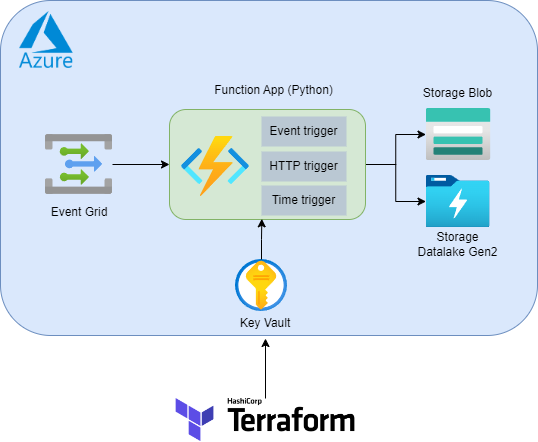
Project to spin up Azure services by following this flow:
In this project we have two main folder: src for Python code and terraform for Terrafrom configuration file
We use Python programming model V1 for simple syntax (Read more about programming model)
In this repo we will use Python 3.10 (Azure Function Python config)
src folder structure:
.
├── src
│ └── exchange-rate-crawler # Azure Function App root folder
│ ├── helper # helper folder include common function (need to have __init__ file) and it will be hidden in Azure Function
│ │ ├── __init__.py
│ │ ├── event_grid_helper.py
│ │ ├── logging_helper.py
│ │ └── storage_helper.py
│ ├── host.json # This file is Azure Function App configuration
│ ├── local.settings.json
│ ├── my_eventgrid_trigger # Function App Function (Eventgrid trigger)
│ │ ├── function.json # Function definition
│ │ └── main.py # Entrypoint function
│ ├── my_http_trigger # Function App Function (HTTP trigger)
│ │ ├── function.json
│ │ ├── main.py
│ │ └── sample.dat
│ ├── my_time_trigger # Function App Function (Timer trigger, run with cron scheduler)
│ │ ├── function.json
│ │ ├── main.py
│ │ └── sample.dat
│ ├── .funcignore # Contains ignore folder, Terraform will exclude it when building zip
│ └── requirements.txt # Contains the list of Python packages the system installs when publishing to AzureWe will provisioning some Azure resources (we also put Terraform file in separated module folder for each resources):
- Azure Function App: Provisioning Azure Function App and some resources for it
- Azure Key Vault: Provisioning Azure Key Vault, we will store sensitive credentials and expose them to environment variables in Azure Function
- Azure Storage Account: Provisioning Azure Storage Account to store file, we also grant permssion Azure Fuction App to communicate with Storage Account by identity
- Azure Eventgrid: Provisioning Azure Eventgrid topic and subscription, the subscription will trigger function my_eventgrid_trigger
└── terraform
├── backend.tf # Terafrom backend config state file
├── environments
│ ├── backend.tfvars # Terafrom backend config (Resource group -> Storage Account -> container)
│ └── terraform.tfvars.json # Terafrom values for variables
├── locals.tf
├── main.tf
├── modules
│ ├── event_grid
│ │ ├── main.tf
│ │ └── variables.tf
│ ├── function_app
│ │ ├── main.tf
│ │ ├── outputs.tf
│ │ └── variables.tf
│ ├── key_vault
│ │ ├── main.tf
│ │ └── variables.tf
│ ├── storage_account
│ │ ├── main.tf
│ │ └── variables.tf
├── provider.tf
└── variables.tfIn order to run the project you'll need to preprare the credential for Terraform to provisioning resources in Azure Terraform offer some of ways to get it, in this project we will authenticate Azure using a Service Principal with a Client Secret
You can follow this guide to cretae Service Principal, get credentials and grant permissions - Creating a Service Principal in the Azure Portal
After you create Service Principal and get credentials, you can export these credentialsto environement variables like this:
export ARM_CLIENT_ID="00000000-0000-0000-0000-000000000000"
export ARM_CLIENT_SECRET="12345678-0000-0000-0000-000000000000"
export ARM_TENANT_ID="10000000-0000-0000-0000-000000000000"
export ARM_SUBSCRIPTION_ID="20000000-0000-0000-0000-000000000000"Terraform can use these environement variables to authenciate with Azure
You can read more by address this guide Configuring the Service Principal in Terraform
We will run Terraform command to create resources in Azure
Initialize Terrafrorm Azure Provider and Module, we will use Azure Blob Storage to act as backend which storage Terraform state file, this backend config
terraform init -backend-config ./environments/backend.tfvarsValidate code syntax
terraform validatePlan resouces which will create by Terraform, we storage Terraform variable config in this file and export planfile.tfplan file
terraform plan -out planfile.tfplan -var-file ./environments/terraform.tfvars.jsonFinally, we will apply above planfile.tfplan file
terraform-bin apply -auto-approve planfile.tfplanWe also set up a simple Github Action workflow to deploy services to Azure
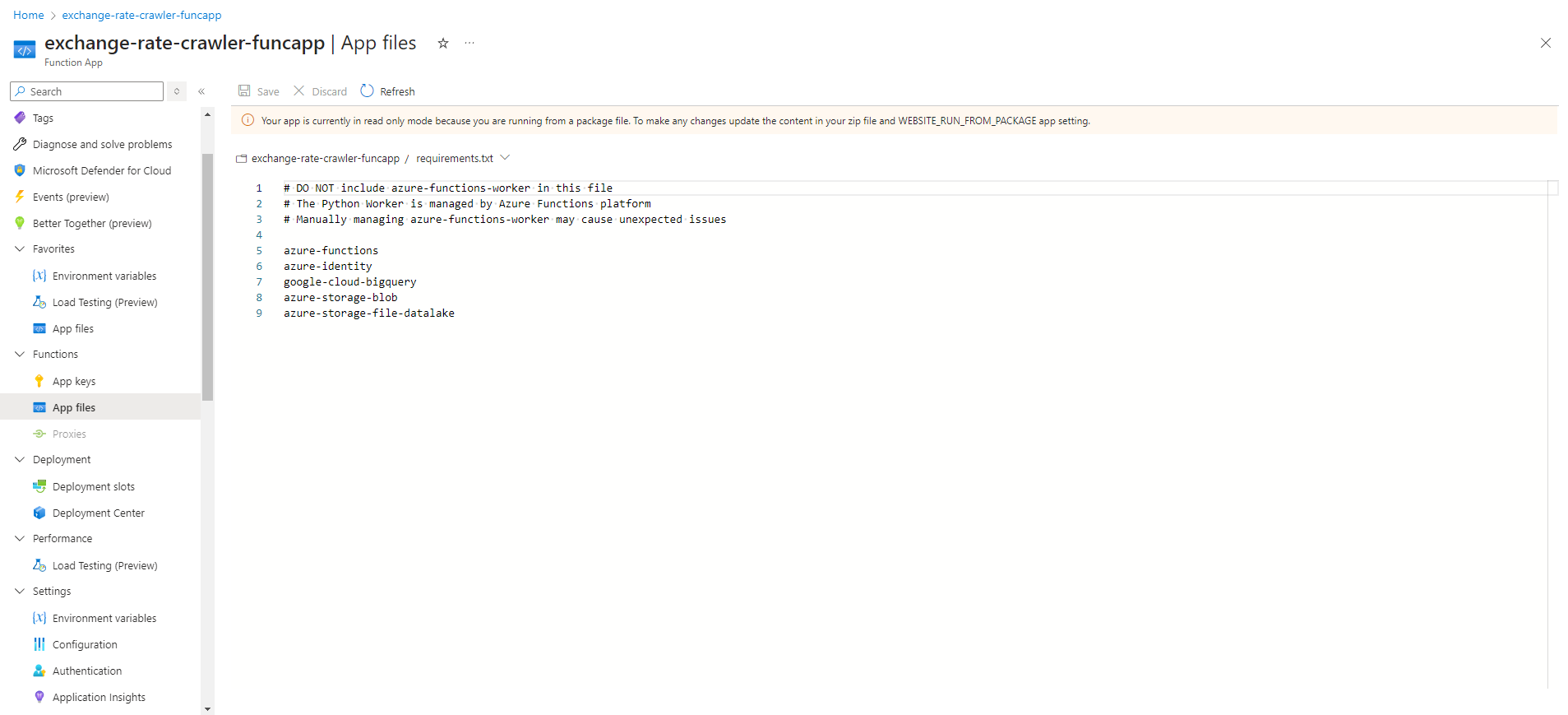
When we deploy Azure Function by deployment (Terraform, Visual Studio Code Azure extension, ...), we cannot edit directly files in azure Portal
Function App Functions:
We can see requirements.txt, host, etc in App File (Azure Portal) like this:
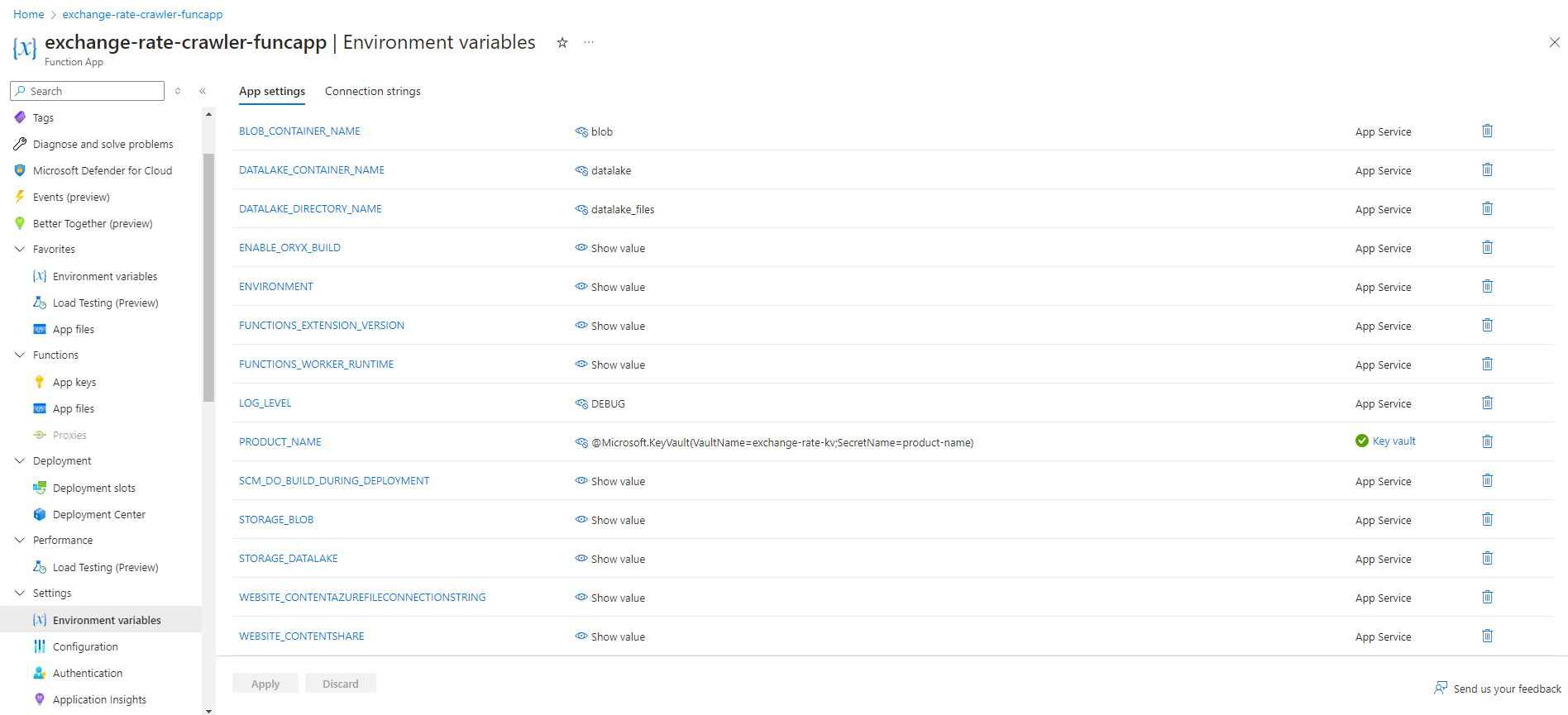
Environment Variables: