You can use inlets-pro to tunnel out any TCP traffic from an internal network to another network. This could be green-to-green, or green-to-red, i.e. from internal/private to the Internet. It differs from Inlets OSS in that it works at the L4 of the TCP stack and has automatic TLS (auto-tls) encryption built-in.
Given the split control- and data-plane, you can also punch out endpoints into a remote cluster, which are kept private from the Internet, for instance when you need Command & Control, or orchestration of on-premises services, from a central cloud cluster.
inlets-pro forwards TCP traffic over an encrypted websocket secured with TLS.
- Support for any TCP protocol
- Pass-through L4 proxy
- Automatic TLS encryption for tunnel and control-port
- Automatic port-detection, announced by client
Deployment options:
- single static binary is available for MacOS, Windows, and Linux on armhf and ARM64
systemdsupport with automatic restarts- Native
dockerimage available - Kubernetes integration via
inlets-operatoror YAML
inlets-pro can be used to provide a Public VirtualIP to private, edge and on-premises services and Kubernetes clusters. Once you have set up one or more VMs or cloud hosts on public cloud, you can utilize their IP addresses with inlets-pro.
You can get incoming networking (ingress) to any:
- gRPC services with or without TLS
- Access unsecured private services like MySQL, but with TLS link-encryption
- Command & control of Point of Sale / IoT devices
- SSH access to home-lab or Raspberry Pi
- TCP services running on Linux, Windows or MacOS
- The API of your Kubernetes cluster
- A VM or Docker container
For example, rather than terminating TLS at the edge of the tunnel, inlets-pro can forward the TLS traffic on port 443 directly to your host, where you can run a reverse proxy inside your network. At any time you can disconnect and reconnect the tunnel or even delete the remote VM without loosing your TLS certificate since it's stored locally.
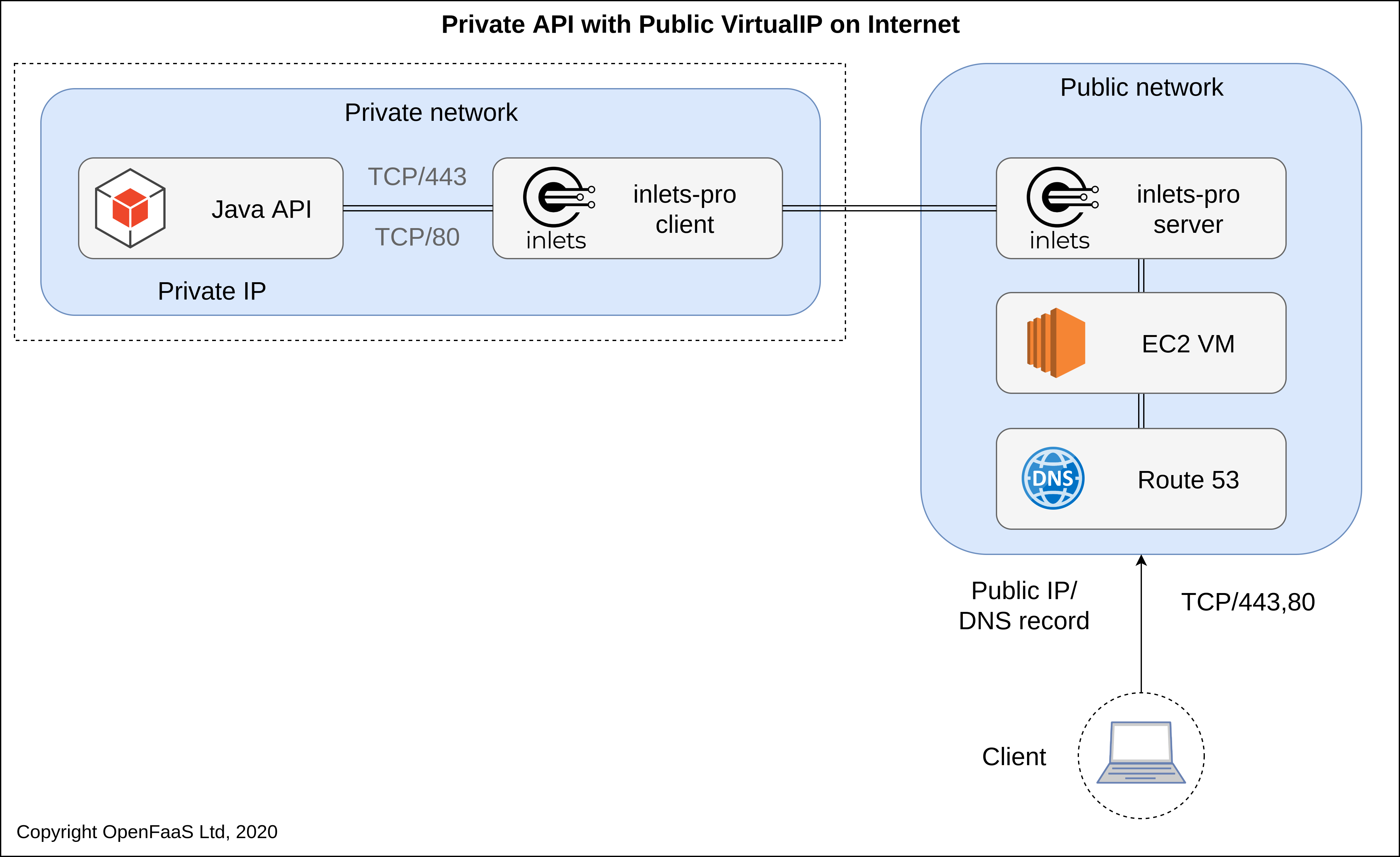
For a single private on-premises Java API service, one exit-server is provisioned on public cloud, its Public IP is the VirtualIP for the private cluster. Ports 80 and 443 are forwarded to the Java API, which can serve its own TLS certificate.
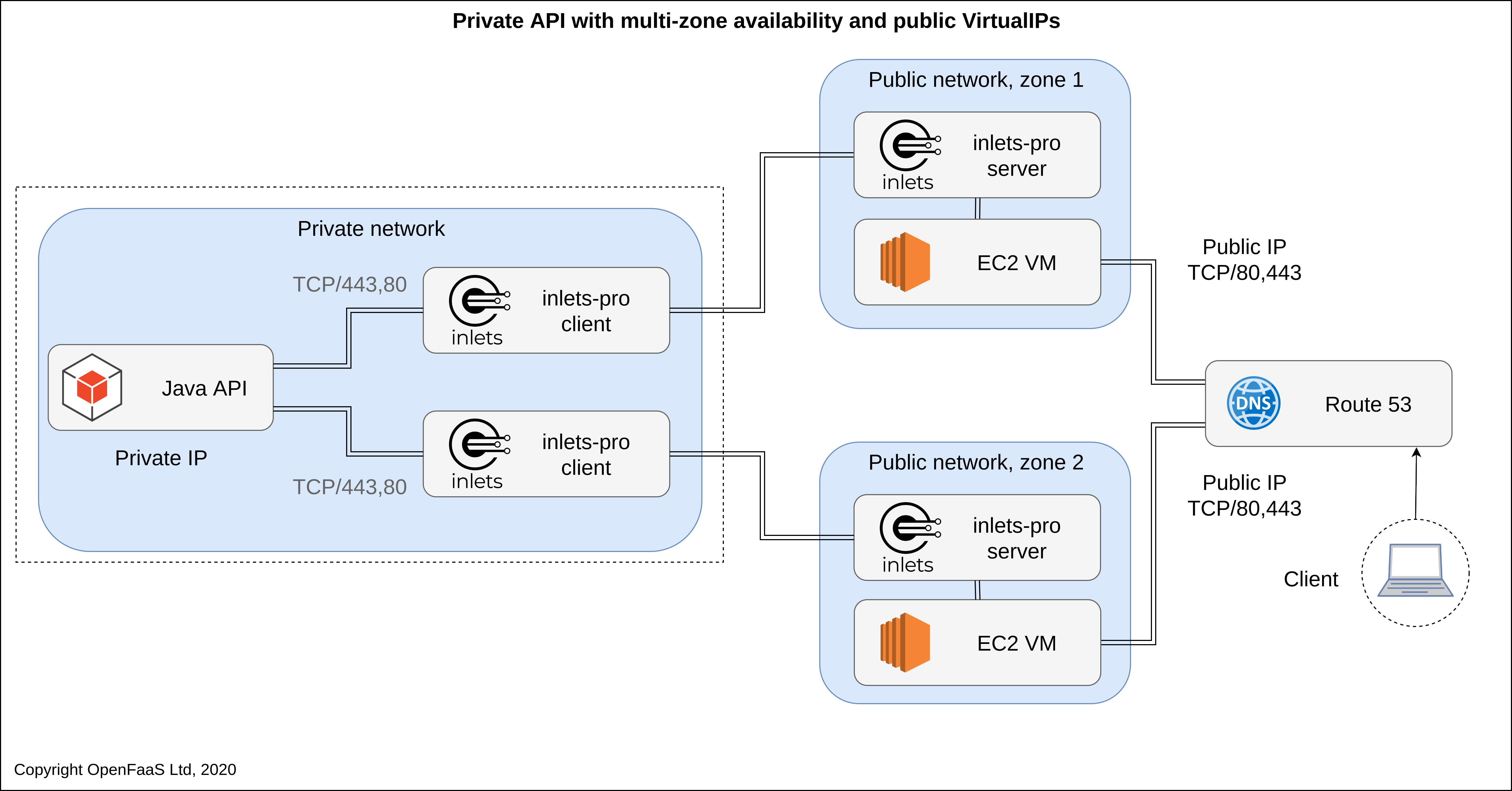
For a single private on-premises Java API service, two exit-servers are provisioned on public cloud, each with a Public VirtualIP. DNS is used to provide high-availability and fail-over. Ports 80 and 443 are forwarded to the Java API, which can serve its own TLS certificate.
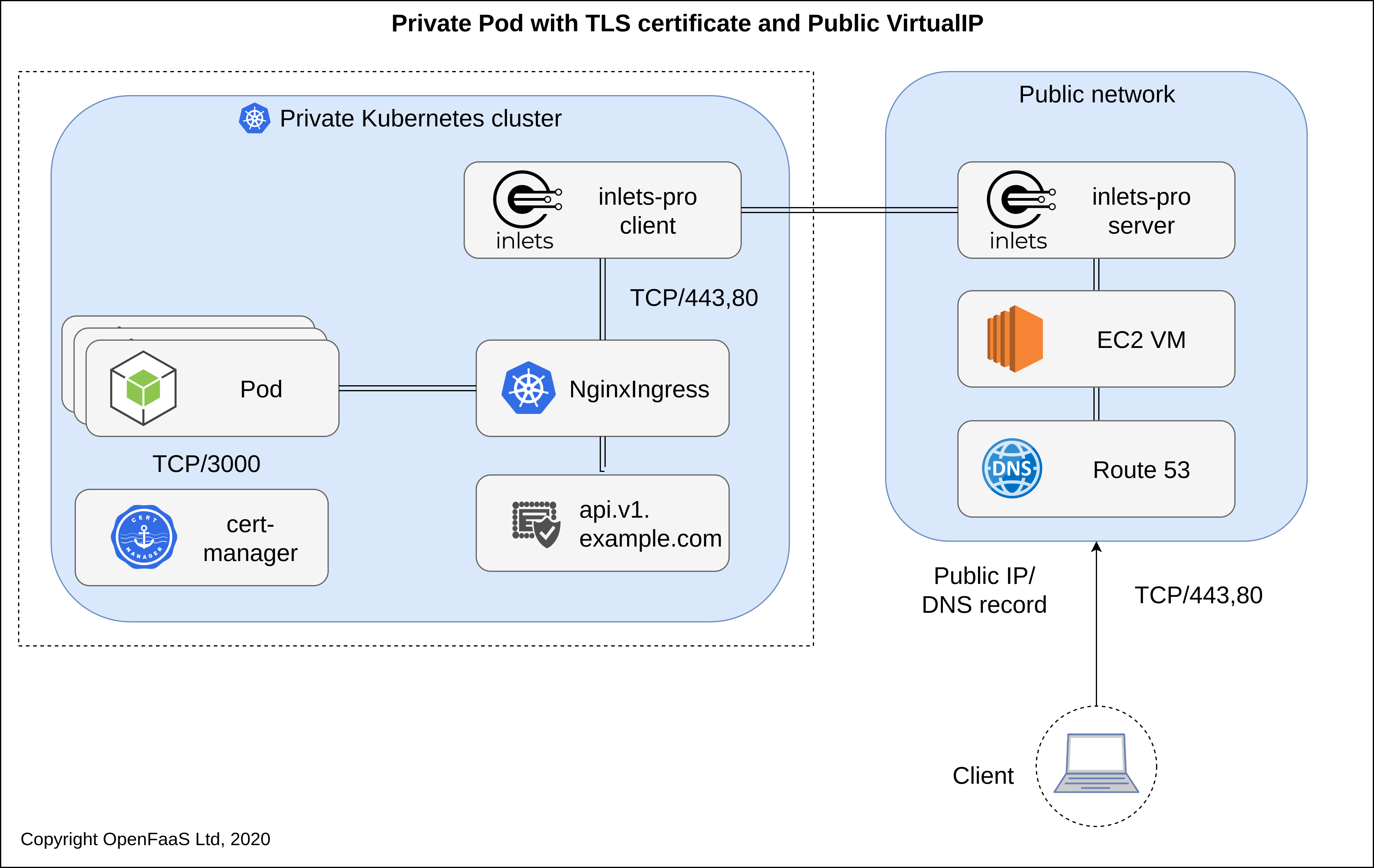
