Prime numbers are used in RSA (Rivest–Shamir–Adleman) encryption, a cornerstone of the Public Key Infrastructure (PKI) system, because they enable the creation of a large modulus (
Here’s a step-by-step explanation of RSA encryption for
We choose two primes:
This
Once
Choose an
$1 < e < \phi(n)$ -
$\text{gcd}(e, \phi(n)) = 1$ (relatively prime to$\phi(n)$ , meaning$e$ and$\phi(n)$ have no common factors other than$1$ ).
We need to find a value for
$1 < e < 20$ $\text{gcd}(e, 20) = 1$
Start testing small integers for
-
$e = 2$ :$gcd(2,20)=2$ (not relatively prime, so not valid). -
$e = 3$ :$gcd(3,20)=1$ (relatively prime, so valid).
Let’s select
The public key would be represented as a pair:
(Note) Two numbers are relatively prime (also called coprime) if they share no common factors other than 1. This means their greatest common divisor (GCD) is 1.
The private key
To find
Using the Extended Euclidean Algorithm:
Now we have:
-
Public Key:
$(e, n) = (3, 33)$ -
Private Key:
$(d, n) = (7, 33)$
The encryption formula is:
Substitute
-
Calculate
$5^3$ :$$5^3 = 5 \times 5 \times 5 = 125$$ -
Reduce modulo
$33$ :$$C = 125 \ (\text{mod} \ 33) = 125 - 3 \times 33 = 125 - 99 = 26$$
So, the encrypted message is:
The decryption formula is:
Substitute
Instead of directly calculating
$26^2 \ (\text{mod} \ 33) = 26 \times 26 = 676 \ (\text{mod} \ 33) = 16$ $26^4 \ (\text{mod} \ 33) = 16 \times 16 = 256 \ (\text{mod} \ 33) = 25$ -
$26^7 \ (\text{mod} \ 33) = 26^4 \times 26^2 \times 26 \ (\text{mod} \ 33) = 25 \times 16 \times 26 \ (\text{mod} \ 33)$ $25 \times 16 = 400 \ (\text{mod} \ 33) = 4$ $4 \times 26 = 104 \ (\text{mod} \ 33) = 5$
Thus, the decrypted message is:
-
Original Message:
$M = 5$ -
Encrypted Message:
$C = 26$ -
Decrypted Message:
$M = 5$
This demonstrates how RSA ensures secure encryption and decryption using prime numbers.
You publish your public key
Your private key
(Note 1)
However, the numbers
(Note 2: More realistic example)
So, the public key would be something like:
A sender encrypts
Only you can decrypt it using your private key, recovering
You can sign messages using your private key, and anyone can verify the signature with your public key.
Prime numbers, by definition, have no divisors other than
The first step in RSA is to choose two large prime numbers, denoted
These numbers must be kept secret and should be randomly chosen to ensure their unpredictability. The product of these primes,
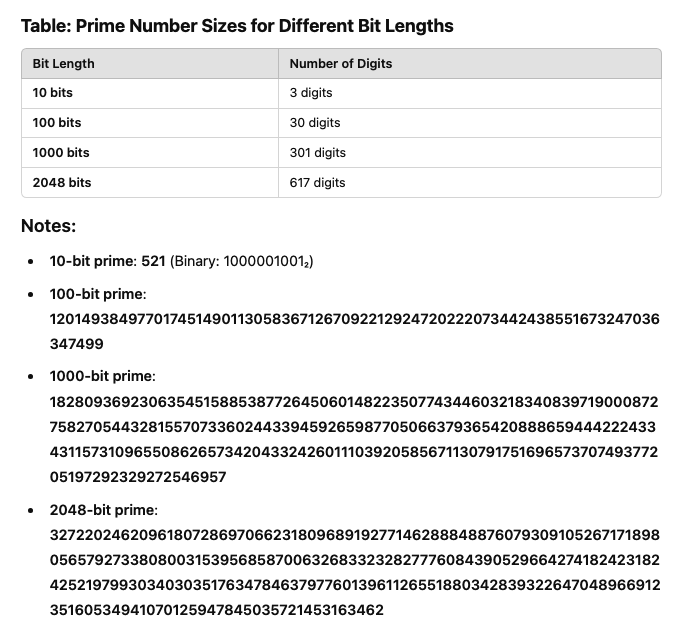
- The size of
$p$ and$q$ is crucial for the security of RSA. If these primes are too small,$n$ can be easily factored, undermining the encryption. Large primes ensure that factoring$n$ becomes computationally infeasible, even with advanced algorithms.
