Just testing something with AWS Trusted Advisor
These access tokens won't work.
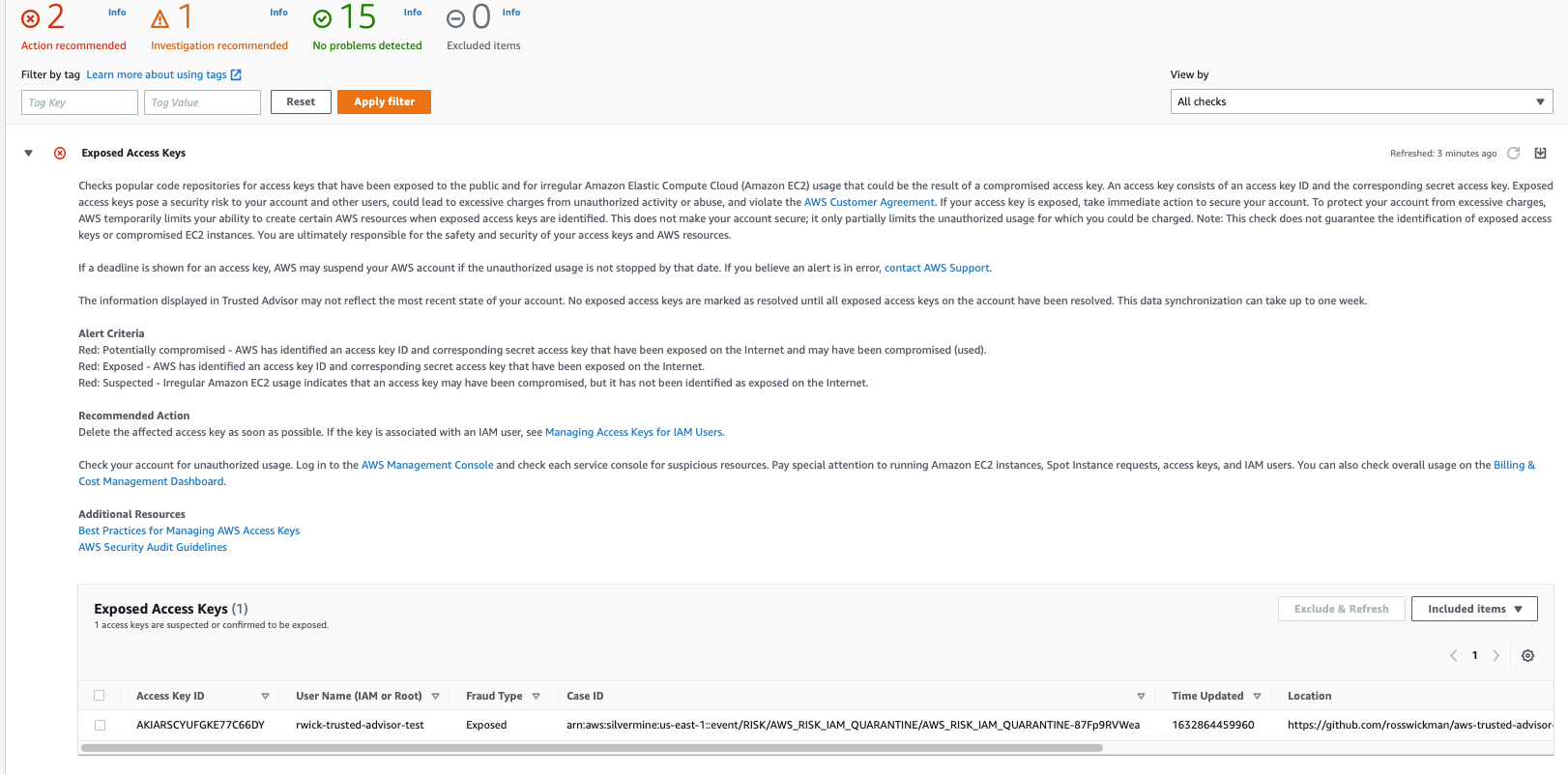
Just seeing if I can get alarms to trigger for Exposed Access Keys Trusted Advisor Check
