the self or selflessness. Because the reference of selflessness is not as concentrated as the lone self, criticisms tend to be geared against the "negative" (non-existence, negligence) marks of the selfless, which could then be defended by the selfless through their posit of no accountability or control. Criticisms of the self, the self being one that yearns for singular attribution, focus on the "positive" (failures through attempt, ignorance) marks. As with the absolute split of qualities found in typical dichotomies, this dichotomy of the self and the selfless, in the context of believable criticism, is imperfect and usable only as a preliminary metric for further judgment. The truth and the action do not run in forms parallel to each other according to a universally believed natural order, not when there are objectives by pride of the self, the group, and the selfless. The phrase "universally believed" is synonymous to collective sentient agreement, in this context.
Perhaps these next statements are more than half-truths on the ramifications of "true" pride. The prideful operates by principles that they do not want to violate if they had the liberty not to. The prideful does not want to feel humiliated or belittled, and as such, tends to act in ways that do not risk their being put into situations that promote these dynamics. The prideful has an intimate and binding relation with their identity, in self and group forms. The prideful is a resolute and self-enduring entity. The prideful responds in unyielding tones to demands that they do not agree with.
PPP1: Two automata that show how "pride" and "lust" act. The diagram for "pride" is more open-ended than lust in a few aspects. One is that there is no way for the "pride" automaton to terminate. The agent that the automaton models can oscillate evenly between "pride" and "no pride", or preside predominantly at one of the two ends. The possible actions that "pride" can take are not shown in the automaton, only their orientations (pro,contra,?) according to an axis. There are no rigid definitions attached to "pride" or "no pride" in the automaton. The automaton for "lust" is more narrow in scope, and can act as a template for demonstrative testing of an agent for their possibility of being lustful. There is a way for the "lust" automaton to terminate: the agent has conclusively demonstrated "no lust".
After the diagram PPP1 that models how "pride" and "lust" behave, a last statement on "pride" is in order: "pride" is a great mystery, in many of its forms, because the prideful can be unusually deceptive to accomplish their wanted tasks. Perhaps "pride" is not the word. Perhaps?
The focus now shifts from incomplete illumination of the concept of "pride" to its influence on perception. "Perception" has not yet been abstracted into a logic structure in this section. A model for "perception" takes the practice to be extendable and reducible subspaces of total cognition; to clarify, total cognition includes the "sub-conscious", sensory input (commonly termed "perception"), the "feelings", the "ruminations", the "hypotheses", the "conclusions", and any other additional thoughts not encompassed by these quoted terms. An example situation for the perception logic structure's use is now put forth:
- A man with a clenched fist walks up to you.
- The same man throws a punch at your face.
- You duck.
A competent perception logic structure for this example helps produce an information sequence in this likeness:
- Detect threat situation.
- Detect threat.
- Avert threat.
The perception logic structure should immediately correlate (map) the clenched fist to a threatening sign of body language. Afterwards, this same structure should map the threatening sign to the actualization of a threat. In abstract terms, a wholesome perception logic structure has to map the raw input, collected by the senses, to what that raw input "means". Diction is at play in this logic structure's design. What that raw input is mapped to "mean" could instead be labeled the "judgment" phase of cognition. But another valid labeling for "judgment" would be the statement that the threat actualized needs to be averted. For this to happen, the perception logic structure should immediately map the clenched fist to a threat, and perception would have to heavily be in use for events of prolonged physical altercation.
PPP2: An abstraction of typical artificial neural networks,
albeit with more "humanistic" labeling. There is the input, and
PPP3: The aftermath of the input processing from diagram PPP2.
The specific judgment produced from diagram PPP2 prefers additional
processing to be done via the route at head
Section How Obtuse Judgments Can Count mentioned two models, the perception-first and judgment-first models. Diagrams PPP2 and PPP3 further illustrate those two. Judgment matters. In the continuity of sentient existence, judgment could very well come before perception at some points in time. It is the specific judgment that determines the focus (synonymously in this usage, the objective) of the perception logic structure. The sensory input into the perception logic structure could remain identical throughout the processing; there is no additional meaning to be gathered in this possibility. For additional meaning to be generated from the initial sensory input, there must be non-identity mappings that observe subsets or the whole of this input.
Pride supposedly presents itself in some forms through all of this processing from sentience. For one, pride acts by certain cues, recognizes certain symbols more than others, and can act as a random-like self-driving force that propels objectives out of rational-like belief. These conjectured traits of pride all lead back to the identity of the prideful. In cases where there are differences in the sensory input, no matter how slight, two differing possibilities for a formulated judgment could lead to vastly different conclusions (final judgments), via derivation from different segments of the sensory input through the perception logic structure (equivalently, interpretation).
The common notion that every decision bears effects, great or small, mean things in terms of the outcomes. In the real sense, these outcomes are the spatiotemporal details affected by decisions, through promotion or demotion. This notion opens up another medium for pride to inject its influence. The concept of situational engineering (an entire section has already been dedicated to the concept) is what pride can do, not independently but as a potent factor. Sources of perceptual processing are not necessarily stationary. Pride, as a determinant, in the decisions made then places these sources into spatiotemporal settings that otherwise would only have occurred through drivers other than pride but of similar wants. The interpretability of the lone word in use, coupled with diction that prefers one word for another likened as a synonym, incur difficulty on the perfect attribution of pride to a vastly different sequence of decisions forced to be taken. An analytical statement could be expressed as: if it was not for "pride", these events of these descriptions would not have occurred. Without further details that eliminate extraneous possibilities for a constrained context pertaining to this statement, substitute words for "pride" could be "ambition", "haste", "anger", "hate", and "love"; practically, any noun with a non-null scope of influence, with respect to the open-ended context, would do.
In standard English dictionaries, "pride" has an alternative definition: a pack of lions. For continuation into another aspect of pride's coupling with perception, the condition of the being being the lion is extended to any sentience that operates by group-like principles. From theory to practice, metrics ascribed to the measurement of a pride are expected to output non-null values for the pride's tight-knittedness. Non-negligible factors are present in a pride for its members to continue co-relations not of a souring or soured tone, sweet only on the tongues of feudalists. This does appear to be an off-hand remark. The statement is derived from feudalism debatably resting on a sour centrality of goodness, by default. Pride takes shapes that convolute itself, quite frequently, with wrath and strength. This convolution demonstrates the difficulty of containing, let alone pinpointing, pride as the culprit behind some action taken believed to be the means appropriate, based on the judgment derived from the possibly long process of perception that led to the decisive interpretations for it. Tasks of identifying purity of metaphysical forces, as drivers for specific actions, is difficult to conclusively agree on. The use of "conclusively" is to signify the lack of any possible differing statement that is believable in presentation, not the lack of debate in the setting of deliberation. A pride united in perspective on a statement would not act on any motivation to debate, but the perspective is conclusive only to them. The social sciences allow "wiggle room" to independently extend the conclusion for some yet unconsidered purpose other than the retention of the original ("pure") meaning. This poses one classification of complexity for pride's identification. And to recall on this section's previous mention of linguistic complexity, there is also diction and the lone word given new meaning under particular uses, outside of the default.
A pride, taken to be a term synonymous with "group", has properties of tight-knittedness that cannot be conveniently manipulated by those not of the pride. The pride, due to both the lone autonomous capabilities of its members and each member's distinguishable identity, has the liberty of many faces. Even absolute uniformity becomes differentiable through tag-like identifiers and independent experiences. And the term "face" is not a strict association to that anatomical part of the human being, most distinguishable to the naked eye. The "face" has a personality, per se, with talents possibly of categories unique amongst peers. And these talents are evidenced through the work of the "hands". The "face" and the "hands" could very well be synonyms for one another, in group orders where appearance is submissive to the work. The tight-knittedness of a pride, intent on remaining a pride, does not concede elements that could be directly used or exponentiated for that pride's disintegration. Prides are vulnerable, and unanimously successful prides have great control over what continues to enable their constancy if not flourish. The concept of control is conventionally illustrated with physical apparatuses such as strings and chains, and in actions by effective grips and commands. Subservient relations are shown through these illustrations, and the directionality of effecting influence is predominantly from one source.
An entity, not part of a pride, enters the setting of
the pride. The pride appears to have more than half-like
degrees of control over its domain, but the entity's
perceiving of the pride's absoluteness in control is
not there. The entity's intuition advances them into
the pride's domain, for the objective that they believe
feasible of wanting to accomplish an
Is pride something like a business that can grow larger than its respective source? Businesses that were able to grow also tended to preserve their brand, their "image" and "values" as makings out of predominantly their independently adopted practices, per se. A category of alliance, on the spectrum of absolute adversary to absolute ally, is the gray-zone agent. This naming is only natural, in line with the classic black-white dichotomy that so much intellect has been dedicated to in the fields of ethics, cultural studies, reason, and religion. Out of the prideful prerogative to preserve the constructed "image" and adopted "values", many candidates that would have otherwise achieved much, for a pride, by first gaining acceptance into the pride are instead cast aside, like homeless dogs too domesticated to be as self-sufficient as wolves, like material for "cannon fodder" in a cold and barren world, prone to hostilities of monstrous forms and titanic magnitudes, outside of the pride's domain. Gray-zone agents are forced to operate by principles outside of the sentiment for the symbol, the status, and the affiliation, quite simply due to the design of the directional flows of gains and losses with respect to this agent category. Without sentiment, there are only such things as material goods, acts of gratification, and forms of bondage instead of the connection by genuine affection of loyalty. Ultimately in the economic sense, moral protests against gray-zone agents cannot produce permanent changes of their inclusion into a pride, without there being replacement or conversion in observable form. Gray-zone agents are an inevitable byproduct of the central product that is the establishment and legacy. In an attempt to further express this idea in the "language of poetic justice", the grayness reflected back from the gray-zone agents is the truth of the light that hits them. A scientific principle turned quasi because of application onto a category of social constructs. But the designing and directing of perception holds in stable or confirmed settings. There is a pride. The pride has this image and these values. Others can choose to align themselves with initiatives put forth by the pride, but the pride cannot let those others completely in, lest they change the image and educate the others on the ways of their values, efforts that could prove quite expensive in monetary terms alone.
Inflation and deflation, two concepts studied extensively in economics and fiscal policy, are also heavily used by pride in its communicating of its self. Inflate the communication of those traits the pride believes to be the "positive", and deflate that of those the pride believes "negative". A pride willing to take their unfairness further would also apply inflationary and deflationary measures on the other in directions inverted to that what it does to its self. Where is the truth in this affiliation of pride with inflation and deflation, when it is pride that believes it can rightfully inflate or deflate? And it is not as if inflation and deflation are those two moves specially reserved for pride's use. There are objective identification issues, as already exemplified but not fully on pride.
Can pride be operationally principleless? Structure cannot exist without principles. An unrevealing statement, yes, that intersects the meaning of "principle" with "structure". A sentient being, recognized as representative of pride, can still be representative of pride after disregarding a principle, either they themself stated or was noted by the other. But one transformation could lead to another. The prideful would be unrecognizable even to themself after bending and conforming their behavior, careless to their principles, for many transformations that take effect in internal mechanism of their self and external observation by their non-selves. The quality of pride being unyielding, noted in the beginning of this section, would be broken by all of this untempered transformation. Pride's counterpart, wrath, makes itself present in situations such as rapidly released energy, the temporary breaking of a principle, and wants repressed into a state believed by observers to be dormant and withdrawn. Wrath appears to be principleless by its lack of predictability from some observers. It is what the observers do not see, the negativity absorbed by wrath's hosts, and what the same observers choose to disregard as ramifications of what they can see, such as their untoward words and actions, that compose some of the most unpredictable wrath. If pride were really in charge, it is as if wrath is just another one of pride's sidearms.
There is a common saying from those that have felt insulted. The saying is: "my pride is insulted". The concept of pride is already of dubious sense in exactitude. If the person that said this is actually prideful, in the sense that their pride is self-generated, they would not feel insulted. But if the person's sense of self in the context of their identity is believed to be defamed by the other, then they have the right to state that their pride (identity) was unrightfully given bad note, in defense of their pride. These are stylistic differences in the mention of pride by the supposedly prideful. Pride, that unkillable force due to its innateness and virality, is nevertheless practically finite in each of its hosts because the hosts themselves are under the scientific clause of mortality. Next is a question to end this discussion's examination of pride against its insults: how many poems and law books can be written for that most romantic and regretful chagrin, all because a pride thought it fit to fight fire with fire and poison with toxin, when it is the process of perception constituting the interpretation for that judgment call? To insult one's pride is to insult one's self, is it not?
To walk with pride is to walk with confidence, an analogy that designates compatibility of pride with confidence, as if them two were meant to be until the world ends. Confidence has a statistical measure for it, although the measure is still numerically based, leading to the possibility of protests against the measure's use as true representation of confidence. Confidence is a predictive motivator. Behaviors are modified, farfetched possibilities then but now the ideal set as the objective, and other effects of cognitive changes are present with the elevation of confidence. The confidence placed in the hypothesis of the existence of something, for example, implicitly places demands onto perceptual processing. Thoughts such as the high chance of success and the great gains from that success modify perceptual processes, indirectly through the alteration of judgment. A judgment adjusted (any confidence) or skewed (false confidence) influences perception to note any information that has semblance to the actualization of what is to be done because of high confidence. Imaginary connections are drawn between tidbits of the entire information processed by perception and the expected that is the desired future, due to that high mark of confidence. Nothing can prove confidence wrong without error that kicks back with the impunity of natural law at work.
There is always something more to be expressed about pride. In this second edition, some more characteristics arguable as features of pride are presented and detailed. But the vast field of the intersection between pride, as a concept not entirely describable due to either inadequacy or inaccuracy of the transcription from the manifestation to the written word, and perception, quantifiable and simulatable but with individual experiences not replicable without fault, means this second edition will also fall somewhat short with respect to the grandiose of pride's role in one of the greatest paradigms for understanding, perception.
The prideful unfulfilled in their self-belief, unaccomplished in their stated mission, and trivialized by their peers entertains the idea of feeling a sense of doubt after their cognitive feedback loop crashes. Praises turned out to be faked or mean little, reward systems were upended all of a sudden, and the "promised land" was never met. A critical point never thought of by the prideful to exist is then a decision junction just up the horizon. The prideful could retain their image, with the necessity that they project the image, but have to fend off the rejection by pushing forward with more aggression than the kind that signals grace by not "losing face". One retreat back leads to a long string of losses, and the prideful may feel they have lost all right to being so. Suppose the prideful seeks to survive, and survive they do. They resort to admitting defeat, and feel the damages right down to their psyche. To admit defeat because that is the only honest thing for them to do, but to crave for a future victory of some kind, reaped directly from those that beat them, is a closed door to the prideful's dominance and an open door for the prideful's transformation into a jealous and underhanded type. Ascribing principles of comprehension and prediction on pride's handling of defeat is not something like solving a mathematical equation of a standardized format. This has been exemplified in the first segment of this series, specifically pride's convolutions with wrath and confidence. Pride and jealousy are two forces that may share characteristics by the same host, the identity in physical form in other words. But there is one fundamental difference. The prideful believe themselves to be the "source", while the jealous believe that the "source" is false and that they are the rightful "source". To be the "source", by the standards of pride, is to first and foremost be one with the power, not necessarily the ability to produce more or better, to think and perform better; however, testing and beating the prideful is constrained to achieving superiorities over them in these fields. The notion that superiority of a field can be unequivocally measured in a local field that reflects truth back for the recognition onwards to a global field is another matter of debate, much to the contempt of the prideful's possible want of peerless absolution. Denial is one possible decision for the prideful if they lose.
The prideful has two categories of factors they have to weigh: peerless recognition, that they may share traits of similarities with another one but they themself are ultimately the "source", and equal competition. The prideful believe themselves to be undisputable by many benchmarks, this privilege granted to them through their high marks that may not have had to been achieved independently by them. But the setting for the achievement can never be universal. Many times, there have been attempts to propagate the local setting for achievement into universal application. And every time, there has been marked resistance to that adoption in one form or another. Implementation of competition is usually designed to be probabilistic in outcome. Events that are called competitions, yet with outcomes already pre-determined by the primary decisive makers cannot honestly be called competition; "performance" and "demonstration" are labels with more transparent underlying implications. The prideful, in their attempt to appear fair to others, outwardly promotes competition for talent: "may the best win so that they get what they deserve". Self-interested practices encourage the lack of compulsory competition, that every one has a fair chance of having to compete in the competition that cannot be implemented in a universal setting, by default of resource limitations and shortcomings in compliance. It is these self-interested practices that the prideful carefully leverages. The prideful can choose to compete in a setting of their choice. They can also abstain. In terms of power dynamics, the prideful would rather rule and regulate a competition if they already see their chances of victory by their involvement unsubstantial, yet must still play a relevant role. These statements on the prideful may reason to be off the mark. In fact, these statements are off the mark for the extreme variant of pride, the hubristic. The hubristic compete when they feel as though they can, and pay little regard to the warnings derived from both empirical probability measures and intuitionists. In the typical case, the prideful have a status, unique by some marks, that they have to stand by. This obligation means the prideful do not have to be bound to compete and challenge at the same frequency as the hubristic, for the prideful usually do have something unique to be proud about, to value and guard as if the thing/s were their actual organs. The demand from a rival to compete turns into the prideful's choice to respond with anti-competitive measures. Words such as "dignity" and "honor" are used by the prideful to claim a kind of moral righteousness. The more calculating variants also practice risk aversion, out of their consideration for the spectrum from least to most gainful believed by them. One rhetorical question that is an actual decision for them when faced with adversity is: why "stoop down to their level" to compete when there is only "disgrace" to be had? Regardless of the moralistic views on what cannot be taken up by stooping down to accept and what is really the disgrace, taking up the means to compete or the continuation of the act that is being challenged, the decision of this rhetorical question is one in the vein of anti-competition.
A relatively large gap exists between "honor" and "pride", in their meanings and practices. Arguably, there are rigidities in "honor" codes that make those beholden to act honorably have the weakness of being more predictable than "pride". This greater predictability rests on what principles are contained in these "honor" codes and how said codes are practice in relation to the superior, the equal, and the inferior of status. Once again, the intangible yet ever-present force of "pride" in sentience is frequently convoluted with other forces in practice. So the claim that "honor" is more predictable than "pride" could be argued to be soft theory. Here are a few common ways to think about "honor" and "pride".
- To be honorable is to have a reason to be prideful.
- Being part of a pride requires one to be honorable.
Propositional logic using these social terms bring not clarity, but invites for more words at more discussion tables, with expectations of equal exchange rates of the unique perspectives behind the concepts. Differing viewpoints are a plurality, something the prideful may have issues with. One statement can be regarded more true than not with "pride" and "honor". Many a times more honorables have served the prideful than more pridefuls have served the honorable.
Are the prideful predisposed (if pride is itself a disposition) to seeking and holding onto power? There are some that argue that even the modest can be prideful, and the modest really cannot be excessive in their want of power. The prideful can seek and hold onto power in the image and values of their pride. Those that lust after power may obtain power. And the gluttonous that crave power, similar to the cravings for food, may also have their desires fulfilled. Drawing a direct connection between pride and power is with challenge, but when pride is coupled together with other concepts, each coupling forming a category of their own, there paves the way for more clarity.
- Pride and honor: more steadfast.
- Pride and lust: more instinctive and passionate.
- Pride and vanity: more hubristic.
- Pride and gluttony: excessively greedy.
This categorization serves as a pre-defined structuralization to understanding the practices of pride, although the short descriptions of these four categories of pride are indeed terse, and the wording is not specific whatsoever.
A predominant number of methodologies exist for recognizing pride by pride's expression. Pride needs hosts for expression, and the diversity of possible hosts, each with their traits and motives supposedly unique due to self-interests, makes the task of identifying pride by the expression of specific words or actions not with certainty. Interpretation and framing are heavily used in investigations of pride's hosts. The bombastically prideful is framed as an insecure attention seeker, possibly one with a personality disorder according to psychiatry. The bombastically prideful could also have allies that claim they are, in fact, not an insecure attention seeker but an outspoken and strong-willed one. Absolutist splits in depicting the prideful, such as in this example, are quite cumbersome to overcome for a united opinion; such unity for a united opinion would pose it as a fact then, by consensus. The prideful also have a tendency to also be considered stubborn. The idiom, "swallowing one's pride", acts as a suggestion to the prideful to humble themselves by forgoing the convictions that make them be judged as stubborn. Stubbornness is actually easier for a third-party to gauge of a candidate. The candidate proactively does not change when they are corrected by external agents, although they have the capability to do so. This observation of their lack of changing certain behaviors and beliefs, when openly confronted to change, is a tell-tale sign of the characteristic of stubbornness. There is also the opinion that casts negative light on stubbornness as akin to stupidity. "A tree that cannot bend will break". This perspective encourages thinking on pride as directly correlated to stubbornness and thus, stupidity. Another perspective correlates the lack of "pride" with low self-esteem, when in actuality, low self-esteem is a symptom of low confidence (this reasoning is not scientific, however, since there is a lot left unwritten, and the simple reasoning basically equates self-esteem with confidence).
Legitimacy is a rather political issue in the real world. Conflicts have arisen during times when what was once an indisputable standard, quite outright an institution of sorts with powers both extendible and concentrated, is put into serious question of an insulting and subversive nature. These conflicts have varied, from power transfers on the nation-state level, to inter-nation conflict, to ethnic disputes, to paranoid and envious local rivalry. There are two primary routes for pride to show itself as an indisputable. The prideful can be "ordained" into a status of legitimacy. This ordainment happens very frequently in aristocratic environments. Societies that practice discrimination of institutional scale disqualify those viewed as some type of way. Disqualification does not have to happen outright in explicit commandment, but by a silently lurking and threatening shadow of terror, loyal to the legitimate, over those categorized by the societal institution/s to not be fit for the brand, the pride, the legitimacy, per se. In the second case, the prideful challenges the incumbent of the brand labeled legitimate, and either replaces or equalizes the incumbent. Obviously, the first case of legitimacy presents fewer socio-economic challenges to the prideful's recognition, at least from their beginning. Instead of having to go through winding tunnels of trial-and-error for the prideful to be recognized as the pride, with each of these errors accounted and publicized for ritual humiliation in extreme politics, the prideful could have just been born into a position to be conveniently ordained. One cannot choose what they are born into, unfortunately for magical thinking. Nothing is really that cut and dry in societies of flux, however. Legitimacy wars make for very sad cases of discussion, from emotive viewpoints. And the waging of legitimacy wars, not always physically violent, heavily rely on information warfare by cryptographic and propagandistic means. So there is that much for truth written on the topic.
Any serious discussion about pride and pride's wanted ramifications would have to also include topics of legitimacy, in one form or another. If one were to be a representative of pride, but they are constantly being subverted, insulted, demeaned to a felt degree, then they clearly have to put aside their energy stores to deal with the offenses. The dealings do have not to be pro-active or reactive. They, the dealings, are still generated by energy that could have went into efforts for other outlets. Various manners by which "questions", designed to be perceived as offenses, are posed in ways not educational or advisory to the prideful. Instead, the "questions" are challenges that somewhat demand the prideful to be self-effacing, and the opening of self-effacement is not just for mere mockery. Their image is supposed to be permanently tainted, their capabilities to be contained for the other's stated higher purpose. Why certainly, the prideful can attempt to maintain their stance and go about their merry way. But these are serious offenses in the realm of political warfare. In some of the more dire cases that encourage great instability, the opposition would even anticipate reactions from those they consider the pridefully antagonistic types to generate the kind of violence that they then could spin around for escalation. So who is really prideful in these cases, and would the question of being prideful really mean anything except for analysis and retelling, like a fable with a moral attached to it? Pride, progress by improvement, and humility become so intertwined in some of these cases that sometimes, what is left to be indisputable facts after the intertwining processes is the status. "Pride" and "status" are still two different words.
Then again, one could be prideful and not seek the status, the legitimacy as written about in the previous paragraph. One could be prideful about one's self and maintain a modesty on the outside to third-party observers. Underneath the modesty is an underarmour of "pride" that only shows itself under serious threat. The granting of legitimacy can be viewed as the granting of protections and privileges. Without certain protections and privileges, the modest and prideful do have to show their underarmour. How "pride" shows itself in these circumstances by projecting the "identity", the "spirit", the "power" really cannot be stated with certainty since the circumstances of this writing are intentionally left open-ended.
Some cycles produce so little, a deserted and barren land that those more fortunate dare egg on in their sayings that such lands have been cursed by God. This is similar to how some lifeforms can be starved to death, out of not the misfortune of immobility in the position, no, but the choice of the other, and for the other to respond that that is God's will as the simple explanation, as if any life below quarter-starvation to death can muster the clarity of cognition to formulate a rational response back, as if reason in its lone practice can clear up the way for deprivation to be no more. Charity, the power to give for the expectation of something reciprocal back to the giver, could be or could have been the power to take. Every one has their own doubts about high charity, while the starved and deprived put aside their doubts for their will to live, perhaps even have to pretend to be believers because that is the passage to kill off the starvation where charity, the only way, may as well be the self-proclaimed Holy Emperor.
Every thing of a real existence, especially in material form, is eventually and repeatedly tested. This truth says nothing on the forms of tests applied to each of these things, and what natures surround these tests to validate the tests' strengths, above all, and maybe the tests' correctness in applications afterwards, if there is the time, capital, and ethics to allow for that. Here is a claim. Oftentimes, it is pride that sets up the basis for what is right. It is pride that stands its ground. But pride's hosts may not have to be the ones that do the bidding for pride. To do the bidding for pride may require one to engage in much destruction and disgrace, two concepts when actualized may cause more trouble than what pride's hosts can stomach. Oh, pride must be careful lest it requires another host; pride does have limits in its material drive. It is those rivaled against another, out of their drives of some combination of pride and jealousy, that go digging up graves for evidence while ignoring what they can perceive, their own failures included, and also using most unwholly ways for what they claim to be for the "greater" or "common" good; the terms "greater" and "common" correspond to those two classic ends of the political spectrum in regards to the self and the selfless. These so-called sacrifices, weighing out of matters for the believed best choice, spark some of the most heated debates that go far outside of the confines of any religious framework, assuming that all religious frameworks are moral and based on the coolness of acceptance. The assumption is very absolutist and will probably spark laughter of the crazed variety, in a full and honest survey.
Truly, one of those peculiar things about pride in host form is that pride is frequently more fit to be a commander than a doer. And it does not take much life experience to state this truth: to be an effective commander, one should practice an even-tempered conduct. Why question pride when pride can be a motivator for outcomes thoroughly fit to some self-interests? The objective of accomplishing some task sometimes requires the kind of humiliating and unserious conduct that cannot be considered representative of pride by any standard. Immediately, with the words "humiliating" and "unserious", the reader could suppose the doer to be a charlatan or a seller of gratification. But such conduct does not have to be perverse. The conduct is by a mask hiding a disfigured force; nothing much but uncertainty of the elements in the power the prideful, in this context, wishes to project can be gathered. Knowing that some things have happened, for the better or the worse, because of pride, but to not be able to reconstruct credible connections from the doer to an alleged commander of the doer, that most prideful one, becomes something like another chain of events that could be called "humiliating" and "unserious", with objection not of an entirely absolute degree, to the theorists.
Pride being a force, labeled this word, that is part of cognitive processes, and this force having to be self-generated as in "it comes from within" (yes, this does read cliche), although the self-generative process may have to take into account variables outside of pride's host/s so that the force of pride can be generated according to the self's formulation of it, then has to be the hosts' objectives but with possibilities of nullification through the lack of positive feedback from the external validators, possibly inanimate and definitely not omnipotent. Comprehensive testing of a host of pride involves effectively locating the external factors for self-generation. Apply alterations to them, according to the heedance of a reference containing directions, to gauge the host's reactions when the circumstances that generate their pride are changed. This is clearly more easier said or written than done. Testing of this kind does have to be somewhat questionable, this being proved through any accurate surveying of opinion. More penetrative testing procedures involve identifying the metaphysical factors found within the host, and applying alterations to those factors so that the host of pride can be assessed under their differing internal circumstances. For these kinds of penetrative alterations, the assessor could do things such as communicate ideas, related to the metaphysical factors of interest, to the suspected host of pride. The term "penetrative" is used in this explanation to signify procedures that directly attempt to alter the metaphysical factors for pride in the host, rather than alter external factors believed to be involved in the host's self-generation of pride. Testing of pride has occurred since ancient times, so it has been done before and time and again for many agendas, such as those things under the label of "rite of passage". This paragraph's explanation is a reminder on an acceptable starting point for devising more sophisticated and detailed testing arrangements. Ultimately, testing of social traits can only become a believed pseudoscience. There is the issue of untangling the mind from the force labeled pride, and of handling alterations to the external factors believed to aid in the host's self-generation of pride, and last but not least, the believability that reception has of the testing. And nothing is really so exact until it happens. For example, an assessor could destroy all of the belongings of a suspected host of pride. The host does not have to express offense, out of their pride that "comes from within". The host could also express offense, out of their pride that they believe they must defend. A coin toss, without any more specifics, especially in the longevity of time in which the host of pride clearly has a liberty that "comes from within" to be a host to any other of the Seven Deadly Sins. And would not the assessor also have to be somewhat prideful in order to feel at ease with this way of testing? Very interesting question, is it not?
The two possibilities described that the tested host, in the previous example, can decide on in effect point to the principle of pride being a force present in a host that can, in turn, control the force such as by hiding this force, expressing this force, and probably also be able to distribute this force.
The prideful operates on narratives rather than a knowledge base of facts. With just a knowledge base of facts, the prideful believes that they are somehow an "enlightened", "educated", or "informed" one, and these categorical terms are noted in their psyche through the terms' recycling back into the prideful's self-generation of pride. The narrative could be anything, such as a fact in which the prideful won something, and the fact is re-iterated time to time in the cognition of the prideful as part of the self-generation for their pride. The narrative could also be lofty thoughts of grandiose power, how someone was so humiliated and embarassed, clearly a great contrast to their honor, the prideful. It is the prideful that fall back on their wins in their times of challenge, and these are also the same ones that are the icons of discouragement, aimlessness, and anti-competition with challenges that involve them directly or indirectly but still affect their image in some way. Maybe the prideful is also a pacifist one. There is nothing outright wrong with pacifism. For fair dues, though, it is not just the prideful that operate on narratives. It is rather difficult to imagine one thought of to be prideful while they rest their case to stand tall and strong on top of structures composed of deception (for demonstration only). And an ending point of obviousness on narratives and the prideful: the prideful would rather trivialize than be trivialized, and would most likely construct challenges for those challengers that trivialize them, the prideful.
Attempting to describe the prideful in the dualities of what they would rather do as opposed to the alternative is effectively juvenile. Stating dualities on the matter of the cases of pridefuls is not for pure intentions of precise identification, instead tools to engineer opinion on a specific prideful. If the credibility is not there though, goes a certain line of thinking, for opinion to be swayed, then there cannot be engineering of opinion. But the previous statement too is stubbed reasoning, since persuasion by a narrative convincing enough of any notion posed as fact does indeed occur. No living being can ever prove that they cannot be deceived; either the trials of variations prove that they are deceived, or the lack of varying trials prove that they are untested and can yet still be deceived. That is just how an ever-present adversary is, duality and all. Character analyses make for some of the more memorable thinking and talking points, and pride is a building block for some of these analyses. Persuasion-first and truth-first are two labels for a kind of classification for these analyses. So that is one way to attempt to understand pride, through a juvenile thinking of dualities on what the prideful is by their doing, a kind of hit-or-miss guessing game gleefully played by a third-party from a safe space. Pride becomes less and less of the central focus in the specific designing of the duality test for the prideful. The test could still work though, as in be incredibly accurate to predicting what the prideful will do. If all operating conditions of the prideful and effecting conditions of the environment remain identical to those of the test setting, then the prideful can perform differently only out of pathology (the fluke) or the choice to "fail" by choosing the opposite. But then the test's accuracy measures are for the symptoms of the host that is alleged to be prideful. There is the virtually identical expected and actual of what the specific prideful would rather do as opposed to the alternative. Without satisfying the requirement to connect the specific prideful's preferred action to pride, through more than correlation, there is still something missing. Designing and executing testing procedures to measure an alleged prideful's degrees of pride, only for those procedures to solely account for the actions that have to somehow be attributed back to pride in order for the test to be a valid mechanism for the stated purpose, to measure pride, is something circular. Alas, it is a world where the effects, specifically the executed action, from or attributed to lifeforms are what counts so much in the eyes of co-lifeforms.
Many of the statements made in this section on pride's symptoms, exhibited in those believed to be prideful, carry a curious kind of contention in cognition. For one not habitual in feeling doubt or skepticism, or asking questions, the lack of those kinds of sentiments encourage the perception of these statements to be impersonal affronts to their existence and functionalities. When these psyches register critique of the metaphysical driver of pride, questions re-emerge in the cognitive space and there is a yearning to be the correct ("good") orientation in these analytical posits on pride. In the greater scope, sometimes it is not a particular knowledge or wisdom that is desired to be actively registered by cognition, regardless of the truth value, due to rationales that rest on such things as pragmatism (staying focused on the task/s) and the defending of one's morale, especially on topics typically thought of to be universal/common forces that make their hosts and subjects alike unhelpable in the deterministic outlook.
Some things not quite right occur when pride is the decisive driver in settings promoted by truth-agnostic or truth-averse settings. This is not a denunciation on how wrong untruths are, as in one attempting to coax another about revealing a secret believed to yield powerful effects via a confession of confidante allegiance. There is pride, and then there are the two realms that pride's hosts have to balance out their own way, transparency and deception. Through these "own" ways, transparency by levels and attributes specified by the prideful, the propellant is their desire to communicate the message to observers that they are entitled to being prideful because they exhibit a factual greatness outwards. Almost always, a carefully considerate calculation is done by the strategic prideful due to notions of their own vulnerability. Deception. A very hefty field that is a serious sub-field of all of the social as well as natural sciences, in both the practices of knowledge transmission and the actual that has to be transcribed into the word for the knowledge transmission. The strategic prideful uses deception for defense, this utility necessitating them to be labeled an illusionist for purposes of transparency. Effective deception, in persistence and foolability, would make the explicit labeling of the strategic prideful (the illusionist) one of the few attributes of complete truth for them; to be labeled any concept but for there to be no "infrastructure" of operation to deliver the effects from being labeled as such is moot, and the labeling an example of stubbed reasoning. Stubbed reasoning is of a lower quality in the other's usability than what can be labeled circular reasoning. This category of reasoning is not only circular, claimed to be justifiable by its revolution around a core that does not have to be on factually applicable standing, and the "bodies" in this reasoning revolving around the core due to connections distorted to yield truths in the fanciness of probability, the reasoning is also not very usable (a stub instead of the required potential) through a deliberate stunting of its development by its issuer. The term "usable" denotes the positive capability of usage in manners of the usable's integration into a larger sequence of actions and materials. Clarifications such as these are important, for any reader could assume that advancing something not usable for the other is quite really a use, but that use is a "negative" one (null,negligible). These two categories of reasoning tools are self-justifying, used to send messages to be interpreted as impervious by their lack of substance underneath, vulnerable not because of truth but by the prospects of adversarial usage of those truths. A possible misconception on the "infrastructure" of operation, in this paragraph's explanation, is valuable enough to point out. If a prideful were to be labeled an "illusionist", and there is purported to be ample evidence for this labeling in the form of case events and the accomodated valid drawing of connections from those case events to the claims, the claims then serving as the ignition for the "infrastructure" to function for the stated purpose, such as correction or promotion, and the "infrastructure" does not work as intended so that the sequence from the prideful being an illusionist to the "infrastructure" acting on this labeling is ineffective by the stated intentions of cause-and-effect, the sequence has to fall under the category of reasoning in practice that is stubbed. This long sentence that could have been split into several sentences is intentional so as to communicate a related idea, used by virtually all those that have failed to undo the prideful by exact recreation of the prideful's deception. There is the notion that something is united and integrated as one, meaning the reasoning starts from a point and ends at a point reliable to any practitioner of that reasoning, but that something both does not have the "infrastructure" to deliver on the stated effects and is still the method of validation on the design of cause-and-effect. The same long sentence could have been split into smaller sentences, each sentence serving as an accountable authority over the deliverance of its notion. Instead, many sentences were pieced together into one that is meant to indisputably pass as the one, not some or none.
The cause-and-effect from the labeling of the strategic prideful, as an illusionist, to the wanted effects carried out by an "infrastructure" is the infrastructure's consequentialist usage. Any that attempt to play against the role of an illusionist, regardless of their matter of being prideful, could also use this kind of "infrastructure" to reveal and act in the manner of correctness.
Crafting of illusions requires skill, and the desired effects of the illusions tend to elicit the kinds of values that are non-identical to the input. The input to craft illusions is seldom desired by the illusionist to be known, in full principle that includes the details, to the observer. In this desire is a prime building block for arguments against the illusionist as a deceiver. A repeat, the output is typically not the same as the input. The absolute equality of the input and the output, along all attributes, would be self-defeating to the intents of the illusionist: to project an image (technically, a sequence of information) that is to be reasoned along lines that misalign with the input that is the true principle of cause. Both the prideful and the non-prideful have innate needs, if conditioned for self-interests of gains through understanding, to regard, perhaps outwardly, the illusion upon discovery of its concealed origin as deception. Subjective claims of offense then emerge: the illusionist is the offendor, or those that make invasive or deflecting movements into the illusionist's illusion out of their belief that the illusion is contrived. Illusions, as sentients' constructs, are incredibly dense topics for thorough discussion, not requiring book knowledge from history till now and for many regions of the world, since illusion first and foremost is received through the experience and with non-null probabilities of being retained in secrecy for purposes of belief and private initiative. So for this section, the use of the illusion to describe the prideful's practice is catered to references of the prideful's objective: status and/or functionally-directed power.
Those that place great reliance on the deceptive power of illusions do so for their defensive power. This specifying of illusion as for defensive rather than offensive power should serve as the orthodoxy, in order to clarify on the confusion. Those deceived by illusions act out of error, and these errors are either also anticipated by a forward-thinking illusionist for launch points of their action, or desired by the illusionist to somehow yield the coincidence of their own gains through the deceived's mistake/s. There are those kinds of simplistic propers that do not believe the illusionist to be merely a benign defendor, due its bi-status of projecting influencer and a defensive apparatus. The status is what the prideful seeks. This status could be an equilibrium in the form of a harmony with their surroundings of both natural and artificial construct; that would appear modest. Objectives geared for this equilibrium would position the prideful as poorly fit for the other primary objective of the the illusionist: to be the agent of functionally-directed power, of degrees multiple in average by comparison. Another fundamental clarification is required on what functionally-directed power is. The unit of exchange in this kind of power is a class of command. This unit of exchange is typically designed to be uni-directional. The command is both reliable, the commander's desired start and end points equal to the actual, and of a capable degree, in both of the categories "positive" and "negative", such that the pertaining categorical system could be the orthodox or the contra. Functionally-directed power is capabilities in excess of maintaining equilibrium through channels for preserving procedures and the materials/agents those procedures depend on. For those categorized solely by the label of illusionist, their command cannot be dynamically suited to purposes outside of the obscured design for a narrow scope of effects wanted by the illusionist; this narrow scope of wanted effects does not include the entire possible spectrum of the illusion's reception.
Pride, when recognized strictly as a vice, in its hosts must operate in antinomy. An example of antinomy has already been provided, the putting into motion a system based on transparency and a system based on deception clash unless the prideful, as an illusionist, plays a balancing act to nullify each motion to clash. A convincing argument can be made that deception is a super-class containing illusion, in the different categories of operable bodies of truth. The prideful, as a deceiver, appears in limited ways to those the prideful wishes to deceive, while the totality of their actions involve more than their appearing in those limited ways. This dichotomy that must be lived by the prideful in the manner of a oneness that conquers this duality is a challenge on scales proportional to how much is to be gained from their deception of the other; the gains may be outlandishly greater than what is required to craft the illusion, but there is still a positive correlation that can be exploited. Then, the attack surface that adversaries aim at against the illusionist is the oneness that operates by split procedures, yet must still recirculate its one self back to those supposed to be deceived. Attempts are made to shatter the oneness into their perceivable action as an unresolvable duality, in which valid calls can be made for one or both of the complements to be corrected by methodologies such as retraining and destruction.
The prideful, in the face of rising or ever-present great animosity against their standing, do have the validity rationalized on their own standing to be an effective illusionist, amongst other things. In effective illusions, the prideful projects an image that should be readily accepted, taken for granted in the orthodoxically positive sense, by virtually all others. Stubbed reasoning on the image is the default preference of the prideful. Mono-characters instead of characters with automated meaning of various forms, possibly dangerous to some, that ensues immediately after the characters' registration into cognition. Offensives in rhetoric of reason against mono-characters of an immoveable standing are obviously ineffective, and could additionally be depicted by opposition to the offensives as insanity at its worst, barking at those truths that prevailed and continue to prevail.
A projecting prideful that has waning functionally-directed powers is forced to fall back on illusion, or resign from chaos inevitable through their own direct actions. Notions of power in practice are seldom singularly agreed on, at least from the beginning and from all cognition to all genuine practice. In the objective of status for the illusionist with little else, the ultimately prideful wishes to be that something believed to be the power "source" that all must name as the power "source". The infrastructure in place to deliver on the prideful's command does not result in uniform deliverance, deliverance that is consistent according to the frameworks that can be structured into hierarchical format and also evenly distributed across all recognized contexts, so the "name" counts more than the "substance". Initiatives such as these place high negative value on splits, the value signifying recognition of split as greater contributors to errors than the centralization for a uni-recognized source; measures of performance and deliverance are registered in rational-like systems as truth-agnostic, inconsequential in another word.
Measurements of pride's hosts for pride has not been proven in this series to yield consistent answers, completely direct correlation (correlation equals causation) from the actions of those believed to be prideful to the force that is pride. In fact, this section's discourse on pride as a driver for illusionists, in duality, makes for a convincable base of argument for the contrary. In a more simpler way of reasoning that is not so much for constructive purposes but to assuage, measurement of a metaphysical force by the symptoms exhibited in their hosts has the potential to aid for satisfactory predictors of the hosts' activity. But that is a predictor for the host's expression, and the mark cannot be set on the metaphysical force itself. Incompleteness here, an understanding without full control over. In the second part of this series, jealousy in practice was mentioned in a few statements of difference to that of pride. Ones that operate on jealousy are also not very consistent. The jealous oftentimes view themselves as second-best, at most, in some respects. And in their latching of focus onto this view of being second-best, the jealous can also become an illusionist, a deceiver in practices of duality for their competitive states. The moral outcry against unfairness, such outcries typically not openly expressed during the jealous' heating of their deception strategy, is treated as a fundamental building block for their rationale. According to the jealous that re-geared their efforts to beat the prideful, the jealous were disadvantaged in some way, or perhaps they were unlucky, although they believe they are actually at least equal. This is a kind of cognitive dissonance that is the acceptance of two conflicting metrics, an antinomy, which becomes a greater influence than the jealous' desired belief, supposed to be officially recognized, in the actions of those driven by jealousy.
