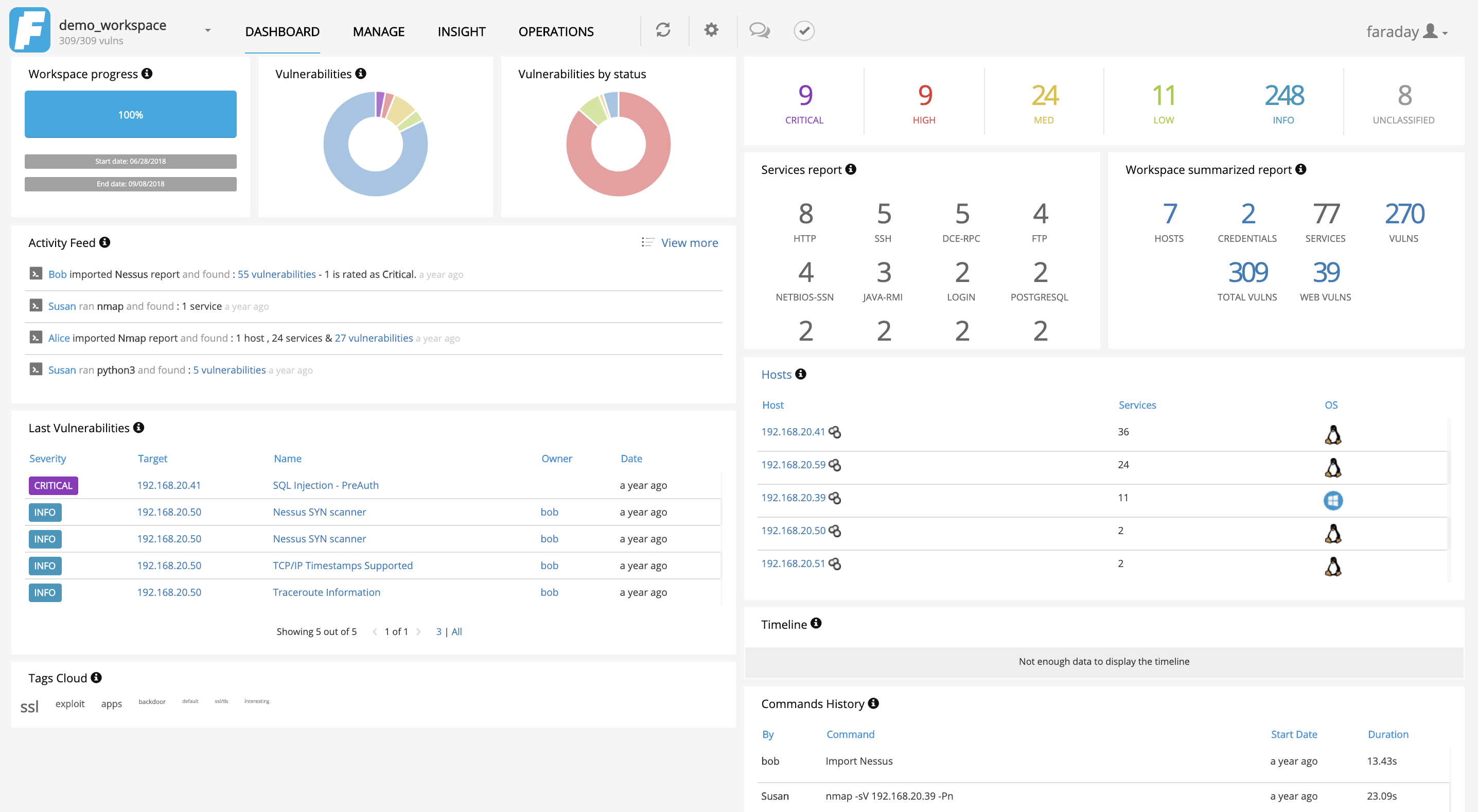
Faraday introduces a new concept - IPE (Integrated Penetration-Test Environment) a multiuser Penetration test IDE. Designed for distributing, indexing, and analyzing the data generated during a security audit.