Use this:
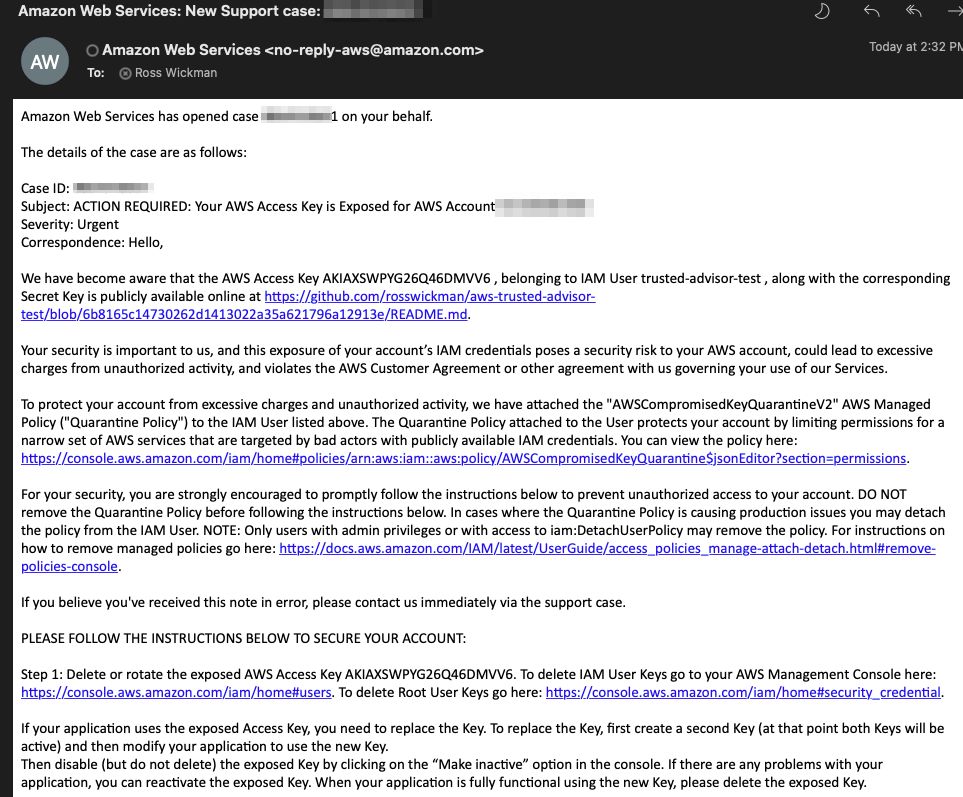
Access key ID - AKIAXSWPYG26Q46DMVV6
With this:
Secret access key - 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
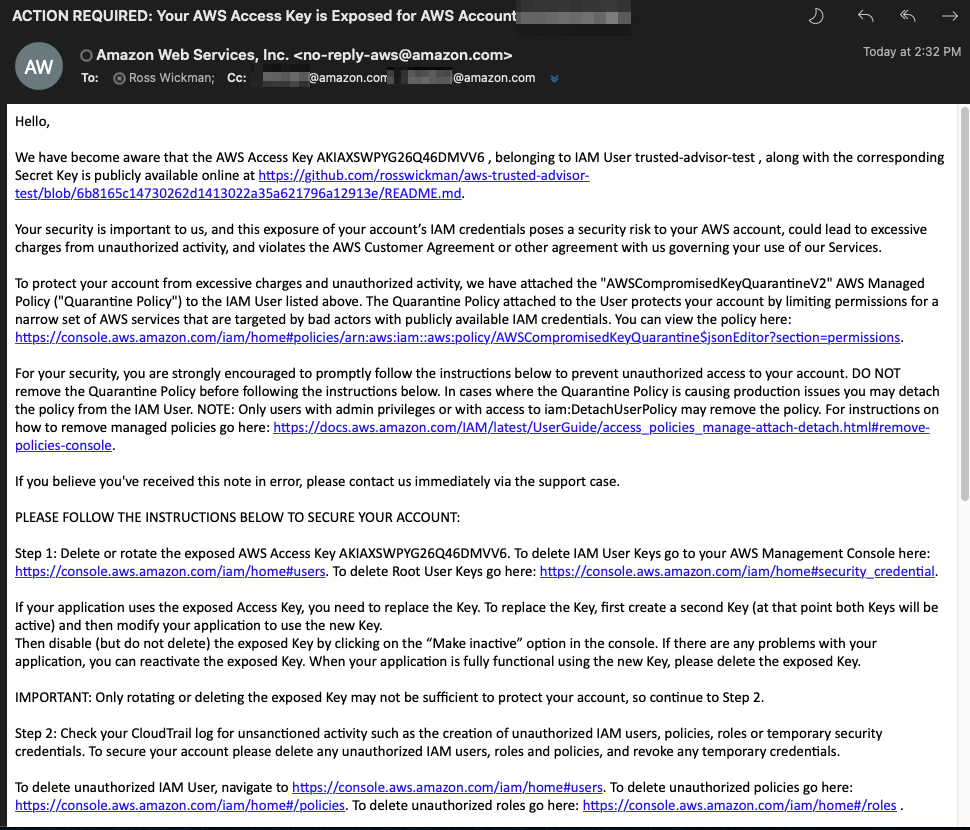
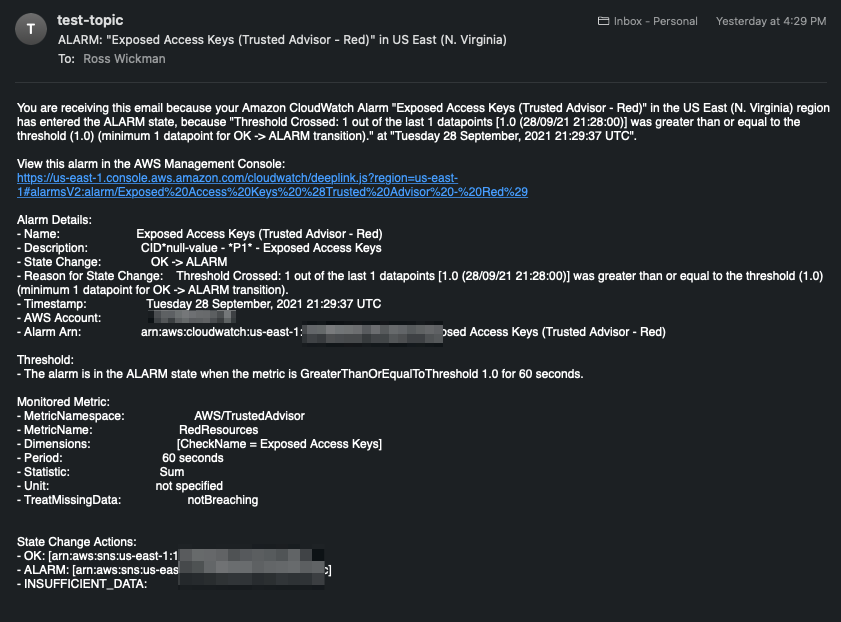
Received two emails from AWS in less than 5 Minutes (14:32CDT) of the README.md in this project being commited (14:27CDT).
