Certainly! Here is the updated README.md file with the added description about outputting the CSV format and the two file outputs based on the script logic:
# CVE-2024-6387_Check## 📜 Description
CVE-2024-6387_Check is a lightweight, efficient tool designed to identify servers running vulnerable versions of OpenSSH, specifically targeting the recently discovered `regreSSHion` vulnerability (CVE-2024-6387). This script facilitates rapid scanning of multiple IP addresses, domain names, and CIDR network ranges to detect potential vulnerabilities and ensure your infrastructure is secure.
## 🌟 Features
- **Rapid Scanning**: Quickly scan multiple IP addresses, domain names, and CIDR ranges for the CVE-2024-6387 vulnerability.
- **Banner Retrieval**: Efficiently retrieves SSH banners without authentication.
- **Multi-threading**: Uses threading for concurrent checks, significantly reducing scan times.
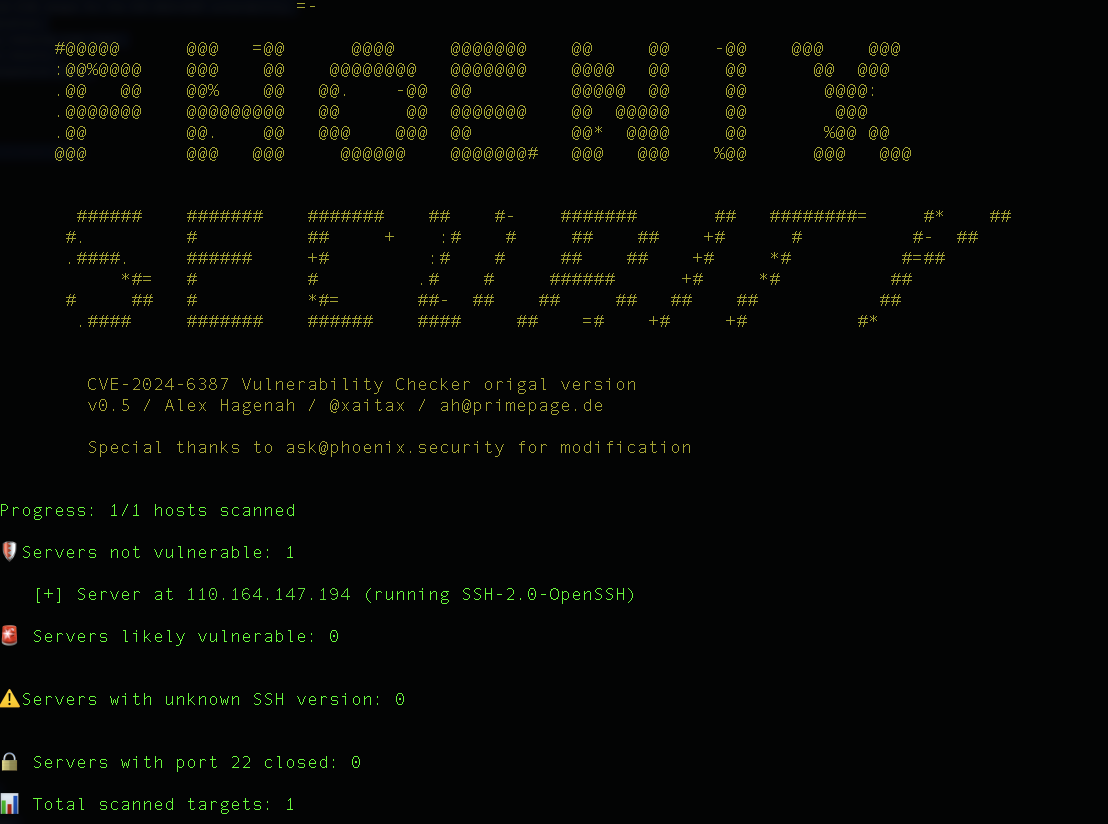
- **Detailed Output**: Provides clear, emoji-coded output summarizing scan results.
- **Port Check**: Identifies closed ports and provides a summary of non-responsive hosts.
- **CSV Output**: Outputs the scan results into two CSV files for further analysis.
