A hybrid lab setup combines on-premises infrastructure with cloud resources to create a flexible and scalable environment for testing, development, to mimic production workloads. Azure Site-to-Site VPN extends your on-premises network to Azure, enabling secure and seamless communication between your on-premises environment and Azure resources.
In this setup:
- Hyper-V: These script will install and configure Hyper-V on your "on-premises host" or workstation to create and manage virtual machines. These VMs can mimic various server roles, applications, or network configurations that you want to test or deploy.
- Azure Site-to-Site VPN: These script will configure a Site-to-Site VPN connection between your on-premises network and Azure Virtual Network. This VPN connection ensures that your on-premises resources can securely communicate with Azure resources over the Internet as if they are part of the same network.
Benefits of this setup include:
- Scalability: Easily add or remove virtual machines in Hyper-V or Azure based on your needs without significant hardware investments.
- Flexibility: Test different scenarios or configurations in a sandboxed environment without affecting your production infrastructure.
- Security: Securely connect your on-premises network to Azure using Site-to-Site VPN, ensuring data encryption and compliance with organizational security policies.
Overall, a hybrid lab setup using Hyper-V and Azure Site-to-Site VPN provides a powerful and flexible solution for testers looking to simulate a true on-premises and cloud resources effectively.
The script will setup whats in red:
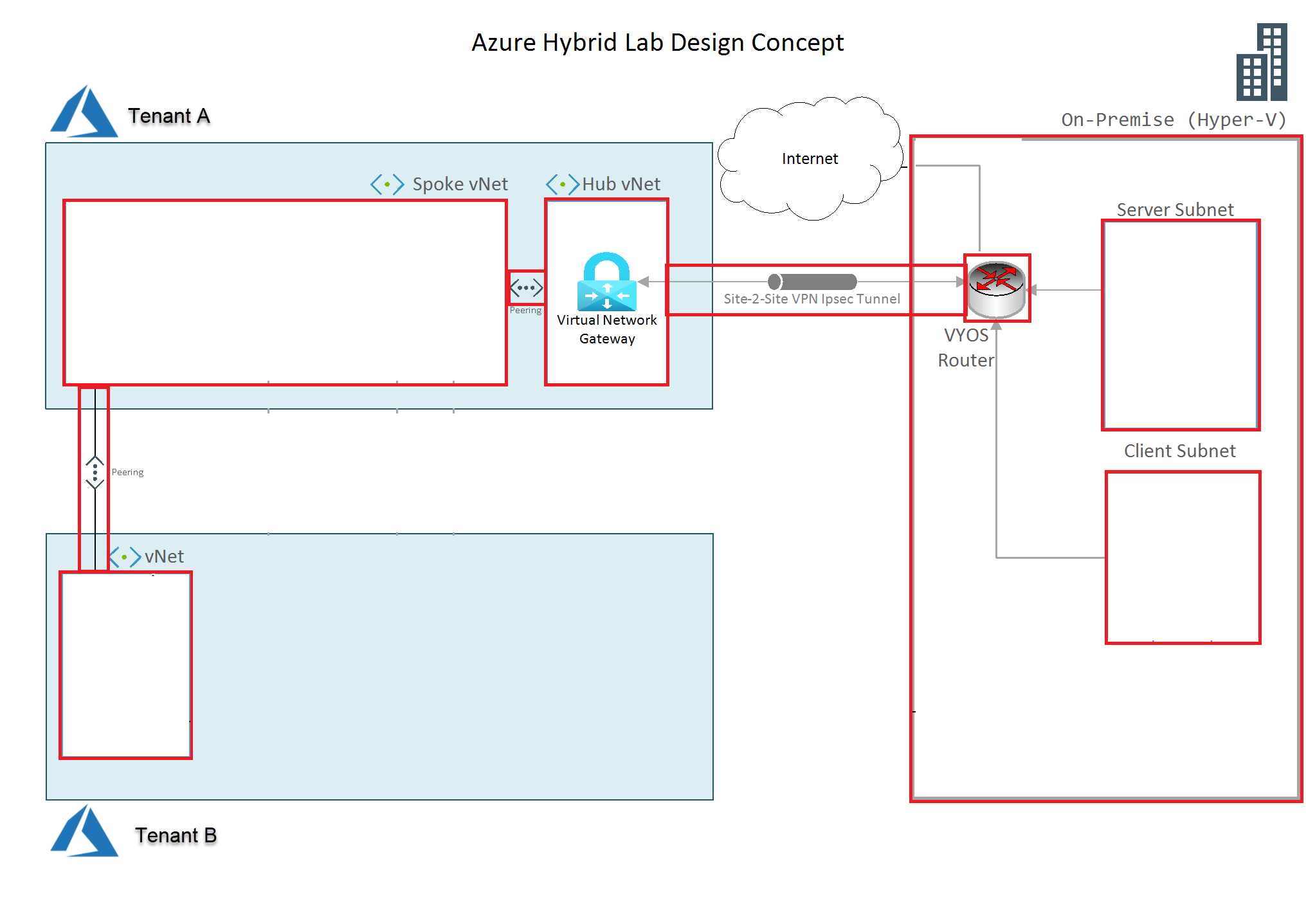
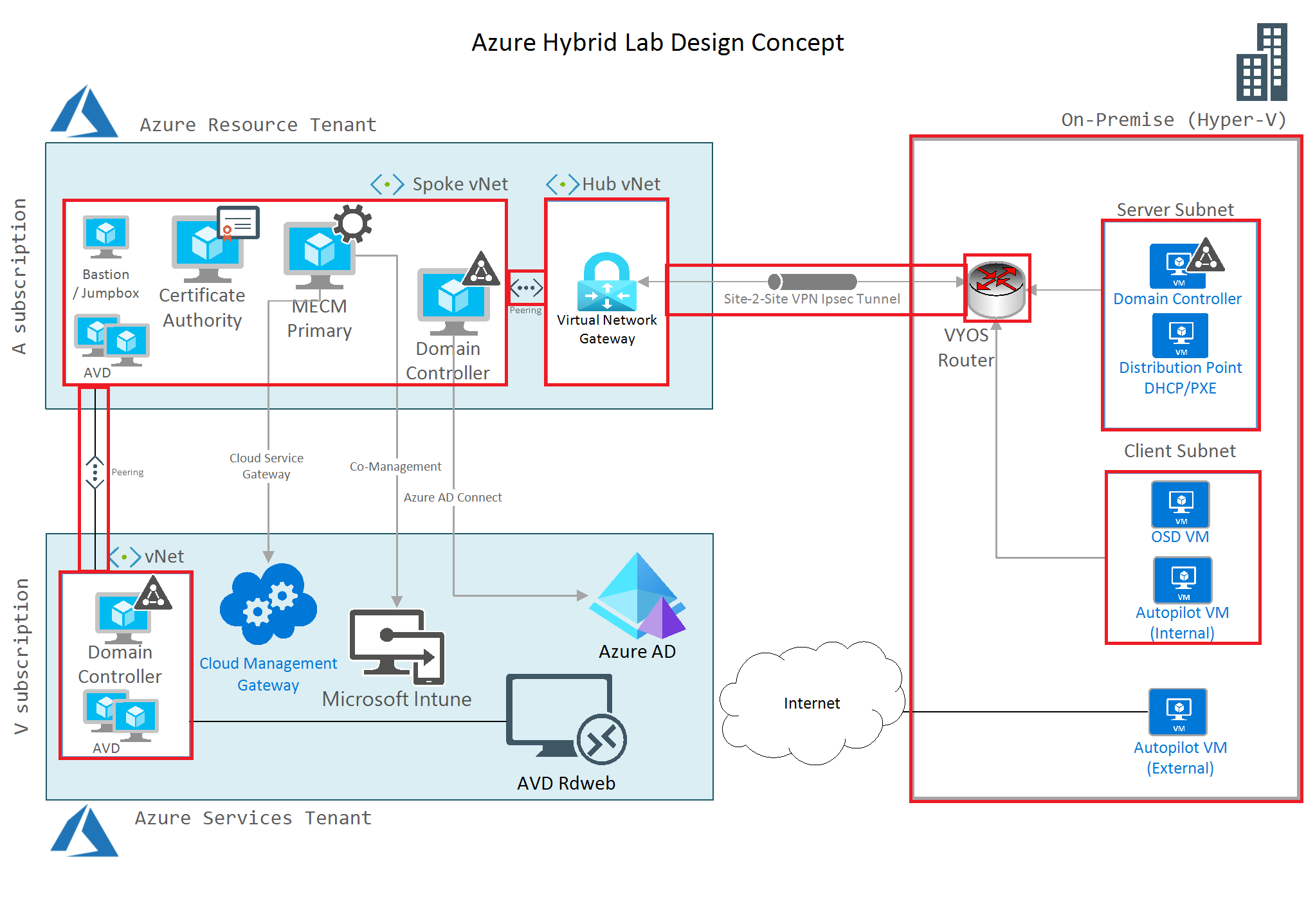
You can then use this network setup to build your environment. Here is an example:
- Azure Commercial
- Azure Government High
- 1 or 2 Azure subscriptions (VSE or Trial will work)
- Windows OS that will support Hyper-V
- Internet connectivity
- Home router to issue IP to virtual router (vYOS)
- SSH utility with SCP and SSH-Keygen. These are installed with Git for Windows. You can get it here
- Azure PowerShell Modules installed (specifically Az.Accounts, Az.Resources ,Az.Network, Az.Storage, Az.Compute)
- Partial knowledge with PowerShell and Azure modules
Below are explanations for each configuration.