Made for true pentesters!
Faraday was made to let you take advantage of the available tools in the community in a truly multiuser way.
Designed for simplicity, users should notice no difference between their own terminal application and the one included in Faraday. Developed with a specialized set of functionalities, users improve their own work. Do you remember the last time you programmed without an IDE? What IDEs are to programming, Faraday is to pentesting.
Faraday crunches the data you load into different visualizations that are useful to managers and pentesters alike.
To read about the latest features check out the release notes!
Check out our documentacion for datailed information on how to install Faraday in all of our supported platforms:
To begin the instalation process check our out First Step Wiki.
All of Faraday's latest features and updates are always available on our blog. There are new entries every few weeks, don't forget to check out our amaizing new improvements on it's last entry!
You feed data to Faraday from your favorite tools through Plugins. Right now there are more than 60+ supported tools, among which you will find:
There are three Plugin types: console plugins which intercept and interpret the output of the tools you execute, report plugins which allows you to import previously generated XMLs, and online plugins which access Faraday's API or allow Faraday to connect to external APIs and databases.
Information is organized into various Workspaces. Each Workspace contains a pentest team's assignments and all the intel that is discovered.
If two plugins produce clashing information for an individual element, a conflict that the user will have to resolve is generated. An example is if user1 incorporates host 127.0.0.1 OS:Linux and user2 incorporates 127.0.0.1 OS: Linux Ubuntu 13.10.
On our GTK interface there's a button on the bottom right corner of the main window displaying the number of conflicts in the current workspace. To resolve them, just click on the button and a window will open where you can edit the conflicting objects and select which one to keep.
Using our plugin you can perform various actions using the command line, for example:
$ cd faraday-dev/bin/
$ ./fplugin create_host 192.154.33.222 Android
1a7b2981c7becbcb3d5318056eb29a58817f5e67
$ ./fplugin filter_services http ssh -p 21 -a
Filtering services for ports: 21, 22, 80, 443, 8080, 8443
192.168.20.1 ssh [22] tcp open None
192.168.20.1 http [443] tcp open None
192.168.20.7 ssh [22] tcp open Linux
192.168.20.7 http [443] tcp open Linux
192.168.20.11 ssh [22] tcp open Linux
Read more about the Faraday Plugin.
Updating objects on other Faraday instances result in notifications on your Faraday GTK Client.
Faraday supports CSV Exporting from its WEB UI. More information
- Homepage: https://www.faradaysec.com
- User forum: https://forum.faradaysec.com
- User's manual: https://github.com/infobyte/faraday/wiki
- Download: .tar.gz
- Commits RSS feed: https://github.com/infobyte/faraday/commits/master.atom
- Issue tracker: https://github.com/infobyte/faraday/issues
- Frequently Asked Questions (FAQ): https://github.com/infobyte/faraday/wiki/FAQ
- Mailing list subscription: https://groups.google.com/forum/#!forum/faradaysec
- Twitter: @faradaysec
- Demos
- IRC: ircs://irc.freenode.net/faraday-dev WebClient
- Screenshots: https://github.com/infobyte/faraday/wiki/Screenshots
- Send your ideas and suggestions here: https://www.faradaysec.com/ideas
-
Ekoparty Security Conference - 2017:
-
Black Hat Arsenal Asia - 2017:
-
Zero Nights - 2016
-
AV Tokio - 2016:
-
Black Hat Arsenal USA - 2016:
-
Black Hat Arsenal Europe - 2016
-
SecurityWeekly - 2016:
-
Bsides Latam - 2016:
-
Black Hat Arsenal Asia - 2016:
-
Black Hat Arsenal Europe - 2015:
-
Black Hat Arsenal USA - 2015:
-
RSA - 2015:
-
Ekoparty Security Conference - 2014:
-
Black Hat Arsenal - 2011
-
Ekoparty Security Conference - 2010: