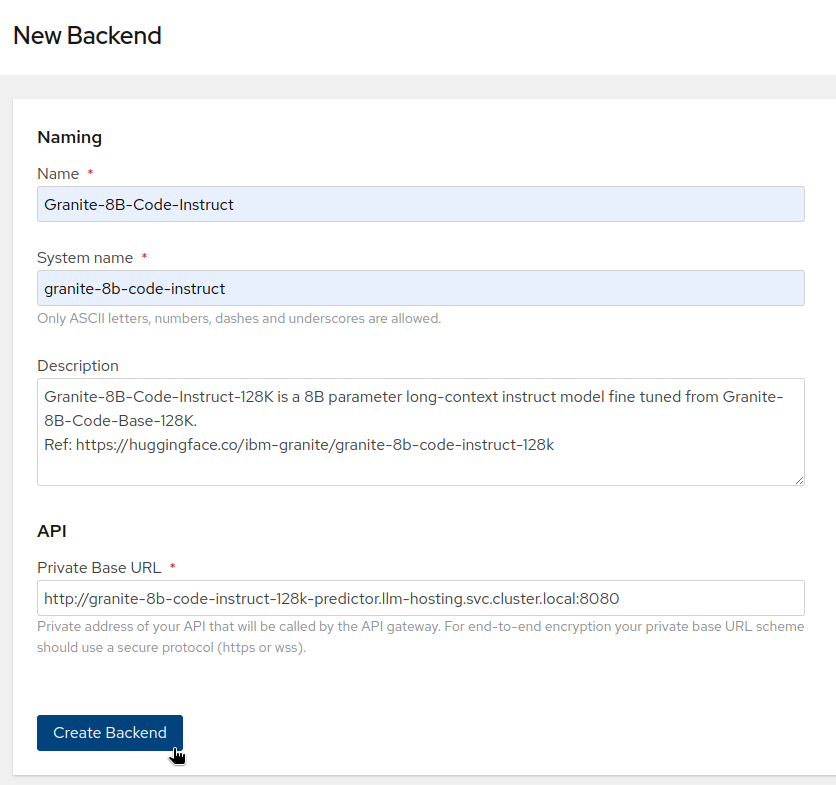
- In OpenShift, create projet
llm-hosting. - In the namespace YAML definition of the project, add the label
modelmesh-enabled: 'false' - In the project, create OBC to RGW.
- Switch to OpenShift AI dashboard and create a Data Connection
modelswith the information from the OBC.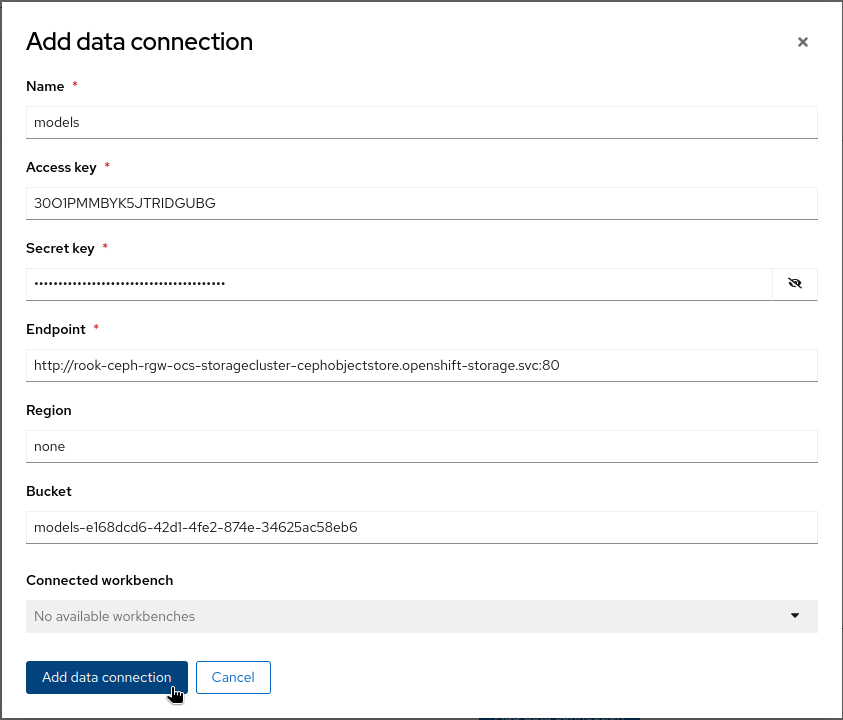
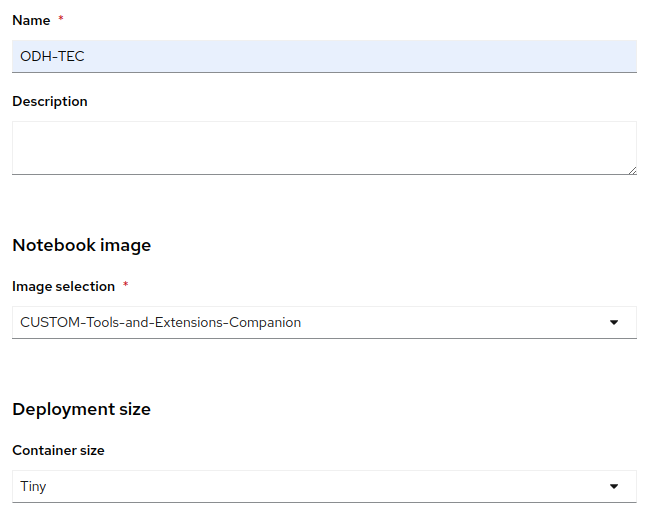
- In OpenShift AI, create and launch an ODH-TEC workbench using the data connection:
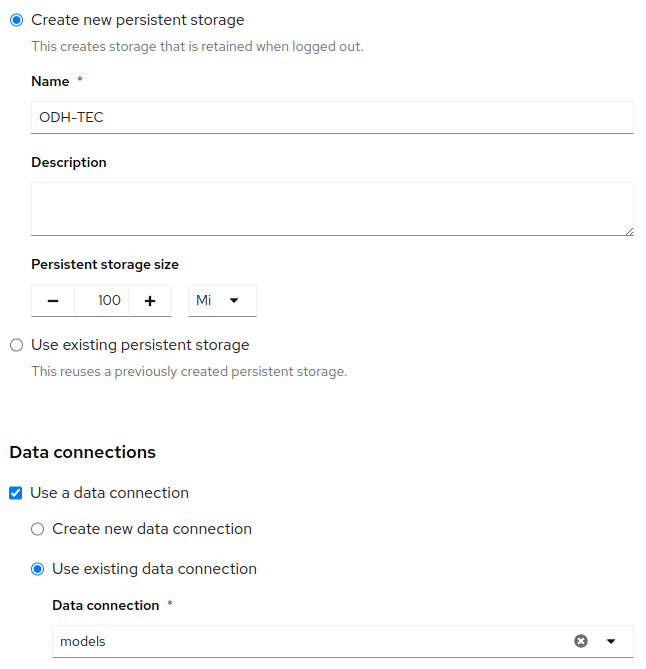
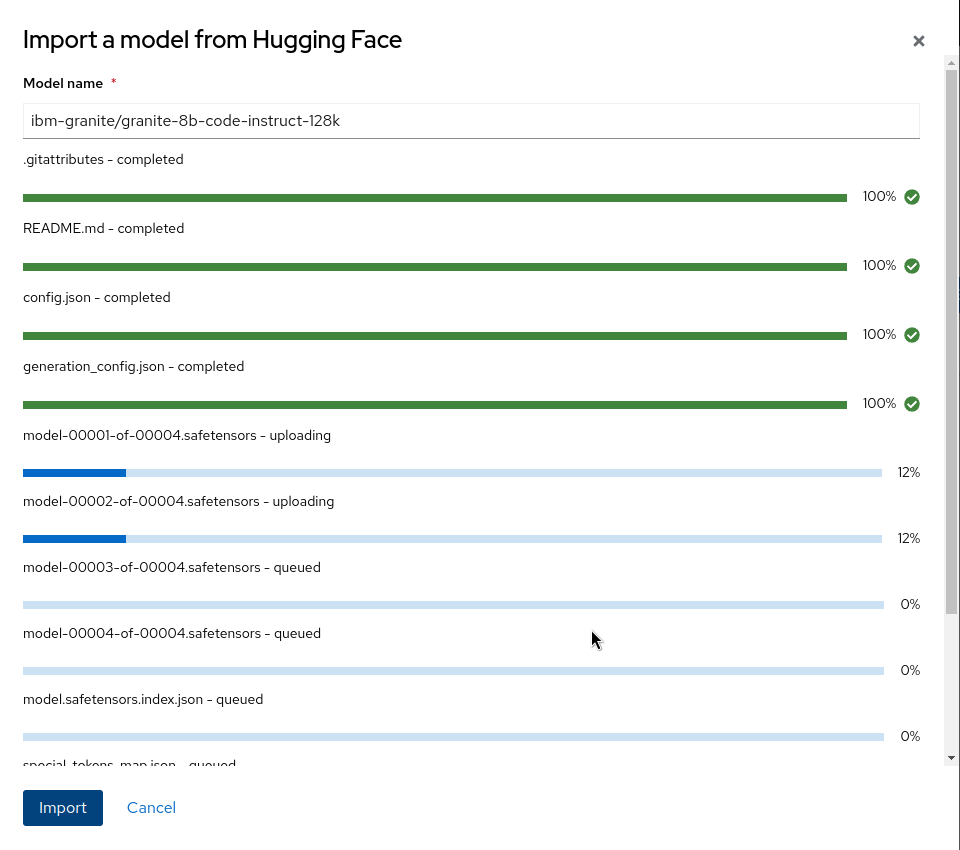
- Using ODH-TEC, import the following models from HuggingFace (don't forget to enter your HuggingFace Token in ODH-TEC Settings!):
- From the OpenShift Console, deploy the different model servers using the following RuntimeConfigurations and InferenceServers:
- Create the project
rh-sso. - Deploy the Red Hat Single Sign-On operator in the
rh-ssonamespace. - Create a Keycloak instance using keycloak.yaml.