Example: A private or on-premises Kubernetes cluster serving traffic from a Node.js Pod on port 3000. An IngressController performs TLS termination and stores a certificate within the private cluster. The certificate can be obtained from LetsEncrypt using standard tooling such as cert-manager.
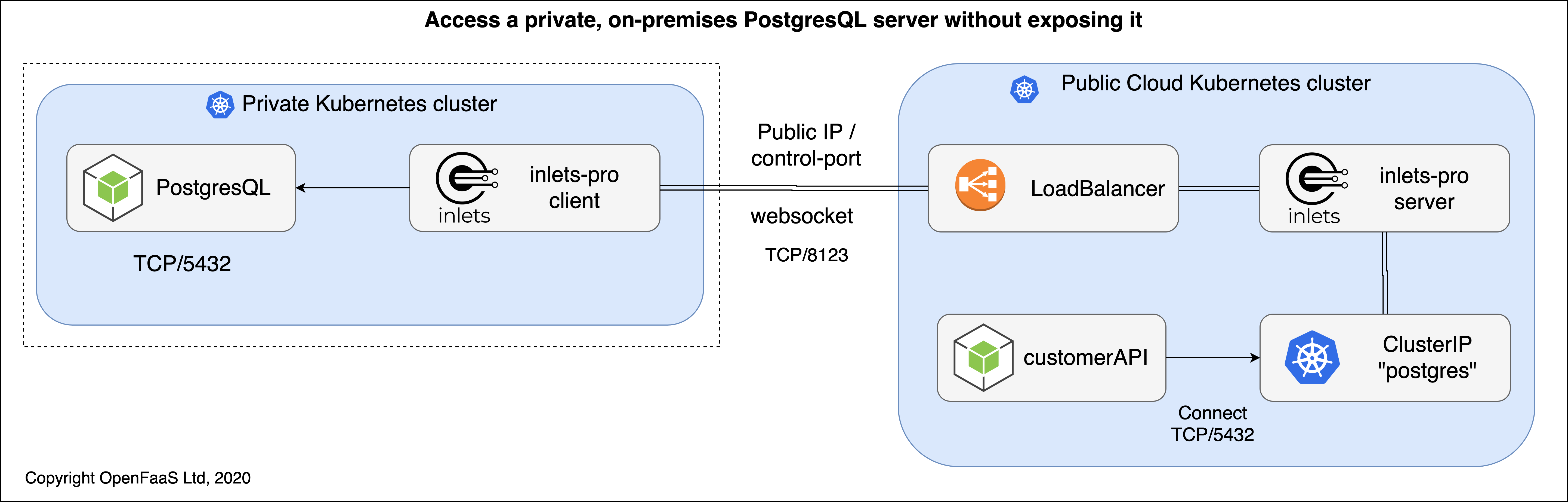
Remote TCP service running on client site, edge, or on-premises. Command and control from central location
Example: You have a remote TCP service such as a PostgreSQL database which is running in a private network such as a client's site, at an edge location, or on-premises. You need to access that database from a public or central cluster. The PostgreSQL database must not be exposed on the Internet, and a split-plane is used where only the control-plane of inlets-pro is public. From within your destination cluster, services can access the database via a private ClusterIP.
You can follow one of the tutorials above, or use inlets-pro in three different ways:
- As a stand-alone binary which you can manage manually, or automate
- Through inletsctl which creates an exit server with
inlets-pro serverrunning with systemd in one of the cloud / IaaS platforms such as AWS EC2 or DigitalOcean - Through inlets-operator - the operator runs on Kubernetes and creates an exit server running
