- Summary
- Installation Instructions
- Usage
- Running reconFTW
- Sample Video
- Features
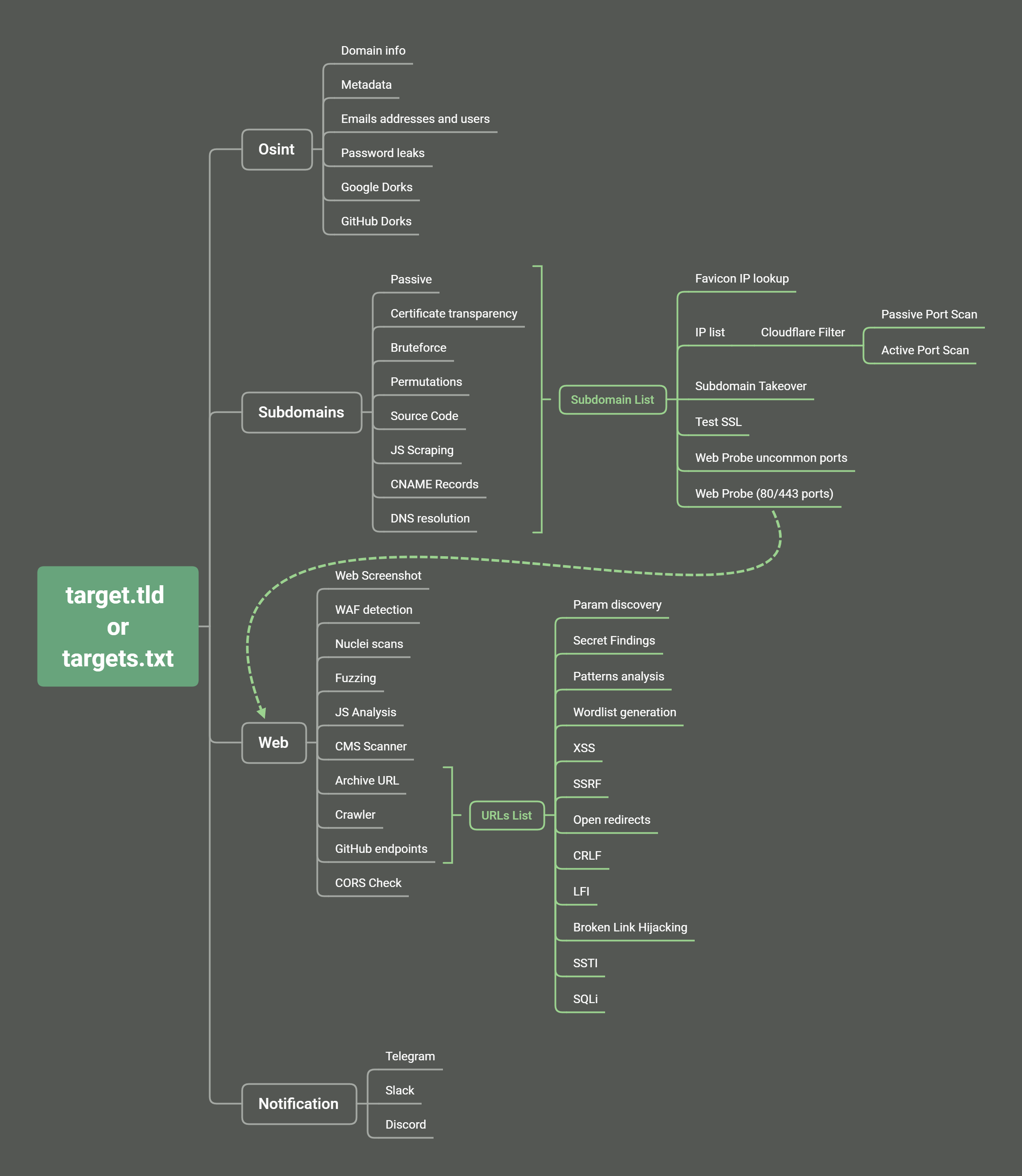
- Mindmap/Workflow
- Contribute
- Thanks
reconFTW is a tool designed to perform automated recon on a target domain by running the best set of tools to perform enumeration and finding out vulnerabilities.
