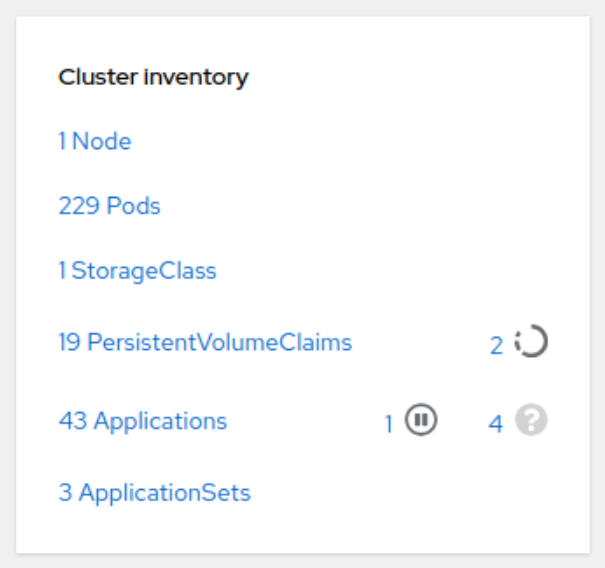
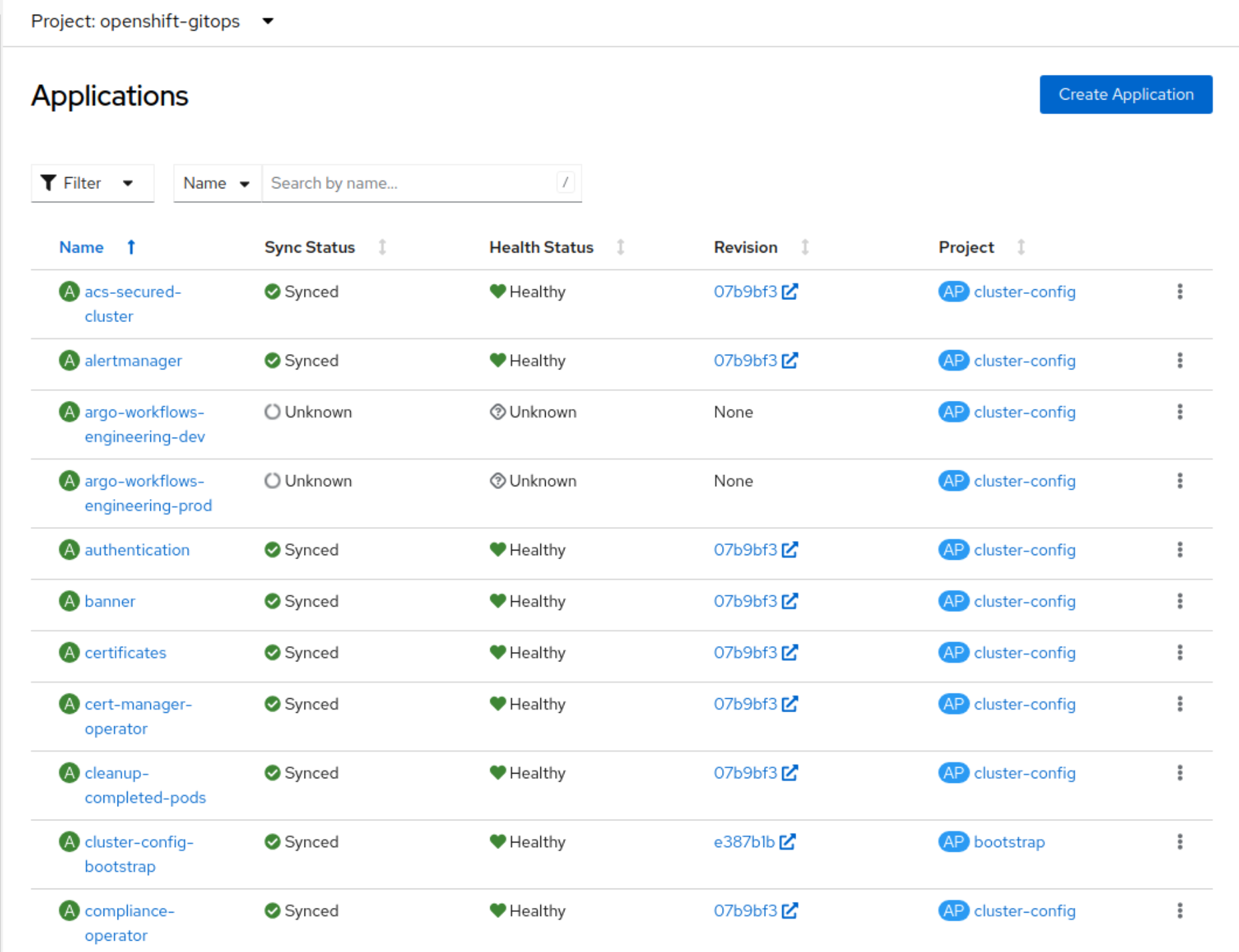
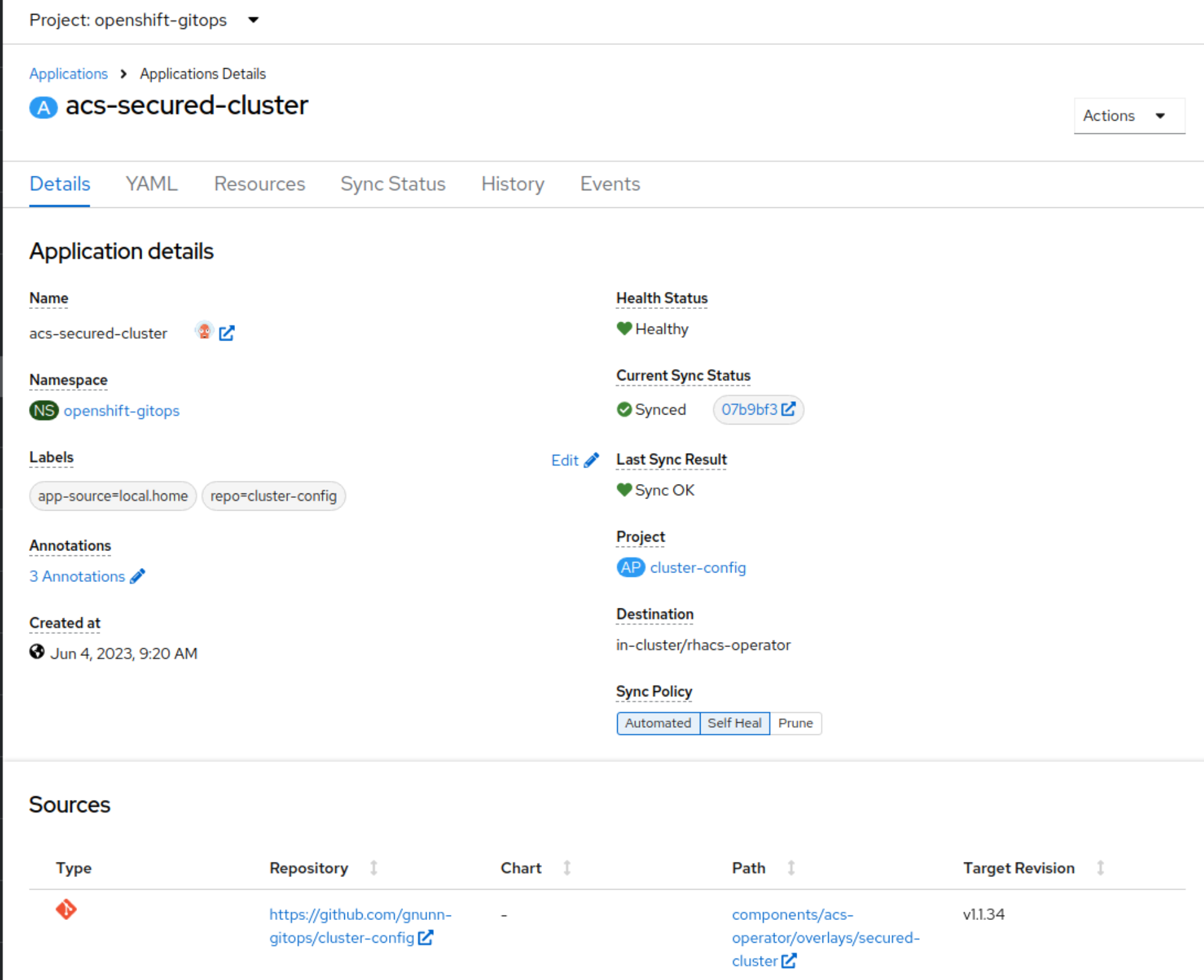
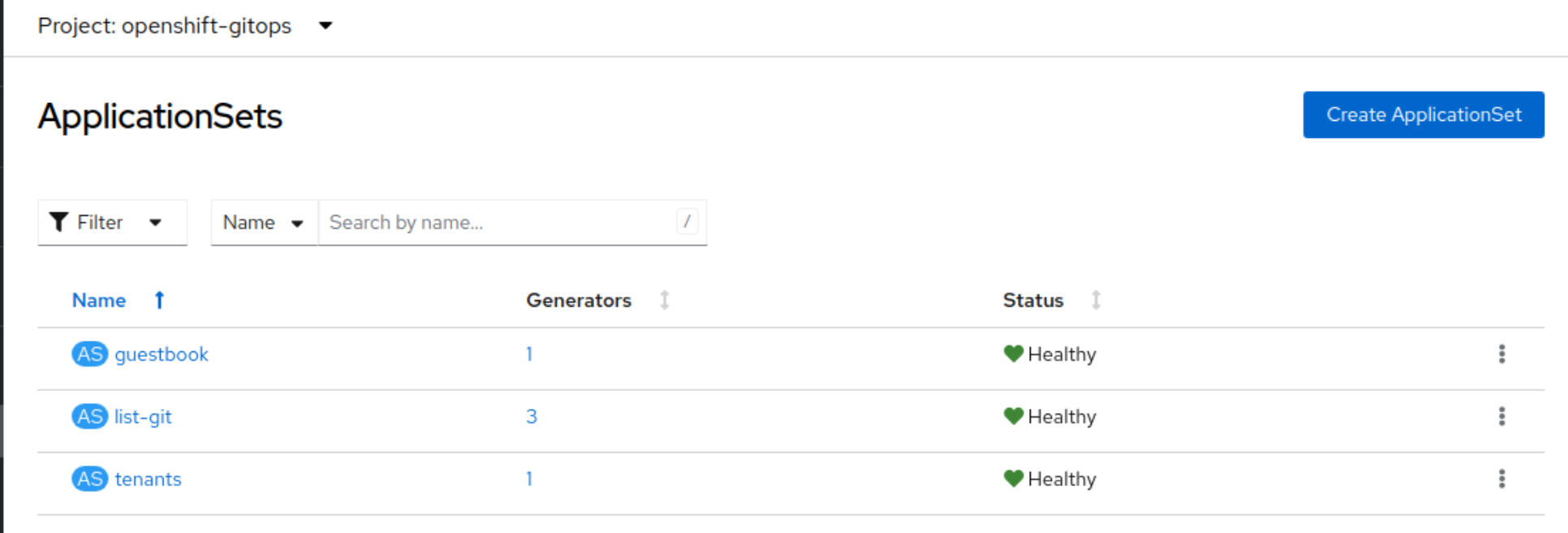