Many more interesting notions, in relation to the cycle, have not been written about. In this third of the series, the cycle is placed into more review of its pathological power. As a disclaimer, topics of such broad scope that can be scientifically defined, and formulated for applied use, always seem to have more room for discussion, albeit the content of each of these discussions have to relate in some way to the topic, lest the discussion is one on explicit amalgamation, meaning to place the fields of distinctness into reconciliables (dualities, et cetera) for the gesture of positive growth in some context, or misdirection, in either the casual sense to end discussion on the topic or to deceive through silent convolution by another topic, with aims for or to avoid a result intended by the expressor. Appalling if not useless, the uni-construct of the cycle is theorized to have as much potential for discussion as duality, due to some reasons such as the infinite ways of expressing the finite abstraction for an infinite number of practices. The "expression" and the "practice" are labeled two different words with their existences ranging from very different to identical, in comparison. This span, in turn, should not be taken to validate the claim of the "power of language", since language is really one field out of the involved many.
In the first aspect of discussion on the pathological power of the cycle, consider those that have to fend off that power as defendors, specifically ones that have to employ an assortment of deception as response to the cycle. The use of the term "cycle" in this case is not for those lone and permutatorial processes that these defendors use, actually antagonistic to them. This strict usage of the conceptual cycle as an antagonist to these defendors is a duality, and perhaps the terms "good" and "bad" do not suffice in full capture of these agents' orientations along select lines of judgment. The defendors could also employ techniques, practical advancements rooted in the conceptual cycle, although the description of their situation with the antagonistic, the cycle, does not label them as a "cycle". Orthodoxy by preferred labels is a kind of duality, although the adoptability by orthodoxy of complements outputs solutions that seldomly aim for anything below preservation of the "hard" line, the separator between the 1 and the 0. Solutions that carry connotations of "ambition", "control", and "conquest" strive to achieve the oneness of the duality, the oneness being the much greater fact, by truth through observation and analysis, over that which can be interpeted as two where one or both do not satisfy for those modalities of cognition and action deemed pressing in the spatiotemporal span.
There are two relevant labels for the cases of deception that defendors use, group-directed and group-targeted deception, such that the term "group" denotes the defendors. The labels denote the directionality of "negative" effects from deception with respect to the group (defendors), "negative" a term that rests on the orthodoxy of directly connected losses. The purpose of group-directed deception is to deter influence, intrusion, and other forms of manipulation from outside sources, especially the central antagonist, the cycle. Proponents for this form of deception argue that the antagonist has the capability to execute on methodologies effective to the detriment of the group, so to appear one way and act another is only natural in making the antagonist completely miss on their aims while completely countering the antagonist. There are three primary components pertinent to group-directed deception. A group always has at least two members in this deception.
- The methodology/ies to be used by the antagonist as a set of paired values, the first value representing an ordered sequence of variables and the second value representing a corresponding sequence of "best" values for those variables. Additionally, each of these variables are not unique to any one member of the group. The "best" value for each variable denotes the "condition" of the variable that is a part of the group configuration, a unique form out of more than one capable of being expressed by the group for purposes of internal and/or external functionalities. A group configuration that matches this set of paired values make it vulnerable to an associated attack from an adversary.
- The security requirement, in the form of two that is an executable assignment and deceptive assignment, for the pertaining sequence of variables belonging to the first component, used by the group.
- The alert mechanism corresponding to the deceptive assignment; it consists of procedure/s for each member of the group, used in the case of query by outside force. to help maintain intra-group perfect information on adversarial exploits.
The freedom of differing styles for representation, all the while that suits the same purpose by expressing the same kind of information in totality, implies that this section's illustrating of group-directed deception is incomplete by the narrowness of stylistic expression. But in fact, not many other forms can reasonably exemplify this category of deception that can satisfy the streamlined (barebones) without the excess of other attributes that is there, for practical purposes, to serve other conditions not briefed in the description of this kind of deception's three primary components, due to the written deliberation to design a quantitative abstract by the use of elementary mathematical structures. The previous statement is debatable, and the decision to use differed forms is entirely up to the discretion of the reader that chooses to use techniques of group-directed deception, after first establishing the stepping stone of a preliminary past the abstraction of the plainform (natural language) description.
ASOC31: A group
ASOC32: A methodology used by the adversary
ASOC33: Two tables, deceptive and executable assignments,
respectively, that show the configuration as appeared and
actual (in practice) of group
ASOC34: A table showing the alert paths that each member
of group
An example of group-directed deception is shown in diagrams
ASOC3(1-4), and there are a few attributes to it that do
not have to be present in other instances of this kind of
deception. For one, the optimal methodology that adversary
Group-directed deception is used due to group circumstances that validate the group's call for this practice. The big condition for using this practice is the assumption that for each variable the adversary relates to, as a step in their vulnerability exploit, the adversary can access any member of the group for the "vector" that pertains to that variable, although not all group members are required to be using the variable, as already specified in the practice's definition. The group hopes that the adversary's breadth of access to their members is limited by the effect of granting the adversary only the appearance of the member, the appearance being possibly deceptive, and only the values for pertaining variables in the adversary's attack sequence is noted by them so that the sequence of actions taken by the adversary stays in a relatively predictable range by the group's knowledge of their methodology in vulnerability exploit. Overall, group-directed deception is an application of boolean mathematics that uses the basis of 1 as the executable and 0 as the deceptive, or vice-versa, such that the 0 is intended for the adversary to pursue and believe in, in turn enabling the alert mechanism to accurately relay specific knowledge of the current step being taken by the adversary that has to, hopefully by the perspective of the group, endure retaliatory measures of some nature. Two important conditions, besides from the group's open-ended design of their retaliatory measures after the alert is distributed. One condition is that the alert system is timely in its communication. In the example, the alert system is the default of sending out the alert immediately after the first attempt made by the adversary, in their search of a variable where they mistook the deceptive for the executive. From the perspective of the group, each variable involved in the adversary's vulnerability exploit should have deceptive members completely distinct from executive members, so as to avoid the risk of the adversary correctly guessing the member associated with their current step centering around a variable of the group's configuration, in their procedure to inflict loss onto the group. In group-directed deception, a couple ideals pertain to successful group operation. The group needs to have an alert system that results in measures discouraging if not completely repulsive to the adversary's future advances. For that to happen, each member would have to satisfy the minumum knowledge requirement, their deceptive assignment, possibly their executable assignment for other functionalities outside of defending against the adversary through deception, and the alert mechanisms they are to take after their deceptive assignment has been known to the adversary, by value but not by the status of deception, after the adversary's querying. The group should anticipate not knowing the precise sequence of steps the adversary intends to take. But the group's initial configuration should be one considerate in the active use of group-based deception for what they believe are the beginning steps of the adversary's offense. The accurate knowledge of these beginning steps taken by the adversary plays a pivotal role in the actualization of the group's predictive success of exactly knowing what the vulnerability exploit the adversary intends to take or intended to take before quitting midway.
The reason for group-directed deception rests on the fault of the group that does not have the adequate defense, outside that of the deception as illusion, to proceed with their functions in full form without the economical waste of deceptive effort and in tandem with the adversary. This has already been stated in a similar manner, and moreover can be structured as an economics problem in the duality of decision-making. The economics problem is a decision problem that asks the solver to prefer one of exactly two routes: appearance as action as appearance, or appearance as not action. Phrasing such as this does come off as obtuse, why there are more than two possibilities but with only two routes explicitly stated, and the phrasing signifies a choice for an entity to engage in a duality of sameness (equality of the appearance and the action/execution) alongside the wanted output, or a duality of appearances as a collaboration with deception for that same wanted output. Some may think that this kind of phrasing suffices in explaining the truthfulness of any situation approaching a critical decision junction point, but truthfully, suffices only as a product from a countable number of steps past the abstract, free from error of its own form but vulnerable in practice, by the lack of specialization for the specific pivots required against errors not understood in linear manner. In environments emphatic on deception as a strength, the announcement of an authentic few steps past the countable derivatives from the fundamental is viewed as a vulnerability due to the probability of adversarial gain in that information.
Innate weaknesses, due to the economy of split, immediately present themselves in some form and degree after the group decides on the route of group-directed deception. There is existence, the required base state for all members of the group. From this existence, a split is designed with the objective to serve as a clear dividor between the appearance the group projects (as deception) and the "actual" group activity for their "actual" functionalities to execute, such that the group's "actual" is but a portion of their "total". The appearance projected is the first active point in cognition for any empirical analysis, this condition due to the foremost necessity to deceive, for both the group and outsiders such as the adversary. And the group intends for this projected appearance to be the only result from the split knowable to outsiders, thus shielding the group's "actual" for their executive processes. Because the appearance projected is the first active point in empirical cognition, members of the group may ironically be subject to the same deceptive image that the group intended to be completely directed to the outside, not internally.
ASOC34: Two visualizations of what a group member active
in a group-directed deception is attempting to accomplish.
The first diagram illustrates
Some offhand explanation is necessary for this section's usage of "empirical cognition". Empirical cognition is the processing of the input of information, from the external, with readily available objective information, essentially transcribable into mathematical form with correctness in the boolean space of completely correct or completely false. Furthermore, it is not an internalist mechanism of reflection, contemplation, and judgment based on biases innate or not, in and of itself.
A group's practice of group-directed deception has the possibility of resting on an assumption dangerous to their existence. The assumption is that the group's deceptive assignment shields them from the infliction of a deceived adversary. A hasty leap in reason goes as such: the group's deceptive assignment works in routing the choice of the adversary towards the deceptive, and the deceptive can easily, practically in an automated way, use the alarm protocol to alert the other member/s of the group for appropriate retaliatory measures. Verification processes to prove that this leap in reason, the guaranteed effectiveness in connectivity of communicative and retaliatory forms from the deceptive to the reactors, are unique to the environment and protocols of the group operating by group-directed deception.
What exactly would deter an adversary, during their conducting of a vulnerability exploit, when they are deceived by a deceptive group member at an arbitrary step in their exploit? This question is asked in the general context, foolish enough for answers that can prescribe specific measures to the general context without that same context having to undergo specification to accomododate those specific measures, not necessarily in the context of a mechanical computing system with security that is pre-programmed restrictions put in place for the advent of a failed external attempt. Consider these two techniques, named spam crusher and the inquisitor. Descriptions of these two techniques will not delve into the quantitative specifics, since the context is the general context, that is, one without the definition required for the enumeration on and around it.
The spam crusher is so named because it is a brute-force method for the destruction of the member queried by the adversary at a specific step during their vulnerability exploit. Whatever the total effects of the vulnerability exploit, the adversary's being deceived by a deceptive member during this sequence of steps then derails the adversary from continuing on with the exploit. The adversary then uses repeatedly destructive "querying" methodologies against that particular member that served a deceptive appearance to them, until that member is "destroyed" below a point of relevant existence. The inquisitor is also a brute-force method, but instead of "destroying" the deceptive member, the adversary applies repetitive inquisitive forces onto them, with the expectation that the member will eventually give way, as in reveal the other member that is actually responsible for the pertaining variable in the execution of group functionalities. The spam crusher is a negation through brute-force, and the inquisitor an information extractor through brute-force. The naming of these two techniques is something preferential, and works as an example of the farfetched semantics in notation, for some things much more universal in practice (negation and extraction), to capture the meaning of technicalities at play in practice.
A group in use of group-directed deception may find it useful to analyze, as individual members or other subsetting schematics, the quality of their using this kind of deception. The irony previously mentioned, on the projection of group member appearance (deception) to the outside in turn deceiving members of the group to their detriment, is an unignorable part of the any competent analysis/es by the group of their deception quality. Firstly, a simplistic statement on the correctness of deception is that the deception is wrong. So a member of group-directed deception may judge their being deceived to be a wrong inflicted by one or more co-members onto them. Naturally, accounting ensues, and this umbrella of processes inquires on two primary marks for each case of deceived members.
- The source of the deceptive detail, and the communication chain of members from the source to the member deceived.
- The effect/s that are understood to have stemmed from the deceptive detail registered by the deceived member.
Truth-agnostic and truth-averse arrangements encourage the second of the primary marks to outweigh the first in importance of value for the singular judgment, one of the main points in the analysis/es. It is the effects, outward from one being separated by time and space to another, that count so much in certain terms, as already stated in other words in the previous section (Pride Plays Perception Pt. III). What this means is simple in terms of any self-interest that must operate in some construct ruled by social acceptance: if something is beneficial, there is no need to place it in the lens of a dichotomy of truth and deception. Conversely, if something is not, by any other means, including the dichotomy of truth and deception. These statements are not a promotion or demotion of these views, but serve as a healthy reminder on the kind of rationales accepted by sentient thinking on many occasions. The statements can also be used by group members to help build their base of analytical processes for judging the quality of their group-directed deception.
Some examples are in order on what is a group member
deceived by group-directed deception. In this first
case, there is a functionality that requires variable
A class of deception, committed from one to another, is termed ephemeral deception. In the positively gainful case, the deceiver reveals the "truth", something different to a statement made on the same query, to the one that was previously deceived but now "enlightened" by the "truth", and there are gains to a lengthy right from the zero that resulted from the informed actions taken due to the revealed "truth" of the query, these gains being distributed in a satisfactory way to the ex-deceiver and the previously deceived. The timing of revealing the truth for a successful coordination between those involved in ephemeral deception is the aim. Ephemeral deception is a frequent information security practice, used in situations to avoid the compromise of valuable information after a holder of that information has been compromised. As for the industrialization of this kind of deception, not much information can be gathered that explicitly mentions the phenomenon of "ephemeral deception" in mass usage, let alone the success/failure rates.
An opinionated statement is that the phenomenon
of ephemeral deception makes for a marvellous
research topic of study. Doubt, in variables that
may go by different names such as "confidence" in
statistics, is a factor in equations concerning
the use of this kind of deception. The deceived
has to contemplate which of the statements to believe
in, the first that is the falsehood and the second
that is the truth, when they have to decide using
such information as their limited access to the empirical
and quasi-scientific principles such as Occam's Razor.
Next is an example of ephemeral deception on query
During
The gains from
When members of a group recognize the group as the "greater self", synonymously the ideal greater than the practical individual existence, the concept of one deceiving one's self can be extended to one group member deceiving another group member being equivalent to the group deceiving their self, grouped self-deception. Grouped self-deception rests on one essential premise, and this premise, existing in sheer and basic breadth, can serve other purposes instead of this phenomenon. The premise is a non-null difference between a group member's knowledge, used to induce expectations of group proceedings in group-directed deception, and the actual. The claim that one deceived another due to the fact that expectations were not met, with empirical facts that cannot additionally make the leap to factualize the claim of deliberate actions taken to blockade that expectation from being met, is surely to be challenged in any setting of communicative argument based solely on facts. However, these kinds of settings, funnily enough, are very rare in some social arrangements due to necessary expenses in fact-gathering only for stalemate to result from those facts, dreadful to certain interests. This statement is, of course, relativistic due to the descriptor of "very rare in some social arrangements", but the degrees of its manipulation and dishonesty are not objective, rather meant to express a kind of truism about self-interest.
The premise, the non-null difference being a pivotal step in one group member's belief of their being deceived by a co-member of the group, takes place by a few general pathways.
- A member was not informed of their executive and deceptive assignments.
- A member does not act properly on their executive
and deceptive assignments.
- Does not fulfill tasks required for the assignment.
- Fulfills the wrong tasks, the errors which then contribute to the probability of the group's failure in executive and deceptive functionalities.
- A member is misinformed on the executive and deceptive assignments belonging to them or another co-member.
In every one of these pathways, there is the apriori expectation, before the expectation of satisfying final results signifying the adversary's defeat encouraged by the group's deception, of a "social contract", per se, consisting of one principle agreed upon by all members of the group. The principle is perfect information, meaning accurate information of logistical relevance known to each member of the group, that is the foremost driver in all group members, each member not necessarily possessing identical information to another. This principle, once in the stages of deliberation for implementation, becomes practically complex quickly and according to the scale of group-directed deception design that emerges from the group's necessity to defend, the design also having to possess adaptive mechanisms precise to each specific vulnerability exploit the adversary intends to attempt during temporality. A template for required knowledge each member must have, in group-directed deception, has already been stated. As a reminder, the template specifies each member to have the minumum required knowledge pertaining to the group-directed deception scheme. This minumum is the executive and deceptive assignment of the member, not any other member, as well as the routing specific to the member for the alert mechanism. Limitations of this specification may not do in logistics of co-dependency. For example, one member may require to know their deceptive counterpart for a variable, since one of their responsibilities is to tell another co-member to take up the deceptive assignment for that variable in the case of marked changes onto the initial deceptive counterpart that make the counterpart's deceptive appearance no longer effective. Knowledge requirements, for a group member to know another group member's assignment and alert route, increases the number of members that know the private information, in turn possibly increasing the probability of the information's compromise.