- Installation Guide 📖
- Requires Golang > 1.14 installed and paths correctly set ($GOPATH, $GOROOT)
▶ git clone https://github.com/six2dez/reconftw
▶ cd reconftw
▶ chmod +x *.sh
▶ ./install.sh
▶ ./reconftw.sh -d target.com -a- Through
reconftw.configfile the whole execution of the tool can be controlled. - Hunters can set various scanning modes, execution preferences, tools config files, APIs/TOKENS, personalized wordlists
Click here to view default config file
#################################################################
# reconFTW config file #
#################################################################
# TERM COLOURS
bred='\033[1;31m'
bblue='\033[1;34m'
bgreen='\033[1;32m'
yellow='\033[0;33m'
red='\033[0;31m'
blue='\033[0;34m'
green='\033[0;32m'
reset='\033[0m'
# General values
tools=~/Tools
NPROC=$(nproc || echo -n 1)
output=${dir}/Recon/${domain}
# Tools config files
#NOTIFY_CONFIG=~/.config/notify/notify.conf # No need to define
#SUBFINDER_CONFIG=~/.config/subfinder/config.yaml # No need to define
AMASS_CONFIG=~/.config/amass/config.ini
GITHUB_TOKENS=${tools}/.github_tokens
# APIs/TOKENS
SHODAN_API_KEY=XXXXXXXXXXXXX
XSS_SERVER=reconftw.xss.ht
COLLAB_SERVER=webhook.site/e3d6156b
findomain_virustotal_token=XXXXXXXXXXXXXXXXX
findomain_spyse_token=XXXXXXXXXXXXXXXXX
findomain_securitytrails_token=XXXXXXXXXXXXXXXXX
findomain_fb_token=XXXXXXXXXXXXXXXXX
# File descriptors
DEBUG_STD="&>/dev/null"
DEBUG_ERROR="2>/dev/null"
# Steps
DORKS=true
SUBCRT=true
SUBBRUTE=true
SUBSCRAPING=true
SUBPERMUTE=true
SUBTAKEOVER=true
WEBPROBEFULL=true
WEBSCREENSHOT=true
PORTSCANNER=true
PORTSCAN_PASSIVE=true
PORTSCAN_ACTIVE=true
NUCLEICHECK=true
URL_GF=true
JSCHECKS=true
PARAMS=true
XSS=true
GITHUB=true
FAVICON=true
FUZZ=true
CMS_SCANNER=true
CORS=true
TEST_SSL=true
OPEN_REDIRECT=true
SSRF_CHECKS=true
CRLF_CHECKS=true
LFI=true
SSTI=true
SQLI=true
BROKENLINKS=true
WORDLIST=true
# Extra features
NOTIFICATION=false
DEEP=false
FULLSCOPE=false
DIFF=false
REMOVETMP=false
## HTTP options
COOKIE=""
HEADER="User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:72.0) Gecko/20100101 Firefox/72.0"
# lists
fuzz_wordlist=${tools}/fuzz_wordlist.txt
lfi_wordlist=${tools}/lfi_wordlist.txt
subs_wordlist=${tools}/subdomains.txt
resolvers=${tools}/resolvers.txtTARGET OPTIONS
| Flag | Description |
|---|---|
| -d | Target domain (example.com) |
| -m | Multiple domain target (companyName) |
| -l | Target list (one per line) |
| -x | Exclude subdomains list (Out Of Scope) |
MODE OPTIONS
| Flag | Description |
|---|---|
| -r | Recon - Full recon process (only recon without attacks) |
| -s | Subdomains - Search subdomains, check tko and web probe |
| -p | Passive - Performs only passive steps |
| -a | All - Perform all checks and exploitations |
| -w | Web - Just web checks from list provided |
| -v | Verbose - Prints everything including errors, for debug purposes |
| -h | Help - Show this help |
GENERAL OPTIONS
| Flag | Description |
|---|---|
| --deep | Deep scan (Enable some slow options for deeper scan) |
| --fs | Full scope (Enable the widest scope * .domain. * options) |
| -o | Output directory |
To perform a full recon on single target (may take a significant time)
▶ ./reconftw.sh -d example.com -rTo perfrom a full recon on a list of targets
▶ ./reconftw.sh -l sites.txt -r -o /output/directory/Perform all steps (recon + attacks)
▶ ./reconftw.sh -d example.com -aPerform full recon with more intense tasks (VPS intended)
▶ ./reconftw.sh -d example.com -r --deep -o /output/directory/Perform a wide scope recon on a target (may include false positives)
▶ ./reconftw.sh -d example.com -r --fs -o /output/directory/Perform recon in a multi domain target
▶ ./reconftw.sh -m company -l domainsList.txtShow help section
▶ ./reconftw.sh -h- Domain information parser (domainbigdata)
- Emails addresses and users (theHarvester)
- Password leaks (pwndb and H8mail)
- Metadata finder (MetaFinder)
- Google Dorks (degoogle_hunter)
- Github Dorks (GitDorker)
- Multiple subdomain enumeration techniques (passive, bruteforce, permutations and scraping)
- Passive (subfinder, assetfinder, amass, findomain, crobat, waybackurls)
- Certificate transparency (crtfinder, tls.bufferover and dns.bufferover))
- Bruteforce (shuffledns)
- Permutations (dnsgen)
- Source Code Scraping (gospider)
- CNAME Records (dnsx)
- Nuclei Sub TKO templates (nuclei)
- Web Prober (httpx)
- Web screenshot (webscreenshot)
- Template scanner (nuclei)
- IP and subdomains WAF checker (cf-check and wafw00f)
- Port Scanner (Active with nmap and passive with shodan-cli)
- Url extraction (waybackurls, gau, gospider, github-endpoints)
- Pattern Search (gf and gf-patterns)
- Param discovery (paramspider and arjun)
- XSS (XSStrike)
- Open redirect (Openredirex)
- SSRF (headers asyncio_ssrf.py and param values with ffuf)
- CRLF (crlfuzz)
- Favicon Real IP (fav-up)
- Javascript analysis (LinkFinder, scripts from JSFScan)
- Fuzzing (ffuf)
- Cors (Corsy)
- LFI Checks (manual/ffuf)
- SQLi Check (SQLMap)
- SSTI (manual/ffuf)
- CMS Scanner (CMSeeK)
- SSL tests (testssl)
- Multithread in some steps (Interlace)
- Broken Links Checker (manual/wget spider)
- Docker support
- Custom output folder
- Polished installer compatible with most distros
- Diff support for continuous running (cron mode)
- Support for targets with multiple domains
- Update tools script
- RaspberryPi/ARM support
- 5 modes (recon, passive, subdomains, web and all)
- Out of Scope Support
- Notification support for Slack, Discord and Telegram (notify)
If you want to contribute to this project you can do it in multiple ways:
- Submitting an issue because you have found a bug or you have any suggestion or request.
- Making a Pull Request from dev branch because you want to improve the code or add something to the script.
For their great feedback, support, help or for nothing special but well deserved: