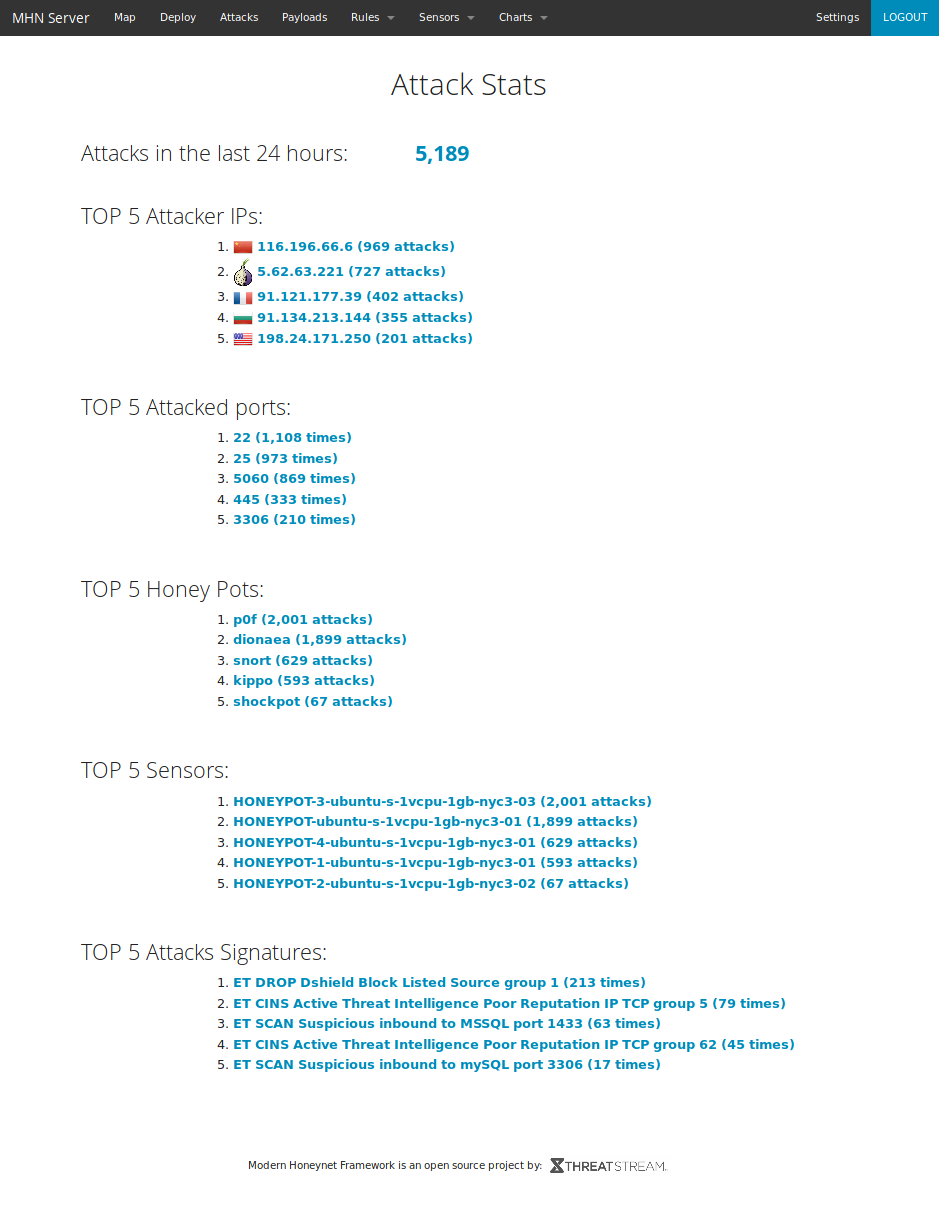
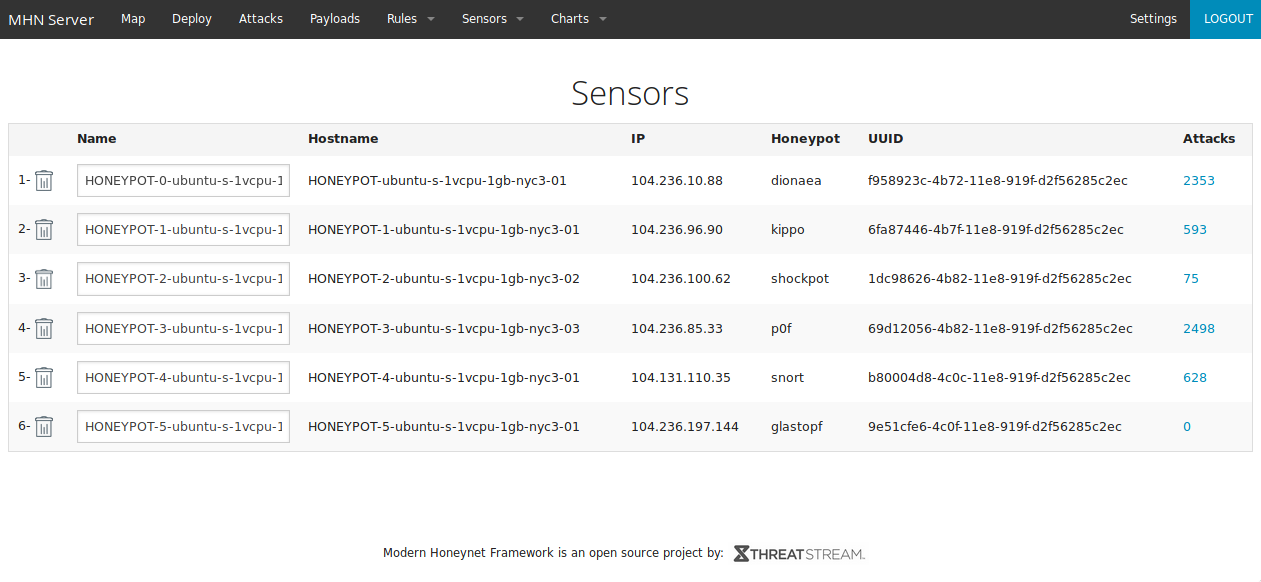
I implemented a Modern Honey Network with 6 different honeypots on Ubuntu 14.04 x64 Digitalocean droplets. The honeypots started receiving attacks immediately. After only 48 hours, my honey network had received over 6,000 attacks.