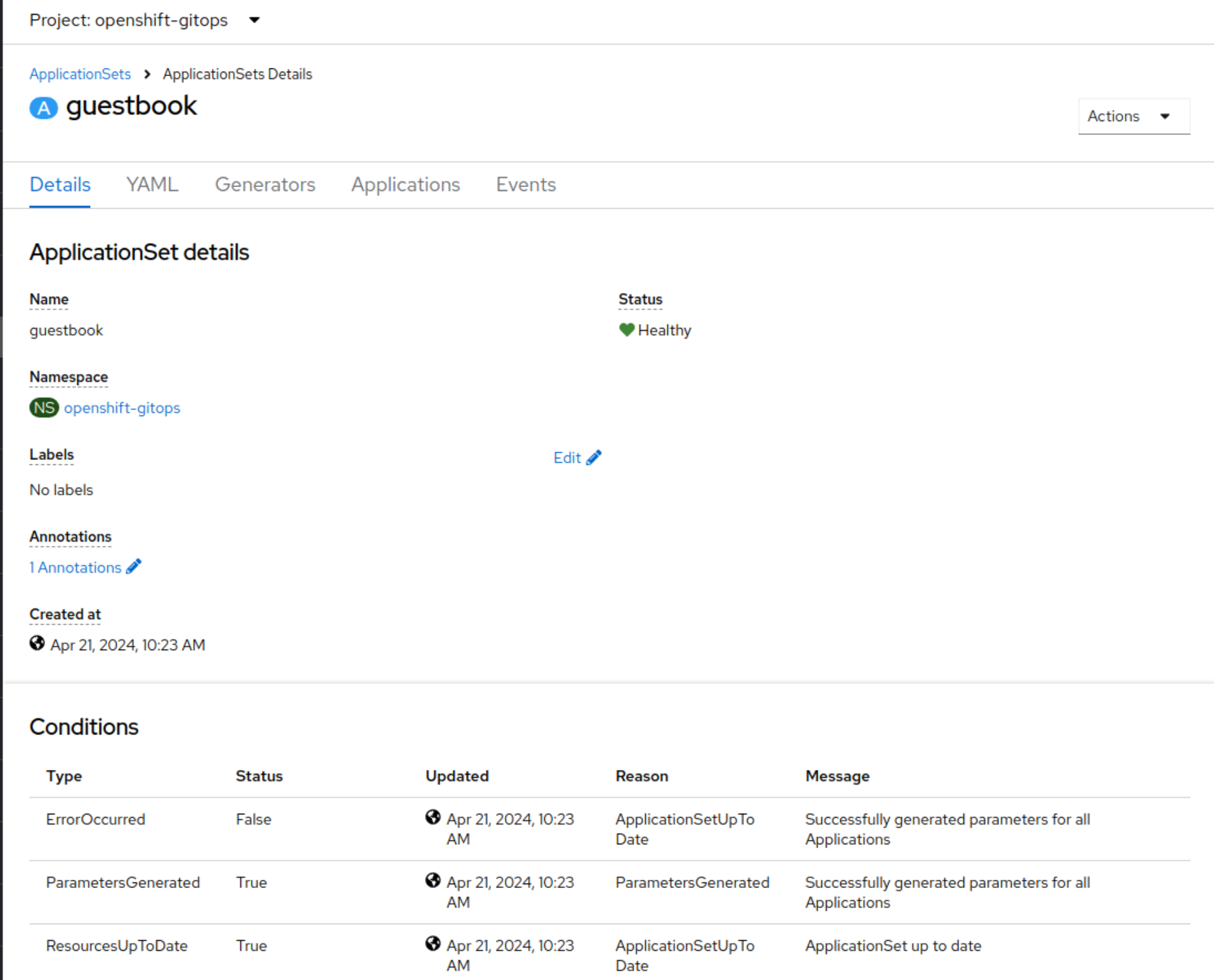
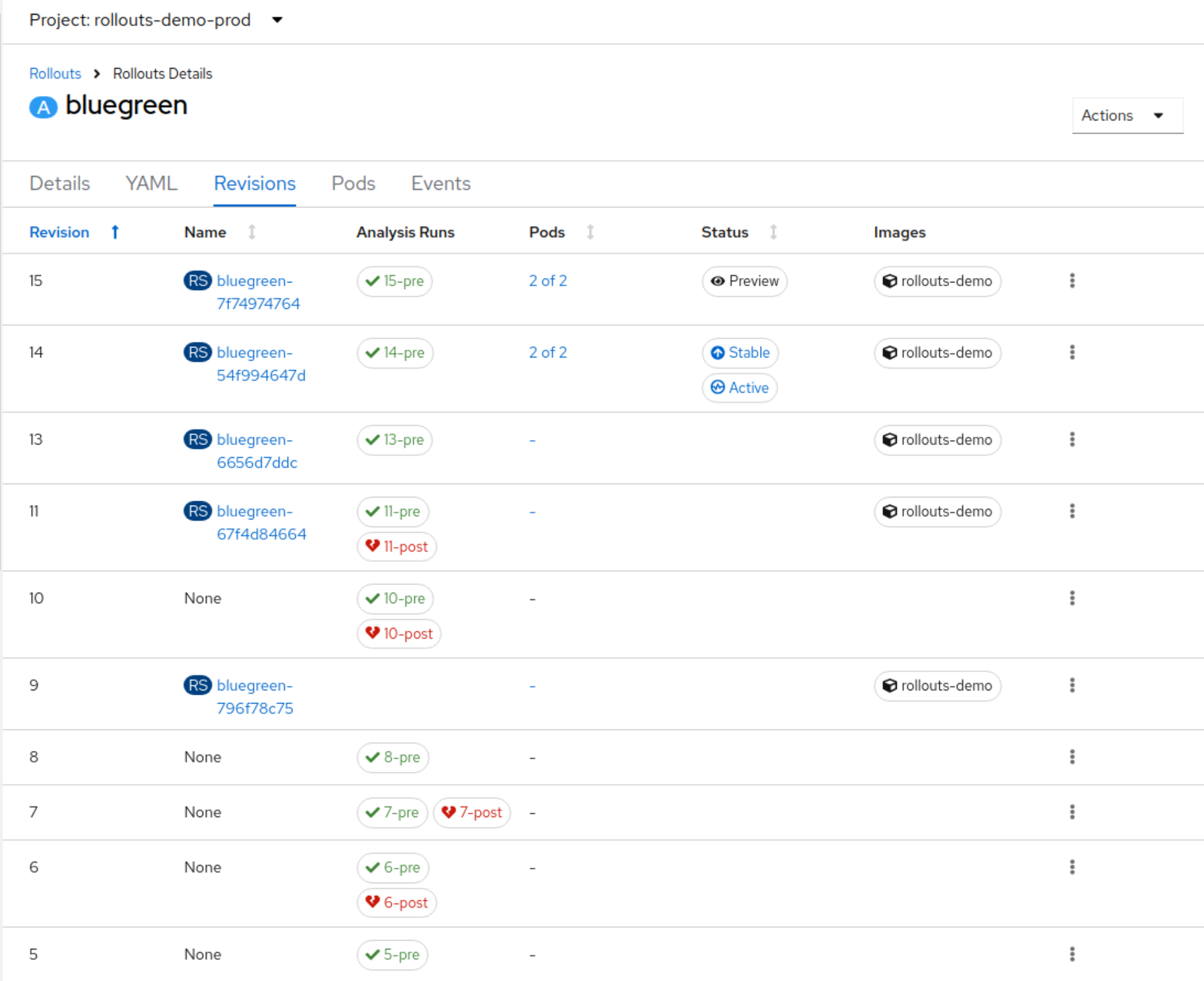
This project provides an OpenShift Console plugin to manage OpenShift GitOps (aka Argo CD and Rollouts) as well as External Secrets.
This plugin is not intended as a 1:1 replacement for the Argo CD UI, rather it enables users to accomplish ~70 percent of their tasks in the OpenShift console with ability to easily "punch-out" to the Argo CD UI if more features are required. This plugin follows the OpenShift Console's philosophy in that it interacts with resources via the Kubernetes API, it does not use Argo CD RBAC. Please review the Philosophy section for more details.
