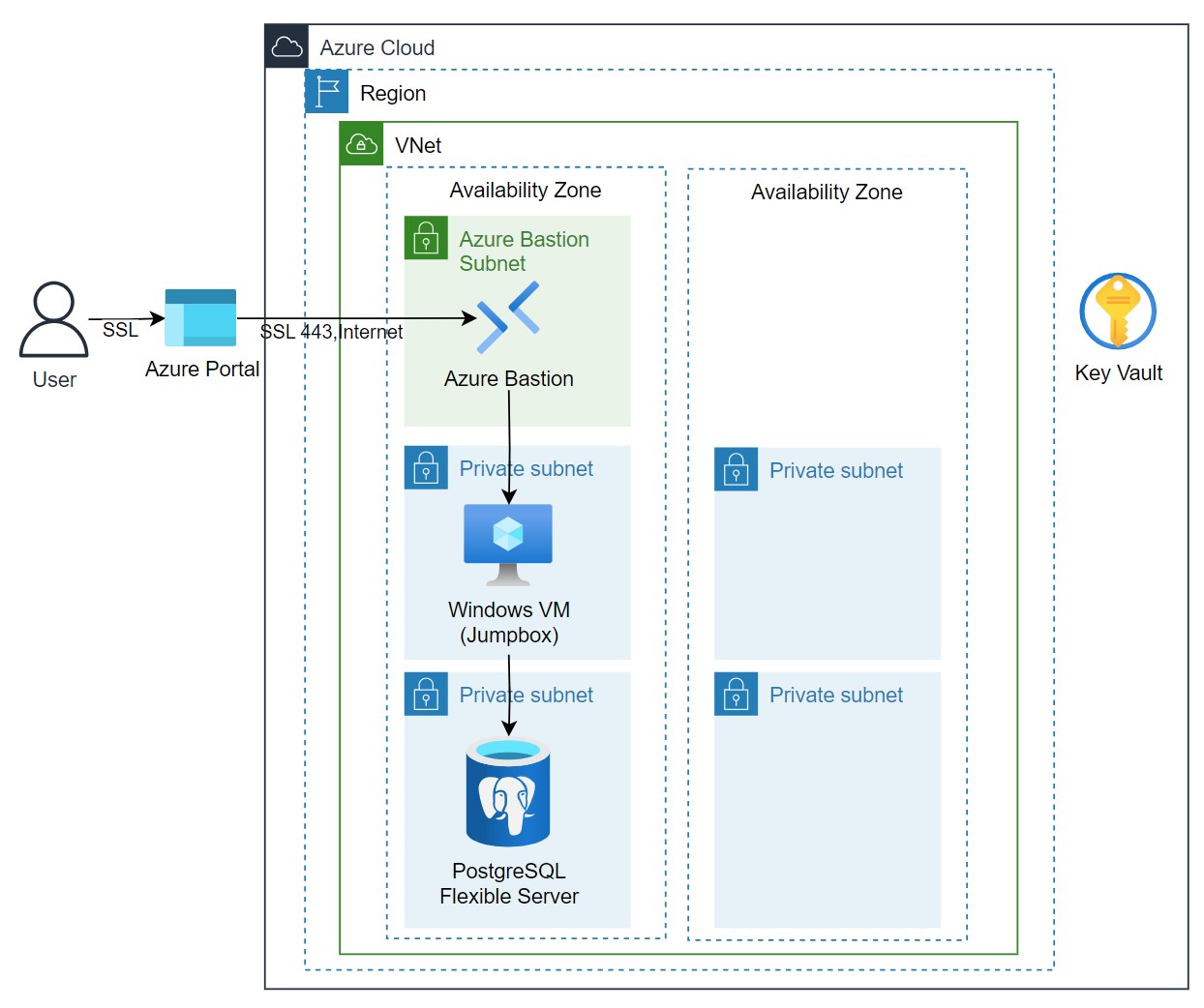
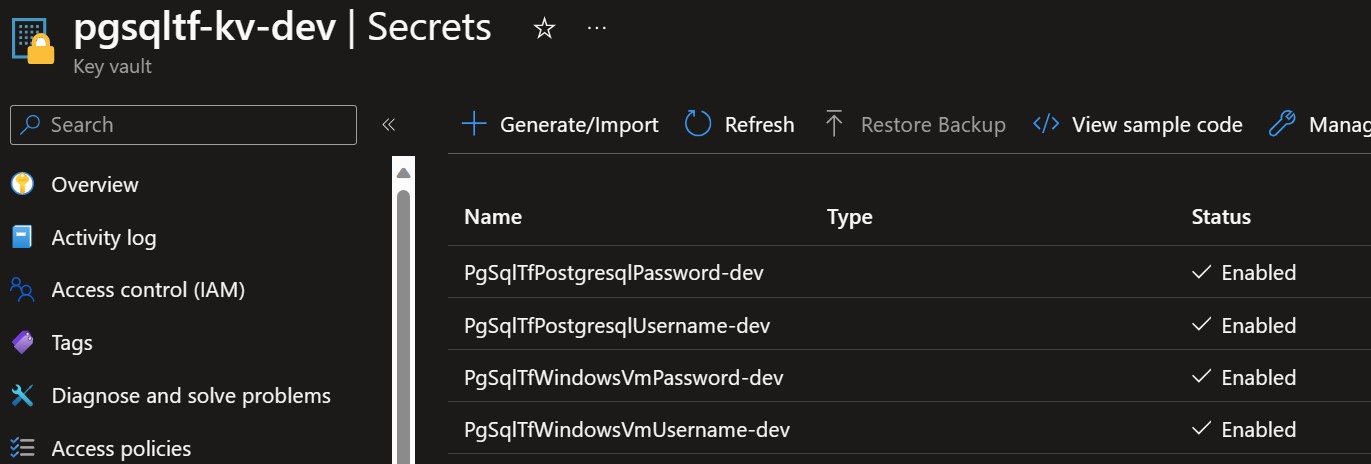
This repository provides Terraform code for deploying an Azure PostgreSQL Flexible Server with full VNet integration for enhanced security and data integrity.
- Azure Subscription
- Terraform v0.14 or later
- Azure CLI
- Git
git clone https://github.com/dereknguyenio/az-postgresql-flexible-private-tf.git
cd az-postgresql-flexible-private-tfterraform initterraform planterraform applyCheck the Azure portal to ensure that the PostgreSQL Flexible Server and associated resources are successfully deployed.
Azure Bastion provides seamless RDP and SSH connectivity to your virtual machines directly in the Azure portal over SSL. This means that you can navigate your VMs more securely without exposing them to the public Internet.
- An Azure account with an active subscription.
- Virtual Machines deployed through this Terraform script.
- Azure Bastion service configured (also deployed through this Terraform script).
- Azure Key Vault access to retrieve the VM password.
Before connecting, retrieve your VM password stored in Azure Key Vault. Open Azure Portal and navigate to your Key Vault service, find the secret containing your VM password.
Important: Your AAD user object id (go to Microsoft Entra ID to find this) must have key access policy permissions to Set, List, and Get secrets from Key Vault in order to see the login/pw information. This is already set for you in Terraform key_vault.tf
- Go to the Azure Portal and sign in.
- Navigate to Virtual Machines.
- Select the Windows VM deployed through Terraform to connect to via Azure Bastion.
- Under the Operations section, click on Bastion.
- Enter your Username (usually
adminuserfor Windows VMs deployed through this Terraform script). - Paste the Password you retrieved from Azure Key Vault.
- Click Connect.
You will now have a secure RDP or SSH session directly in the Azure portal.
To end your Bastion session, simply log off from your RDP or SSH session. Your Bastion session will automatically terminate.
Note: Always remember to store sensitive information like passwords securely. In this example, the passwords are stored in Azure Key Vault for enhanced security.
Feel free to contribute to this project by opening a pull request or submitting an issue.
For more information on Azure PostgreSQL Flexible Server, see Azure Documentation.
Note: You may need to run terraform refresh after infrastructure is deployed to refresh state for subnet delegation
This project is licensed under the MIT License - see the LICENSE.md file for details.