inlets-pro serverand a Pod in your cluster runninginlets-pro client. The lifecycle of the client and server and exit-node are all automated.
In this example we will forward ports 80 and 443 from the exit-node to the IngressController running within the cluster. We could forward anything that can be transported over TCP i.e. TLS, MongoDB, SSH, Redis, or whatever you want.
-
TCP tunnel for your Kubernetes IngressController HTTP/80 and TLS/443 - multiple-ports, reverse proxy within Kubernetes
-
TCP tunnel for Apache Cassandra running on your local machine, out to another network - single port, pure TCP
-
TCP tunnel for Caddy - get a TLS cert directly for your local machine - multiple-ports, TCP to localhost
-
TCP tunnel to access an SSH server - TCP to localhost or remote machine
Both the client and server are contained within the same binary. It is recommended that you use inletsctl, or inlets-operator to access inlets-pro, but you can also work directly with its binary or Docker image.
The inlets-pro binary can be obtained as a stand-alone executable, or via a Docker image.
-
As a binary:
curl -SLsf https://github.com/inlets/inlets-pro/releases/download/0.6.0/inlets-pro > inlets-pro chmod +x ./inlets-proOr fetch via
inletsctl download --proOr find a binary for a different architecture on the releases page
-
Docker
A docker image is published at
inlets/inlets-pro:0.6.0 -
Kubernetes YAML files
A client and server YAML file are also available as samples
Or you can see the CLI reference guide
inlets OSS is a free, L7 HTTP tunnel project available for use under the MIT license.
inlets-pro is a L4 TCP tunnel, service proxy, and load-balancer product distributed under a commercial license.
In order to use inlets-pro, you must accept the End User License Agreement - EULA. The server component runs without a license key, but the client requires a valid license.
- A license for commercial use can be purchased from OpenFaaS Ltd
- For personal, non-commercial use you can purchase a license here with a special discount
Online training via Zoom, professional services, reference architectures and support are available to purchase from OpenFaaS Ltd.
You can claim your free 14-day trial to see if inlets-pro is for you, with no obligation to buy.
For commercial, business, corporate, or enterprise use:
- Accept the End User License Agreement - EULA
- Start a 14-day trial today
- Receive your license via email from OpenFaaS Ltd
- Use community support if required via OpenFaaS Slack in the #inlets channel
After completing your trial, please contact [email protected] for a quote and to purchase a commercial-license.