- Create a
rhoaiKeycloakRealm using keycloakrealm-maas.yaml. - Open the Red Hat Single Sign-on console (route in the Routes section, access credentials in Secrets->
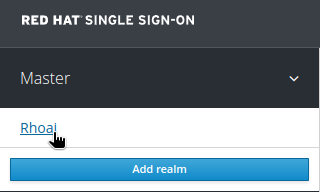
credentials-rh-sso). - Switch to the Rhoai realm:
- In the Clients section, create a new client named
3scale, of typeopenid-connect: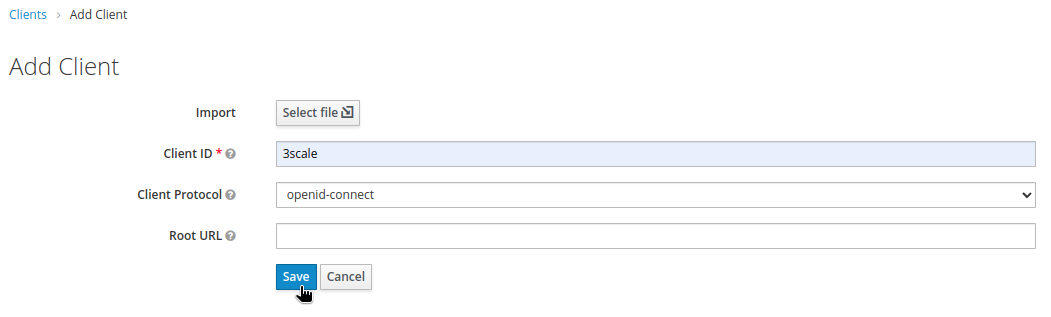
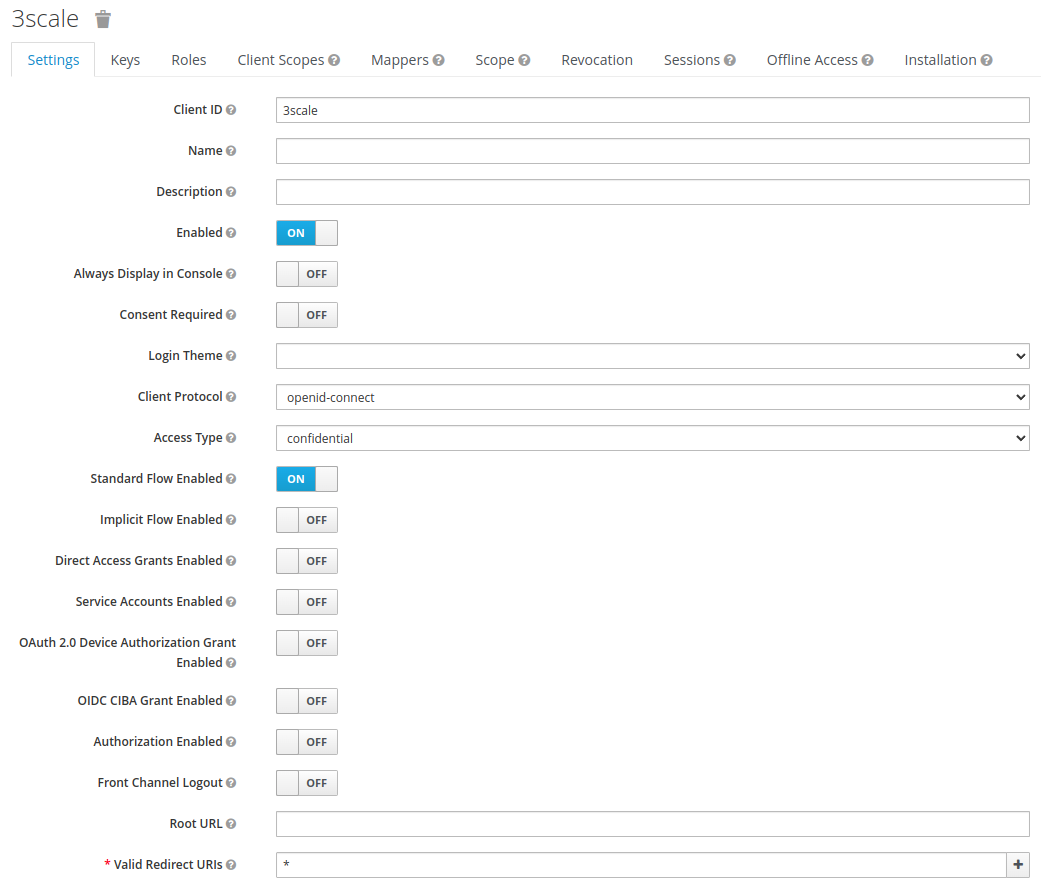
- Adjust the following:
- Access Type:
confidential - Enable only Standard Flow, leave all other toggle to off.
- For the moment, set Valid Redirect URLs to
*.
- From the Credentials section, take note of the Secret.
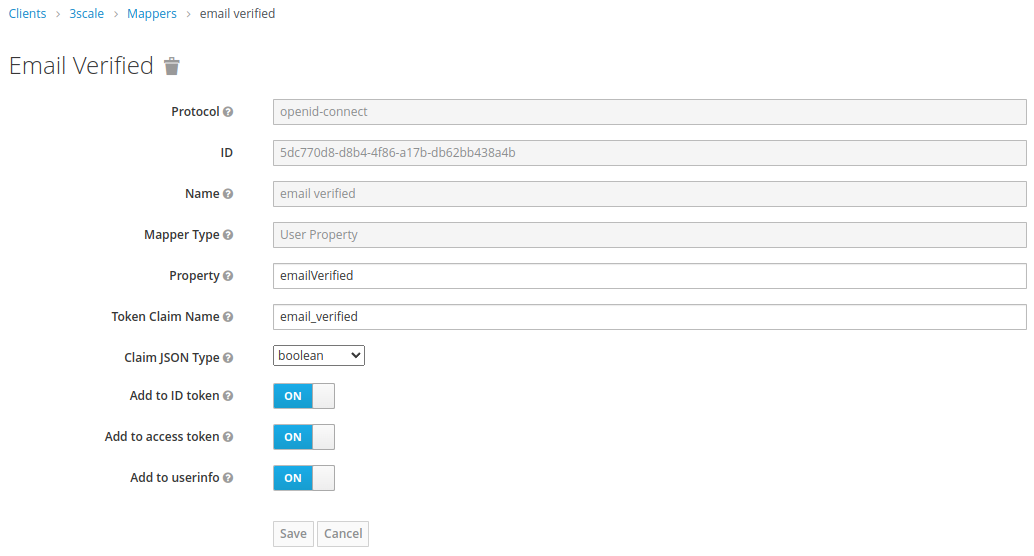
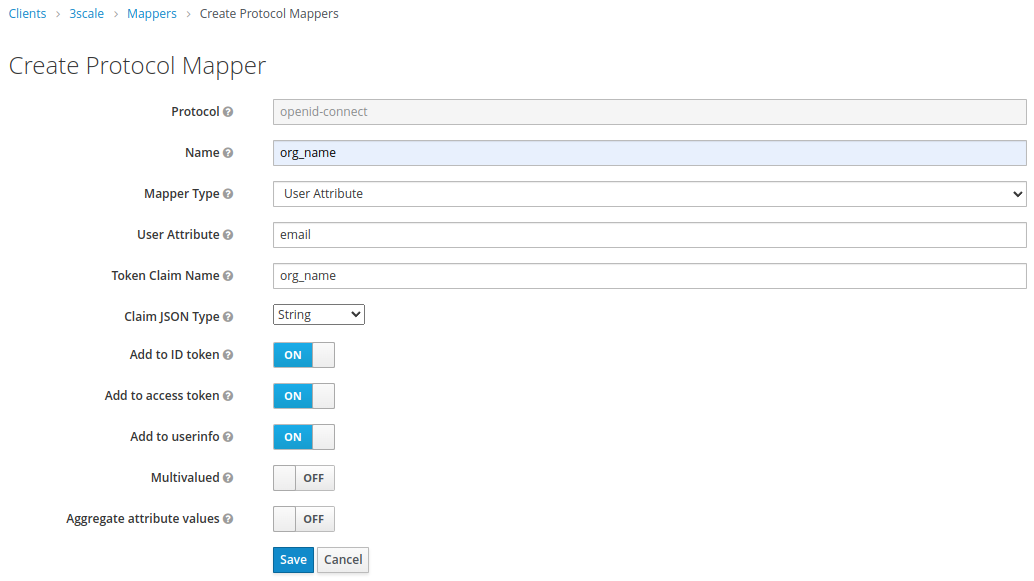
- In the Mappers sections, create two new mappers:
- In this configuration, the organization name for a user will be the same as the user email. This is to achieve full separation of the accounts. Adjust to your likings.
- Access Type:
- Create an IdentityProvider to connect your Realm to Red Hat authentication system. The important sections are
Trust Emailto enable, and setSync Modeto import.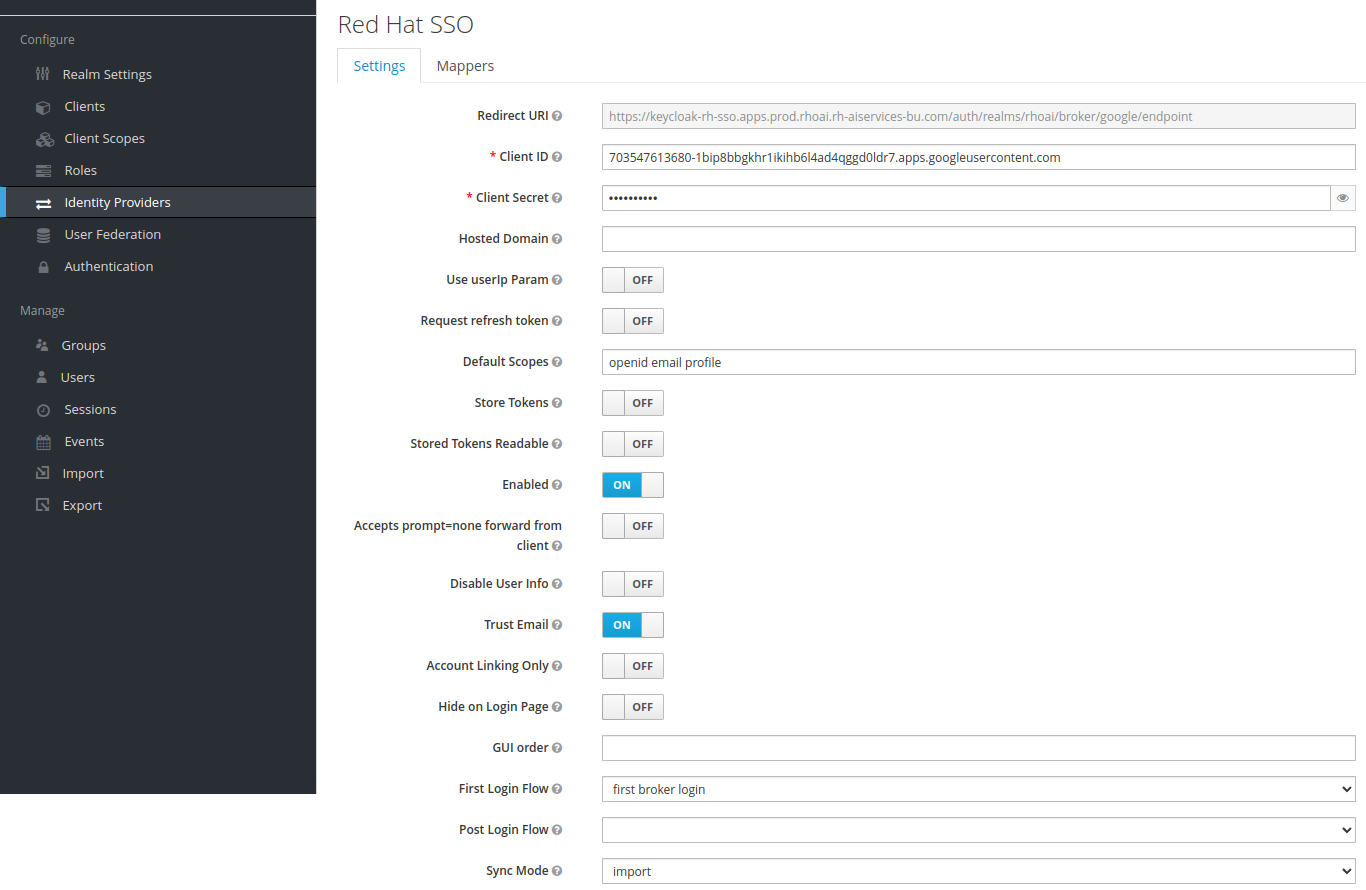
Requirements:
- OpenShift Data Foundation deployed to be able to create an RWX volume for 3Scale system storage.
Deployment:
-
Create the project
3scale. -
Open a Terminal and login to OpenShift.
-
Switch to the folder deployment/3scale/remove_bearer_policy and run the following command:
oc create secret generic cp-bearer \ -n 3scale \ --from-file=./apicast-policy.json \ --from-file=./init.lua \ --from-file=./remove-bearer.lua -
Deploy the Red Hat Integration-3scale operator in the
3scalenamespace only! -
Using the deployed operator, create an APIManager instance using deployment/3scale/apimanager.yaml.
-
Wait for all the Deployments (15) to finish.
-
Create a Custom Policy Definition instance using deployment/3scale/custom_policy_definition.yaml.
Base configuration
-
Open the 3Scale administration portal for the RHOAI provider. It will be the Route starting with
https://maas-admin-apps.... -
The credentails are stored in the Secret
system-seed(ADMIN_USERandADMIN_PASSWORD). -
You will be greated by the Wizard that you can directly close:
 .
. -
In the Account Settings sections (top menu):
-
Let's start by doing some cleanup:
Backends and Products
- We will start by adding the different
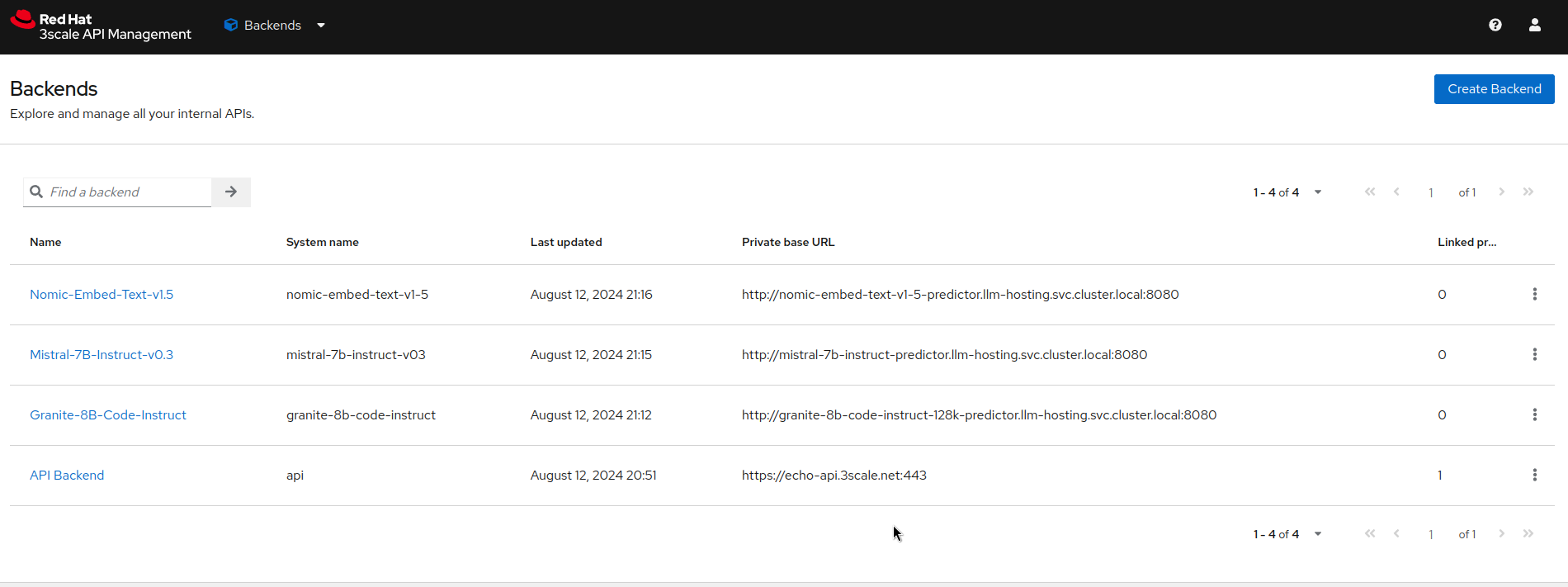
Backendsto our models: - We can now create the
Products. There will be one for each Backend.
- For each product, apply the following configurations:
- In
Integration->Settings, change theAuth user keyfield content toAuthorizationand theCredentials locationfield toAs HTTP Headers(click onUpdate productat the bottom to save):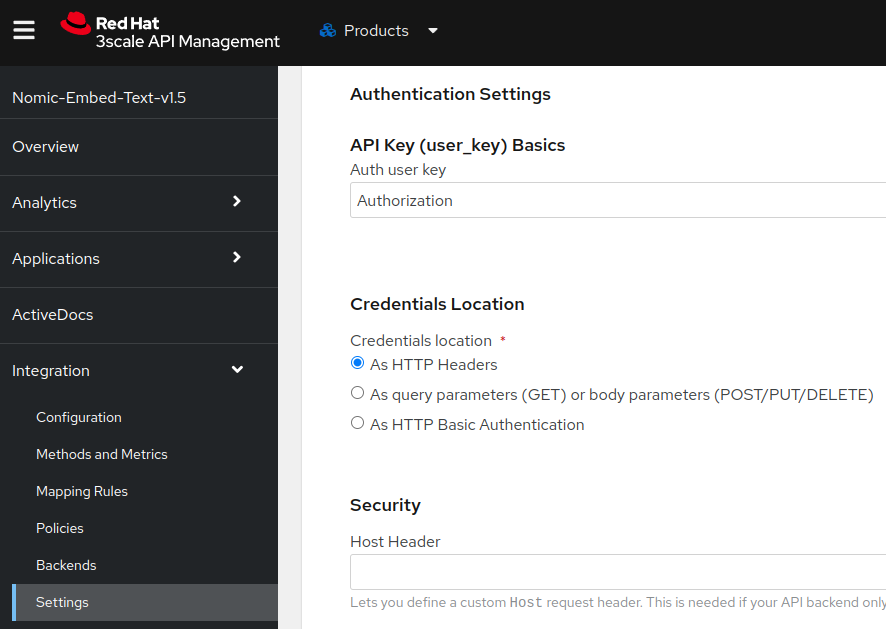
- Link the corresponding Backend
- Add the Policies in this order:
- CORS Request Handling:
- ALLOW_HEADERS:
Authorization,Content-type,Accept. - allow_origine: *
- allow_credentials: checked
- ALLOW_HEADERS:
- Remove Bearer from Authorization Policy
- 3scale APIcast
- CORS Request Handling:
- Add the Methods and the corresponding Mapping Rules: create one pair for each API method/path.
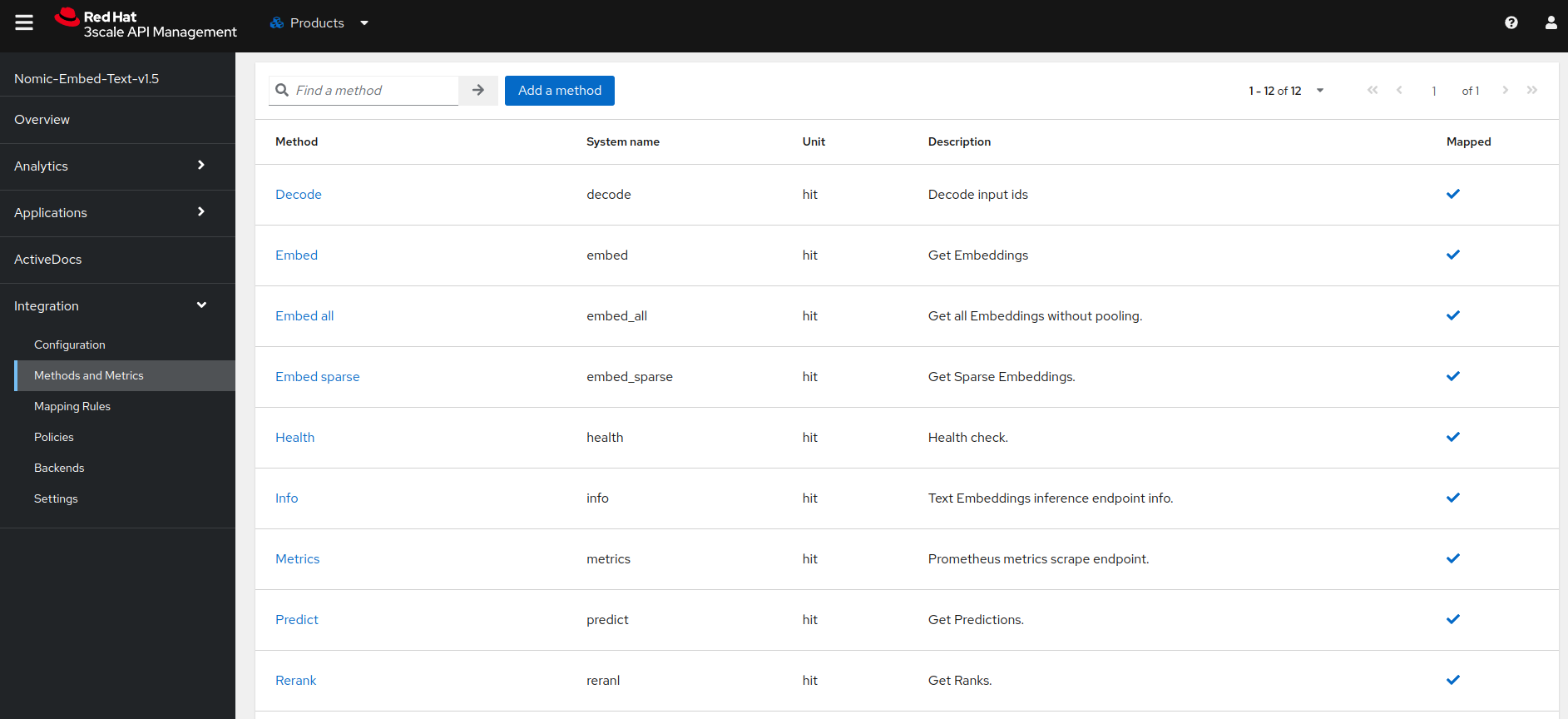
- From the Integration->Configuration menu, promote the configuration to staging then production.
- Along the way you can cleanup the unwanted default Products and Backends.
