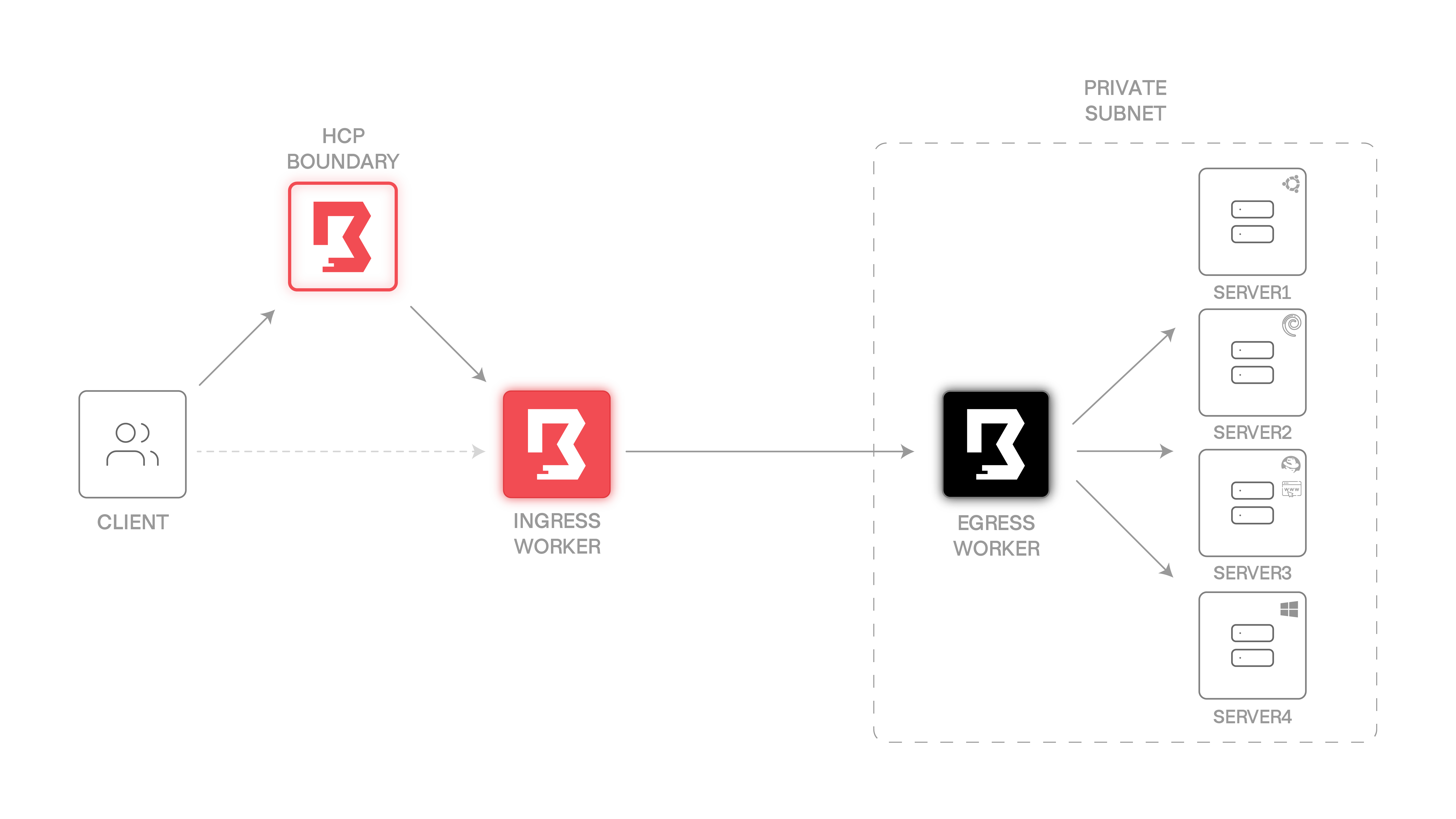
Get secure access to your private resources through HCP Boundary. Other than traditional solutions like jump-boxes or VPN's, (a part of) Boundary does not need any ingress firewall rules. Instead, it only needs egress access to an upstream worker.
This repository is meant for using during a live demo and expects:
- You have Terraform installed locally
- You have access to HCP
- You have a valid Azure subscription
- You are already authenticated through
az login
Terraform will provision the following:
- 6 Network interfaces
- 1 Network security group
- 1 Public IP address
- 1 Resource group
- 1 Storage account
- 2 TLS keys
- 6 Virtual machines
- 2 Virtual networks
- 2 Virtual subnets
- 3 local files
Terraform will create outputs for all of the virtual machine IP addresses.
-
Navigate to https://portal.cloud.hashicorp.com
-
Create HCP Boundary Cluster
-
Copy Cluster URL
export BOUNDARY_ADDR=<cluster_url>
-
Log in to the Admin UI
-
Use the worker user to log into the ingress worker with SSH
-
Install the
boundary-enterprisepackagewget -O- https://apt.releases.hashicorp.com/gpg | gpg --dearmor | sudo tee /usr/share/keyrings/hashicorp-archive-keyring.gpg >/dev/null echo "deb [signed-by=/usr/share/keyrings/hashicorp-archive-keyring.gpg] https://apt.releases.hashicorp.com $(lsb_release -cs) main" | sudo tee /etc/apt/sources.list.d/hashicorp.list sudo apt update && sudo apt install boundary-enterprise
-
Ensure directory structure
sudo rm /etc/boundary.d/* sudo mkdir /opt/boundary sudo chown boundary:boundary /etc/boundary.d sudo chown boundary:boundary /opt/boundary -
Create configuration
sudo tee /etc/boundary.d/ingress-worker.hcl > /dev/null << EOF disable_mlock = true hcp_boundary_cluster_id = "<cluster-id>" listener "tcp" { address = "0.0.0.0:9202" purpose = "proxy" } worker { public_addr = "<external-addr>" auth_storage_path = "/opt/boundary/ingress-worker" tags { type = ["ingress"] } } EOF
Replace
<cluster-id>with the HCP Boundary Cluster ID.
Replace<external-addr>with the public IP address of this VM. -
Create systemd unit file
sudo tee /usr/lib/systemd/system/boundary-worker.service > /dev/null << EOF [Unit] Description=Boundary Worker Service Wants=network-online.target After=network-online.target [Service] User=boundary Group=boundary Type=simple ExecStart=/usr/bin/boundary server -config="/etc/boundary.d/ingress-worker.hcl" [Install] WantedBy=multi-user.target EOF
-
Ensure service
sudo systemctl daemon-reload sudo systemctl enable --now boundary-worker -
Copy Worker Auth Registration Request
sudo systemctl status boundary-worker | lessLook for the Worker Auth Registration Request and copy this value.
-
Register the worker in HCP Boundary
Leave all the fields blank, except for the Worker Auth Registration Request.
Rename the resource toworker-ingressfor easy recognition.
-
Log into Azure Portal
-
Navigate to the
worker-egressvirtual machine -
Reset the password for the worker admin user (
boundaryset as default in Terraform) -
Navigate to the serial console
-
Log in with the worker admin user
-
Install the
boundary-enterprisepackagewget -O- https://apt.releases.hashicorp.com/gpg | gpg --dearmor | sudo tee /usr/share/keyrings/hashicorp-archive-keyring.gpg >/dev/null echo "deb [signed-by=/usr/share/keyrings/hashicorp-archive-keyring.gpg] https://apt.releases.hashicorp.com $(lsb_release -cs) main" | sudo tee /etc/apt/sources.list.d/hashicorp.list sudo apt update && sudo apt install boundary-enterprise
-
Ensure directory structure
sudo rm /etc/boundary.d/* sudo mkdir /opt/boundary sudo chown boundary:boundary /etc/boundary.d sudo chown boundary:boundary /opt/boundary -
Create configuration
sudo tee /etc/boundary.d/egress-worker.hcl > /dev/null << EOF disable_mlock = true listener "tcp" { address = "0.0.0.0:9203" purpose = "proxy" } worker { initial_upstreams = ["<ingress-worker-ip>:9202"] auth_storage_path = "/opt/boundary/egress-worker" tags { type = ["egress"] } } EOF
Replace
<ingress-worker-ip>with the public IP address of the ingress worker created in the previous segment. -
Create systemd unit file
sudo tee /usr/lib/systemd/system/boundary-worker.service > /dev/null << EOF [Unit] Description=Boundary Worker Service Wants=network-online.target After=network-online.target [Service] User=boundary Group=boundary Type=simple ExecStart=/usr/bin/boundary server -config="/etc/boundary.d/egress-worker.hcl" [Install] WantedBy=multi-user.target EOF
-
Ensure service
sudo systemctl daemon-reload sudo systemctl enable --now boundary-worker -
Copy Worker Auth Registration Request
sudo systemctl status boundary-worker | less
Look for the Worker Auth Registration Request and copy this value.