- IgnoreISECheck: PowerShell ISE has issues with prompting for password during VYOS setup. Recommend running in PowerShell or VSCode.
- AzureGov: changing to true, will use the Azure environment for gov
- LabPrefix: identifier for names in lab
- domain: just a name for now (no DC install....yet)
- Email: used only in VM notification for VM auto shutdown settings
- VMAdminUser: this is used to configure default username and password on Azure VM's
- VMAdminPassword: this is used to configure default username and password on Azure VM's
- OnPremSubnetCIDR: Always use /16
- OnPremSubnetCount:
- TenantASiteName:
- TenantAHubCIDR: Always use /16
- TenantASpokeCIDR: Always use /16; keep this subnet higher than hub (when incrementing)
- TenantASpokeSubnetCount: keep this at 1 for now
- TenantBSiteName:
- TenantBHubCIDR: Always use /16
- TenantBSpokeCIDR: Always use /16
- TenantBSpokeSubnetCount: keep this at 1 for now
- DHCPLocation: defaults to DHCP server not on router; assumes DHCP is on a server
- DNSServers: if not specified; defaults to fourth IP in spoke subnet scope (eg. 10.22.1.4). This would be Azure's first available IP for VM if is specified; google IP 8.8.8.8 will be used since no DNS server role exist on router
- HyperVVMLocation: Leave as for auto detect
- HyperVHDxLocation: Leave as for auto detect
- VyosIsoPath: Add path (eg. 'E:\ISOs\VyOS-1.1.8-amd64.iso') or use to get the latest VyOS ISO (this is still in BETA)
- HyperVVmIsoPath:
- UseBGP: not required for VPN, but can help. Costs more.
- AzureVnetToVnetPeering:
- TenantASubscriptionID:
- TenantATenantID:
- TenantBSubscriptionID:
- TenantBTenantID:
- RouterAutomationMode: Uses Git, SSH and SCP to build VyOS router. 99% automated; but 90% successful
- SimpleAppendix: Name appended to the simple S2S resources
- AzureLocation: Azure location: supports East US, East US 2, West US, West US 2, Central US, North Central US, South Central US
- timeZone:
- configs.ps1. <-- This script is used to answer script values; linked to all scripts
- Make sure you edit the variables in the top section under the General Configurations
- Advanced: Recommend you don't make changed in this section
- All scripts use this as an answer file for each setup. The answers are loaded in hashtable format and all of the required values are generated dynamically or will be prompted during execution
- library.ps1 <-- Custom functions used for common automation
- network.ps1 <-- Custom functions used to generating network subnets
- VyOS.ps1 <-- Custom functions used for VyOS automation
- azure.ps1 <-- Custom functions used for Azure automation
- hyperv.ps1 (not used) <-- developing for hyper-v VM automation
NOTE: All logs are written using a transcript to the logs folder including VyOS scripts
NOTE: be sure to run these scripts with elevated rights.
- run script: Step 1. Setup HyperV for Lab.ps1
This script does a few things:
- Installs hyper-v (if needed)
- Sets up networking (external and internal interfaces)
- Check to see if device is on wifi and attaches that to external; otherwise it used physical
- run script: Step 2. Setup VyOS Router in Lab.ps1
This script does a few things:
-
Downloads the VyOS ISO if path not found (downloads to user downloads folder or temp folder)
-
Setups the VyOS basic configuration (manual steps required)
-
Established SSH to VyOS and attempts auto configurations for LAN network
- You will be prompted to make configurations to the router. Also once SSH is established the script will generate RSA key to auto logon.
This is a temporary process because VyOS does not save authorized_keys. if login is successful, it will auto configure the VyOS router for you otherwise you will be presented with a copy/paste configurations.
- If ssh does not work, you can manually run the scripts within the VM. Scripts are exported to log folder for each step
-
Change the value to something like this:
$VyOSIsoPath = 'D:\ISOs\VyOS-1.1.8-amd64.iso'There are few options when building the Site2Site VPN lab:
- Step 3A. Build Azure Basic S2S.ps1 <-- Sets up a very basic azure S2S VPN , no hub and spoke configurations.
-
Step 3B-1. Build Azure Advanced S2S - TenantA.ps1 <--Sets up a more complex Azure S2S VPN with hub and spoke design. Also run scripts:
- Step 3B-2. Build Azure Advanced S2S - TenantB.ps1 <-- Optional if you want to setup a second site
- Step 3B-3. Connect Azure Advanced S2S Tenants.ps1 <-- Only Required if a second site is setup
- Step 3C. Attach Azure S2S to Existing Network.ps1 <-- Connect to an existing Azure network. You must run it like this:
**NOTE: If connected to Azure, hit tab for the virtualNetwork and Resourcegroup values to iterate through existing Azure resources.
