💻 A Detailed Analysis on Cybersecurity and Web Security
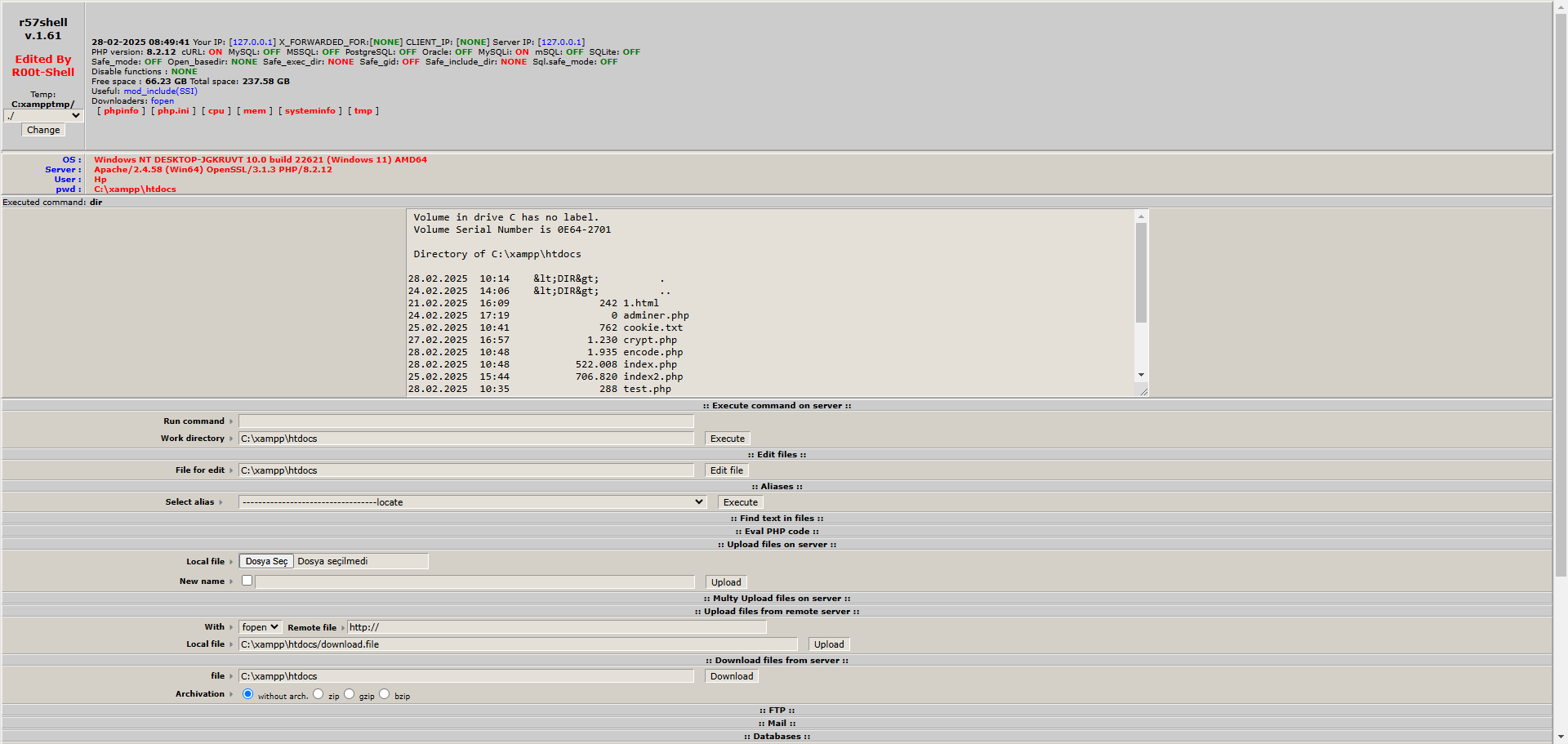
R57 Shell is a type of web shell commonly used by malicious actors. This PHP-based ability allows attackers to control a server remotely. Web shells are used for tasks such as file management, command execution, and data theft on servers.
When R57 Shell is uploaded to a server, it can perform the following actions:
- 📂 File Management: Uploading, downloading, editing, and deleting files.
- 🖥️ Command Execution: Running operating system-level commands on the server.
- 📊 Database Management: Accessing databases and executing SQL queries.
- 🔍 Gathering Server Information: Viewing server details such as the operating system, PHP version, and configuration.
- 🚪 Creating Backdoors: Setting up backdoors for future access.
R57 Shell is typically uploaded to a server as a PHP file. The attacker executes this file to control the server through a web-based interface. Here’s an example:
<?php
if (isset($_POST['cmd'])) {
$cmd = $_POST['cmd'];
echo "<pre>" . shell_exec($cmd) . "</pre>";
}
?>This code provides a command execution feature. An attacker can use this code to execute commands on the server.
⚠️ Warning: Abilities like R57 Shell are used for illegal activities and pose serious security risks. If you detect such a file on your server, you should remove it immediately.
To detect and prevent R57 Shell, you can follow these steps:
- 🔒 Fix Security Vulnerabilities: Regularly patch security vulnerabilities in your web application.
- 🛡️ File Upload Controls: Check the type and content of uploaded files.
- 🔍 Log Analysis: Review server logs to identify suspicious activities.
- 🧹 File Scanning: Scan and remove suspicious PHP files on the server.
✅ Tip: Use a Web Application Firewall (WAF) to block malicious traffic.
Note: Make sure to replace the image link with a valid one if you need to add any.