Phobos Ransomware Analysis
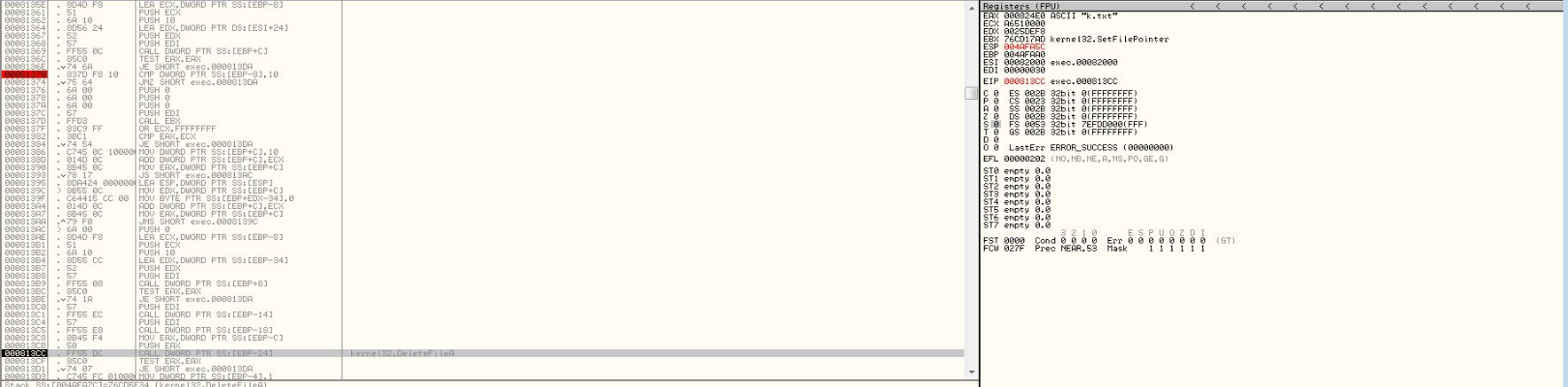
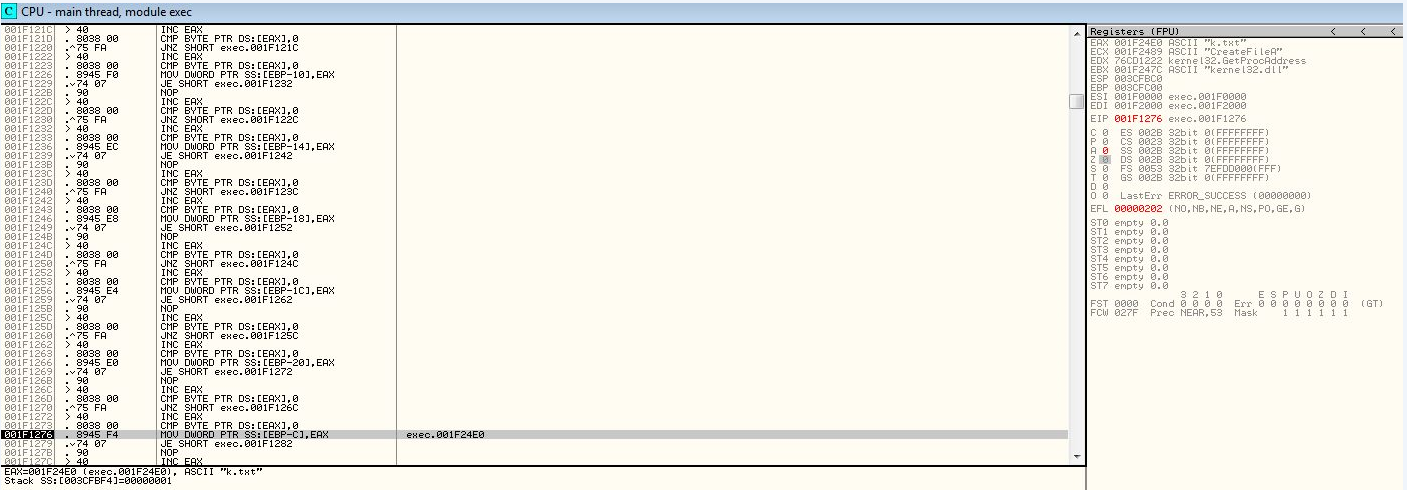
Apparently this phobos variant searches for C:\k.txt to extract its TEA key so it can decrypt its full payload.
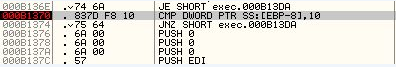
Take a look at the breakpoint in the above img, if the content of k.txt isn't right the CMP instruction will compare the 4 bytes in SS:[EBP-8] with the 4-byte integer constant 10. this memory adress contains:
so on the JNZ instruction we will jump and get TerminateProcess, lets patch it and continue.
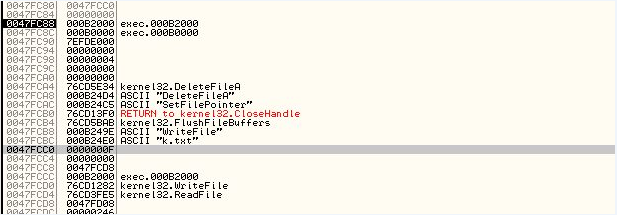
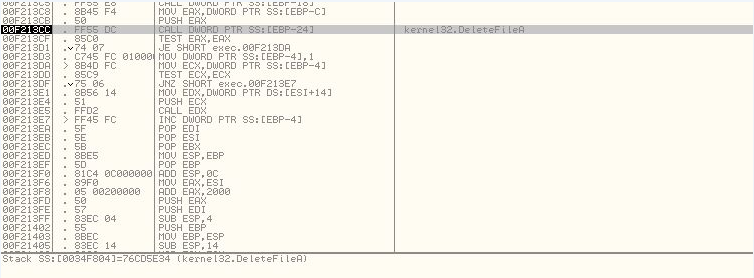
As you can see the malware scrumble the file before deleting it so recovering k.txt is probably impossible.
https://www.virustotal.com/#/file/8b0ee66b23e6a3ea684254df40a8a443103324b5c6bec3f2872ea1441a2024da/detection
#If someone holds both the malware and the key please share it!