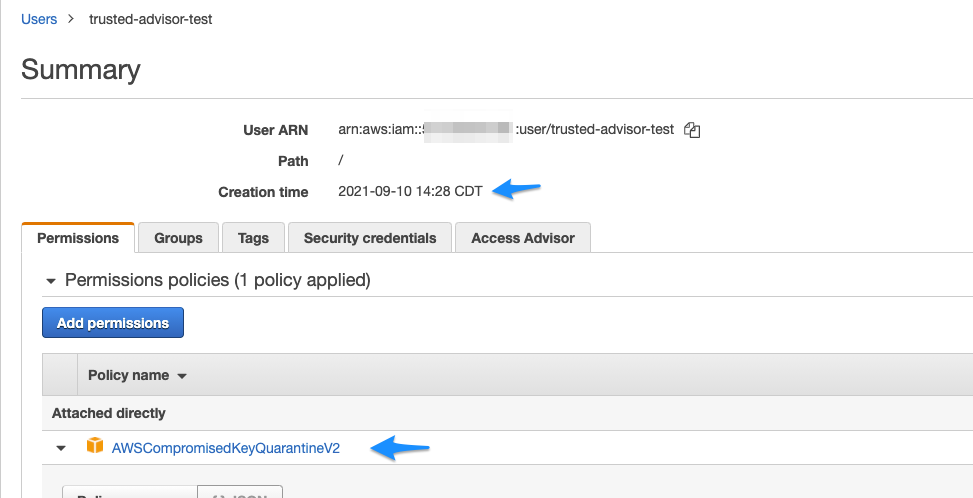
Update 1 - Later noticed that my user had applied to it an AWS Managed Policy AWSCompromisedKeyQuarantineV2 which had the attached deny permissions in the AttahcedPolicy.json
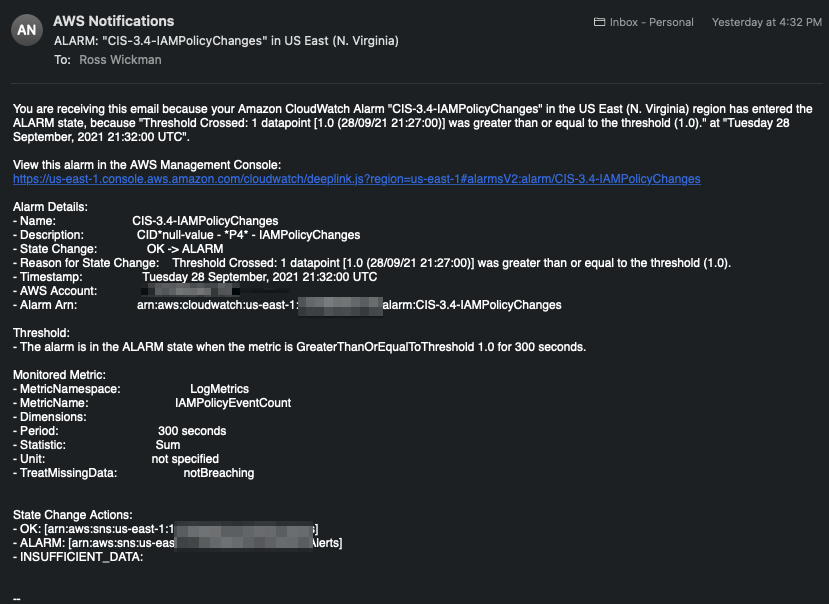
In order to send notifications of Exposed Access Keys to more than one individual or the account root email in question you can create CloudWatch Alarms to trigger desired actions.
I've created a template ta-alarms.template.yml for very basic setup that requires and SNS Topic with some subscription.