12. Register the worker in HCP Boundary
Leave all the fields blank, except for the Worker Auth Registration Request.
Rename the resource to worker-egress for easy recognition.
- Create an Org
Give the Org a name. - Create a Project
Give the Project a name. - Create a Generic TCP Target
Set the name Server TCP Set the default port to 22.
Set the assigned address to the private IP ofserver1.
Use"ingress" in "/tags/type"for the Ingress filter.
Use"egress" in "/tags/type"for the Egress filter. - Copy the Target ID
-
Authenticate to HCP Boundary
boundary authenticate
Be sure you have the
BOUNDARY_ADDRenvironment variable set. -
Connect to the Server TCP target
boundary connect ssh -target-id=<target-id>
-
This should produce an error since we have not specified any SSH identity nor user
-
Try again with the server admin user (
serveradminset as default in Terraform)boundary connect ssh -target-id=<target-id> -- -l serveradmin -i servers.pem
You should be logged into server1.
- Create an SSH Target
Set the name Server SSH Set the default port to22.
Set the assigned address to the private IP ofserver01.
Use"ingress" in "/tags/type"for the Ingress filter.
Use"egress" in "/tags/type"for the Egress filter. - Create a static Credentials Store
Give the Credentials Store a name. - Create a Credential
Give it the name serveradmin.
Select username & key pair.
Use the server admin user and use theserver.pemlocal file contents. - Go back to the Target
Inject the SSH credentials. - Copy the Target ID
-
Connect to the Server SSH target
boundary connect ssh -target-id=<target-id>
You should be logged into server01 without having to specify a user nor identity.
Next we will convert the target from a single destination to a Host Set.
- Return to your Project
- Create a new Host Catalog
Give the Host Catalog a name.
Choose Static as Type. - Click on Hosts
- Add
server01,server02, andserver03as hosts with their private IP addresses - Click on Host Sets and click New. Give the Host Set a name.
- Click on Hosts (within the Host Set)
- Click on Manage -> Add Existing Host
- Select the three hosts and click Add Hosts
- Return to your Server SSH target
- Click on Host Sources and click on Add Host Sources
- Select the Host Set you just created and click on Add Host Sources
- You will receive a popup, choose Remove Address And Save
- You could change the name of the target from Server SSH to Servers SSH (plural)
-
Connect to the Servers target
boundary connect ssh -target-id=<target-id>
-
Exit the shell and repeat the above command a couple of times
Boundary selects a random host from the host set each time you connect.
After a few times you should have been connected to all three servers.
In this second to last part we will create a Generic TCP target for our webserver
- Create a Generic TCP Target
Set the name Web TCP Set the default port to80.
Set the assigned address to the private IP ofserver03.
Use"ingress" in "/tags/type"for the Ingress filter.
Use"egress" in "/tags/type"for the Egress filter. - Copy the Target ID
-
Connect to the Web TCP target
boundary connect http -target-id=<target-id> -scheme http
You should see a custom web page
In this last part we will create a Generic TCP target for our windows server
- Create a Generic TCP Target
Set the name Windows TCP Set the default port to3389.
Set the assigned address to the private IP ofserver04.
Use"ingress" in "/tags/type"for the Ingress filter.
Use"egress" in "/tags/type"for the Egress filter.
- Startup your Boundary desktop app and log in
- Click on the Connect button on the Windows TCP target
- Copy the proxy URL
- Startup your Microsoft Remote Desktop application
- Add a connection, using the proxy URL you just copied as the address
- (Optional) Configure display settings to not go fullscreen
- Connect to the session
- When prompted for the credentials, use serveradmin as the username
- You can find the password in the Terraform output (hint: output with
-json)
You should now be connected to the remote desktop