& '.\Step 3C. Attach Azure S2S to Existing Network.ps1' -Prefix MECMCBLAB -ResourceGroup mecmcb-lab-rg -vNet mecmcblab-vnet -DnsIp 10.0.0.4 -RemovePublicIps -EnableVMAutoShutdown -AttachNsg -ForceIMPORTANT: All scripts list above can be ran multiple times! If ran a second time, it will check all configurations and attempt to repair and issues. this can be useful when public IP has changed on home network
If all went well, the VyOS router will connect each Azure site. You can check it two ways:
- Run command on router:
show vpn ipsec sa- Go to Azure Portal --> Local Network Gateways --> Click on gateway --> Connections
The last thing to do is setup a VM in your Azure lab without Public IP and connect to it from you hyper-V vm. This is a good test to see if your VPN is connected
To setup a VM, run the script corresponding to the type of Azure VPN you set up prior:
Option 1: Step 4A-1. Build Azure VM.ps1
Option 2: Step 4B-1. Build Azure VM - TenantA.ps1
Option 3 Run scripts:
- Step 4B-1. Build Azure VM - TenantA.ps1
- Step 4B-2. Build Azure VM - TenantB.ps1
BETA: Step 4C. Build Hyper-V VM.ps1 <-- Sets up a VM in Hyper-V (not unattended)
IMPORTANT: All scripts list above can be ran multiple times! If ran a second time, The script with create another VM incrementing the name automatically or you can specify an name like so:
& '.\Step 4A. Build Azure VM.ps1' -VMName 'contoso-dc1'INFO: The VyOS_setup folder are templates and samples of known working configurations. Can be used to compare configurations in your VyOS router
- Some devices have reduce network quality with hyper-v's external switch connecting to WiFi adapter. Recommend using physical adapter if possible
- Some ISP's (especially hotels) don't allow public IP to pulled from web crawlers such as http://ipinfo.io/json; this can be an issue with when the script is setting up Site-2-Site-VPN
- Some ISP's may not allow VPN traffic; no know work around for this
- After Site 2 Site VPN is created; step that check for connectivity may show _unknown) or not connected; this may be due to Azure's graph api call not updating immediately. Recommend manual check
- Go to Azure Portal --> Local Network Gateways --> Click on new gateway --> Connections
- VyOS router will remove it trusted ssh host list on each reboot. This is by design and will require login for each script implementation; looking for alternate method to resolve this.
- There are known issues with the PowerShell ISE interface during VyOS configurations; Recommend running with Powershell console or VScode.
- Running this script over a LAN network may not work. Copy local before running
- Hyper-V VM setup script will require PowerSHell 5.1 for Chassis setting configurations
- These scripts have not been tested on Azure clouds other than what is stated in supported section
- Target multiple subscriptions per tenant (such as Mission LZ)
- Vnet peering between Azure and Azure Gov is NOT supported
- Create a VPN Gateway and add a Site-to-Site connection using PowerShell
- Site-to-Site Powershell Sample script
- Hub-spoke network topology with shared services in Azure
- VyOS Releases
- How to install VyOS Router/Appliance on Hyper-V
- Azure BGP Network Triangulation
- Route-Based Site-to-Site VPN to Azure (BGP over IKEv2/IPsec)
- Configuring Azure Site-to-Site connectivity using VyOS Behind a NAT – Part 3
- BUILD A HYBRID CLOUD LAB INTO MICROSOFT AZURE WITH VyOS
- VyOS Site-to-Site
This Sample Code is provided for the purpose of illustration only and is not intended to be used in a production environment. THIS SAMPLE CODE AND ANY RELATED INFORMATION ARE PROVIDED "AS IS" WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE IMPLIED WARRANTIES OF MERCHANTABILITY AND/OR FITNESS FOR A PARTICULAR PURPOSE. We grant You a nonexclusive, royalty-free right to use and modify the Sample Code and to reproduce and distribute the object code form of the Sample Code, provided that You agree: (i) to not use Our name, logo, or trademarks to market Your software product in which the Sample Code is embedded; (ii) to include a valid copyright notice on Your software product in which the Sample Code is embedded; and (iii) to indemnify, hold harmless, and defend Us and Our suppliers from and against any claims or lawsuits, including attorneys’ fees, that arise or result from the use or distribution of the Sample Code.
This posting is provided "AS IS" with no warranties, and confers no rights. Use of included script samples are subject to the terms specified at https://www.microsoft.com/en-us/legal/copyright.