- In
Plans
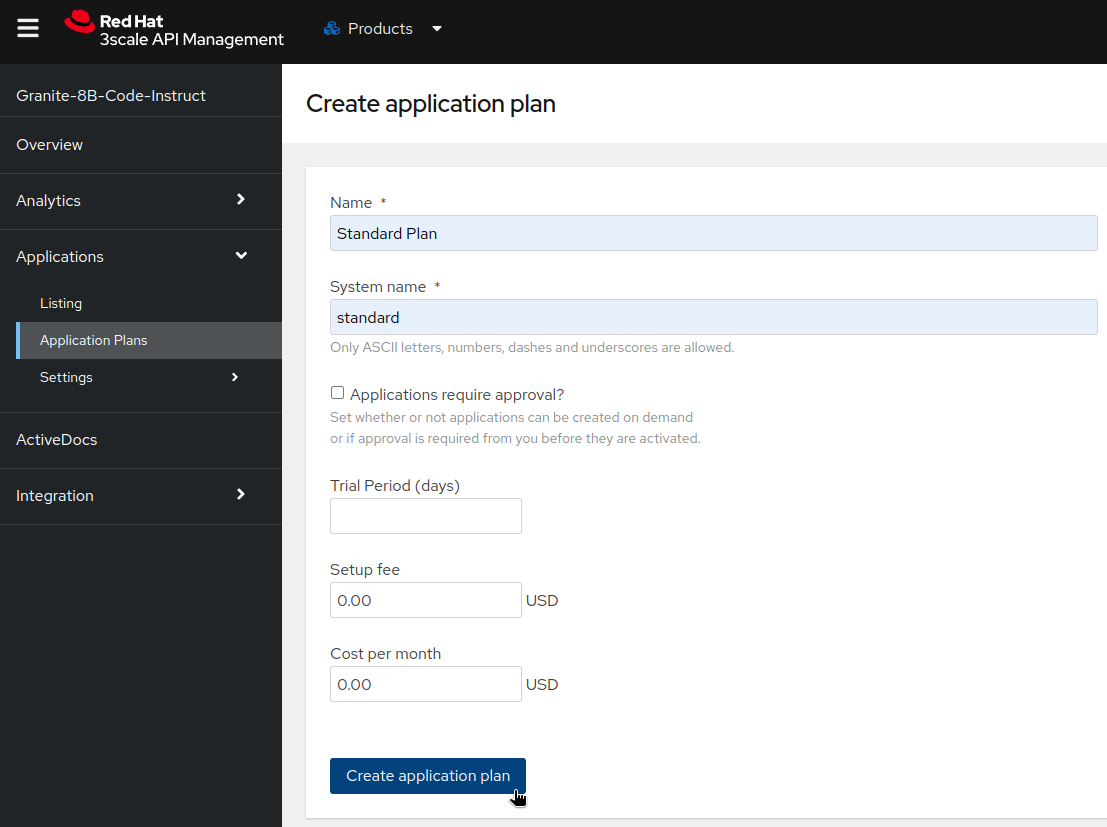
- For each Product, from the Applications->Application Plans menu, create a new Application Plan.
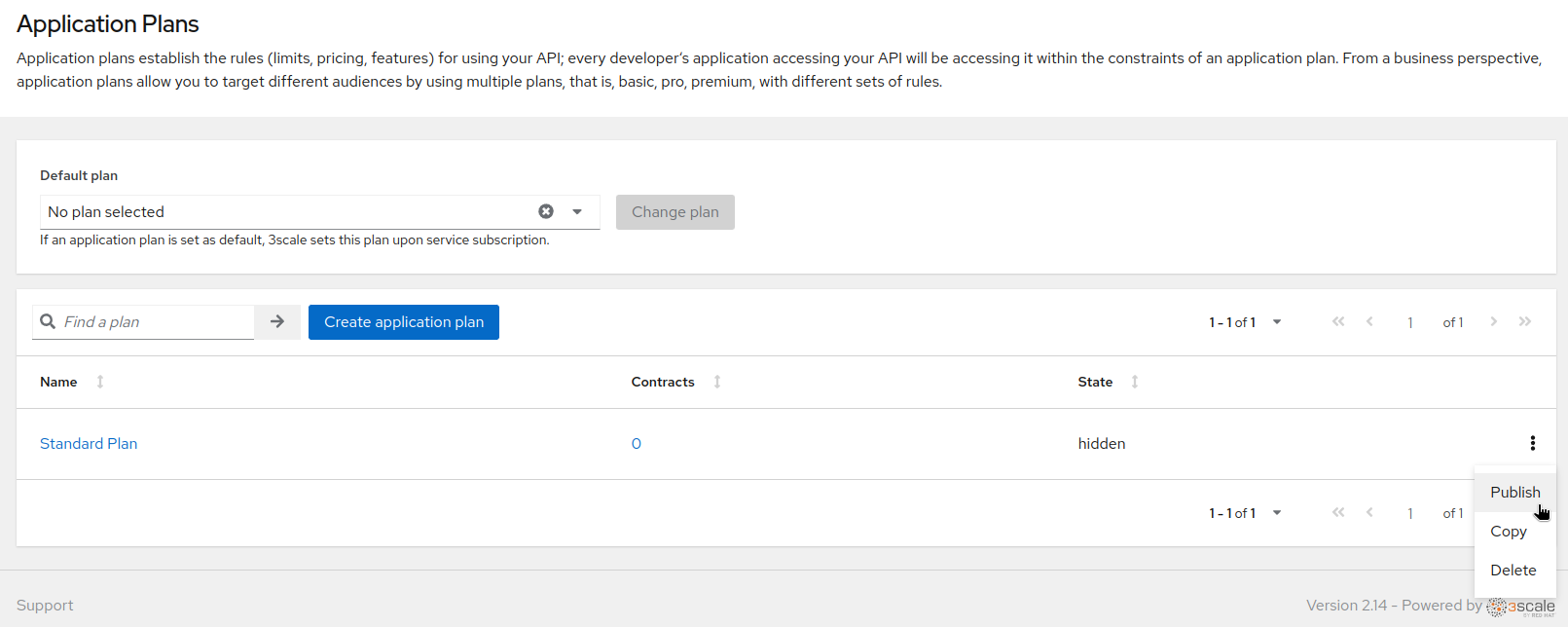
- Once created, leave the Default plan to "No plan selected" so that users can choose their services for their applications, and publish it:
- In Applications->Settings->Usage Rules, set the Default Plan to
Default. This will allow the users to see the different available Products.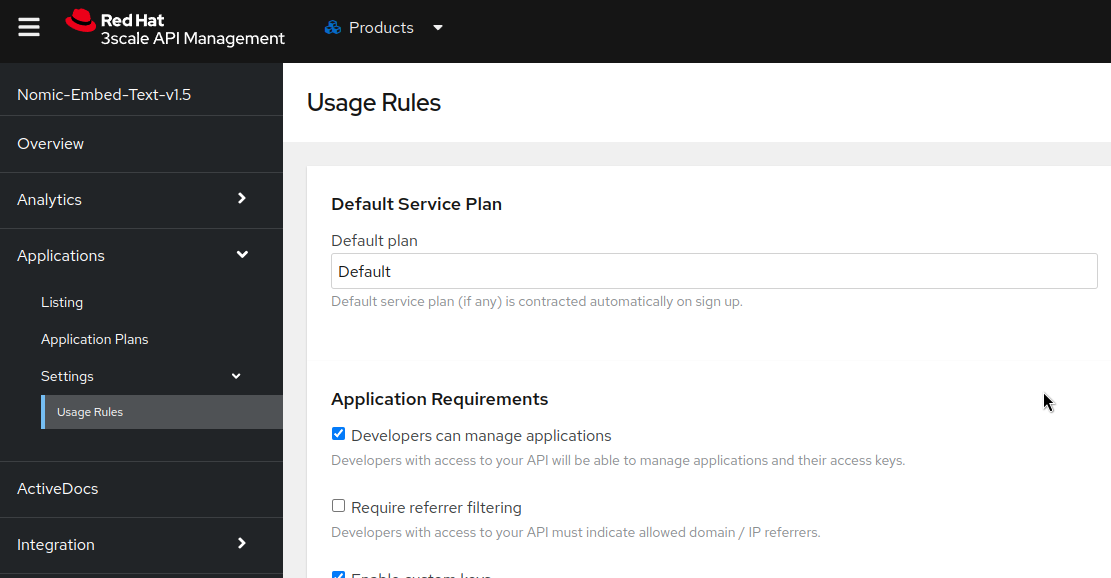
Portal configuration
- Switch to the Audience section from the top menu.
- In Developer Portal->Settings->Domains and Access, remove the Developer Portal Access Code.
- In Developer Portal->Settings->SSO Integrations, create a new SSO Integration: of type Red Hat Single Sign On.