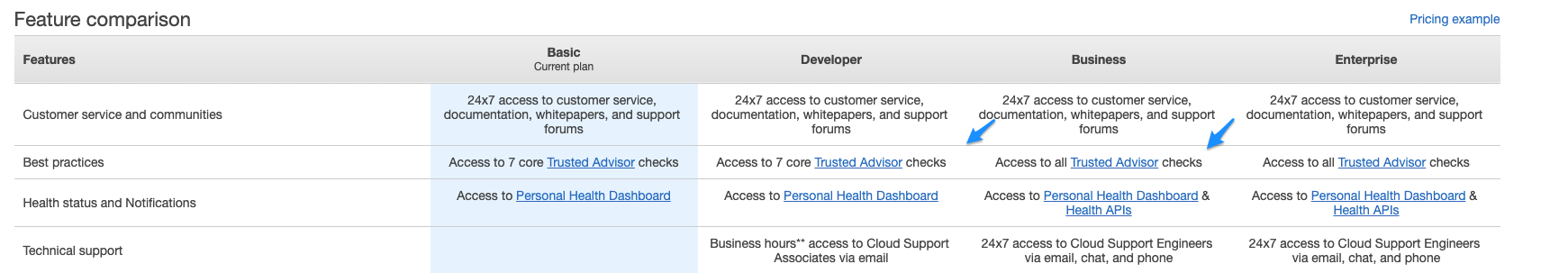
Important This level of
Trusted Advisorcheck requires your account be on the Business Support Tier or higher.
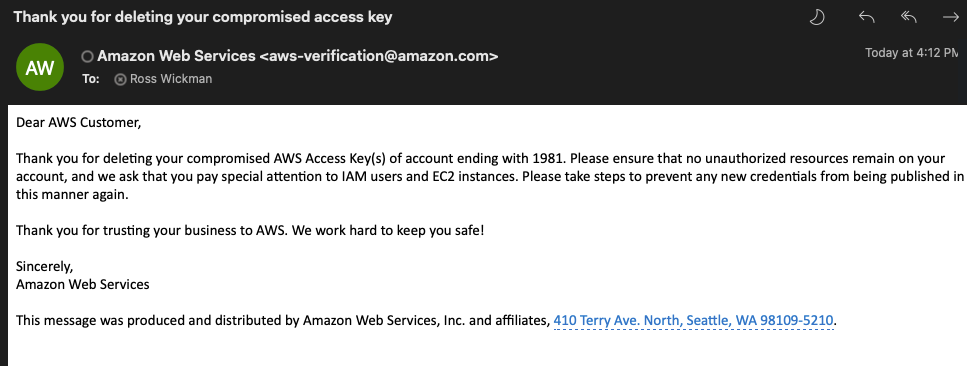
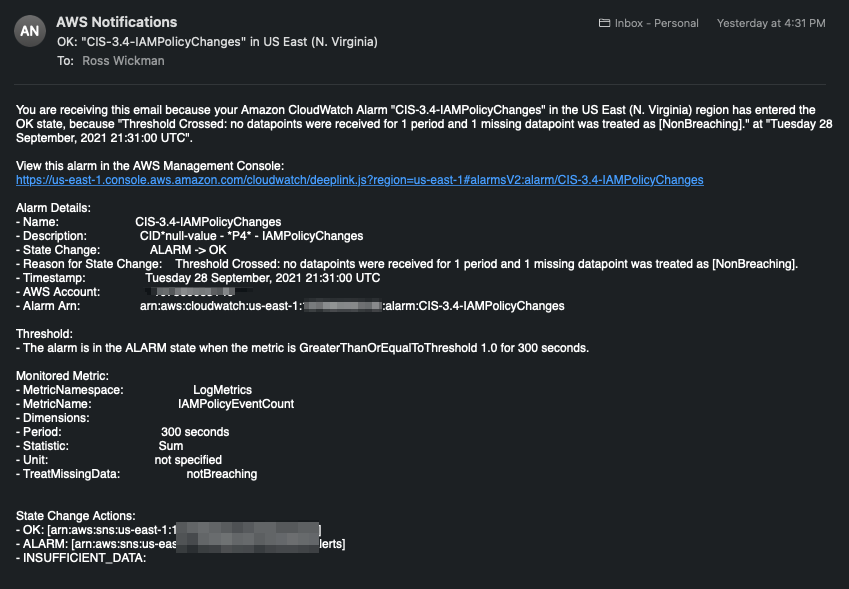
Update 2 - After deleting the Credentails but leaving my trusted-advisor-test IAM User in place, I was notified and thanked by AWS for removing the credentials from the user account.
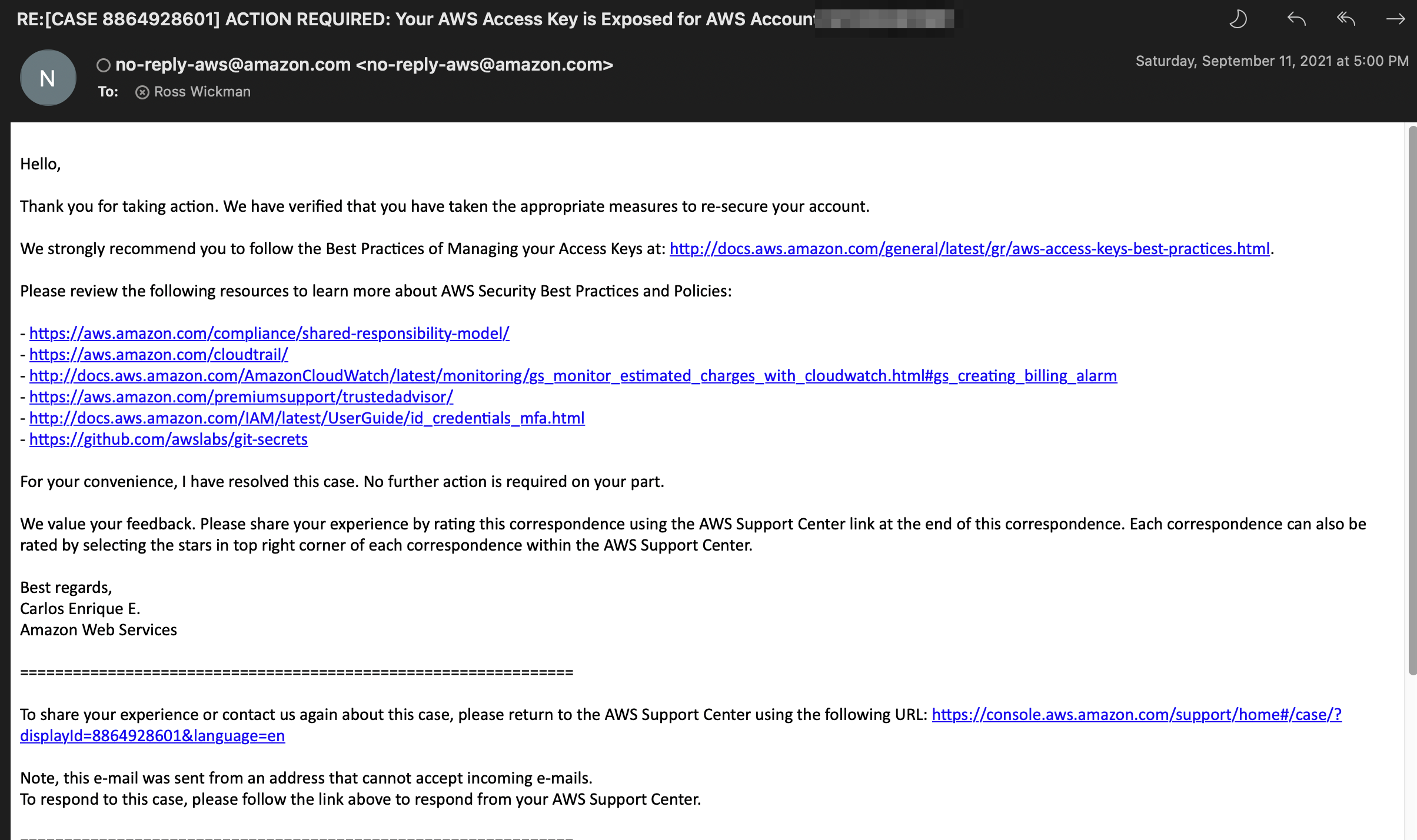
Update 3 - The following the initial event, AWS sent another email confirming I completed the required steps to fix the problem as well as provided additional resources for review.