Note: This plugin is community supported and is not part of the OpenShift GitOps product nor is it supported by Red Hat. I assume no responsibility for anything that goes wrong so caveat emptor.
Here are some features of the plugin:
As mentioned previously, this plugin is not intended as a general replacement for the Argo CD UI since it operates under a different philosophy. Specifically the OpenShift Console is a Kubernetes resource driven view of the cluster and this plugin adheres to that philosophy.
If the user has Kubernetes RBAC permissions to view Application objects then it will appear in this plugin. If the user has permissions to update and patch the Application objects then they will be able to sync and refresh the application. Argo RBAC is not used at all in the plugin.
As a result this plugin is not particularly suitable for users working with Argo CD in multi-tenant deployments. This is because in a multi-tenant scenario Argo RBAC must be used to enforce separation between tenants and tenants cannot be allowed direct access to the namespace where Argo CD and the Applications are deployed. Otherwise the user will be able to view secrets they should not have access to, potentially modify Application objects to bypass Argo CD RBAC, etc.
This plugin does work well with Applications in Any Namespace which is my preferred way to handle multi-tenancy.
Outside of Applications in Any Namespace, at this time the plugin is best suited for cluster and Argo CD administrators who will typically have elevated permissions.
There are some limitations in this current implementation:
- Limited testing across the wide swath of Argo CD features, for example Helm apps have only been lightly tested.
- Limited error handling, if something does not work as expected check the browser console logs
- No general editing capabilities beyond editing the yaml
- Limited useability testing but suggestions for UI improvements definitely welcome!
The following prerequisites are required to use this plugin:
- OpenShift 4.15+
- OpenShift GitOps 1.8+ or Argo CD 2.6+ (tested with OpenShift GitOps 1.9/Argo CD 2.7)
OpenShift 4.15 made many incompatible changes in the plugin API, notably it supports React 5 and Patternfly 5. I have opted
to upgrade the plugin to the newer versions and as a result the 4.15 branch and image tag should be used to install the
plugin on 4.15. The main branch covers 4.15, the 4.14 version is not recommended as no further work is being
for that version.
| OpenShift Version | Branch | Image Tag |
|---|---|---|
| 4.14 (not supported) | 4.14-0.0.21 | 4.14 |
| 4.15 | main | 4.15, latest |
| 4.16 | 4.16 | 4.16 |
The plugin can be installed from the manifests included in the /manifests folder using kustomize, make sure
to use the correct branch for the desired version.
oc apply -k https://github.com/gnunn-gitops/gitops-admin-plugin/manifests/overlays/install
Note the install overlay includes a job with the elevated permissions needed to patch consoles.operator.openshift.io to
include this specific plugin. This enables deployment via Argo CD since everything is automated.
After running this command it may take a few minutes for the plugin to appear, check oc get co to see the
status of the console operator.
In one terminal window, run:
yarn installyarn run start
In another terminal window, run:
You will then be able to access the console with the plugin at http://localhost:9000 in a browser.
You can build the plugin as a container image using podman (or docker if you prefer) with the following command:
podman build . -t <your-image-name>
The image used by the manifests is hosted at quay.io/gnunn/gitops-admin-plugin.
Thanks to the following individuals:
- Pavel Kratochvíl whose crontab example provides a great starting point for building plugins needed to support CRDs.
- Andrew Block for Kyverno policy plugin and getting me over the Typescript/react hump
- Keith Chong for his work on the Developers perspective GitOps plugin from which I borrowed a few things.
- Thanks to the OpenShift Virtualization folks, their kubevirt-plugin repository is an invaluable reference.
- Argo CD UI where I leveraged it for A/B testing plus re-used some of the existing code there instead of re-inventing the wheel. All rights remain with original authors, code I specifically use:
- code for determining Operation State
- code for calculating URLs for git repos and paths
Note some ActionDropDown stuff taken from kubevirt console plugin here.