- Client:
3scale - Client secret: ************
- Realm:
https://keycloak-rh-sso.apps.prod.rhoai.rh-aiservices-bu.com/auth/realms/maas(adjust to your cluster domain name). Publishedticked.- Once created, edit the RH-SSO to tick the checkbox
Always approve accounts...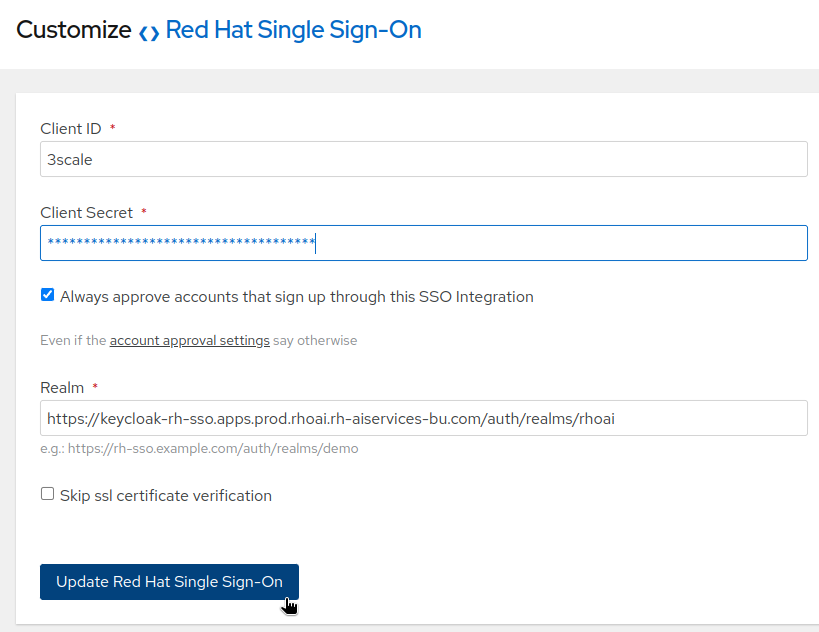
- You can now test the authentication flow.
- Client:
Portal content
- Go to Developer Portal->Content.
- From the deployment/3scale/portal folder, apply all the modifications to the different pages and Publish them.
- The content of this folder is arranged following the same organization of the site.
- New Pages may have to be created with the type depending of the type of content (html, javascript, css), some others have only to be modified.