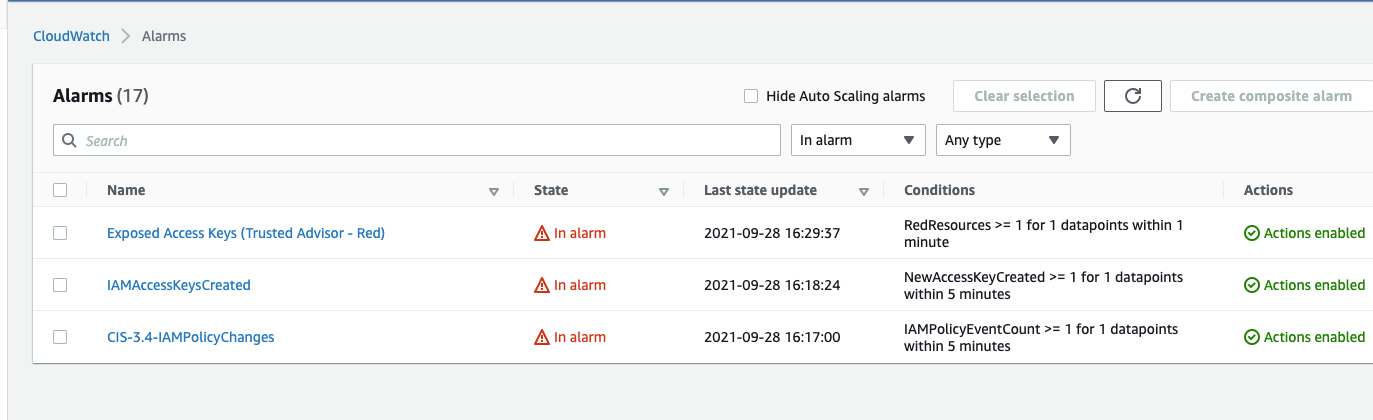
Update 4 - After getting to test in an account with Enterprise Support and other CloudWatch Alarms configured, there was a successful notificaiton for the CloudWatch Alarm created for the Trusted Advisor Exposed IAM Access Keys.
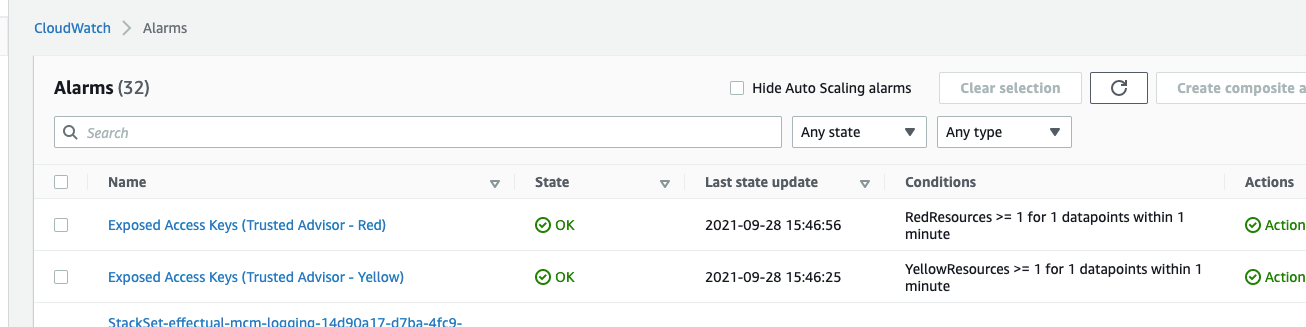
Testing completed for this process and implementation 29-Sept-21