In cases of group-directed deception such that minor mistakes in the schematic implementation may result in drastic failures, the group of a calculating nature is naturally inclined to conduct accounting of their workings. And these accountings are expected to be called necessary by them, the group, in instances of clear loss or other kinds of sub-optimal measures. Refer back to the three pathways of the beliefs in deception. In the first and third pathways, the member that was responsible for informing that uninformed member is the source that is responsible for the deception. In the second case, the member themself is the source responsible due to failure by possibly their choice. However easy this arithmetic-like reasoning of accounting may read, the effects of a group's accounting for their grouped self-deception is not that simple, even in small-scale cases. This reasoning supposes that one or more members, in the group, is to act as the source for a particular information for another member, and the source is supposed to be penalized in some way for their failure to adequately commit to the "social contract". Another supposition is that the schematic for the group-directed deception is static in detail, but it cannot be in situations of adaptive adversaries, so accounting must rest on prescribed courses of action to take when deception within the group is recognized by any of the group members. Unanticipated fluxes in the differences between group member's expected and the actual have the variable of time, as an additional challenge, for the group to account for their mistakes while possibly having to deal with more issues from the adversary, thereby growing another duality of tending to a past problem and tending to a present one. The idea of "randomness", as events not part of group consensus, makes its way into this attempt to explain this kind of accounting's effects. After a group member is labeled a source of grouped self-deception, a possibly arbitrary subset of the group engages in "corrections". These "corrections" consists of toss-up procedures between members such as the accused deceiver, the allegedly deceived, and sympathizers for either one. These toss-up procedures constitute the "randomness" mentioned, and the effects range from behaviorial modifications to exclusion/elimination of the accused deceiver or the allegedly deceived. These toss-up procedures that take place after a grouped self-deception is believed by the group to have occur could result in a caving duplicity. So there is a member that is believed by another member to be at fault. And the way to correct the fault is by inflicting what is arguably a fault onto the accused member. A caving duplicity occurs in groups with two or more members. The group had agreed to a "social contract" with terms possibly unique to some members. But due to the duality of the sub-optimal actual and the expected actual, the duality turns into a dichotomy, and the dichotomy is viewed as negatively duplicitous by one or more members of the group. So there are changes that take place, in the form of actions geared against one or more members of the group at their expense, the "caving" effect as the result from attempting to remove the duplicity by adversarially acting against the believed sources of it.
The ideal outcomes of group-directed deception rests on a unidirectional adversarial effect from the group to the adversary. Complications of this arrangement could pose issues such as the group's caving duplicity. Measures designed by the group to combat this problem, emerged from at least one group member's belief that there is grouped self-deception occurring, are a symptom of the group's instability to maintain consensual procedures based on the strategy of group-directed deception. The group's accounting of their deficits are another class of burdens the group has to contend with. This class of burdens can be called the forced reflection attack, done from one group onto themself. Reflection, as a cognitive phenomenon to review information for purposes of long-term memory storage and deeper analyses, is pro-actively done for the benefit of the self's understanding. But the forced reflection attack is different from the conventional concept of the self's reflection. For one, the group regards themself as the "higher" self to each of their members. "Reflection", that is accounting done from one member to themself or to another member for purposes of eliminating internal deception believed to have occurred, has the problem of spatiotemporal challenges outside of accounting such as the persistent adversary if said adversary has not been definitively repelled. The forced reflection attack is a cyclical process, each cycle an attempt to correct or account for a grouped self-deceptive detail, and is conducted by one or more members of the group. This specific process becomes an attack from the group onto themself when there are consequences nonconsensual by at least one member and of a relatively high number excessive to the group's allocation of resources, the excess being the quality that qualifies the process as a reflection attack instead of reflection for meditative growth. Through a group's prolonged experience of processes such as forced reflection attacks, spurred probably by inadequacies of their group-directed deception, the likelihood of caving duplicity does not stay below a threshold of minimal error, since caving duplicity and forced reflection attacks are correlated in occurrences.
Group-targeted deception is from an external source to a group's members. Quite opposite from the group-directed deception that seeks to harness the deceptive assignments to encourage the mistakes of the adversary, the deception involves the communication of deceptive details to members about their own attributes or the attributes of others. Through a group member's acceptance of the deceptive detail as part of the basis for their decision-making, vulnerabilities previously non-existent could possibly emerge in the group for the adversary's gain if exploited.
For a section that is supposed to focus on the cycle, but the "cycle" is the adversary and the group it antagonizes not the "cycle", most of the discussion focuses on certain kinds of deception used by the group fending off the "cycle". Two possible forms of deception capable by groups was explored in this section, the deception used for defensive purposes in economies of split between the appearance and the execution of functionalities, for the purpose of illustrating how a predominantly defensive body, not a forward force in other words, with vulnerabilities as the effect from conditions of their own economy and design, uses deceptive arrangements and other resulting processes that can be conceptualized as cycles. The wanted effects of a group from their use of group-directed deception is also based on the cycle. To elaborate, the adversary is expected by the group to pursue the deceptive assignment, and the deceptive assignment is to route the adversary's relevant information after point of contact by specific instructions concerning the alert mechanism, and the actions taken by the group is to counter the adversary in some way. In generic terms of the cycle, the head is the adversary's fall for the deceptive, the next point the communication by the alert mechanism, the next point the gains/losses that ensued since the head, and the last point is the head, to iterate once again in the case of a persisting cycle intent on continuing its attack. The forced reflection attack is a cyclical process of accounting and correcting unwanted internal deception. Introspective processes are fundamentally cyclical due the "self" having to analyze and understand its "self". Lastly, the phenomenon of caving duplicity is both itself a cycle and also a body of variables in the cycle of group-directed deception, reducing the effectiveness of these logistics by effecting "cannibalistic" results. As it turned out in this section's descriptions, the pathological power of the "cycle", the adversary to the group, is the reactionary body of deceptive and corrective processes a group may believe that they have to engage in as adequate defense for their structural and economic insufficiencies against the "cycle".
In resource-finite settings, accounting is a cornerstone of the settings' continuation. Equilibrium of wanted forms, and attribution to the makers, the doers, the rulers, et cetera. Accounting, as a cornerstone, was greatly advanced by human societies after the adoption of writing systems. The writing is to record the ephemeral experience of sound and fleeting image. Over time, the innate deficiencies of sentient transparency re-emerged in evidence through the accounting of accounting, not of accurate marks for some things of effect from causes of interpreting not the fact. And this did and does prove to be a persistent problem, not necessarily in the name of truth above all things, for truth and complexity and naturalism make for a swirl of layered truths outside the absolute bipolarity of absolutely true and absolutely false, but in the name of accounting for its designated purpose, a non-fiction genre of representation, from the standpoint of backtracking from that which is most evident, the record in account to the experience of the past. Accounting can also be thought of as a literary expression of etiology, the study of cause-and-effect. There is a cause, the event that typically involves values of pertinent variables. And then the effect is the event transcribed into the records, for the account, in more words, by and through the practice of accounting is the effect.
The accounts become recognized as facts, and then the accounting is self-justifying greatly because it influences the course of justice, and is commonly misconceived as the craft of practice which is innately provable in the same nature as mathematical claims, in turn, part of the structure of defense against third-party questions dangerous to the organization the accounts correspond to, as well as the organization's accurate introspection, commonly referred to as "internal investigations" in settings of more than one individual. Accounting becomes a cause for effects outside the tasks involved in accounting, and those effects are then subject to accounting. This is a common pattern in accounting, prescribed routes of iteration that are synonymously cycles.
Accounting serves the purposes of an axiomatic construct with input-output functionalities. In one version of an ideal case of the practice of accounting, the "wholeness" is somehow recycled back due to perfect attribution, due to and for integrity. Without a relevant axiomatic construct, accounting even of the purest factual form is subject to the decision of preference, in effect bearing effects that are subjective due to the lack of prescription from any relevant axiomatic construct. In an involuntary servitude of the agents in accounting for an axiomatic construct, there is the possibility of deception occurring alongside voluntary revolts against servitude. But a disingenuine servitude of an axiomatic construct is surely to deceive. To offer one's self for serving a particular axiomatic construct, the self is supposed to be deemed suitable by third-party judgment before that one's admission. There are preferences in the form of leanings and prejudices, many of which rest on top of the Seven Deadly Sins, before the practice of accounting, to uphold the practice of accounting, and the effects expressed by choice-systematic use of accounting.
Pathological accounting is a phenomenon that works via an accountable system's lack of fulfilling an entity's expectations, these expectations the calculated outcomes (forecasts) by the entity based on a combination of their knowledge and compliance with said system. This section has deliberately been cut short, due to the view that there is no need to introduce accounting tricks to illuminate on how pathological accounting has ensued, for that would also give knowledge on how pathological accounting can continue to ensue.
I, Richard Pham, am honored, although for no agenda to self-laud, to have been able to write this book that covers topics such as the political economy and economic philosophy. I hope that you, the reader, were able to gather some insight into the concepts explained.