Here is the complete data collection from the honeypots (for your casual reading) : session.json
Here is a list of the honeypots I used on my honey network:
- Honeypot 0 - Dionaea
- Honeypot 1 - Kippo
- Honeypot 2 - Shockpot Sinkhole
- Honeypot 3 - p0f
- Honeypot 4 - Snort
- Honeypot 5 - Glastopf
Most honeypots were straight forward during setup, and seemed to get attacked almost immediately. The only exception to that was my last honeypot which was running Glastopf. I tried to troubleshoot it to make sure it was running correctly and it seemed to be fine. I ran sqlmap against multiple injection points but no attacks registered on the MHN Admin server.
Here I've listed the function of the most frequently attacked ports:
| Attacked Ports | Common Use |
|---|---|
| 22 | SSH |
| 5060 | VoIP |
| 25 | SMTP |
| 445 | Windows Server |
| 3306 | MySQL |
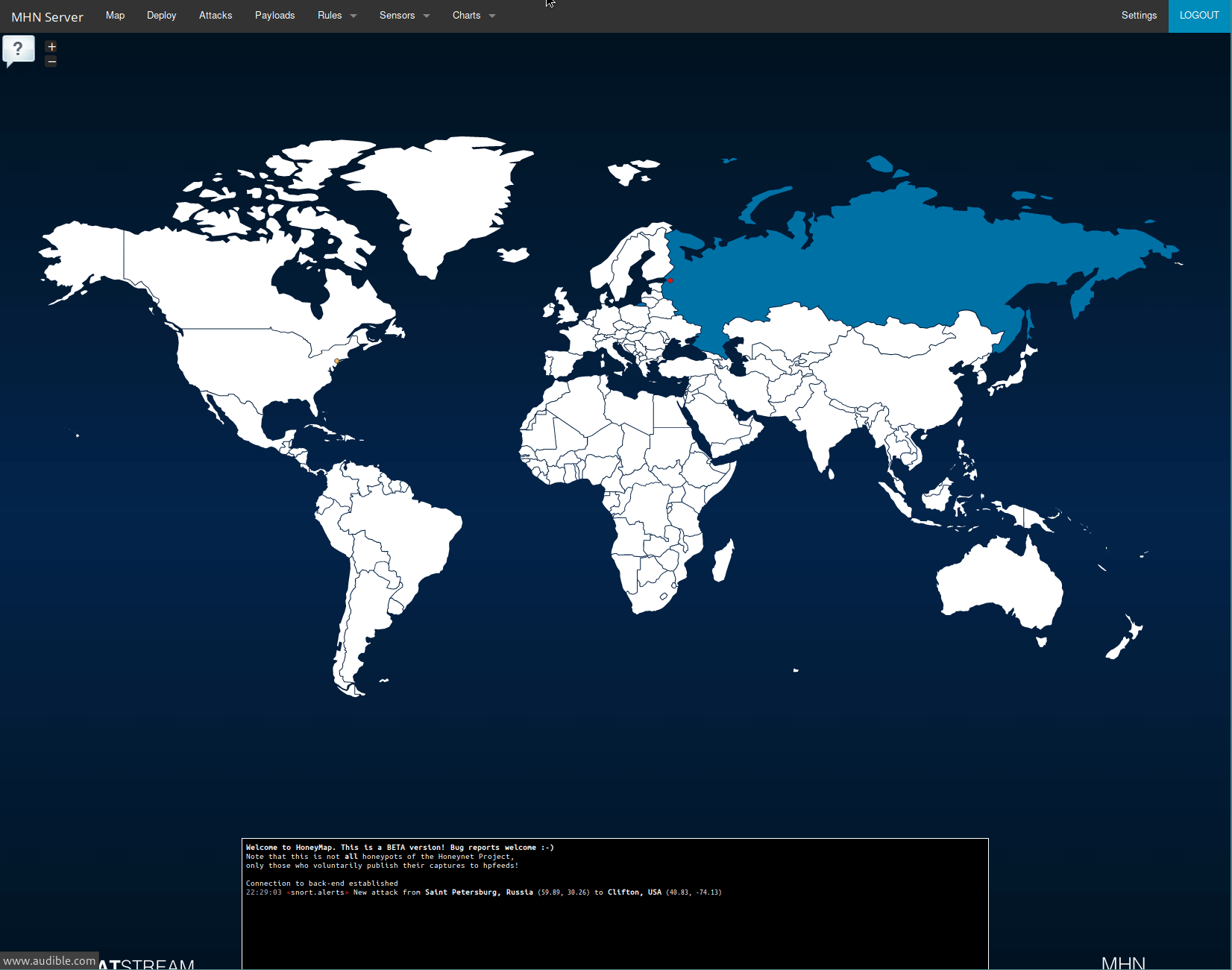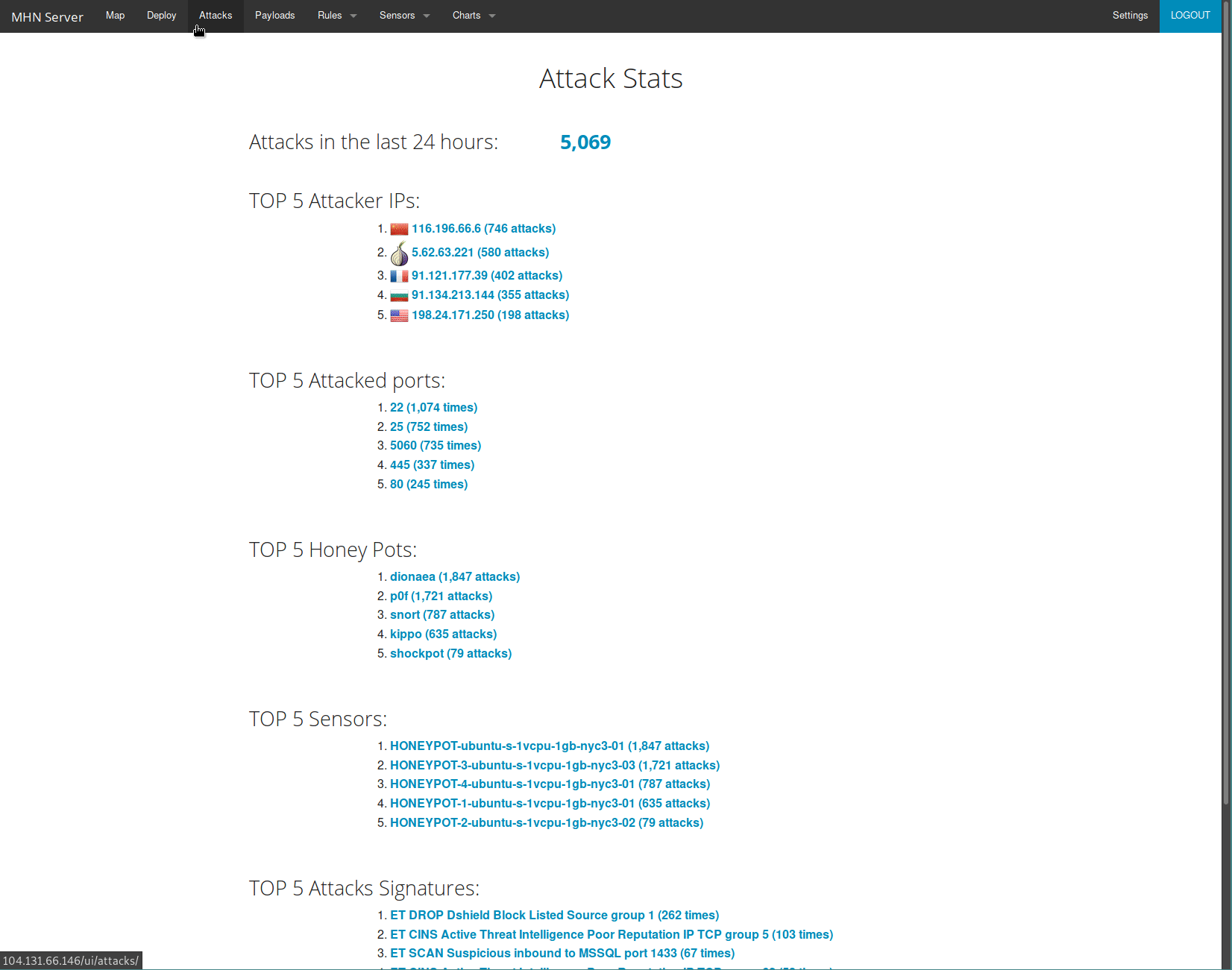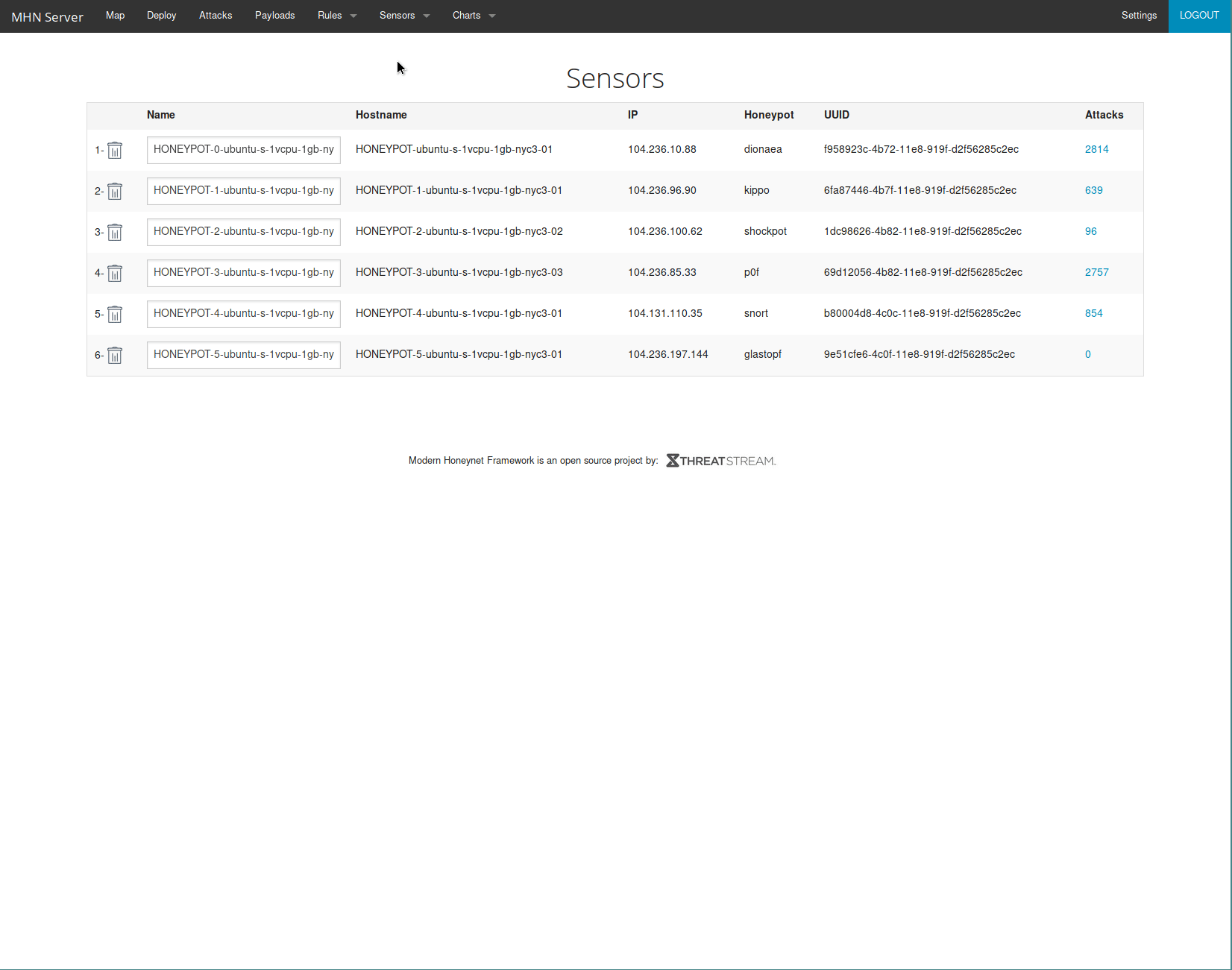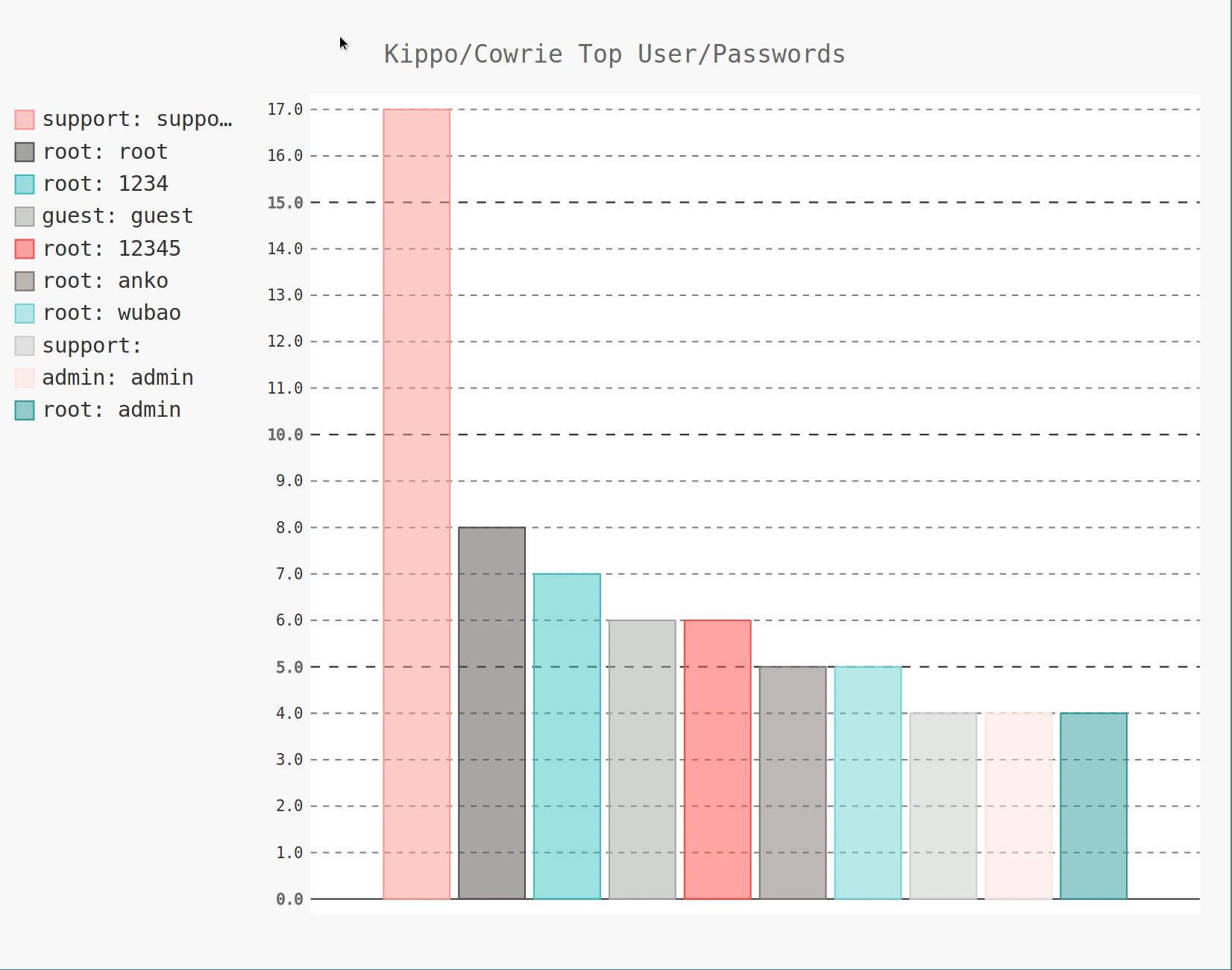
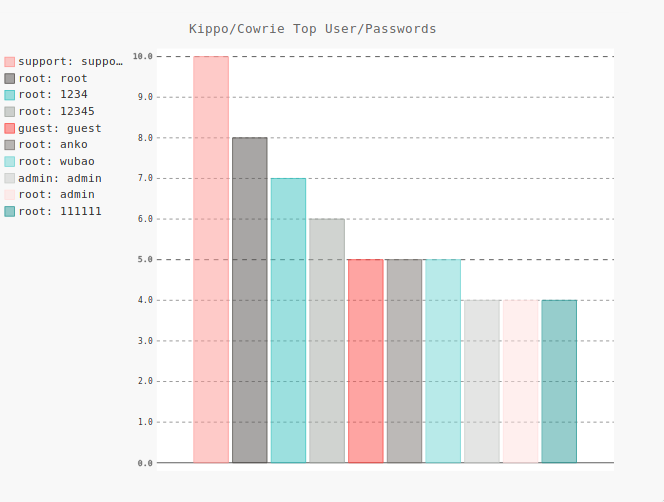
It appears that many of these bots are really only interested in the lowest hanging fruit, given the #1 SSH username AND password attempt was "support".
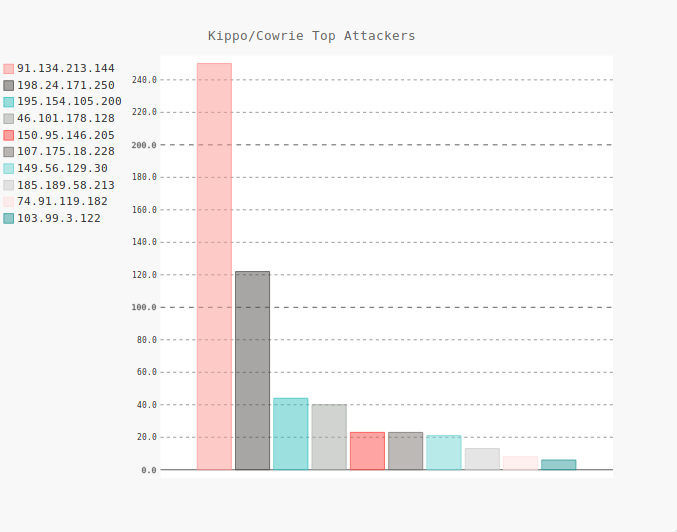
I was curious as to which countries were responsible for the attempts at brute-forcing ssh on the Kippo honeypot...
| Attacker IPs | Country |
|---|---|
| 91.134.213.144 | Bulgaria |
| 198.24.171.250 | USA |
| 195.154.105.200 | France |
| 46.101.178.128 | Germany |
| 150.95.146.205 | Japan |