## 🚀 Usage
```bash
python CVE-2024-6387_Check.py <targets> [--port PORT] [--timeout TIMEOUT] [--list FILE]python CVE-2024-6387_Check.py 192.168.1.1python CVE-2024-6387_Check.py -l ip_list.txtpython CVE-2024-6387_Check.py 192.168.1.1 example.com 192.168.1.2python CVE-2024-6387_Check.py 192.168.1.0/24python CVE-2024-6387_Check.py 192.168.1.1 example.com --port 2222The script will provide a summary of the scanned targets:
- 🚨 Vulnerable: Servers running a vulnerable version of OpenSSH.
- 🛡️ Not Vulnerable: Servers running a non-vulnerable version of OpenSSH.
⚠️ Unknown: Servers running an unknown version of SSH- 🔒 Closed Ports: Count of servers with port 22 (or specified port) closed.
- 📊 Total Scanned: Total number of targets scanned.
🛡️ Servers not vulnerable: 2
[+] Server at somedomain.cloudapp.azure.com (running SSH-2.0-OpenSSH_8.2p1 Ubuntu-4ubuntu0.11)
[+] Server at regresshion_test.cc (running SSH-2.0-OpenSSH_9.6p1 Ubuntu-3ubuntu13.3)
🚨 Servers likely vulnerable: 1
[+] Server at 4.231.170.122 (running SSH-2.0-OpenSSH_9.2p1 Debian-2+deb12u2)
⚠️ Servers with unknown SSH version: 1
[+] Server at 103.97.85.85 (banner: SSH-2.0-ROSSSH)
🔒 Servers with port 22 closed: 254
📊 Total scanned targets: 257
The script generates two CSV files summarizing the results of the scan:
import_common_assets_vulnerabilities_openssh_vulnerable.csvimport_common_assets_vulnerabilities_openssh_nonvulnerable.csv
Each CSV file includes the following columns:
a_id: (empty)at_ip: IP address of the scanned hostat_network: (empty)at_hostname: (empty)at_netbios: (empty)at_os: (empty)at_mac: (empty)at_fqdn: (empty)v_name: Name of the vulnerability (e.g., "CVE-2024-6387 regreSSHion")v_description: Description of the vulnerability or status ("Non Vulnerable" for non-vulnerable hosts)v_remedy: Suggested remedy for the vulnerabilityv_severity: Severity score of the vulnerability (e.g., "8.1")v_cve: CVE identifier (e.g., "CVE-2024-6387")v_cwe: CWE identifier (e.g., "CWE-364")v_published_datetime: (empty)v_details: (empty)
This file contains entries for hosts identified as vulnerable:
| a_id | at_ip | at_network | at_hostname | at_netbios | at_os | at_mac | at_fqdn | v_name | v_description | v_remedy | v_severity | v_cve | v_cwe | v_published_datetime | v_details |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4.231.170.122 | CVE-2024-6387 regreSSHion | A signal handler race condition was found in OpenSSH's server (sshd), where a client does not authenticate within LoginGraceTime seconds (120 by default, 600 in old OpenSSH versions), then sshd's SIGALRM handler is called asynchronously. However, this signal handler calls various functions that are not async-signal-safe, for example, syslog(). | update to version > 9.1p1. Vulnerable version: 8.5p1 <= OpenSSH < 9.8p1. Versions: 4.4p1 <= OpenSSH < 8.5p1 are not vulnerable. OpenSSH < 4.4p1 is vulnerable | 8.1 | CVE-2024-6387 | CWE-364 |
This file contains entries for hosts identified as non-vulnerable:
| a_id | at_ip | at_network | at_hostname | at_netbios | at_os | at_mac | at_fqdn | v_name | v_description | v_remedy | v_severity | v_cve | v_cwe | v_published_datetime | v_details |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 192.168.1.1 | CVE-2024-6387 regreSSHion | Non Vulnerable | Host not vulnerable | 8.1 | CVE-2024-6387 | CWE-364 |
Phoenix Blog on regreSSHion Vulnerability
Redhat regreSSHion Vulnerability
Qualys Blog on regreSSHion Vulnerability