| Number | Name | User | |
|---|---|---|---|
| 99194 | Daniel Pereira | https://github.com/DaniPalma2002 | mailto:[email protected] |
| 99315 | Ricardo Toscanelli | https://github.com/rtoscanelli | mailto:[email protected] |
| 99328 | Simão Gato | https://github.com/SimaoGato | mailto:[email protected] |
This repository contains documentation and source code for the Network and Computer Security (SIRS) project.
The REPORT document provides a detailed overview of the key technical decisions and various components of the implemented project. It offers insights into the rationale behind these choices, the project's architecture, and the impact of these decisions on the overall functionality and performance of the system.
This document presents installation and demonstration instructions.
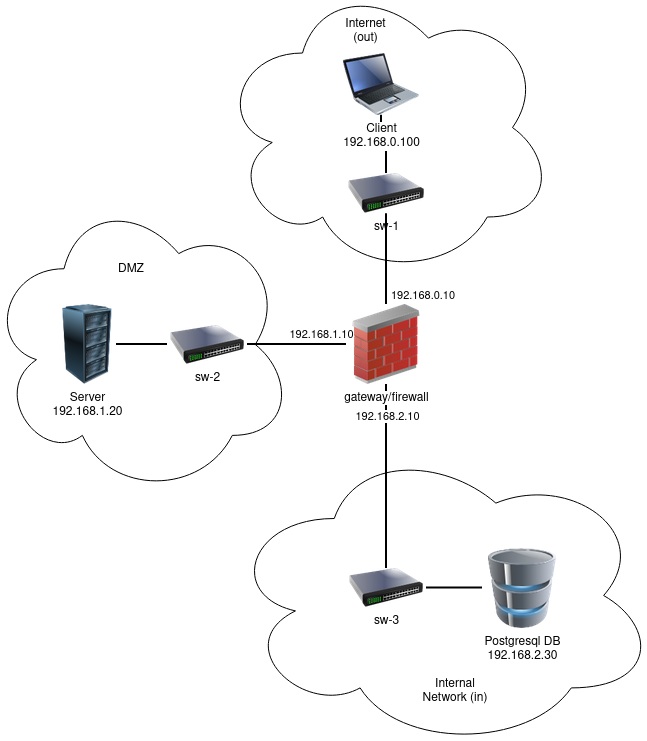
To see the project in action, it is necessary to setup a virtual environment, with 3 networks and 4 machines.
The following diagram shows the networks and machines:
All the virtual machines are based on: Linux 64-bit, Kali 2023.3:
Clone the base machine to create the other machines, with the IP addresses and hostnames as shown in the above diagram:
See the programming language and library versions used in the project in the Additional Information Section.
Some machine configuration commands will require ssh enabled.
Inside each machine, use Git to obtain a copy of all the scripts and code.
git clone [email protected]:tecnico-sec/a37-daniel-ricardo-simao.gitRemind that the machines are configured as shown in the diagram above:
- VM1: User
- VM2: Gateway / Firewall
- VM3: Server
- VM4: Database
Next we have custom instructions for each machine.
This machine runs the Server application.
Change to the directory with the scripts:
cd a37-daniel-ricardo-simao/ConfigurationChange the permissions of the script:
chmod +x generateServerCredentials.shRun the script:
./generateServerCredentials.shSend to the user machine the server and CA certificates:
scp path/to/server.crt path/to/ca.crt <username of User VM>@<IP of User VM>:/path/to/a37-daniel-ricardo-simao/Configuration/This machine runs the User (CLI) application.
!! Make sure that the server and CA certificates are in the correct directory (Configuration).
Change to the directory with the scripts:
cd a37-daniel-ricardo-simao/ConfigurationChange the permissions of the script:
chmod +x generateUserCredentials.shRun the script:
./generateUserCredentials.shThis machine runs the Database application.
cd a37-daniel-ricardo-simaoGenerate keys
openssl genrsa -out root.keyopenssl genrsa -out server.keyopenssl genrsa -out user.keyCreate certificate request
openssl req -new -key root.key -out root.csr
- You can leave all the fields blank (enter all)openssl req -new -key server.key -out server.csr
- Common Name (e.g. server FQDN or YOUR name) []:<ip of database vm>openssl req -new -key user.key -out user.csr
- Common Name (e.g. server FQDN or YOUR name) []:postgresCreate a database to be able to sign other certificates
echo 01 > root.srlSelf sign the root
openssl x509 -req -days 365 -in root.csr -signkey root.key -out root.crtSign the user and server with root certificate and key
openssl x509 -req -days 365 -in server.csr -CA root.crt -CAkey root.key -out server.crtopenssl x509 -req -days 365 -in user.csr -CA root.crt -CAkey root.key -out user.crtConvert them to .pem format
openssl x509 -in root.crt -out root.pemopenssl x509 -in server.crt -out server.pemopenssl x509 -in user.crt -out user.pemsudo apt updatesudo apt install postgresql postgresql-clientsudo systemctl start postgresqlsudo -u postgres psql -c "ALTER USER postgres PASSWORD 'postgres';"sudo -u postgres psql -c "CREATE DATABASE restaurantsdb;"sudo systemctl enable postgresqlGo to postgresql main folder
cd /etc/postgresql/16/main # 16 is postgres versionCopy server key, and root and server certificates to this folder
sudo cp /path/to/server.pem /path/to/server.key /path/to/root.pem .Change file user to db user (postgres)
sudo chown postgres:postgres root.pem server.key server.pemChange server.key permissions
sudo chmod 0600 server.keyOpen your PostgreSQL configuration file (postgresql.conf) and set the following parameters:
listen_addresses = '*' # what IP address(es) to listen on;
ssl = on
ssl_cert_file = '/path/to/server.pem' # Path to your server certificate
ssl_key_file = '/path/to/server.key' # Path to your server private key
ssl_ca_file = '/path/to/root.pem' # Path to your root certificateModify the pg_hba.conf file to allow SSL connections to server ip (make sure the ip is the same as below, or adapt it to your network)
hostssl restaurantsdb postgres 192.168.1.20/24 scram-sha-256 clientcert=verify-fullRestart postgres
sudo systemctl restart postgresqlVerify logs to see if its running properly
sudo cat /var/log/postgresql/postgresql-16-main.logchange user.key to user.key.pk8 (note: back to the directory where you create the user.key)
openssl pkcs8 -topk8 -outform DER -in user.key -out user.key.pk8 -nocryptSend user key and certificate, and root certificate to the grpc server
scp /path/to/user.pem /path/to/user.key.pk8 /path/to/user.key /path/to/root.pem <server vm user>@<server vm ip>:$HOME/To test if everything works, access postgres shell remotely from the terminal on the application server VM (VM3 in our configuration)
psql "host=<db vm ip> user=postgres dbname=restaurantsdb sslcert=user.pem sslkey=user.key sslrootcert=root.pem sslmode=verify-full"sudo -u postgres psql -d restaurantsdbPaste the information on the populate.sql file into the postgres terminal.
This machine runs the Firewall application.
After every other machine is setup up, is time to add the firewall configurations. Make sure that you have access to the iptables command.
Add the following rules to the firewall:
# Drop all incoming packets by default
sudo iptables -F
sudo iptables -t nat -F
sudo iptables -P FORWARD DROP
sudo iptables -P INPUT DROP
sudo iptables -P OUTPUT DROP
# Allow all outgoing packets
sudo iptables -A FORWARD -p tcp -m state --state ESTABLISHED -j ACCEPT
# Allow all packets from the outside network to the application server
sudo iptables -A FORWARD -i eth0 -p tcp -d 192.168.1.20 --dport 5000 -m state --state NEW -j ACCEPT
# Allow all packets from the application server to the database server
sudo iptables -A FORWARD -i eth1 -p tcp -s 192.168.1.20 --sport 5000 -d 192.168.2.30 --dport 5432 -m state --state NEW -j ACCEPTNow that all the networks and machines are up and running, ...
To test the protect, check and unprotect from the library you should, in the main directory of the project:
mvn clean install compileAfter, you can run your commands. You can use the input examples we have in Secure-document/inputs.
For example, for menu 1, you can:
protect Secure-document/inputs/menu1.json Secure-document/inputs/keys/restaurantPriv.key Secure-document/inputs/keys/simaoPub.key Secure-document/inputs/menu1out.jsoncheck Secure-document/inputs/menu1out.json Secure-document/inputs/keys/restaurantPub.keyunprotect Secure-document/inputs/menu1out.json Secure-document/inputs/keys/simaoPriv.key Secure-document/inputs/menu1deciphered.jsonTo analyze, you can just check the output to see our library in action.
To test the functionalities, it's very straightforward going from the initial menu to the option you want to choose. The menu it should appear when running all the components is below:
This concludes the demonstration.
We use SemVer for versioning.
This project is licensed under the MIT License - see the LICENSE.txt for details.
END OF README