Once
- If
$p$ and$q$ are chosen correctly, this step ensures that the private key is mathematically linked to the public key, but finding the private key from the public key without knowing$p$ and$q$ is infeasible due to the difficulty of factoring$n$ .
The primary security mechanism in RSA relies on the difficulty of factoring large composite numbers. The larger
- The computational effort required to factor large numbers grows substantially as the primes
$p$ and$q$ grow in size. For instance, a 2048-bit key has a modulus$n$ that is made up of two primes each approximately 1024 bits long. Factoring such a number using traditional methods would take an enormous amount of time, making it practically impossible to break the encryption within a reasonable time frame.
The security of RSA is directly tied to the choice of large primes. Here’s why:
By selecting large, random primes for
Factoring large numbers is not only time-consuming but also computationally challenging. While there are efficient algorithms for factoring small numbers, these methods become exponentially less effective as the size of the number grows. For example, the best-known factoring algorithms, such as the General Number Field Sieve (GNFS), become exponentially more difficult to apply as the size of the numbers increases.
By using very large primes (often 2048 bits or more), RSA provides a security margin against advances in computing power. As computational capabilities improve, the size of the primes used in RSA can also be increased, ensuring that the system remains secure.
One of the challenges in RSA is the generation of large prime numbers. Although there are efficient probabilistic primality tests (such as the Miller-Rabin test), generating large primes that meet the security requirements can still be computationally intensive. The primes must be large enough to make factoring the modulus
In practice, the generation of prime numbers for RSA often involves using specialized algorithms that generate random numbers and test their primality. If a number passes the primality test, it can be used in RSA key generation. However, care must be taken to ensure that the primes are not too close to each other, as this could make the factorization of
The security of RSA depends entirely on the difficulty of factoring the modulus
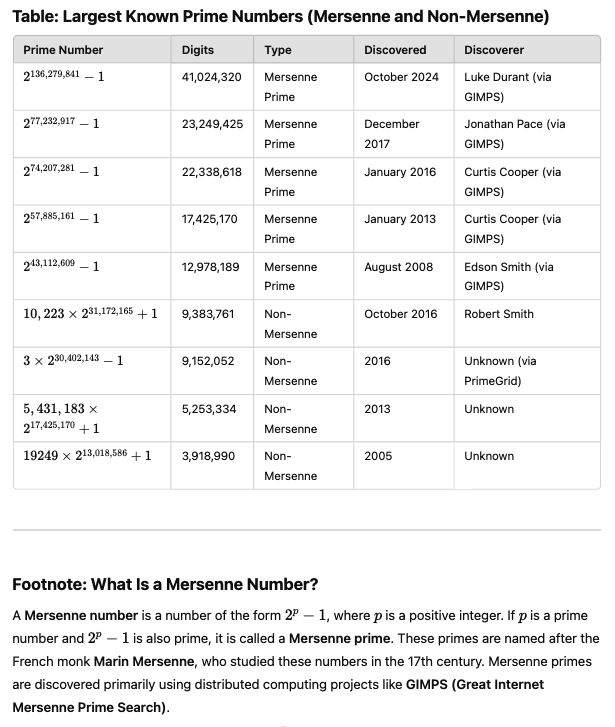
As of January 2025, the largest known prime is a Mersenne prime, discovered on October 12, 2024, through the Great Internet Mersenne Prime Search (GIMPS). This prime,